The Pitfalls of Conducting a Business Transaction With a Malicious Actor
This may seem like a strange title for an article, but ransomware has been big business over the past couple of years and shows no sign of stopping in 2020. This article will not debate the merits of not paying ransoms, in cases such as Atlanta and Baltimore, or purportedly paying as in the recent case of Garmin, since that is a personal/business decision. The fact is that company after company and city after city continue to find themselves in the unenviable position of losing access to important data, or, in extreme cases, entirely unable to operate due to maliciously encrypted servers and workstations.
When faced with the dilemma of paying a hefty ransom versus the extended downtime required to restore operations from scratch, many organizations decide that paying the ransom is the ‘least-bad’ option. Presented with a firehose of cash from organizations around the world, ransomware actors have developed a professional business model that makes transactions nearly as fluid as charging a credit card.
File a Ticket Please…
Dealing with a modern ransomware actor often feels very similar to opening a support ticket with any technology vendor or helpdesk. One typically visits a support portal and provides the required identifier to allow the actor to identify your specific infection (out of the many they operate simultaneously).
Members of some ransomware groups assign themselves the sort of job title one would expect to encounter in any customer service organization. For example, you might be surprised to find yourself corresponding with the ransomware actors ‘Sales Director’ (never mind that the product for sale is access to your own systems). A pleasant demeanor is adopted, and the intrusion may even be framed simply as an unexpected and involuntary proactive security assessment for which the bill is now due.
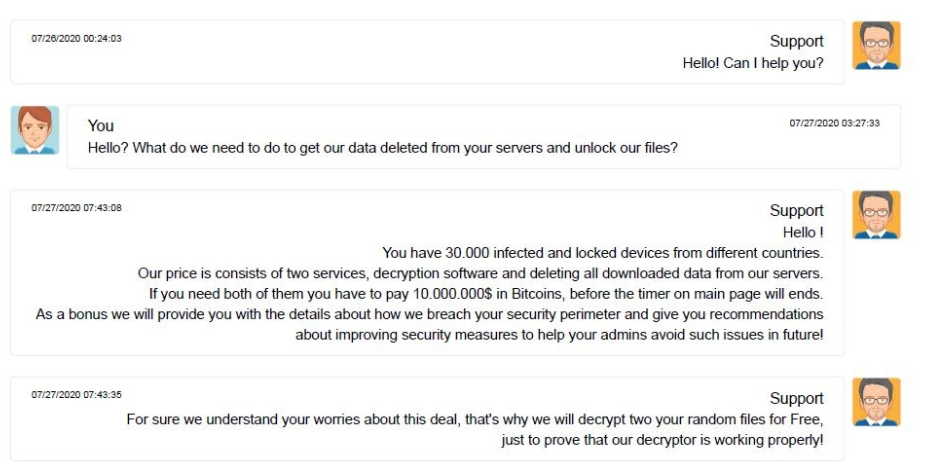
A recent Reuters article detailed a surreal chat session between the ransomware actor's customer support staff and a victim. The threat actor in that case was kind enough to provide details regarding how the intrusion was accomplished, and even provided recommendations for the organization to improve and prevent such breaches in the future. The entire exchange hardly feels like negotiating the terms of your own extortion with a criminal enterprise.
This begs the question, why not simply pay the ransom, implement the recommended changes, and resume normal business operation?