Parite is a polymorphic file infector, meaning it creates several new variations of itself after infiltrating a host system. By implementing minor changes with each self-replication Parite effectively evades signature-based detection. The malware performs massive file infection upon the host which makes removal of this threat difficult and uncertain. A Parite infection often requires a full system re-image to ensure no obfuscated copies of the malware remain.
The BlackBerry Cylance Threat Research recently analyzed Parite to document the behaviors of this shapeshifting threat.
Parite Analyzed
When Parite executes it thoroughly propagates itself across the host environment. It searches the victim’s computer and network shares for two types of executable files (.exe and .scr). When these files are located, Parite adds the malicious code to a newly appended portable executable (PE) section.
Parite infected files generally originate from two sources, USB memory devices and the Internet.
Systems infected with Parite display four common characteristics:
- Additional/strange PE sections - The last PE file section name tends to follow this format: “.{Three ASCII characters}{Non ASCII character}” (e.g., “.khe{Non ASCII character}”). In addition, the entry point is changed “to store a relative virtual address (RVA) into the appended section.
- DLL file creation under %TEMP% - Viral code added by Parite drops a DLL file under %TEMP% directory. The dropped file has a random name and a .tmp extension (e.g. qal9A7.tmp). This file is loaded into the executable that originally dropped it. After the initialization phase, Parite uses the SetWindowsHookExA function to inject the dll file into other processes. The injected dll module checks whether the running process name is "explorer.exe". If it is "explorer.exe", Parite also checks whether there is the "Resident" mutex or not. If "Resident" mutex does not exists, Parite creates it.
- Mutex - Parite creates a mutex named Residented.
- New registry entries - The full path to the dropped DLL file is saved in the registry. Relevant registry entries include:
◦ Key – HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer
◦ Value – PINF
◦ Data – (e.g. %TEMP%/qal9A7.tmp)
Upon completing the infection process Parite returns to its original entry point and allows infected files to run as expected. By allowing infected files to operate normally, Parite can often hide its presence from casual observation for long periods of time.
Additional PE Sections
Files infected with Parite display three characteristics, see Figure 1:
1. The last PE section name tends to be:
".{3 readable alphabets}{Non ASCII character}"
2. The section is writable and executable
3. Parite changes the entry point from original to the last PE section
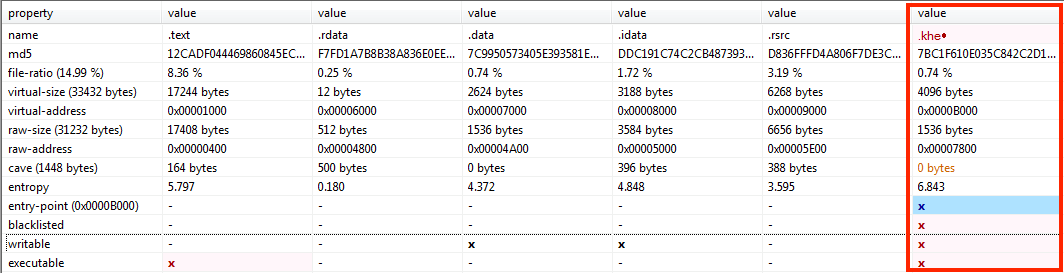
Figure 1: .khe{Non_ASCII character} appears on the last PE section.
