BlackBerry’s Open Source PE Tree Tool for Malware Reverse Engineers
Today at BlackHat, we announced the availability of PE Tree – a new open-source tool developed by the BlackBerry Research and Intelligence team for viewing Portable Executable (PE) files in a tree-view using pefile and PyQt5. Aimed at the reverse engineering community, PE Tree also integrates with HexRays’ IDA Pro decompiler to allow for easy navigation of PE structures, as well as dumping in-memory PE files and performing import reconstruction.
Overview
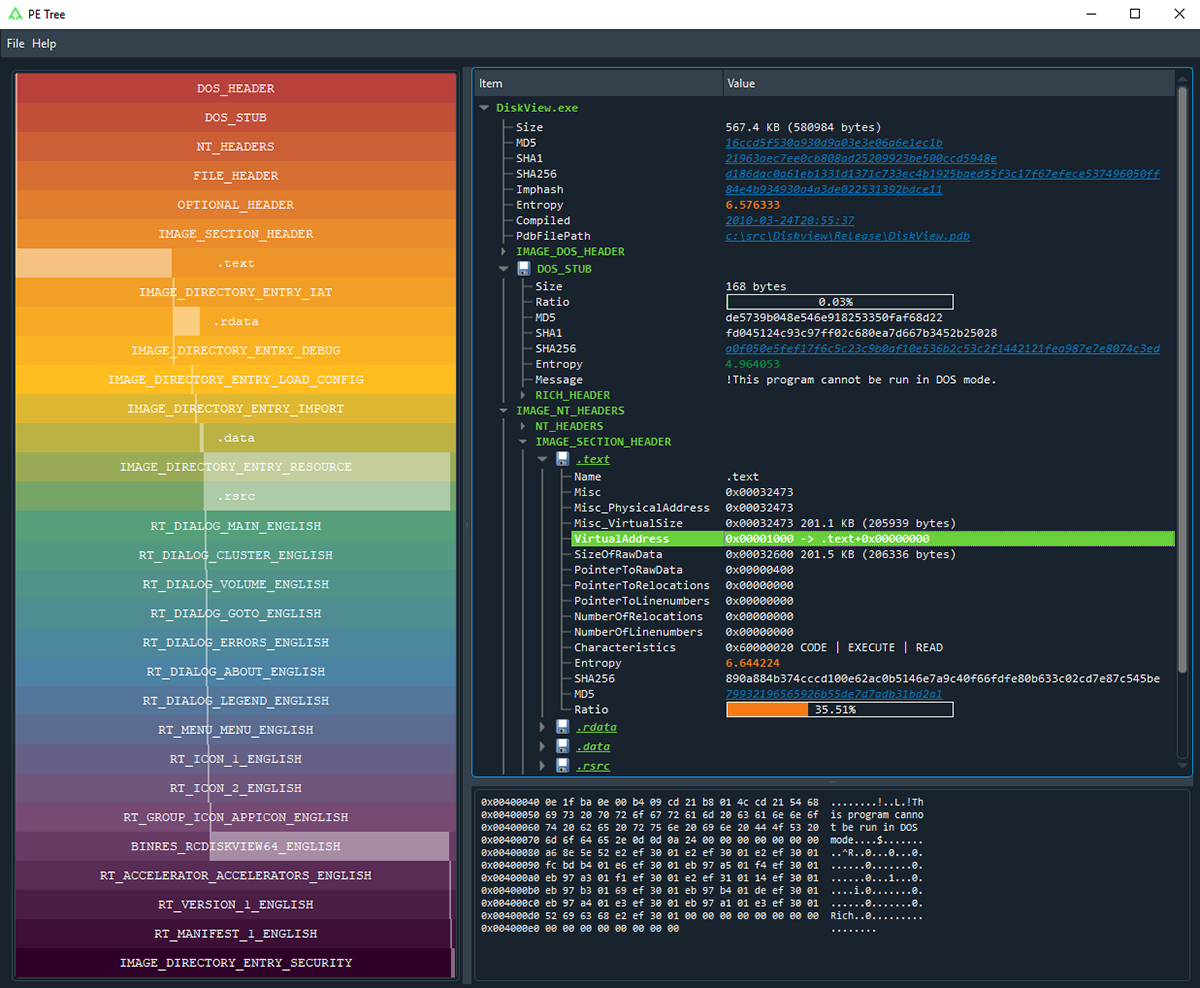
PE Tree is developed in Python and supports the Windows®, Linux® and Mac® operating systems. It can be installed and run as either a standalone application:
Figure 1. Standalone application
… or an IDAPython plugin:
Figure 2. IDAPython plugin
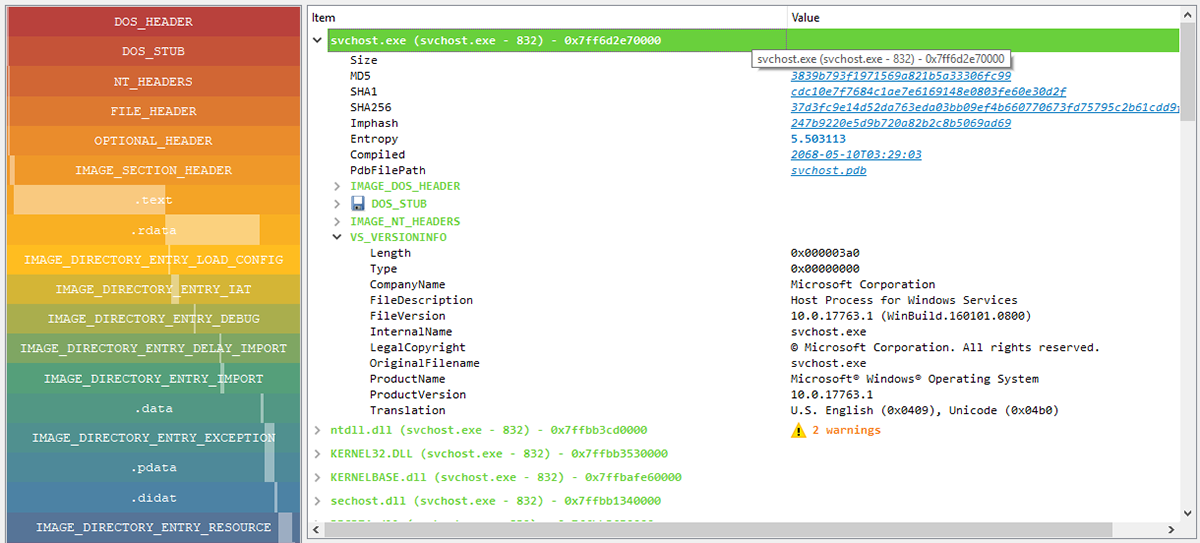
PE files are parsed using Ero Carrera’s pefile module before being mapped into a tree-view, providing a summary of the following headers:
- MZ header
- DOS stub
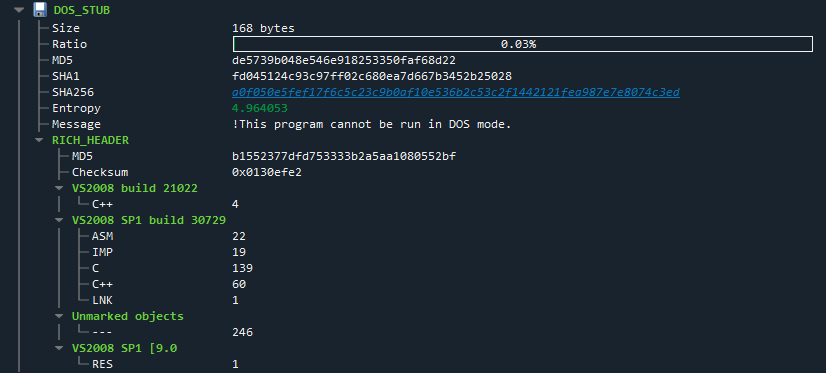
- Rich headers
- NT/File/Optional headers
- Data directories
- Sections
- Imports
- Exports
- Debug information
- Load config
- TLS
- Resources
- Version information
- Certificates
- Overlay
Figure 3. Overview of rich headers
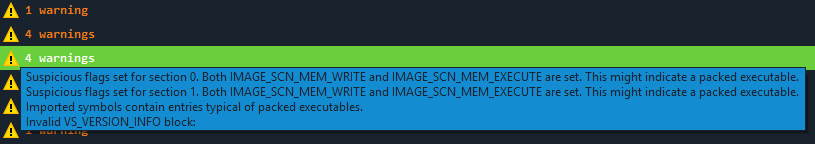
Hint! – If pefile detects any issues during parsing then hover over the warning icon for more details:
Figure 4. pefile warnings
Any highlighted links can be clicked to perform a search in VirusTotal, including:
- File hashes
- PDB path
- Timestamps
- Section hash/name
- Import hash/name
- Export name
- Resource hash
- Certificate serial
Hint! - The IMAGE_DIRECTORY_ENTRY_DEBUG and IMAGE_EXPORT_DESCRIPTOR timestamps are often set by the compiler but not “timestomped” by malware authors, which can prove useful for further pivot searches.
