How Cuba Ransomware Works
Update 5.25.2023 with new details reported below.
Introduction
The Cuba ransomware variant first appeared in mid-2020 and made headlines due to its attack on the company known as American Funds Transfer Services (AFTS)
Since that time BlackBerry threat researchers have learned much more about this group, as TechCrunch reported in May 2023:
"According to security researchers at BlackBerry, the cybercrime group known as Cuba Ransomware, which was previously linked to a malware strain known as RomCom RAT, is not a cybercrime group at all. It’s actually a group working for the Russian government targeting Ukrainian military units and local governments, the researchers said.
“It’s a misleading attribution,” said Dmitry Bestuzhev, senior director of BlackBerry’s cyberthreat Intelligence team, referring to the links between RomCom RAT and Cuba. “It looks like it’s just another unit working for the Russian government,” he said.
Now let's look at how Cuba ransomware operates.
Cuba is often dropped via first-stage Hancitor loader malware, which gains access through phishing attacks, exposed vulnerabilities, or stolen or brute-forced RDP credentials. To lock targets out of their files, Cuba uses the symmetric encryption algorithm ChaCha20 and then appends and encrypts the decryption key using an RSA public key for which they hold the matching private key.
Upon execution, Cuba enumerates the victim host and stops various SQL and Microsoft® Exchange related services as well as processes.
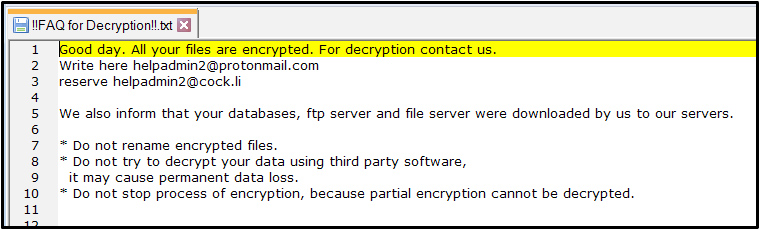
It then begins its encryption routine on targeted file types, appends a ‘.cuba’ extension to each affected file, and drops a ransom note titled ‘!!FAQ for Decryption!!.txt’ upon completion of encryption.
The ransom note contains instructions on how to contact the attacker via an email address, and also mentions that all of the victim’s databases, FTP servers and file servers have been uploaded to the attacker’s servers.
Operating System
Table 1: Impacted Operating System
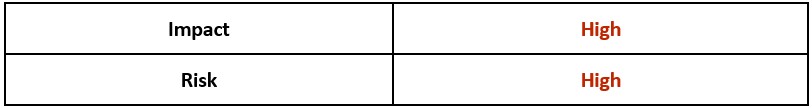
Impact
