Summary
The DarkSide ransomware variant first appeared in mid-2020. It is distributed as a Ransomware as a Service (RaaS) that is used to conduct targeted attacks. DarkSide targets machines running both Windows® and Linux, and made headlines recently due to its attack on the U.S. fuel pipeline system, the Colonial Pipeline.
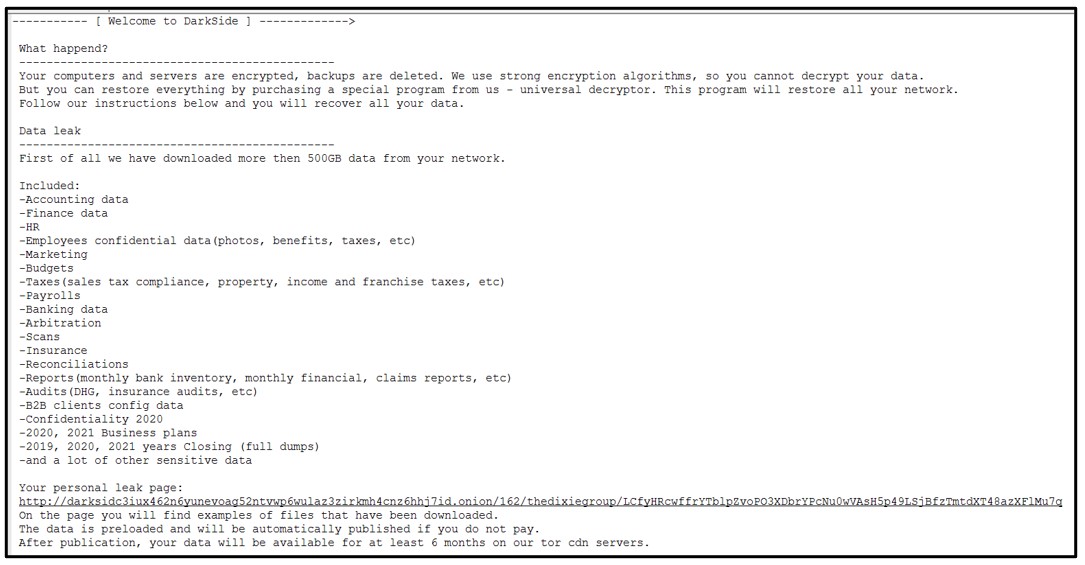
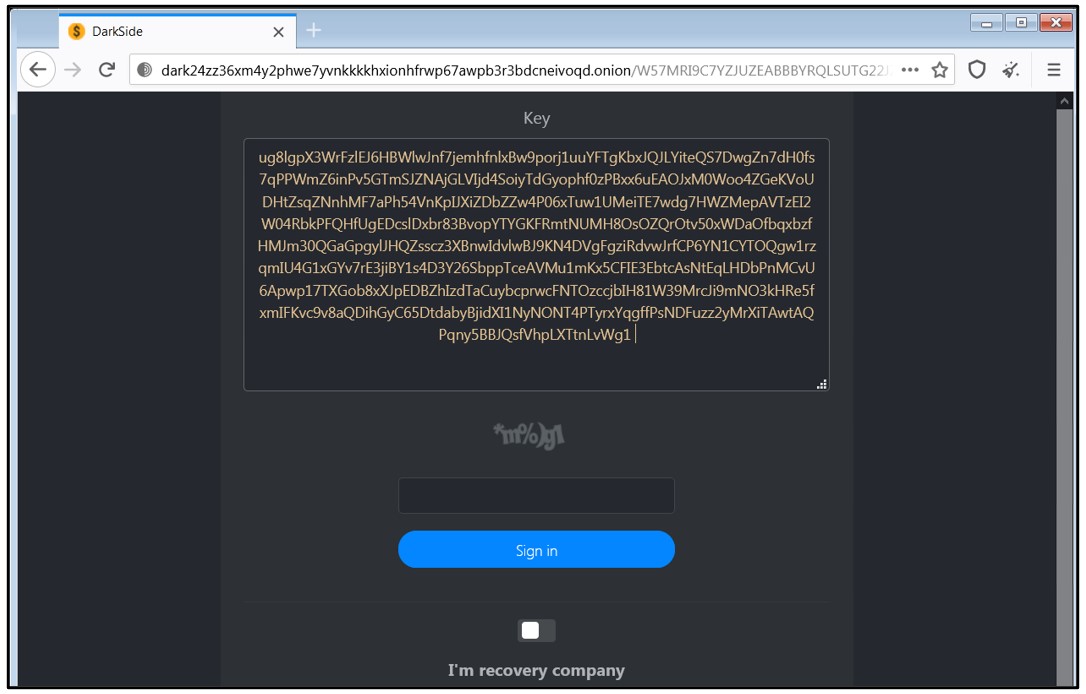
DarkSide uses a double extortion scheme where data is both encrypted locally and exfiltrated before the ransom demand is made. If the victim refuses to pay, their data is published to a site located on the dark web:
hxxp[:]//darksidc3iux462n6yunevoag52ntvwp6wulaz3zirkmh4cnz6hhj7id[dot]onion