In addition, certain portions of the PE file can be saved or exported to CyberChef for further processing, such as:
- DOS stub
- Sections
- Resources
- Certificates
- Overlay
Figure 5. Save or export certificate
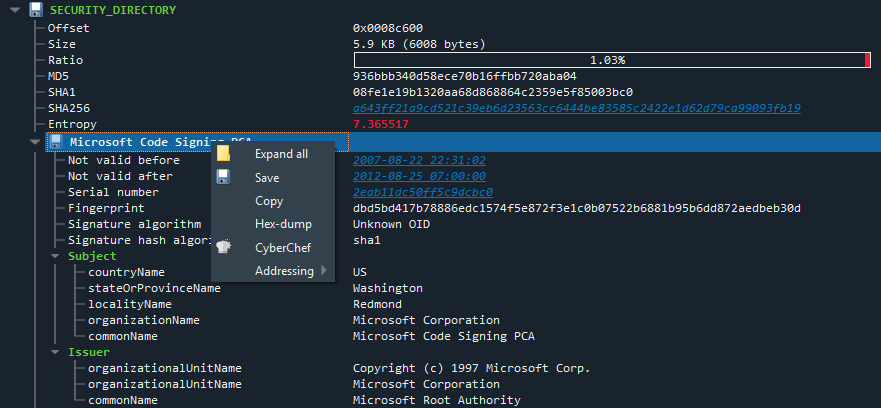
The left-hand “rainbow view” offers a high-level overview of the PE file’s structure, as well as conveying the offset/size/ratio of each region. For example, here is a PE containing several resources and a large overlay appended to the file:
Figure 6. Rainbow map
Each region can be clicked to jump to in the tree-view, or right-clicked to save to file or export to CyberChef.
Hint! - The rainbow map can also be a useful visual aid when processing a directory of PE files, as it makes it easy to spot similar file compositions and determine possible relationships between samples.
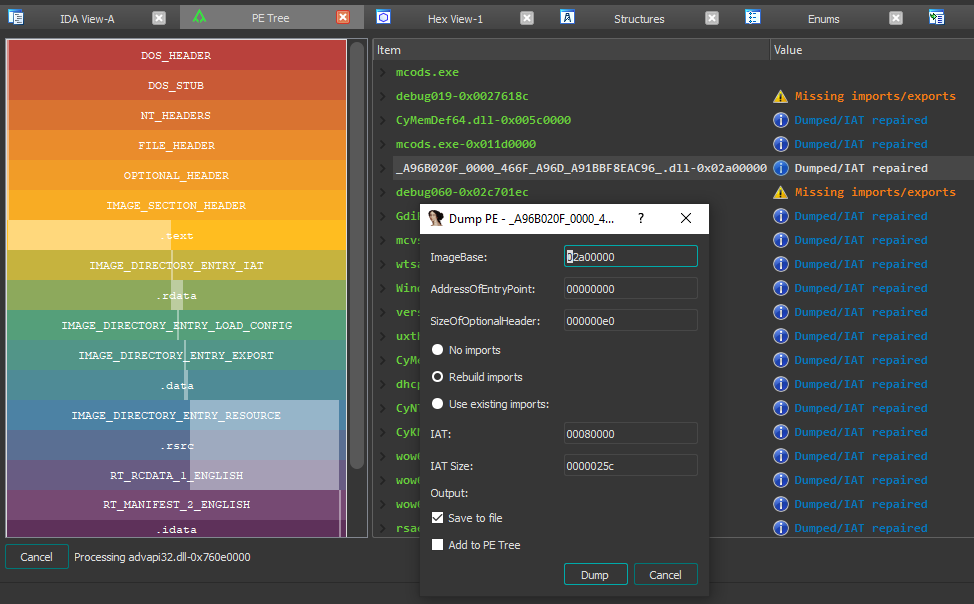
IDAPython
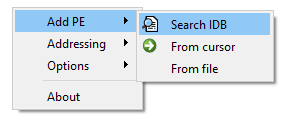
HeyRays’ IDA Pro integration is via an IDAPython plugin, and allows for more advanced functionality, such as the ability to find and dump PE files from an IDA database (IDB) and reconstruct imports:
Figure 7. Search IDA database for PE files
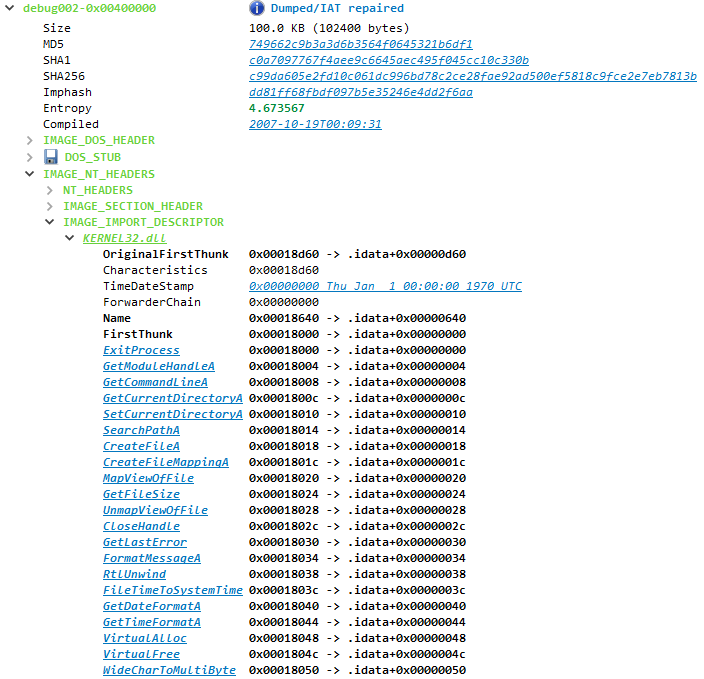
When dumping in-memory PE files, PE Tree will add basic comments on file structures to the IDB, as well as rename offsets to IAT functions, making it easier to explore and analyse injected/unpacked PEs from within a single IDB.
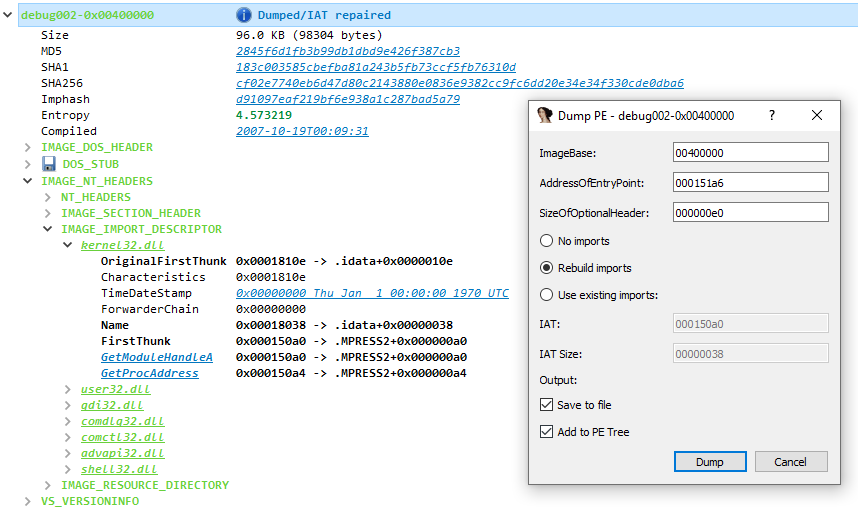
