BlackBerry Protect vs. CoViper Malware
As it tends to happen whenever society goes through a major event, cybercriminals have recently been using COVID-19 as an opportunity to lure victims into phishing campaigns by impersonating the Centers for Disease Control and Prevention (CDC) or similarly the World Health Organization (WHO), with the end-goal of stealing users’ personal information.
More recently, we have observed malware attacks targeting multiple platforms such as the traditional Windows® OS, but also Android™ and Linux® operating systems in a variety of forms such as Trojans, ransomware, and wipers.
Similar to other threats we have seen in the past such as MBRKiller, the coronavirus-themed CoViper malware overwrites the Master Boot Record (MBR) of the victim, leaving the computer useless from an operating system standpoint:
VIDEO: Watch BlackBerry® Protect in action against CoViper malware
Upon execution on a machine, CoViper drops three PE executables, one vbs script, two Windows batch scripts, one icon image, and one backscreen image to a specific folder as follows:
- (/C/COVID-19/end.exe)
c3f11936fe43d62982160a876cc000f906cb34bb589f4e76e54d0a5589b2fdb9
MBR Wiper module
- (/C/COVID-19/mainWindow.exe)
b780e24e14885c6ab836aae84747aa0d975017f5fc5b7f031d51c7469793eabe
Create coronavirus window module
- (/C/COVID-19/run.exe)
c46c3d2bea1e42b628d6988063d247918f3f8b69b5a1c376028a2a0cadd53986
Persistent launcher of mainWindow.exe with run.bat
- (/C/COVID-19/Update.vbs)
a1a8d79508173cf16353e31a236d4a211bdcedef53791acce3cfba600b51aaec
- (/C/%Temp%/831A.tmp/run.bat)=
df1f9777fe6bede9871e331c76286bab82da361b59e44d07c6d977319522ba91
- (/C/%Temp%/CD61.tmp/coronavirus.bat)=
4fd9b85eec0b49548c462acb9ec831a0728c0ef9e3de70e772755834e38aa3b3
- (/C/COVID-19/cursor.cur)
13c4423ed872e71990e703a21174847ab58dec49501b186709b77b772ceeab52
- (/C/COVID-19/wallpaper.jpg)
4a17f58a8bf2b26ece23b4d553d46b72e0cda5e8668458a80ce8fe4e6d90c42d
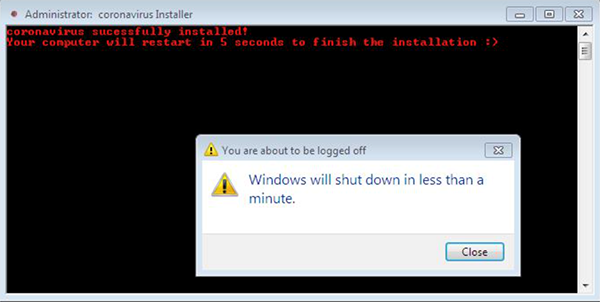
At first, this file executes ‘coronavirus.bat.’ This script is used for setting up persistence of these files. It disables the Windows Task Manager tool and User Access Control (UAC) function. It then executes a first reboot:
Figure 1: Coronavirus.bat executing
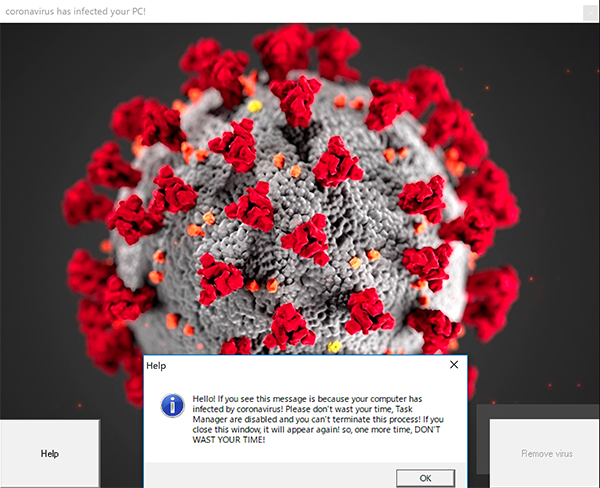
After the first reboot, it executes the run.exe, end.exe, mainWindow.exe and Update.vbs files previously dropped. When the victim logs back into the operating system, CoViper modifies the wallpaper to a black background and executes ‘mainWindow.exe’ which displays a message announcing that the computer has been ‘infected by coronavirus’:
Figure 2: Ransom note by CoViper
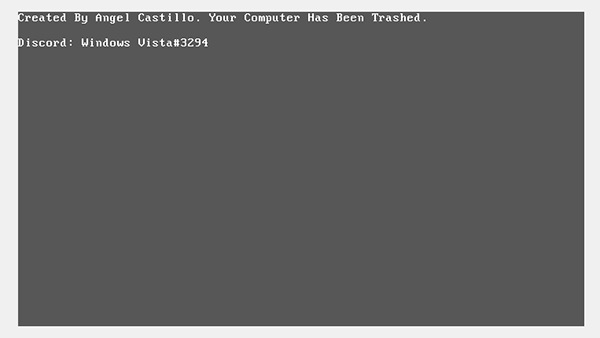
After the second reboot, the MBR has been broken by end.exe, and the victim is unable to use their computer:
Figure 3: Gray screen of death showing part 2 of ransom note
In addition, the update function in Update.vbs seems to be under construction. It has a sleep function but not much else, it doesn’t update, and there is no ransomware message or contact address for receiving money or virtual coin in this application. This could be included in a follow up version.
BlackBerry Defeats CoViper Malware
The BlackBerry Predictive Advantage is able to prevent this threat from executing five years before it existed. The conviction is made with no additional intervention, no updates and no need for Internet connectivity, while also maintaining our well-recognized low friction on system resources.