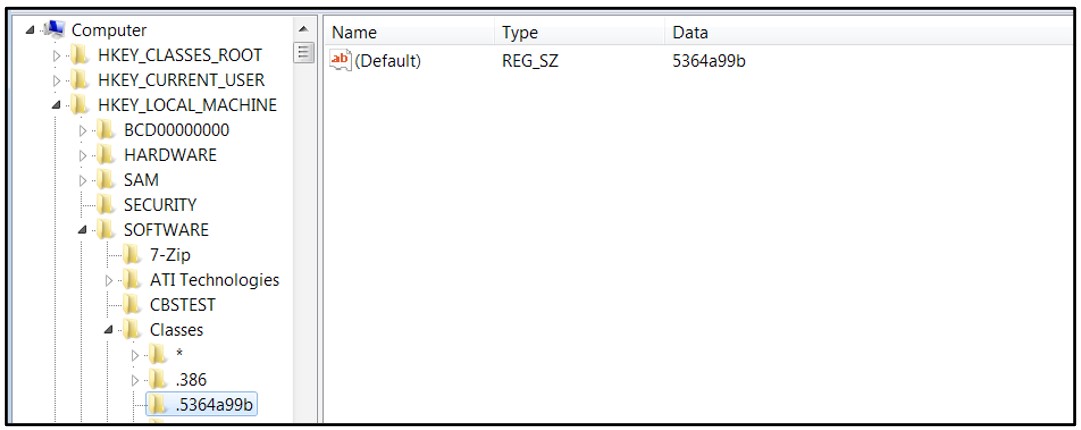
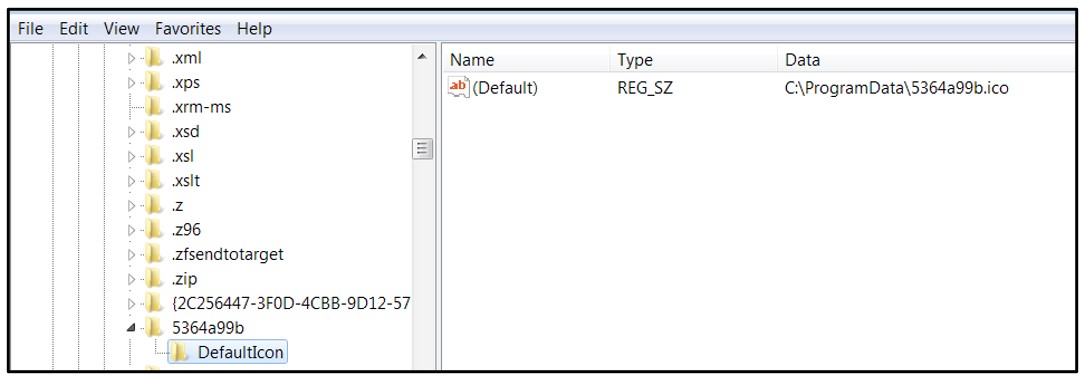
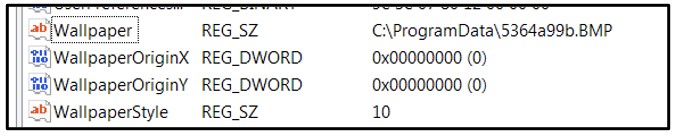
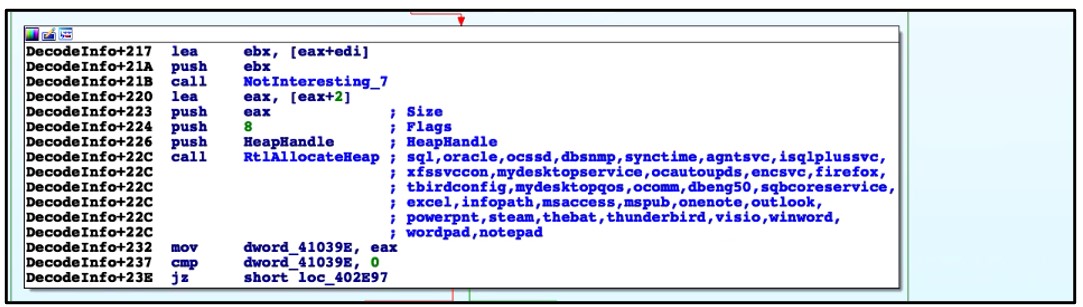
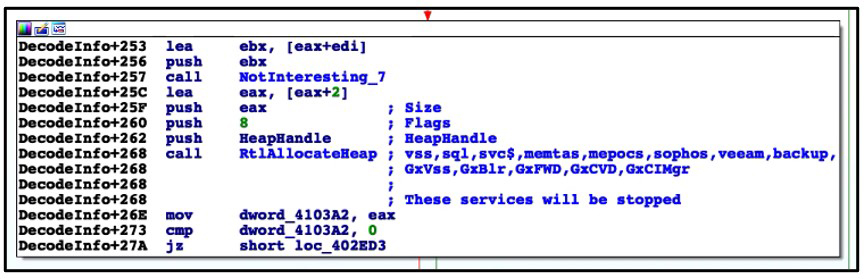
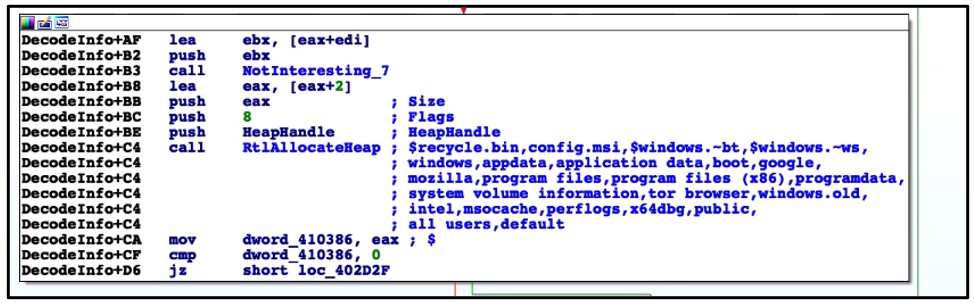
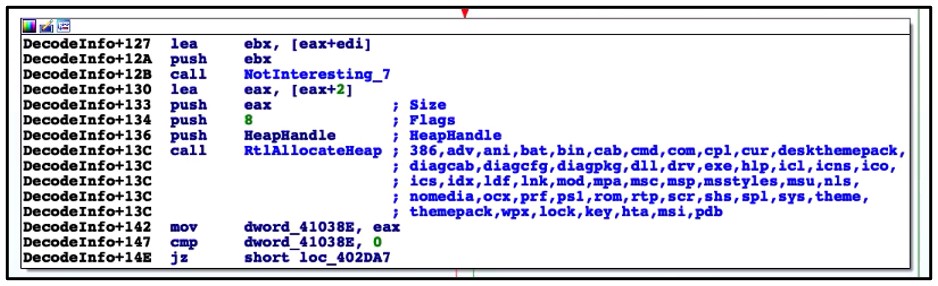
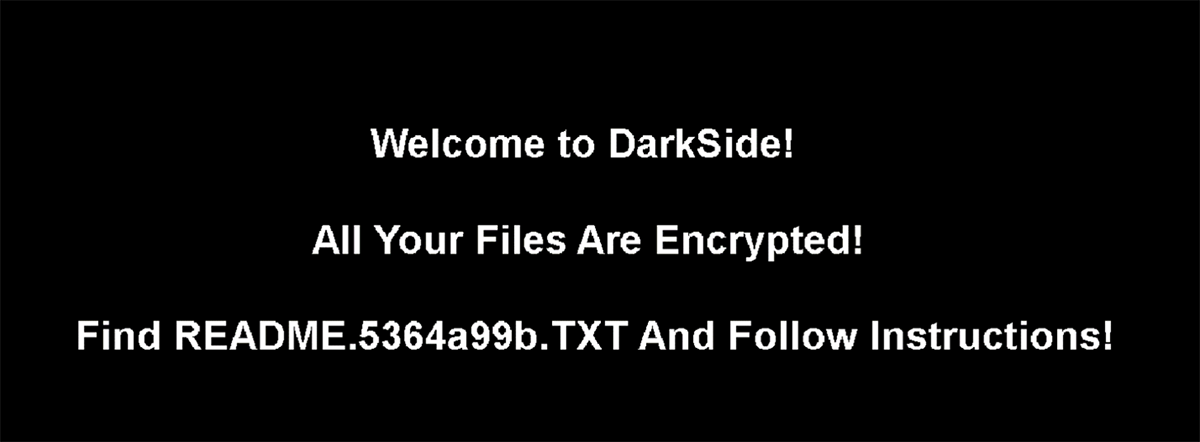
Upon execution, this ransomware deletes volume shadow copies and system backups to hamper recovery efforts. It then encrypts files, changes the file icons, and appends an extension to the affected files. Finally, it drops a README file to the affected directories and changes the desktop wallpaper, in a similar way to other ransomware families.
In the aftermath of the Colonial Pipeline attack, the DarkSide Group has stated publicly that it was not their intent to affect hospitals or medical facilities, education, not-for-profit, or Government systems.
It’s important to note that current indications point towards the DarkSide group shuttering operations, possibly with the hopes of restarting and rebranding once the bad publicity quietens down. While the threat of the current iteration of this ransomware may be winding down, it’s important to be aware of their tactics, techniques, and procedures (TTPs), as these may clue us in to the group’s future endeavors.