BlackBerry Cylance vs. IcedID Banking Trojan
IcedID, originally known as BokBot, is a banking Trojan featuring modular malicious code and infostealing capabilities. It was first identified in the wild in September 2017 by IBM X-Force researchers.[1]
IcedID gathers financial information and credentials from infected hosts through sophisticated web injection and redirection attacks. The infostealer targets banking portals, webmail clients, payment card providers, mobile services providers, payroll portals, and online retail websites.
IcedID may be connected to past activity by the threat actor Neverquest. Neverquest was a Russian Cybercrime-as-a-Service group which disbanded in 2017 following the arrest of one of its members, Stanislav Lisov.[2],[3]
Technical Analysis
IcedID was initially delivered by another Trojan - Emotet.[4] Developed as a banking Trojan, Emotet has been repurposed to become one of the most successful threat distributors via its established botnet.[5] Emotet is generally delivered through spam carrying infected Microsoft Word document attachments. The Word document is often password-protected with the password appearing in the email body.[6]
The Word documents contain malicious macros which, if enabled by the user, invoke PowerShell to download the Emotet payload. Once successfully installed, Emotet downloads IcedID. IcedID uses Emotet's geotargeting capabilities to focus its attacks primarily on North America and the UK. Variants of IcedID were observed being distributed by Ursnif/Dreambot7, another Trojan similar to Emotet, early in 2018.
Threat actors traditionally work in competition with each other, often removing existing infections before installing their own malicious binaries on systems. There appears to be a recent shift towards threat actors using a more collaborative approach.
Analysts at Flashpoint identified host machines infected with both IcedID and Trickbot8 and highlighted a potential partnership between the two. IcedID's Command and Control (C&C) servers were observed sending commands instructing victim systems to download Trickbot and vice versa. Also, modifications to updated IcedID variants show indications they may have been influenced by Trickbot's modules.
Static analysis of this specific IcedID sample file shows a compile date of April 3rd, 2016 - over a year before IcedID was discovered in the wild. The binary contains a section named .ndata with a raw data size of 0 bytes. This indicates the executable was created with Nullsoft Scriptable Install System (NSIS). Extracting the Nullsoft archive reveals it contains several benign files and a malicious DLL file – aerometers.dll, SHA256:
19591882B072D3DA133E1C6106FDC0A4413DFB86CA5605F94ACBC4EB6968B693
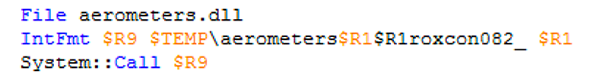
Figure 1: Extract from [NSIS].nsi file
A distinguishing feature of the IcedID infostealer is how it executes its process injection. It implements an alternative method that does not require the target process to be started in a suspended state. This approach has not been previously observed being used by malware authors.
When executed, the sample first launches a copy of itself. The sub process then starts the legitimate Windows process svchost.exe, where its malicious code is injected:
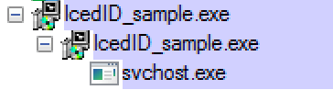
Figure 2: Spawned processes
It is not concerning to see multiple instances of svchost.exe running on a system as the process is used to load services run from Dynamic Link Libraries (SvcHost DLLs). Injecting IcedID's main payload into an svchost.exe process is an attempt by the attackers to conceal their activities on the victim machine.
The following functions allow IcedID to avoid starting the svchost.exe in a suspended state:
- kernel32!CreateProcessA
- ntdll!ZwProtectVirtualMemory
- ntdll!ZwAllocateVirtualMemory
- ntdll!ZwWriteVirtualMemory
The function ntdll!ZwCreateUserProcess is hooked within the memory space of the IcedID sample process. The kernel32!CreateProcessA function is then called to launch svchost.exe. Although svchost.exe has launched, its main thread has not been executed. The call to kernel32!CreateProcessA then hits the hook on ntdll!ZwCreateUserProcess which initiates a function call to ZwCreateUserProcess.
Next, ntdll!ZwCreateUserProcess returns the process handle for svchost.exe. With this process handle the ntdll!NtAllocateVirtualMemory and ntdll!ZwWriteVirtualMemory functions can write malicious code into the memory space of svchost.exe.
Calling svchost.exe without any arguments means it has no service to run and will result in the process terminating. Before svchost.exe shuts down the function ntdll!RtlExitUserProcess is called. The malware authors exploit this call to ntdll!RtlExitUserProcess by inserting a jump to the malicious code. The main thread of svchost.exe is then run and the original executable is terminated.
This minimalist approach to process injection is significant as the execution of malicious code is less likely to be detected by process hollowing countermeasures. It succeeds without creating the svchost.exe process in a suspended state or creating new threads in svchost.exe.
The IcedID sample dropped the malicious aerometers.dll file into the user Temp folder. The original IcedID executable is modified slightly before being copied (with a unique generated name) to the %ProgramData% directory, e.g. C:\ProgramData\{5D189AD3-A8D3-4093-881B-7E03AAE7B040}\pdkdkdkqg.exe. Each infection of this copied file has a unique hash.
