BlackBerry Protect vs. WastedLocker Ransomware
WastedLocker is an enterprise-targeting ransomware variant that has been attributed to the malware crime gang commonly known as ‘Evil Corp Gang’, currently one of the biggest ransomware operators on the Internet.
Also known as the Dridex gang, Evil Corp Gang was founded in 2007 when threat actors who had previously worked on the infamous ZeuS banking Trojan went solo in order to distribute their own malware. The gang is also thought to be responsible for spreading the Locky ransomware that targeted home consumers in 2016.
The attacks carried out by the threat actors appear to be targeted towards specific organizations. Security researchers say that so far, the ransomware has only been deployed against U.S. companies. The most notable attack to date has reportedly been navigation/ smartwatch maker Garmin, who suffered a worldwide outage for several days in July 2020, leaving customers unable to access their connected devices.
Unpacking WastedLocker Ransomware
The BlackBerry Threat Research team obtained a sample of WastedLocker ransomware for testing. Here is a summary of what we learned.
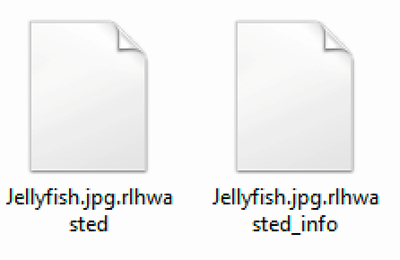
WastedLocker encrypts files with an AES 256-bit CBC mode encryption key that is protected by asymmetrically encrypting it using 4096-bit RSA. Once the encryption of the victim’s files has been carried out, the encrypted file gets appended a ‘.wasted’ file extension.
The attacker also creates an additional file that contains the ransom note. The ransom note has the same name as the encrypted file but with the addition of “_info”:
Figure 1: File encrypted with '.wasted' extension and accompanying'.wasted_info' file containing ransom note
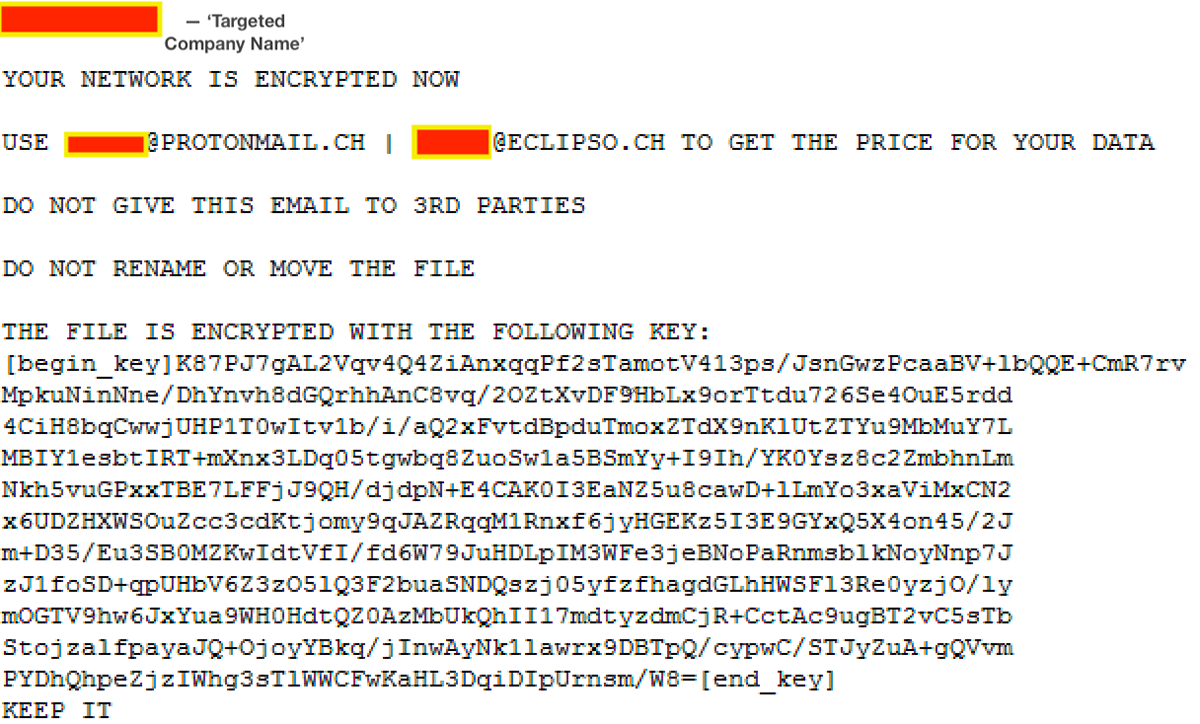
The following screenshot shows the ransom note, which follows the same layout. It starts with the name of the organization that is being targeted, informs them that their network has been encrypted, and then provides a contact email where the victim can retrieve information about the cost of returning their data and also the encryption key of the file:
Figure 2: Ransom note with the targeted company name and contact email blanked out
Remediation
An emerging trend among newer variants of ransomware is that they are increasingly designed to avoid detection by security tools and antivirus (AV) software. This allows the ransomware to persist long enough to encrypt the victim’s files.
According to security researchers, WastedLocker appears to have adopted an evasion technique highly similar to BitPaymer, a related ransomware strain. This technique adds an extra layer of obfuscation by doing its malicious deeds in memory, where it’s harder for behaviour-based detection rules to catch it.
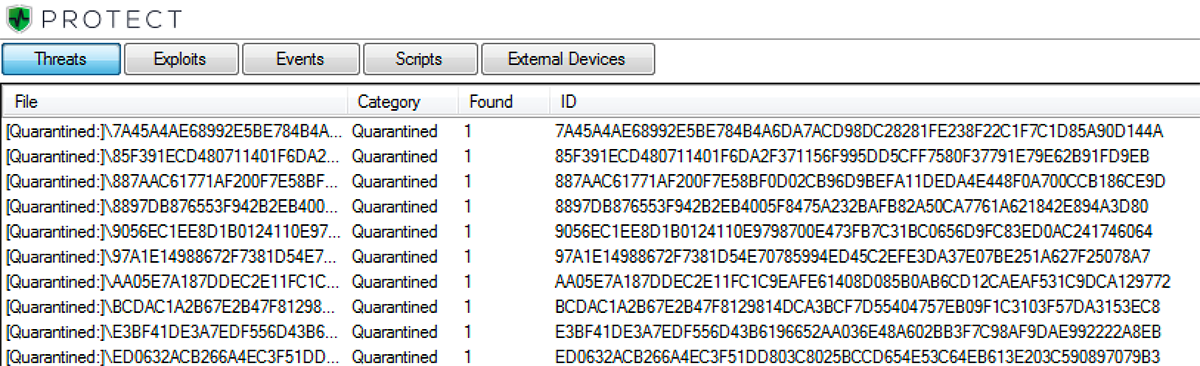
Figure 3: BlackBerry Protect console displaying all tested files that were quarantined
In terms of file scoring, the files were all scored negatively by BlackBerry® Protect's machine learning models.
BlackBerry uses artificial intelligence-based agents trained for threat detection on millions of both safe and unsafe files. Our automated security agents block WastedLocker based on countless file attributes and malicious behaviors instead of relying on a specific file signature.
When it comes to protection, early action is far cheaper than remediation. Companies should review their existing security setups frequently and backup vital data regularly.
Learn more about BlackBerry Protect.