Threat Spotlight: Nuke Ransomware
Nuke ransomware, first identified in 2016, encrypts files with an AES 256-bit encryption key that is protected by asymmetrically encrypting it using 2048-bit RSA. Once a file is encrypted, Nuke changes the file name to a combination of random characters followed by a .nuclear55 extension. For example, an infected file name might be “ab0a+afbamcdEcmf.nuclear55”.
Once Nuke executes it drops two files to the desktop: !!_RECOVERY_instructions_!!.html and !!_RECOVERY_instructions_!!.txt. The files inform the victim of the infection and provide details on how to pay ransom. Nuke also changes the desktop wallpaper to alert the user to the infection.
The BlackBerry Cylance Threat Research team recently analyzed a Nuke sample as part of our ongoing effort to inform the public about modern threats. This blog details our investigation.
Technical Analysis
The Nuke sample we analyzed hides itself by using an Adobe icon and displaying itself with the file name (and description) ‘Adobe Reader’:
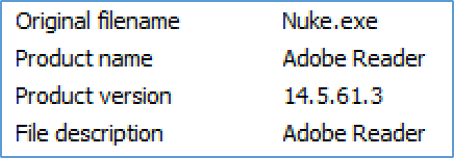
Figure 1: File displaying itself as Adobe Reader
The malware creates persistence by modifying registry keys to ensure it automatically runs at startup:

Figure 2: Modifying registry keys to ensure malware runs automatically at system startup
Nuke then begins the encryption process. File encryption is performed using standard AES and RSA encryption schemes. First, file bytes are symmetrically encrypted using an AES 256 key generated specifically for the victim’s machine. Next, the AES 256 key is asymmetrical encrypted using the attacker’s public RSA key and the result is appended to the encrypted file bytes. In order to decrypt the files, the RSA private key is required, which the attacker promises to supply to the victim once the ransom has been paid.
Once a file is encrypted its file name changes to a combination of random characters followed by the ‘.nuclear55’ extension:

Figure 3: File changes file name to random characters and appends ‘.nuclear55’ extension
Post-encryption, Nuke drops the file desktop_wallpaper.bmp and sets it as the victim’s desktop wallpaper:

Figure 4: Malware drops the file ‘desktop_wallpaper.bmp’
The wallpaper alerts the victim that their files have been encrypted (see Figure 5). It displays information about what type of encryption was used and provides instructions on how to recover the files. Victims are warned that the encryption key required to decrypt the files will be deleted after 96 hours. Users are instructed to send an email to ‘opengates[at]india[dot]com’ in order to receive further information on recovering their files:
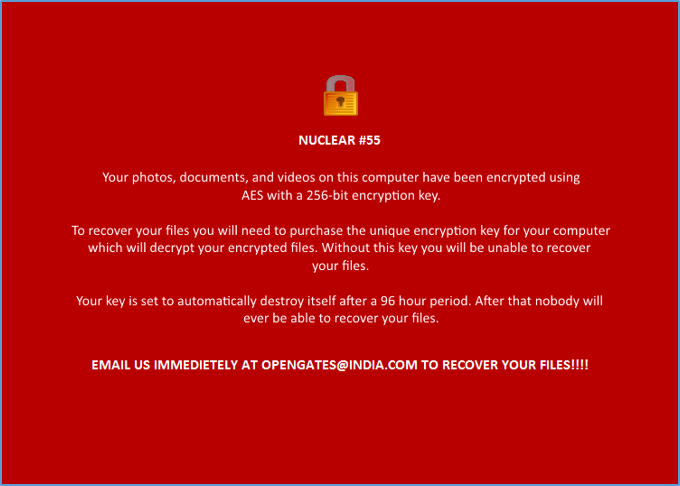
Figure 5: This is set as the victims’ desktop wallpaper post encryption of files
Nuke uses vssadmin to delete shadow volume snapshots by using the command “vssadmin delete shadows /all /quiet”. This command disables the windows repair and backup option, preventing users from restoring copies of the encrypted files.
Using vssadmin to prevent victims from accessing shadow volumes and recover encrypted files is a common tactic for ransomware. This has led some users to rename the vssadmin tool, thus causing ransomware calls to the tool to fail. By foiling malware calls to the vssadmin tool users can preserve access to their file backups.
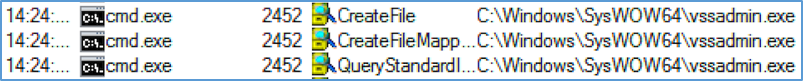
Figure 6: Uses vssadmin to delete shadow copy
Once the encryption is complete, Nuke drops two files to the victim’s desktop and launches them. The files are “!!_RECOVERY_instructions_!!.html” and “!!_RECOVERY_instructions_!!.txt” (see Figure 7 and Figure 8). These two files give the victim detailed information on what has happened and instructions on what to do next. Directions on how to obtain bitcoin and a bitcoin address for paying the ransom are also provided:
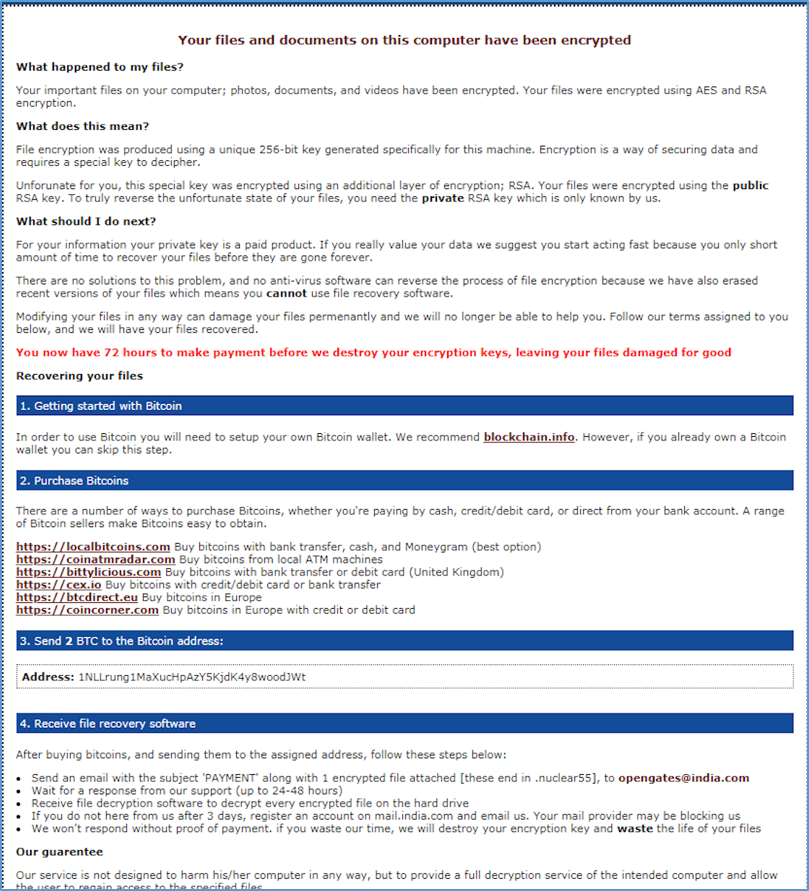
Figure 7: !!_RECOVERY_instructions_!!.html
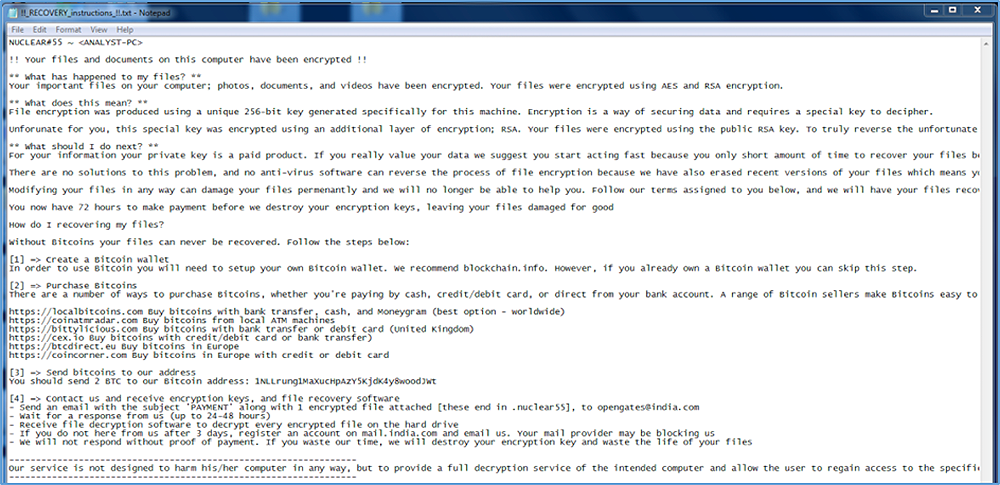
Figure 8: !!_RECOVERY_instructions_!!.txt
Conclusion
Innovative threat actors are working hard to ensure that Nuke and other ransomware remain a threat to organizations worldwide. In fact, ransomware recently experienced a resurgence after unknown adversaries ran several successful campaigns against global utility companies and local governments[1].
Having a robust, adaptive, and predictive security solution in place can save your organization considerable time and money.
If you are using CylancePROTECT®, you have been proactively protected from recent variations of Nuke for over three years (39 months). BlackBerry Cylance uses artificial intelligence-based agents trained for threat detection on millions of both safe and unsafe files. Our automated security agents block Nuke based on countless file attributes and malicious behaviors instead of relying on a specific file signature. Blackberry Cylance, which offers a predictive advantage over zero-day threats, is trained on and effective against both new and legacy cyber attacks.
For more information, visit https://www.cylance.com.
Appendix
File Information
SHA256 | a2d2a485d33fd2ea8cdae677efffda26911bc737d520d1e8d2028136b160c9fb |
Type | Win32 EXE |
Size | 82.5 kb |
Timestamp | 2016-10-13 |
ITW names | Nuke.exe Nuclear 55 |
Indicators of Compromise (IOCs)
STRINGS |
<li>If you do not here from us after 3 days, register an account on mail.india.com and email us. Your mail provider may be blocking us</li> |
<p>Your important files on your computer; photos, documents, and videos have been encrypted. Your files were encrypted using AES and RSA encryption. |
#nuclear55_content_middle{ |
Nuke.exe |
\<!--<li>For a free test decrypt, send one small file which will decrypt free</li>--> |
HASHES |
a2d2a485d33fd2ea8cdae677efffda26911bc737d520d1e8d2028136b160c9fb |
ab95f877d8fe99fa037a406087f9b71e |
FILES |
!!_RECOVERY_instructions_!!.html |
!!_RECOVERY_instructions_!!.txt |
BITCOIN WALLET ADDRESS |
1NLLrung1MaXucHpAzY5KjdK4y8woodJWt |
NETWORK ADDRESSES |
hxxp://yodel-safe-send[.]bowdenol[.]com/hello.php |
REGISTRY |
HKCU\Software\Microsoft\Windows\CurrenVersion\Run\nuke_html |
Citations:
[1] Palmer, Danny. “Ransomware: Why cities have become such a big target for cyberattacks - and why it'll get worse.” ZDNet, 24 Jul. 2019, https://www.zdnet.com/article/ransomware-why-cities-have-become-such-a-big-target-for-cyberattacks-and-why-itll-get-worse-before-it-gets-better/.

