Virlock is a polymorphic, file-infecting ransomware first discovered in 2014. In 2016 it demonstrated new capabilities allowing it to spread through shared applications and cloud storage. When executed, it drops three instances of itself. One instance carries out the file infection, another locks the machine, and the third creates a persistence mechanism by registering as a service. Attackers demand bitcoin payment from victims who want their systems unlocked.
The polymorphic nature of Virlock means every instance is different from a heuristic perspective, a tactic that effectively bypasses signature-based antivirus (AV) solutions. For example, Virlock drops three instances of itself during the first stage of its attack, each one implementing different obfuscation and persistence mechanisms. By varying the functionality that each instance implements, Virlock guarantees all three instances can evade a signature-based detection system.
Technical Analysis
Virlock decrypts and runs the original lure file when executing the first time on a non-infected machine. When executing on a previously infected machine it checks to see if a ransom has been paid. On successfully ransomed machines Virlock will decrypt the host file but take no further malicious actions. If a machine has not been successfully ransomed Virlock executes a malicious behavior (Figure 1) without decrypting the host file.
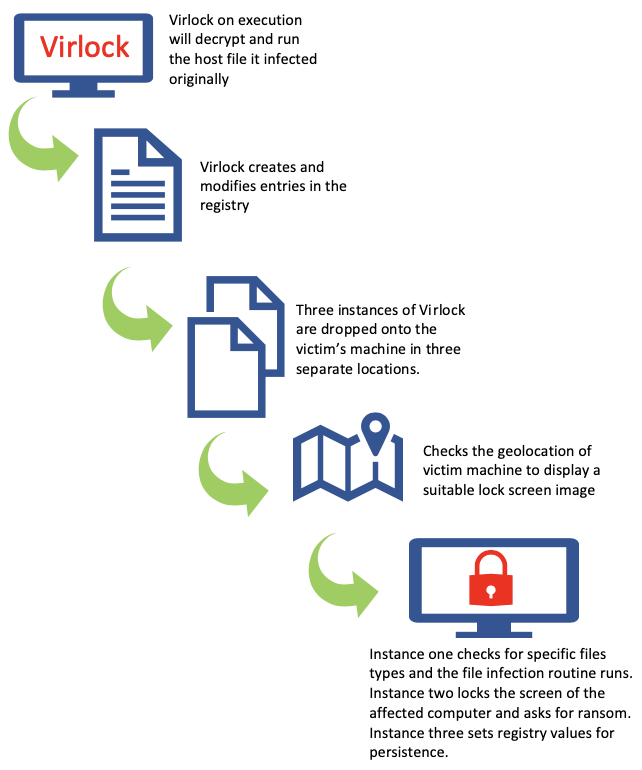
Figure 1: Execution flow
The malicious file was heavily obfuscated and included anti-debugging techniques that complicated analysis. During our investigation we observed the decoding and launch of the second stage payload:
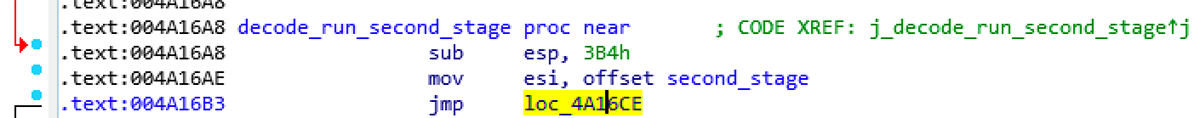
Figure 2: Jump to decode_run_second_stage
The decryption routine uses an incremental xor loop to decrypt the second stage. It checks to verify that the file has been fully decrypted, then calls the second stage:
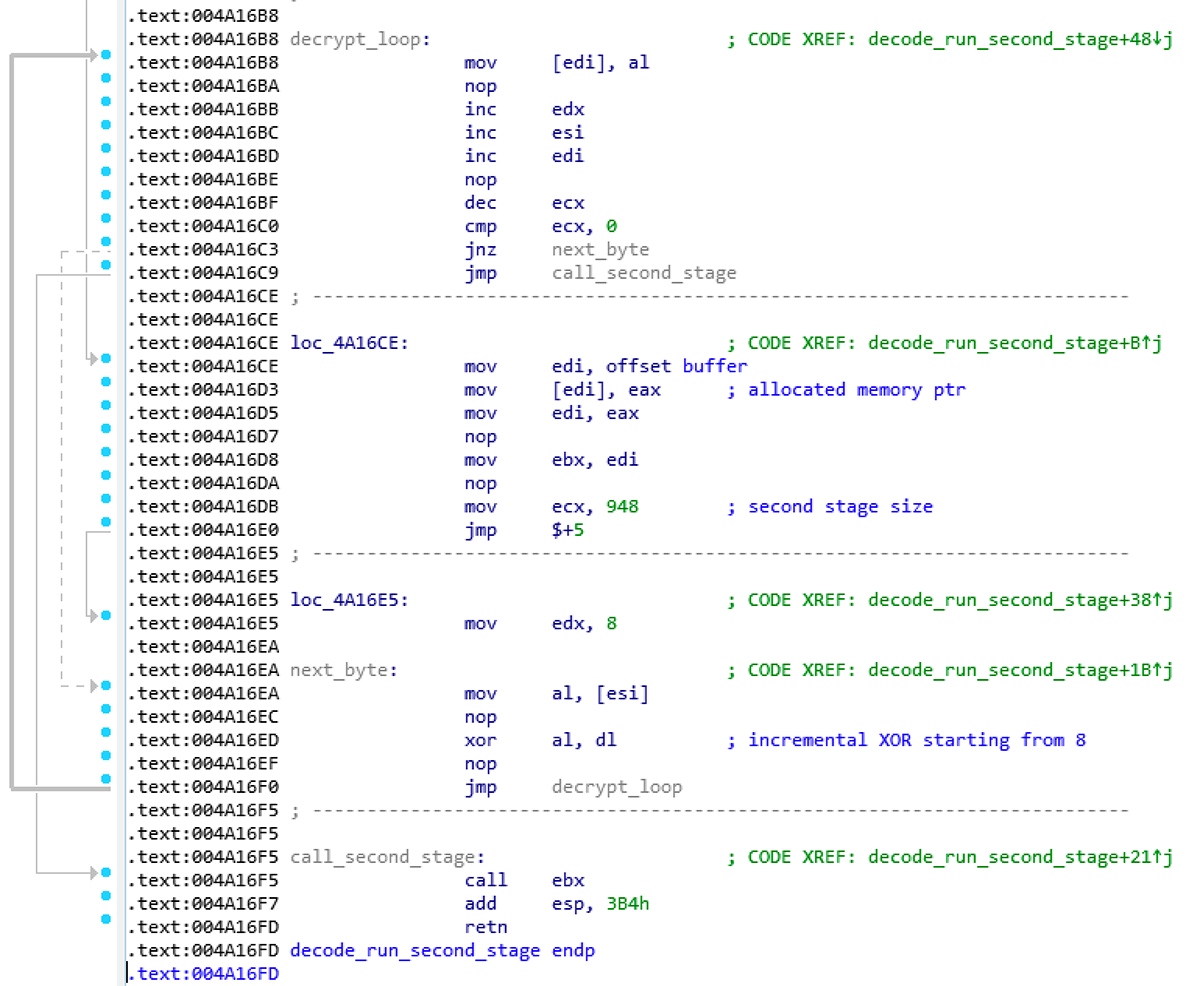
Figure 3: Decryption loop and call to second stage
Next, the second stage decrypts the data representing the instructions to be executed, in a virtualized way, by the third stage stub function. Once decrypted, the instructions bytes are injected into the “execute_opcode” function between RVA 0x1032 and 0x103B as shown in Figure 4.