DLL File Creation
The code in the last PE section of an infected file includes functionality to drop a DLL which is the main payload of Parite. Once a file infected with Parite runs, it drops a new file under %TEMP% as shown in Figure 2. The file name tends to be {random alpha numeric values}.tmp (e.g, qal9A7.tmp). While the file extension is .tmp the dropped file is actually a dll (see Figure 3):
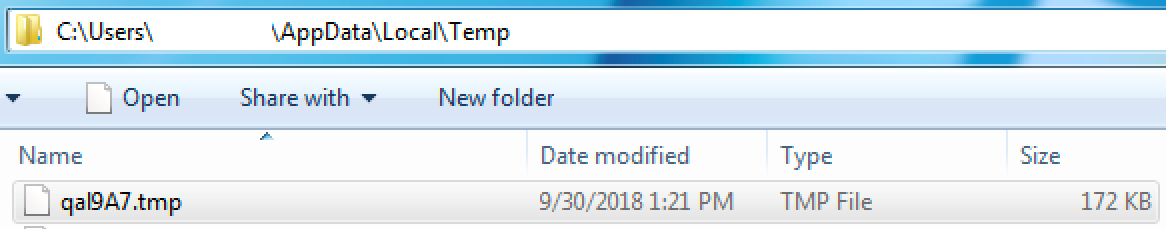
Figure 2: Dropped file by Parite
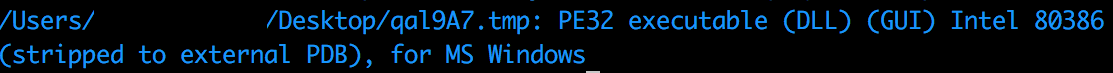
Figure 3: Dropped DLL file
Mutex
The first time Parite runs it creates a new mutex named Residented (Figure 4). During the initialization process, Parite checks Residented with OpenMutexA to ensure only one malware copy runs at a time (see Figure 5):
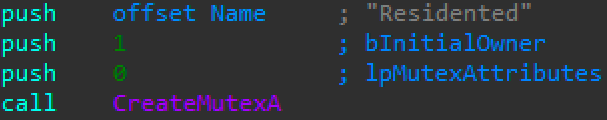
Figure 4: Create a new mutex, Residented
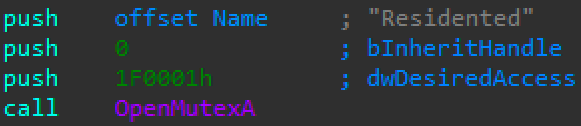
Figure 5: Check for the existence of Residented
The existence of Residented can be confirmed as seen in Figure 6:
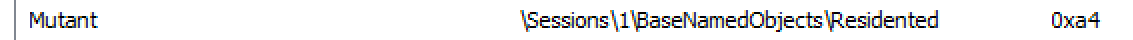
Figure 6: Residented mutex appears on an executable file infected with Parite