The following describes the level of impact along with the likelihood of risk this threat currently presents:
Table 2: Threat Impact
Technical Analysis
Cuba ransomware is C++ compiled, Win32 executable. The sample analyzed by the BlackBerry Threat Research team for the technical analysis in this document did not contain any form of packing or obfuscation.
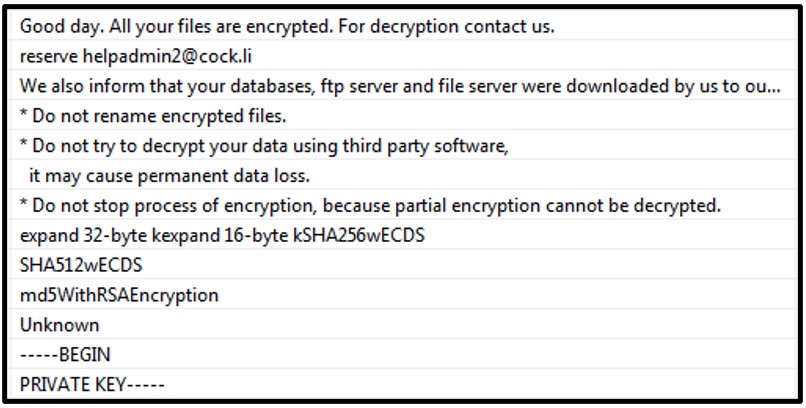
A static examination of the file reveals clues as to a lot of its functionality, such as what appears to be a ransom note and references to the RSA encryption algorithm:
Figure 1: Interesting Strings
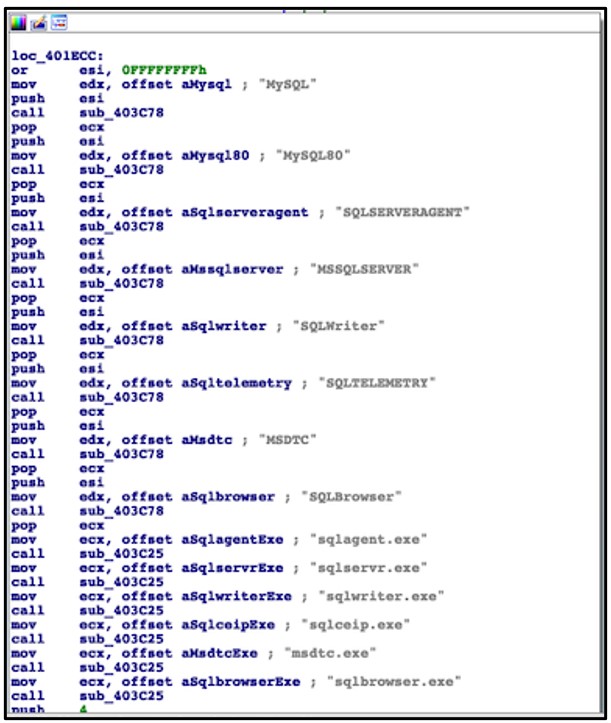
Upon execution, Cuba proceeds to enumerate the victim host and search for a hardcoded list of processes and services related to SQL and Microsoft Exchange, which it aims to terminate should any be found running on the host:
Figure 2: List of Terminated Services and Processes
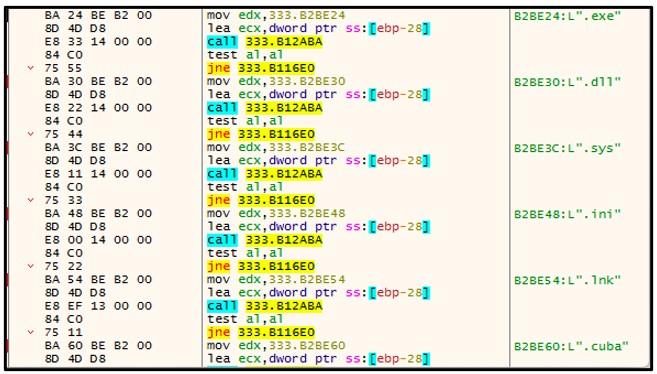
It then continues its execution and proceeds to enumerate all directories/files on the victim host, where each file parsed is compared to a hardcoded whitelist of file types it does NOT encrypt; should a file conform to one on the whitelist it is left alone, and enumeration continues to the next file within the directory with the check being performed again:
Figure 3: Whitelisted Extensions
Should a file not conform to a filetype that is on the whitelist, the malware begins its encryption routine, with the affected file being appended with a ‘.cuba’ file extension:
Figure 4: Encrypted Files
In addition, a ransom note titled ‘!!FAQ for Decryption!!.txt’ is dropped to each directory informing the victim that all of their databases, FTP servers and file servers have been downloaded by the attacker and giving instructions on how to contact the attacker via an email – ‘helpadmin2[at]protonmail[dot]com’ or ‘helpadmin2[at]c*ck[dot]li’:
Figure 5: Cuba Ransom Note
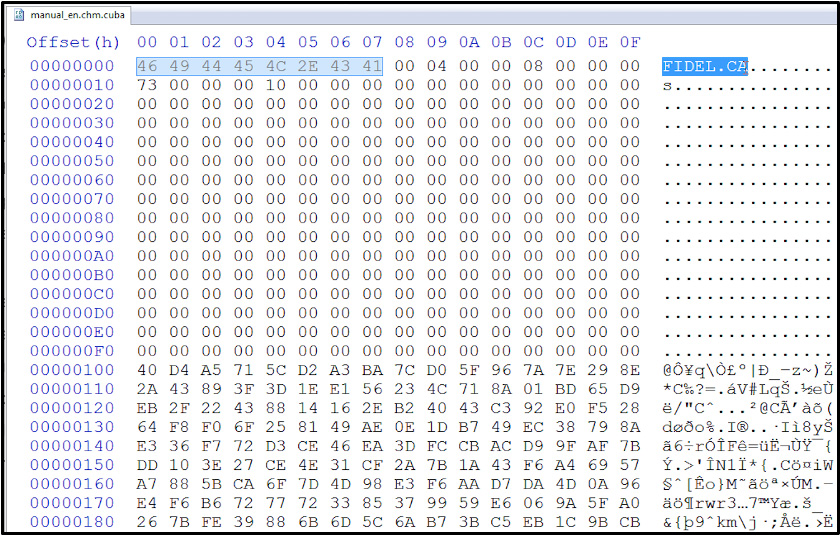
Upon further examination of an encrypted file, it can be seen to contain the string ‘FIDEL.CA’ embedded within its header and likely refers to Fidel Castro, which is another reference to Cuba.
