Summary
During the latter half of 2019 and early 2020, the BlackBerry Research and Intelligence Team observed cyber-criminal gangs utilizing advanced tactics to infiltrate and ultimately extort money from victims using several prominent ransomware families (E.G.: Ryuk, Sodinokbi1 and Zeppelin2), with a distinct shift from widespread, indiscriminate distribution to highly targeted campaigns often deployed via compromised Managed Security Service Providers (MSSPs).
This recent trend also coincides with Ransomware-as-a-Service (RaaS) shifting to a more private model, where access to affiliates is more carefully vetted, and either sold or granted in exchange for sensitive information or an established foothold to compromised MSSPs and/or corporate/governmental networks.
Another alarming trend involves the exfiltration of data prior to, or during, the ransomware encryption process, enabling attackers to blackmail victims with the threat of sensitive data leakage should they fail to pay in a timely manner.
BlackBerry threat researchers observed that approximately 10% of attacks detected/responded to by BlackBerry security products and services utilized the new tactic of threatening to release data. Disturbingly, our researchers learned that within this group, all of the targeted users who opted not to pay out subsequently had their data released by the threat actors in some way – some on Russian hacker forums, others on DarkWeb sites. Some users had all of their data released and others had just portions of their data released.
Based on investigative factors*, approximately half of these observed attacks were deemed to have been targeted towards specific users, leading one to the conclusion that threat actors hand-picked these targets based on their perceived ability to “pay up”, or alternatively banking on the sensitivity of the exfiltrated information to increase their target’s willingness to pay the ransom to preserve the integrity of their data. It is worth noting that this number increased observably over the time our researchers were monitoring these cases, with fewer users being specifically targeted earlier in the year and a larger percentage later in the year. This may be related to the increasing trend of collaboration and information sharing between ransomware threat actors, as in the case of Emotet and Trickbot3.
Around a fifth of the cases out of the group we observed involved the compromise of a managed security services provider (MSSP). To their credit, most MSSPs did a great job of owning the intrusion in most cases, but that does not mean that no harm was done as a result of these attacks.
In an interesting twist to all of the above, threat actors are also threatening to alert data regulators to the fact that victims had been breached and suffered exfiltration of sensitive data, adding additional pressure on the targets to cave to their demands. Since the introduction of General Data Protection Regulation (GDPR) in Europe, companies can face hefty fines if discovered to be victims of an unreported data breach. In some cases, paying the ransom might even seem an easier and cheaper way to resolve the issue – and that’s what the attackers are counting on.
Shifting Threat Tactics
Although these blackmail tactics are not new, up until recently it has been extremely rare for threat actors to actually carry out their threats. However, recent disclosures from the Maze and Sodinokibi affiliates4 highlight a change of approach.
The ransomware business has thus far proven to be infinitely flexible – evolving and adapting to changing circumstances. Since companies and institutions around the world have improved their data handling mechanisms by making backups more frequent and more secure, a promise of data recovery might no longer be enough to convince the victims to pay hefty ransoms. In some cases, publication of sensitive information can prove significantly more damaging to the business than data loss – and far more likely to produce the desired result of a ransomware payment.
For example, in one recent message uncovered by the BlackBerry Research and Intelligence Team, a threat actor claiming to have gained access to several high profile corporate and government networks was seeking a ransomware family to deploy to victims:

Figure 1: Message from attacker seeking ransomware for distribution
Ultimately, the threat actor was able to obtain a copy of the Zeppelin ransomware, which was deployed to multiple victims and contained the same email address embedded within the ransom note:
Figure 2: Zeppelin ransomware note showing the attacker’s email address
We can glimpse some of the dynamics of the current ransomware business due to the fact this message leaked to Pastebin - possibly from some kind of membership-only DarkNet forum. Threat actors behind the biggest ransomware campaigns are employing more careful and sophisticated business models, thereby becoming even more dangerous and elusive. There are still some RaaS families that target individuals and are available to be used by anybody, but these seem to be being slowly phased out, and the damage done is far less serious than in the case of targeted campaigns
The Evolution of Ransomware Campaigns
Below is a comparison of the last year’s most notorious ransomware campaigns. It’s worth noticing that three of them have significantly evolved their business models compared to their predecessors:
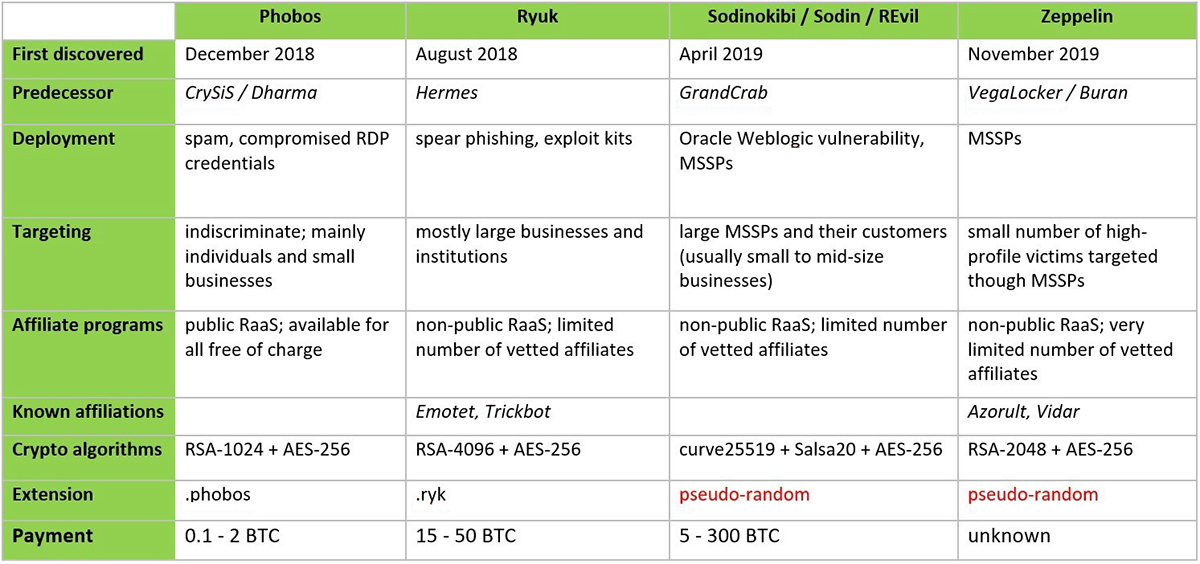
Figure 3: Most notorious ransomware families in 2019
Zeppelin is a direct descendant from the family of commodity ransomware that includes VegaLocker, Buran5, and Jamper. The malware itself doesn’t implement any significant changes compared to its predecessors, but the campaign that it has been part of is remarkably different. Whereas VegaLocker was distributed in malvertising campaigns targeting mostly Russian speaking individuals, and Buran/Jamper/Storm are incarnations of the widely advertised RaaS, the Zeppelin campaign seems to be very exclusive and strictly regulated.