IcedID requires a system reboot to complete its infection. The reboot requirement represents an effort to hinder sandbox analysis:
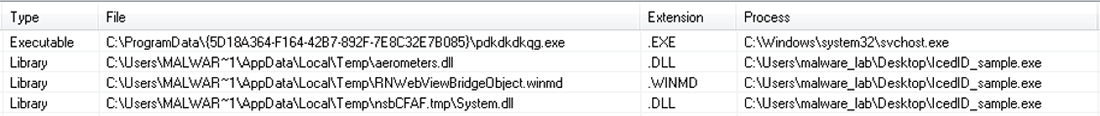
Figure 3: Files dropped to the system during dynamic analysis
Figure 4: Additional benign associated artifacts found in the user's Temp directory
A Windows scheduled task is created to launch the copied IcedID file located under the %ProgramData% directory (e.g. pdkdkdkqg.exe) for every user logon. This allows IcedID to achieve persistence and ensures the infostealer will continue to run following system reboots:
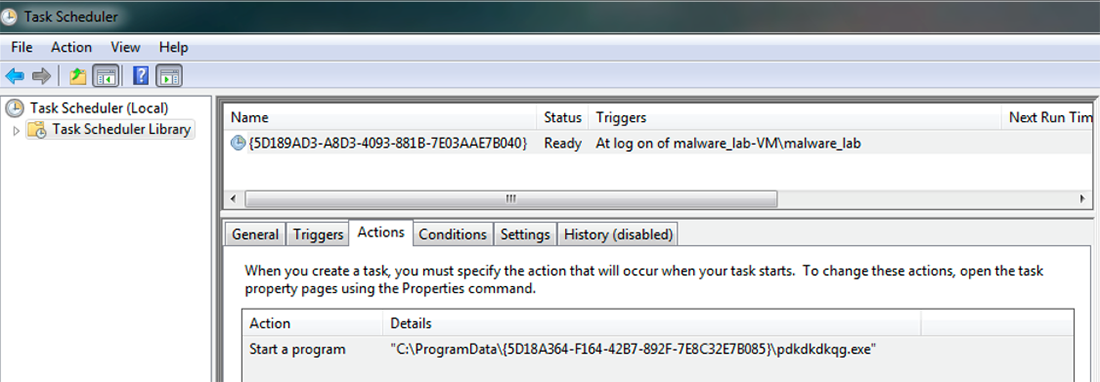
Figure 5: Windows Scheduled Task to launch IcedID with log on
IcedID gathers basic information about the host system to provide to the C&C server. This information is useful for identifying the specific infection bot. All communication between a victim and the C&C server is sent over HTTPS using POST- and GET-requests. Responses from the C&C are encrypted using RC4 and occasionally compressed using LZMAT.
IcedID includes a network spreading module that facilitates infecting other endpoints within an organization. The malware queries the Lightweight Directory Access Protocol (LDAP) to find other users and then attempts to brute-force passwords with a dictionary attack.
IcedID uses web injection to steal login information for targeted banking portals and online retailers. The infostealer downloads a configuration file from its C&C that includes a list of targets for the web injection attacks. It sets up a local proxy, listening on port 49157, to redirect the victim's Internet activity. This acts as a man-in-the-middle (MITM) style attack which can monitor all outbound traffic:
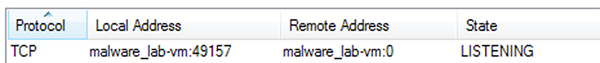
Figure 6: Process listening on localhost, port 49157
When the user attempts to navigate to a targeted URL the web injection attack will present fake content over the legitimate page. To an unsuspecting user, nothing will immediately appear out of the normal. The bank's genuine URL and SSL certificate still appear in the address bar. The local proxy intercepts the user's traffic and the login credentials are exfiltrated to the C&C server. All communications to the C&C server are encrypted and sent by SSL to avoid alerting Intrusion Detections Systems.
IcedID targets webmail accounts and payment card websites with redirection attacks. The local proxy redirects users to fake, nearly identical websites hosted by the attacker's server. The website will look legitimate by displaying the authentic URL and SSL certificate. Credentials submitted to the fake website are redirected to the attacker's server.
Blackberry Cylance Prevents IcedID
Blackberry® Cylance®, which offers a predictive advantage over zero-day threats, is also effective against malware like IcedID. Blackberry Cylance trains artificial intelligence (AI) agents for threat detection using millions of both safe and unsafe files.
Blackberry Cylance prevents IcedID and its variants from executing based on the detection of several malicious file attributes, not a specific file signature. This approach allows our customers to implement a prevention-first security posture effective against unknown, emerging, and polymorphic threats as well as traditional threats.
Indicators of Compromise (IOCs)
- SHA256 F476342981C639D55CE2F5471C3E9962FD2D5162890E55D2B4E45DDC641F207F delivered to the system by Emotet
- Aerometers.dll, SHA256 19591882B072D3DA133E1C6106FDC0A4413DFB86CA5605F94ACBC4EB6968B693
File Information
SHA256 |
F476342981C639D55CE2F5471C3E9962FD2D5162890E55D2B4E45DDC641F207F |
Type |
Malware Infostealer |
Size |
157,816 bytes |
Timestamp |
2016-04-03 21:20:55 |
ITW names |
IcedID, BokBot |
Sources:
[1] https://securityintelligence.com/new-banking-trojan-icedid-discovered-by-ibm-x-force-research/
[2] https://blog.talosintelligence.com/2018/04/icedid-banking-trojan.html
[3] https://www.justice.gov/usao-sdny/pr/russian-hacker-who-used-neverquest-malware-steal-money-victims-bank-accounts-pleads
[4] https://threatvector.cylance.com/en_us/home/cylance-vs-updated-emotet.html
[5] https://www.cylance.com/content/dam/cylance-web/en-us/resources/knowledge-center/resource-library/reports/Cylance-2019-Threat-Report.pdf?_ga=2.194100014.207560192.1557408928-1034628078.1557241850
[6] https://isc.sans.edu/forums/diary/Malspam+links+to+passwordprotected+Word+docs+that+push+IcedID+Bokbot/24428/
[7] https://threatvector.cylance.com/en_us/home/threat-spotlight-ursnif-infostealer-malware.html
[8] https://threatvector.cylance.com/en_us/home/blackberry-cylance-vs-trickbot-infostealer-malware.html