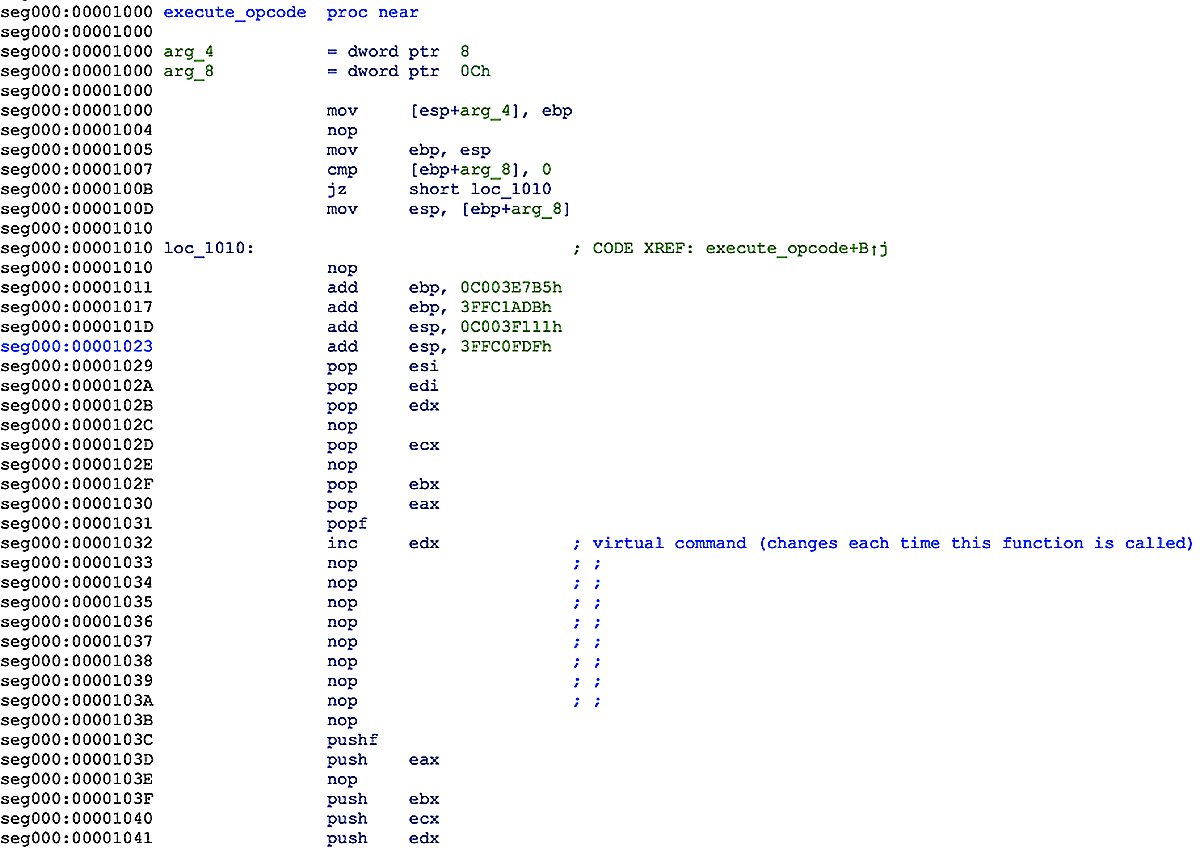
Figure 4: “inc edx” followed by a sequence of NOPs injected into the stub function
Payload Execution
The ransomware drops three instances of itself in three different locations upon execution:
Instance one:
File path: %AllUsersProfile%\<Random_folder_name>\<Random_file_ name>.exe
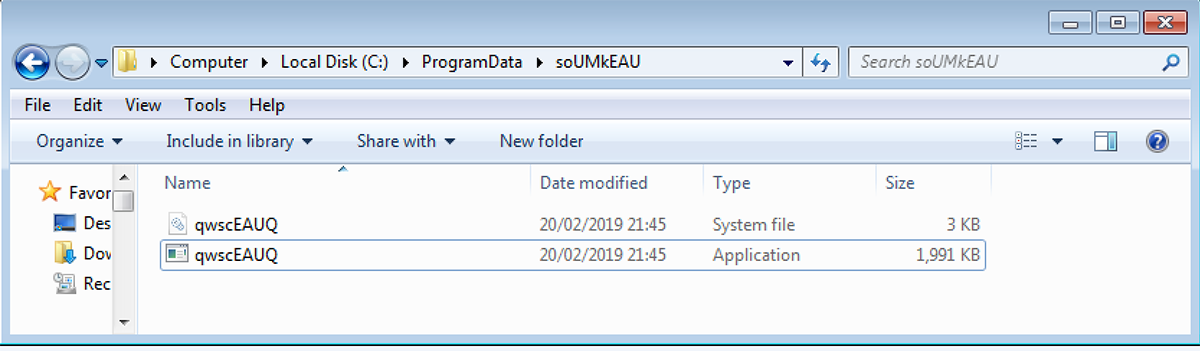
Figure 5: First instance dropped by original file
Instance two:
File path: %UserProfile%\<Random_folder_name>\<Random_file_name>.exe
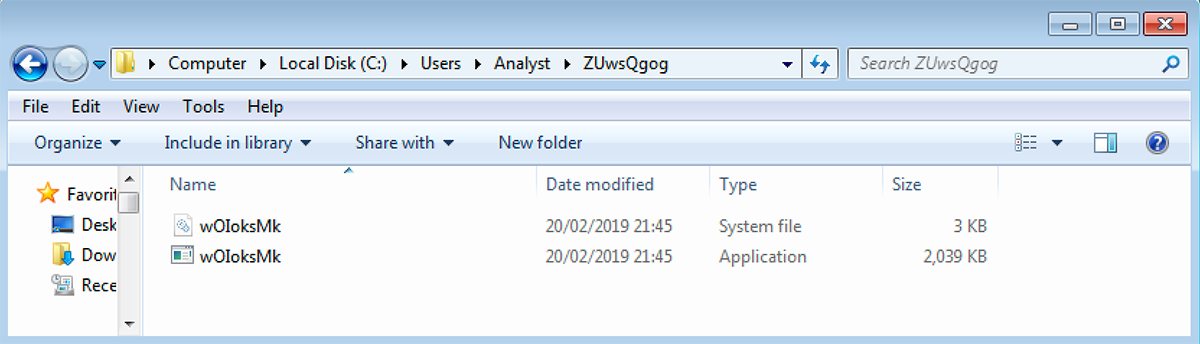
Figure 6: Second instance dropped by original file
Instance three:
File path: %AllUsersProfile%\<Random_folder_name>\<Random_file_ name>.exe
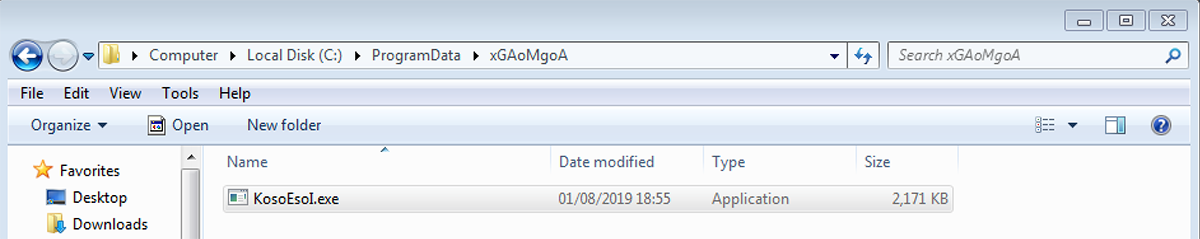
Figure 7: Third instance dropped by original file
Persistence
Virlock modifies the system registry to create persistence on an infected system. It sets two registry values of two randomly named instances of itself in the “CurrentVersion\Run” registry key. These settings cause the programs to run each time a user logs on:
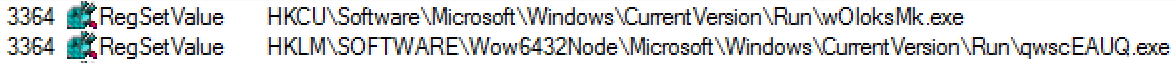
Figure 8: Persistence via Run Registry Key modifications
Virlock modifies a registry key that specifies which program WinLogon executes when a user logs on:

Figure 9: Persistence via Userinit Registry Value modification
Virlock’s registry key modification:
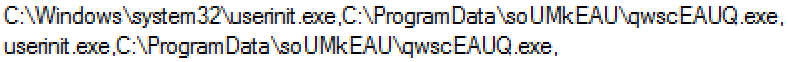
Figure 10: Registry modification for persistence
The third instance sets a value for a randomly named service:
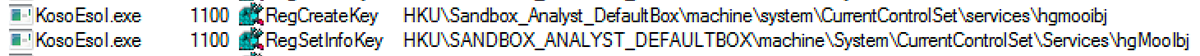
Figure 11: Persistence via new service registration
File Infection
After dropping three instances of itself, Virlock checks for specific file types to infect. Once the targeted file have been identified, the malware encrypts the file and then replaces it with a copy of the virus code with the encrypted original file content appended to it.