The Sodinokibi campaign is believed to be directed by the same actors that were behind the infamous GrandCrab6 ransomware. The GrandCrab campaign was shut down by cybercriminals after the master decryption keys were obtained by the FBI and later published, making the decryption process possible for most of the affected victims. Given these circumstances, it’s no surprise that the gang decided to abandon the GrandCrab project and look for a better, more secure business model.
In the recent Sodinokibi campaign, the threat actors redeveloped the malware from scratch, but also changed their approach to the affiliates. They still seem to possess the master decryption key, which allows them to decrypt files encrypted by any of their partners, but in this case the affiliates are vetted more thoroughly to minimize the risk of leaks, and so far there is no free decryption tool available.
Ryuk ransomware is largely based on the source code of Hermes ransomware. Unlike its predecessor – which has been advertised on many underground forums and used in several campaigns, both targeted and indiscriminate – Ryuk is tailored to enterprise environments and used exclusively in a non-public campaign with a limited number of affiliates. The actors behind Ryuk also teamed up with the TrickBot7 and Emotet8 groups in order to exfiltrate sensitive data prior to file encryption. The threat of releasing the stolen data was then used to blackmail the victim into paying the ransom. This approach seems to pay off, as the gang is believed to have earned millions of dollars in just a few months, with a relatively low number of victims, but a much higher average ransom demand and better success rate.
Ransomware in the Age of COVID-19
With a significant portion of the world’s corporate office workers now working from home following the global COVID-19 outbreak, companies should be on high alert for scammers and threat actors seeking to capitalize on hastily set up and insecure remote work networks and the proliferation of BYOD endpoints.
As of the time of writing, it's too early to say whether there have been any significant changes in cyberattack tactics and targets, but based on our observances to date, the ransomware business seems to be operating uninterrupted as usual. Business owners and employees should be aware that, as happens with pretty much any large natural or man-made disaster, news reports indicate9 that cybercriminals have already started using COVID-19 related themes as a lure; for example, downloadable maps purporting to show outbreaks of the virus near the user’s home (laced with malware), and similar scams10 such as phishing emails that can lead to identity theft or financial losses.
Scammers will always prey on the fear caused by these kinds of national and global disasters, so a healthy dose of skepticism is the best response against any offer that seems ‘too good to be true’.
To Pay or Not to Pay?
As a matter of principle, the security community doesn't recommend paying cybercriminals, simply because doing so justifies and propels the ransomware business. However, we do understand that in some of the highly targeted and most damaging attacks (for example on critical infrastructure or healthcare providers) there might be no other way to recover and preserve human life but to meet the ransom demands. Since the individual cases and circumstances vary dramatically, there is no golden rule. In any scenario, though, the victims should work closely with law enforcement and do everything possible to help with the investigation.
The Final Word…
Considering the severity of these recent developments, it is more imperative than ever to ensure that ransomware incidents are dealt with swiftly, transparently, and in accordance with local data regulators and laws, in order to avoid considerable cost and reputational damage due to poor incident handling.
Citations:
1 https://threatvector.cylance.com/en_us/home/threat-spotlight-sodinokibi-ransomware.html
2 https://threatvector.cylance.com/en_us/home/zeppelin-russian-ransomware-targets-high-profile-users-in-the-us-and-europe.html
3 https://threatvector.cylance.com/en_us/home/blackberry-cylance-vs-trickbot-infostealer-malware.html
4 https://krebsonsecurity.com/2019/12/ransomware-gangs-now-outing-victim-businesses-that-dont-pay-up/
5 https://www.zdnet.com/article/vegalocker-evolves-into-buran-ransomware-as-a-service/
6 https://threatvector.cylance.com/en_us/home/cylance-vs-gandcrab-ransomware.html
7 https://threatvector.cylance.com/en_us/home/blackberry-cylance-vs-trickbot-infostealer-malware.html
8 https://threatvector.cylance.com/en_us/home/threat-spotlight-emotet-infostealer-malware.html
9 https://www.fool.com/personal-finance/2020/04/21/these-covid-19-scams-have-cost-americans-134-milli.aspx
10 https://www.fcc.gov/covid-scams
* This figure was calculated by researchers based on our own internal data drawn from Incident Response (IR) engagements by BlackBerry, and compared side-by-side with publicly available information from the same time-frame.