Figure 6: FIDEL.CA Header
Yara Rule
The following Yara rule was authored by the BlackBerry Threat Research Team to catch the threat described in this document:
import "pe"
rule Mal_W32_Ransom_Cuba
{
meta:
description = "Cuba Ransomware"
author = "Blackberry Threat Research"
date = "2021-04-12"
strings:
//Good day. All your files are encrypted. For decryption contact us.
$x0 = {476f6f64206461792e20416c6c20796f75722066696c65732061726520656e637279707465642e20466f722064656372797074696f6e20636f6e746163742075732e}
//We also inform that your databases, ftp server and file server were downloaded by us to our servers.
$x1 = {576520616c736f20696e666f726d207468617420796f7572206461746162617365732c206674702073657276657220616e642066696c6520736572766572207765726520646f
776e6c6f6164656420627920757320746f206f757220736572766572732e}
//FIDEL.CA
$x2 = {464944454c2e4341}
//!!FAQ for Decryption!!.txt
$x3 = {21002100460041005100200066006f0072002000440065006300720079007000740069006f006e00210021002e00740078007400}
//MySQL80
$x4 = {4d007900530051004c0038003000}
//MSSQLSERVER
$x5 = {4d005300530051004c00530045005200560045005200}
//SQLWriter
$x6 = {530051004c00570072006900740065007200}
//SQLBrowser
$x7 = {530051004c00420072006f007700730065007200}
//sqlservr.exe
$x8 = {730071006c00730065007200760072002e00650078006500}
condition:
uint16(0) == 0x5A4D and
filesize < 3MB and
pe.imports("mpr.dll", "WnetEnumResourceW") and
pe.imports("mpr.dll", "WNetCloseEnum") and
pe.imports("mpr.dll", "WNetOpenEnumW") and
pe.imports("netapi32.dll", "NetShareEnum") and
8 of ($x*)
}
Indicators of Compromise (IoCs)
Files Created:
- !!FAQ for Decryption!!.txt ← Ransom-Note
- <filename>.cuba ← Appended File Extension
Attacker Emails:
- helpadmin2[at]protonmail[dot]com
- helpadmin2[at]cock[dot]li
Exempted File Types:
- .exe
- .dll
- .sys
- .ini
- .cuba
Exempted Folders:
- C:\Windows\
- C:\Program Files\Microsoft Office\
- C:\Program Files (x86)\Microsoft Office\
- C:\$Recycle.Bin\
- C:\Boot\
- C:\Recovery\
- C:\System Volume Information\
- C:\MSOCache\
- C:\Users\Default Users\
- C:\Users\Default\
- C:\INetCache\
- C:\Google\
- C:\Temp
Terminated Processes and Services:
Services:
MSExchangeUMCR
|
MSExchangePOP3BE
|
MSExchangeUM
|
MSExchangePop3
|
MSExchangeTransportLogSearch
|
MSExchangeNotificationsBroker
|
MSExchangeTransport
|
MSExchangeMailboxReplication
|
MSExchangeThrottling
|
MSExchangeMailboxAssistants
|
MSExchangeSubmission
|
MSExchangeIS
|
MSExchangeServiceHost
|
MSExchangeIMAP4BE
|
MSExchangeRPC
|
MSExchangeImap4
|
MSExchangeRepl
|
MSExchangeHMRecovery
|
MSExchangeDiagnostics
|
MSExchangeHM
|
MSExchangeDelivery
|
MSExchangeFrontEndTransport
|
MSExchangeDagMgmt
|
MSExchangeFastSearch
|
MSExchangeCompliance
|
MSExchangeEdgeSync
|
MSExchangeAntispamUpdate
|
MySQL80
|
SQLSERVERAGENT
|
SQLWriter
|
MSSQLSERVER
|
SQLTELEMETRY
|
SQLBrowser
|
vmcompute
|
vmms
|
|
Processes:
sqlagent.exe
|
sqlbrowser.exe
|
sqlservr.exe
|
outlook.exe
|
sqlwriter.exe
|
vmwp.exe
|
sqlceip.exe
|
vmsp.exe
|
msdtc.exe
|
|
BlackBerry Assistance
If you're battling this or a similar threat, you've come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you by providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment