Threat Thursday: BlackBerry Protect vs. Phoenix Cryptolocker
Introduction
The Phoenix Cryptolocker ransomware variant first appeared in early 2021 and made the headlines due to its involvement in an attack on the American insurance provider CNA Financial.
Utilizing an as-of-yet unknown infection vector, the malware comes signed with a digital certificate in an attempt to appear to be a legitimate utility.
Upon execution, Phoenix Cryptolocker creates a copy of itself under a different name to a location on the host, then detonates this copy and proceeds to enumerate the victim host, searching for targeted file extensions which it then encrypts, appending a ".phoenix" extension to each affected file while at the same time dropping a ransom note to each affected directory.
The ransom note contains instructions on how to contact the attacker via a web address link and/or email address.
Once encryption is completed, the malware proceeds to delete all traces of itself such as the binaries and created folder, leaving the user with just their encrypted files and instructions on how to pay to have them decrypted should they wish.
Impact
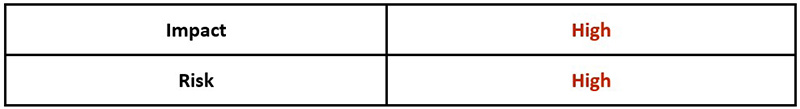
The following describes the level of impact along with the likelihood of risk this threat currently presents:
Table 1: Threat Impact
Technical Analysis
Phoenix Cryptolocker comes with several built-in mechanisms designed to help it appear to be a legitimate utility and trick an unwitting user into executing it. The first being that it uses the 7-Zip icon in an attempt to masquerade as a 7-Zip file:
Figure 1: Phoenix Cryptolocker Icon
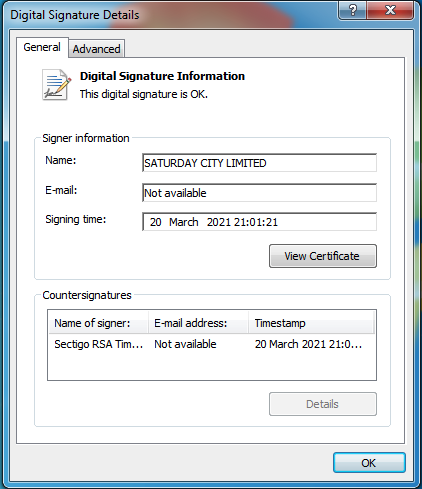
The second is that it is signed with a digital certificate, issued to a company called “SATURDAY CITY LIMITED”, with a signing date of March 20th 2021:
Figure 2: Phoenix Cryptolocker Digital Cert
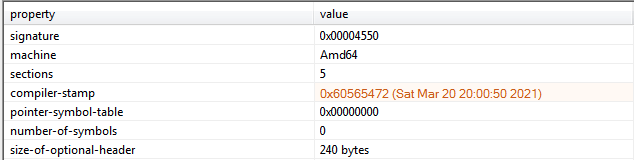
An examination of the file’s compilation timestamp shows the same date of March 20th of this year:
Figure 3: Compiler Timestamp
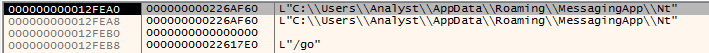
Upon execution, Phoenix Cryptolocker first proceeds to create a new directory in the "C:/%Username%/AppData/Roaming/<installation_folder>" location, where it installs a copy of itself under a random name and without appending a typical Windows executable extension such as “.exe”.
This file also correlates to the same SHA256 as the initial binary.
The naming convention of both the created installation folder and the copied binary typically follow a legitimate-sounding and nondescript format, such as in the example below, where the created folder was named “MessagingApp” with the copied binary titled “Nt”.
This is likely an attempt to remain inconspicuous to a potentially suspicious user or security software:
Figure 4: Copied Binary
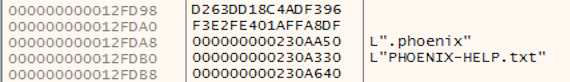
The copied binary is then executed with a “/go” switch:
Figure 5: Copied Binary Execution
Figure 6: Execution Path
Where it can be seen running as a sub-process of the initial binary:
Figure 7: Phoenix Cryptolocker Process Tree
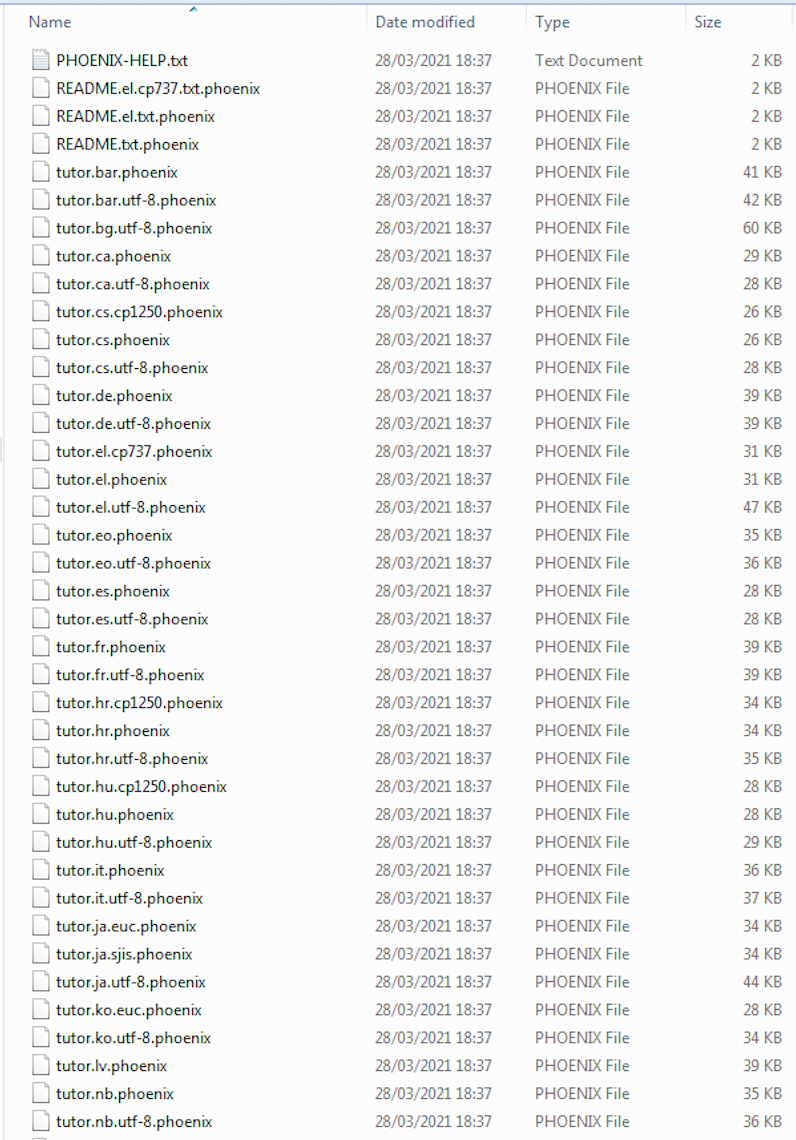
It then continues its execution and proceeds to enumerate all directories/files on the victim host and begin its encryption routine, with each affected file being appended with a ".phoenix" file extension:
Figure 8: Phoenix File Extension
Figure 9: Encrypted Files
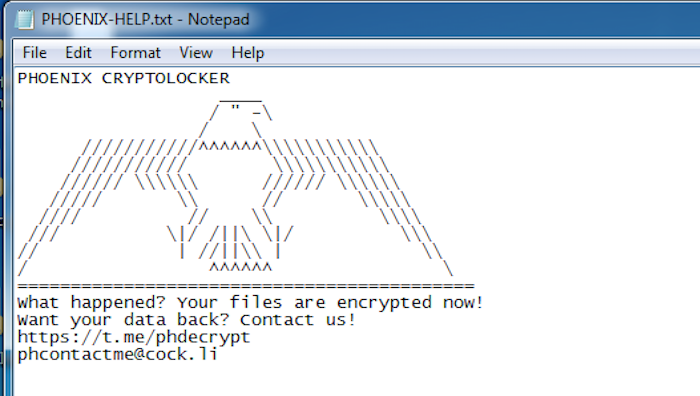
In tandem with the file encryption, a ransom note titled "PHOENIX-HELP" is also dropped to each directory with its contents containing the malware name, an image of a phoenix, and instructions on how to contact the attacker via an email – “phcontactme[at]c*ck[dot]li” or web link – “hxxps://t[dot]me/phdecrypt”:
Figure 10: PHOENIX-HELP Ransom Note
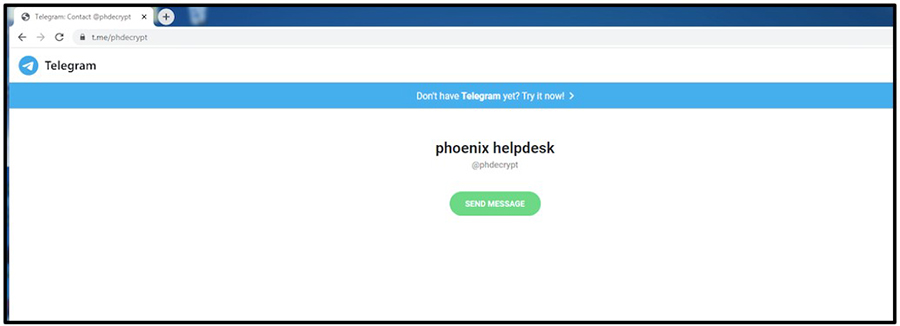
Should a user navigate to the URL provided within the ransom note, it takes them to a page titled “phoenix helpdesk” which prompts the user to download the messaging app “Telegram” in order to make contact with the attacker:
Figure 11: Phoenix Helpdesk
Upon completion of its encryption routine, the malware then proceeds to invoke the built in Windows® binaries “waitfor.exe” and “attrib.exe” via “cmd.exe” to remove both the original binary and the created folder, along with the copied binary - thereby removing all evidence of itself and leaving the victim with just their encrypted files and the dropped ransom note:
Figure 12: Phoenix Post-Encryption Cleanup
Targeted File Extensions
The below is a partial list of file-types targeted by this ransomware:
.html
|
.zip
|
.chm
|
.inc
|
.diz
|
.c
|
.ss
|
.rar
|
.xml
|
.pdb
|
.dd64
|
.h
|
.qm
|
.lib
|
.a
|
.asm
|
.txt
|
.doc
|
.pl
|
.1
|
.vim
|
.sample
|
.GPLV2
|
.GPLV3
|
.RUNTIME
|
.pm
|
.bash
|
.ico
|
.tcsh
|
.zsh
|
.png
|
.sh
|
.cgi
|
.css
|
.js
|
.ioc
|
.its
|
.def
|
.rst
|
.cmderver
|
.map
|
.reg
|