Hint! – PE Tree can also be used to dump PE files and reconstruct imports in a similar manner to OllyDumpEx/ImpRec. For example, unpacking MPRESS:
Figure 8. After performing “Search IDB” the above MPRESS packed PE file was found with an existing IAT (albeit not complete)
Figure 9. After dumping, the unpacked PE file contains a new (and complete) import address table
If “Rebuild imports” is selected, then PE Tree will search the IDA disassembly for all possible IAT references and construct a new IAT, IDT and hint name table (recommended for unpacked or dynamically loaded PEs). Otherwise, if “Use existing imports” is specified, then PE Tree will attempt to reconstruct imports based on the IAT specified via DIRECTORY_ENTRY_IMPORT (this is the default mode and typically recommended for most PEs and system DLLs).
Looking to the Future
PE Tree remains under active development, so expect to see new features frequently. The next major release will focus on rekall support, offering the ability to view and dump processes from either a memory dump or live system:
Figure 10. The future… Dumping active processes using Rekall!
To learn more and to access the PE Tree source code, please visit the BlackBerry GitHub account.
About Tom Bonner
Distinguished Threat Researcher, BlackBerry
Tom Bonner has over 18 years' experience in the cybersecurity/anti-malware industry, focusing on reverse engineering, developing detection technologies, threat intelligence, incident response and digital forensics.