Targeted File Types: | |||||
.exe | .doc | .xls | .ppt | .mdb | |
.zip | .rar | .mp3 | .mpg | .wma | .png |
.gif | .bmp | .jpg | .jpeg | .psd | .p12 |
.cer | .crt | .p7b | .pfx | .pem |
|
Virlock appends an .exe file extension to all infected files, then modifies the registry to hide the file extensions. This is done to trick the user into executing the infected host file:

Figure 12: File extension registry change
Here is an example of the Notepad++ executable before and after infection:
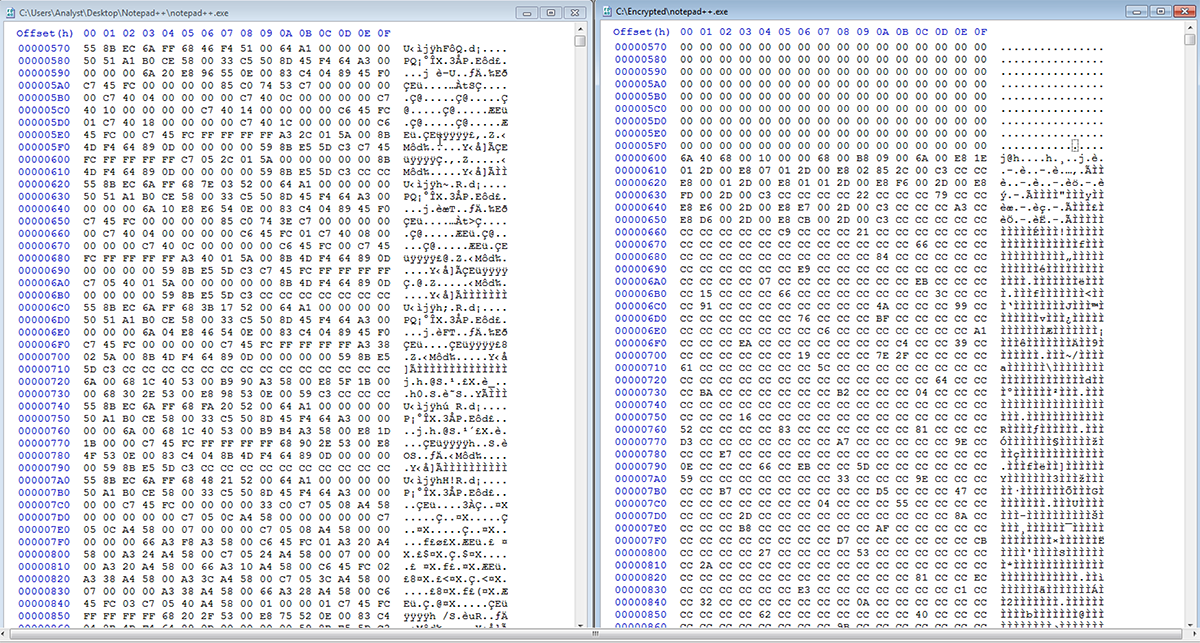
Figure 13: Before and after infection
Locked Screen
While Virlock is running and executing its file infection routine, its second instance locks the screen of the victim’s machine. During this process Virlock also shuts down the process explorer.exe and task manager. It checks the geolocation of the device by searching the registry and displays a message tailored to the victim’s location. The screen-lock message asks victims to pay a ransom in bitcoin:
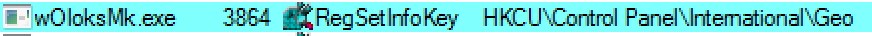
Figure 14: Checks registry geolocation of the machine
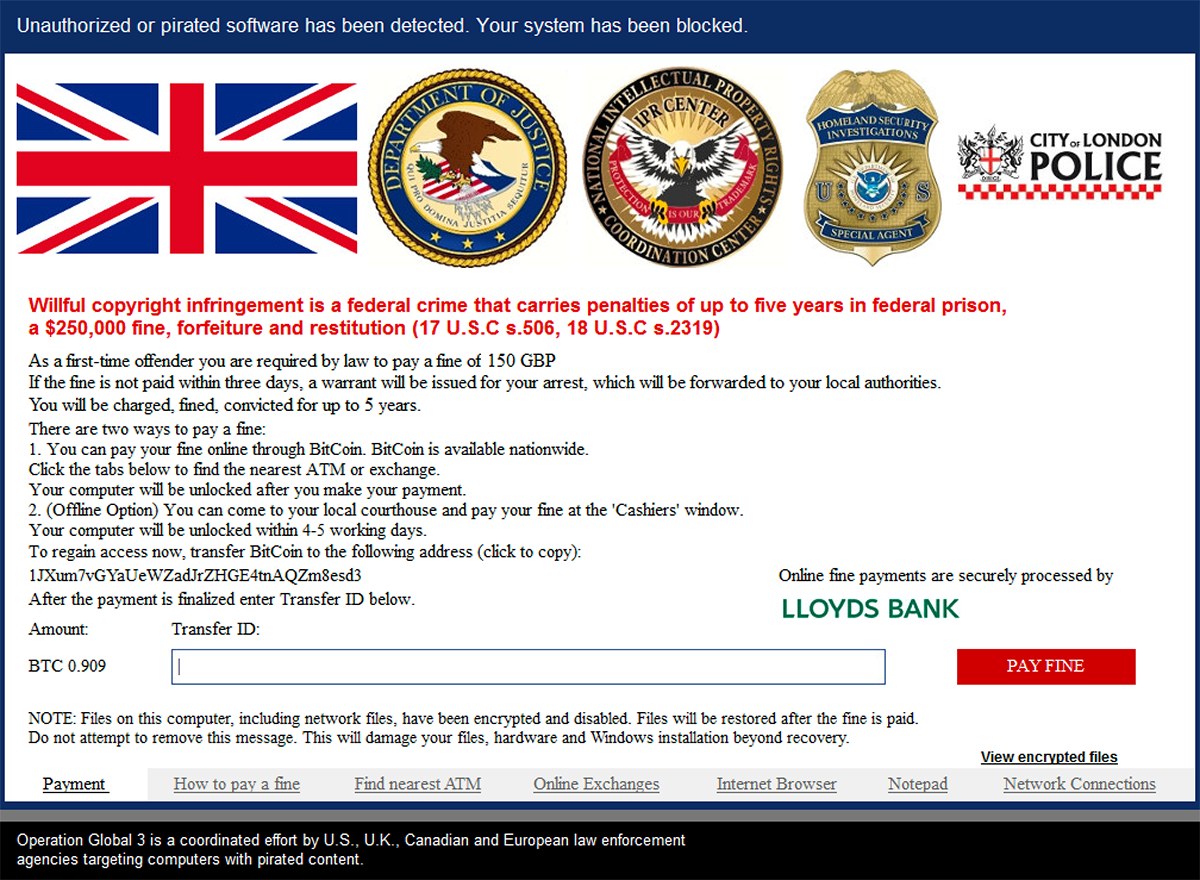
Figure 15: Lock screen message
Why Virlock is Important and Why You Should be Concerned
Virlock was first detected in 2014 but made resurgent appearances in 2016 and 2017. With each reappearance Virlock demonstrated new capabilities, indicating that the malware is actively developed and updated by cyber criminals. Virlock deploys an impressive triple-instance attack strategy and a location-specific ransom screen threatening users with fake legal action should they refuse to comply. With ransomware attacks costing organizations roughly $13,000 USD per incident, Virlock is a threat that businesses cannot afford to ignore.
BlackBerry Cylance Stops Virlock
BlackBerry Cylance uses artificial intelligence (AI)-based agents trained for threat detection on millions of both safe and unsafe files. This lets BlackBerry Cylance spot a threat based on countless file attributes instead of a specific file signature. Virlock is a polymorphic threat, capable of modifying its code, but this evasive tactic does not fool our AI-driven security agents. Our solutions analyze and convict threats based upon millions of threat features, not specific file signatures. Blackberry Cylance, which offers a predictive advantage over zero-day threats, is trained on and effective against both new and legacy cyber threatsattacks.
(EDITOR'S NOTE: This blog was updated on 8/5/2019 to add in extra detail from an extended technical analysis performed by our Threat Research team).