.lua
|
.fml
|
.conf
|
.bmp
|
.farconfig
|
.pyd
|
.lng
|
.properties
|
.api
|
.au3
|
.spc
|
.cspec
|
.pspec
|
.sla
|
.spaspec
|
.exports
|
.pdf
|
.global
|
.fs
|
.fsc
|
.xpm
|
.csc
|
.xbm
|
.tab
|
.gz
|
.mo
|
.docbook
|
.svgz
|
.theme
|
.tmac
|
.mount
|
.page
|
.gr
|
.db
|
.bz2
|
.README
|
.awk
|
.7z
|
.lic
|
Table 2: Targeted File Extensions
Exempted File Types
Exempted Folders
BlackBerry Model Assessment
The BlackBerry® model assessment shows the behavior of current and previous BlackBerry® Protect machine learning (ML) models when analyzing this sample:
Yara Rule
The following Yara rule was authored by the BlackBerry Threat Research Team to catch the threat described in this document:
import "pe"
import "math"
import "hash"
rule Mal_Ransom_Phoenix_Cryptolocker
{
meta:
description = "Phoenix Cryptolocker Ransomware"
created_from_sha256 = "008ec79765325200361d9c93ac35edd430f8b17894ff843268caa5acd6224549"
author = "Blackberry Threat Research"
strings:
$f0 = {48 8D 0D D0 2F 1D 00}
$f1 = {BA 03 00 00 00 B9 01 00 00 00 E8 1A 00 00 00 48 8B 0D 83 2D 1D 00 E8 C6 00 00 00}
$f2 = "SATURDAY CITY LIMITED1" ascii
$f3 = "SATURDAY CITY LIMITED0" ascii
$f4 = "CBviyMgTWm" wide
condition:
// Must be a 64-bit executable
pe.is_64bit() and
// Must be less than
filesize < 2000KB and
// Must have exact import hash
pe.imphash() == "5d2ddf9bb9051294e17ea7cb876c77e2" and
// Must have the below Rich sig hash
hash.md5(pe.rich_signature.clear_data) == "92a167f693b8a618f06e128e6399ad5c" and
// Must be signed with the below digital Certificate
for any i in (0 .. pe.number_of_signatures) : (
pe.signatures[i].issuer contains "Sectigo RSA Code Signing CA" and
pe.signatures[i].serial == "3b:00:73:14:84:4b:11:4c:61:bc:15:6a:06:09:a2:86"
) and
// Must have Strings
all of ($f*)
}
|
Indicators of Compromise (IoCs)
File System
Created
- PHOENIX-HELP ← Ransom-Note
- <filename>.phoenix ← Appended File Extension
- C:\Users\<Username>\AppData\Roaming\<A-Za-z>\<A-Za-z> ← Copy of Main Binary
Deleted
- All files post-encryption
- C:\Users\<Username>\AppData\Roaming\<A-Za-z>\<A-Za-z> ← Copy of Main Binary
Mutex
- \BaseNamedObjects\MachineRendezvous
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.