New registry entries
Parite creates a new registry value under HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer. The new entry name is PINF (Figure 7):
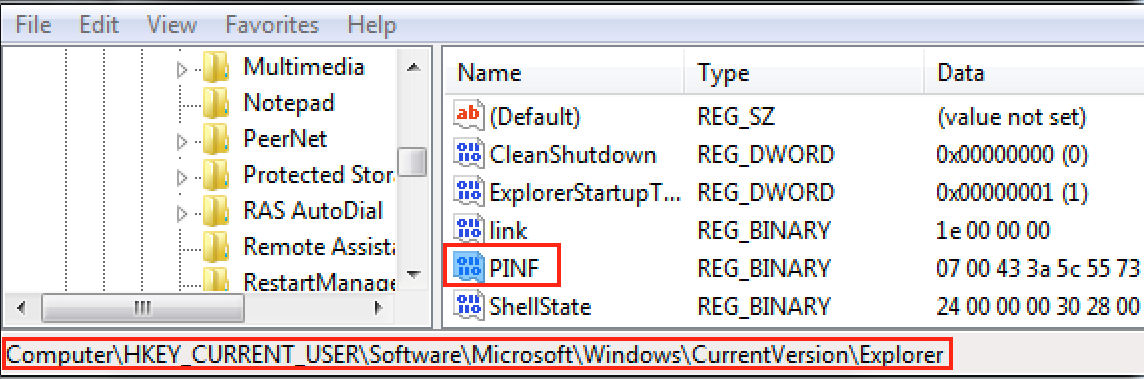
Figure 7: Parite creates PINF under HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer
The value data of the new entry points to the file dropped by Parite (Figure 8):
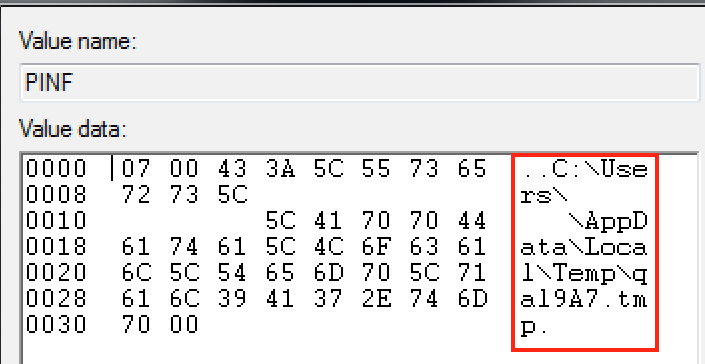
Figure 8: PINF points to the dll file dropped by Parite
File Infection Process
Parite infects files with the .exe or .scr extension. Both extension strings are referenced in the dropped DLL file (Figure 9):
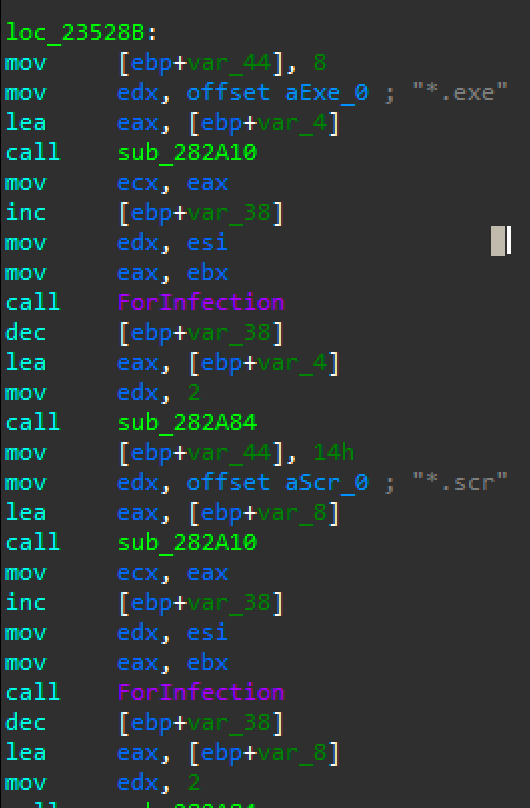
Figure 9: Parite searches files with .exe and .scr extensions
Parite also targets files on network drives as shown in the following code snippet (Figure 10):
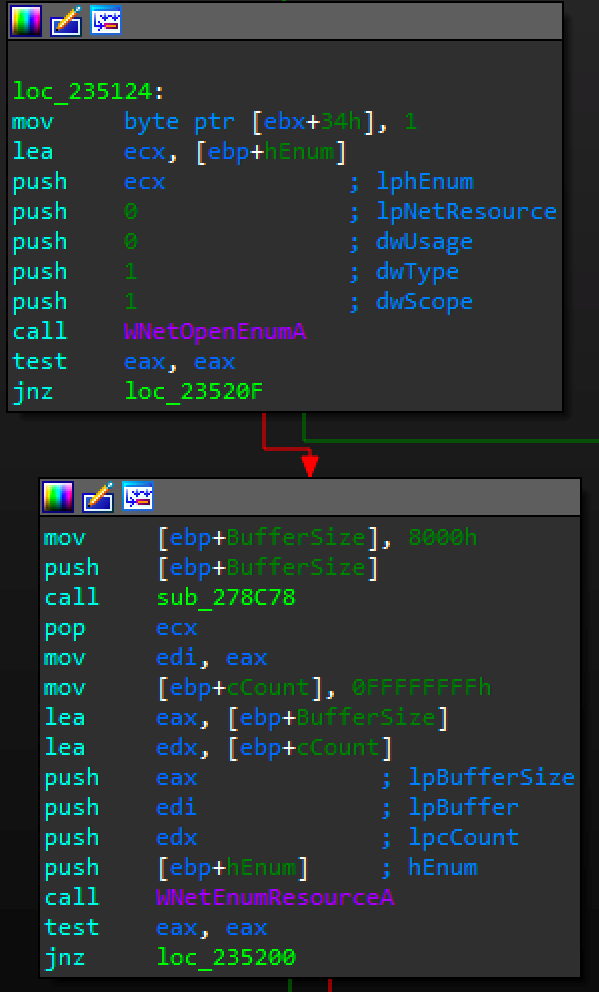
Figure 10: Parite searches network drives
When Parite finds files with an .exe or .scr extension it appends the infected PE section to them. The modifications applied to the section table of a targeted PE file are shown in the before and after screenshots in Figure 11 and Figure 12:
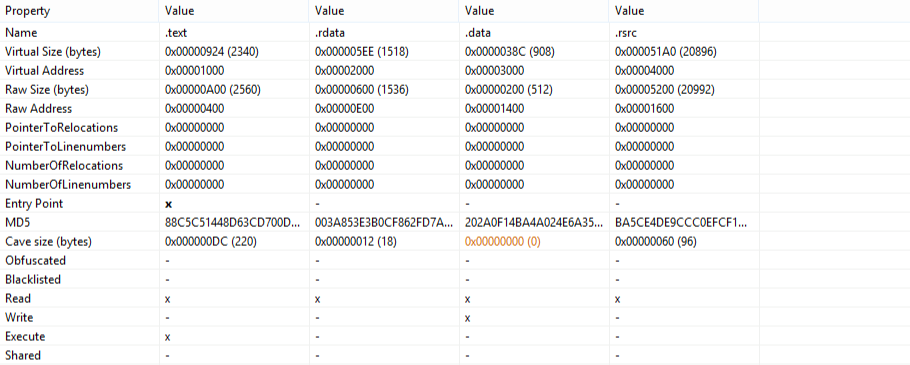
Figure 11: Before a Parite infection
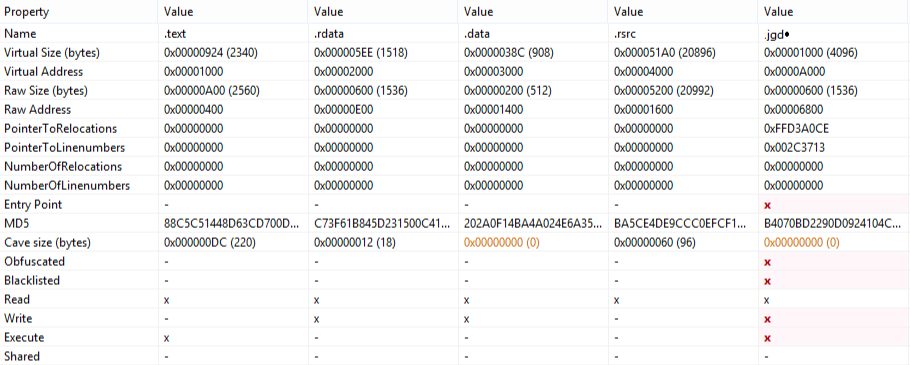
Figure 12: After a Parite infection
Why is Parite Important and Why Should I be Concerned?
Parite is engineered to evade traditional signature-based malware detection by creating multiple, varying, versions of itself. It slowly invades systems through massive self-propagation and hides its presence by allowing infected files to run normally. By the time a user notices a Parite infection, the only reliable way to remediate their system may be a complete re-image.
BlackBerry Cylance Stops Parite
CylancePROTECT® uses artificial intelligence (AI) agents trained for threat detection on millions of both safe and unsafe files. This allows CylancePROTECT to spot a threat based on countless file attributes instead of a specific file signature.
While Parite may change its digital ID multiple times on a host system, it never stops looking like a threat to our advanced AI-trained security solution. BlackBerry Cylance detects and prevents Parite and its countless variations before they can execute.

