Threat Thursday: FluBot - Android Spam is Malware in Disguise
Summary
FluBot is an Android™ malware that disguises itself as a delivery notification. This threat has SMS spamming and information-stealing capabilities: once installed on an Android device it will go after victims’ banking credentials. Initially targeting victims in Spain and Germany, FluBot recently shifted its focus towards English-speaking countries like Ireland and the United Kingdom.
FluBot currently affects only Android-based devices, but it can inadvertently send spam SMS messages to owners of Apple devices. Regardless of what mobile operating system you’re using, it is always recommended to ignore spam messages and avoid clicking attached links sent from unknown senders.
Operating System
Risk and Impact
Technical Analysis
Infection Vector
The malware’s primary infection vector is spamming users with SMS messages. A victim will typically receive a message that will appear to be from either DHL or FedEx, relating to a package. This message will contain a link to get further details or to track a fake delivery.
The content of these SMS messages can vary slightly. Some messages even use the victim’s name to further personalize the message and appear legitimate. Clicking on the phishing link will result in the victim being redirected to a fake website that appears to be a valid service provided by the courier in question. Instead, it will be a malicious download page for the FluBot malware.
Unlike iOS applications, Android Application Packages (APK) can be hosted on a wide variety of sources and are not limited to the official APK distribution service via Google Play Store.
Depending on which Android system or settings a victim is using, they might initially be warned against downloading “unknown third-party applications”. However, this warning can be easily disregarded and manually overridden by the victim, to allow this untrusted application to be downloaded onto the user’s device.
Both Android and Apple iOS users can receive phishing SMS messages distributed as part of a FluBot campaign. Even though FluBot is only Android-based at the time of writing, it is never a good idea to click on an untrusted link regardless of mobile platform. It is also never advisable to supply untrusted websites any form of credentials or private information, or to allow them to download files onto your device.
If you receive one of these text messages relating to FluBot, report it to your mobile carrier and immediately delete the message.
Figure 1: Icon of fake 'DHL' application.
Example App Information: DHL
App Name:
|
DHL
|
Package Name:
|
com.android.AlipayGphone
|
Main Activity:
|
com.eg.android.AlipayGphone.MainActivity
|
Android Version Name:
|
1.5
|
Size:
|
3.38MB
|
SHA1:
|
020870ff50253429fb2aa56cd948c18329fe1ad3
|
Example Certificate Attributes: DHL
Figure 2: Icon of fake 'FedEx' application
Example App Information: FedEx
App Name:
|
FedEx
|
Package Name:
|
com.tencent.mobileqq
|
Main Activity:
|
com.example.myapplicationtest.MainActivity
|
Android Version Name:
|
1.0
|
Size:
|
5.91MB
|
SHA1:
|
eb41401c48e8c336348f50a1ec6d90e75ae60460
|
Example Certificate Attributes: FedEx
Shift towards English Speakers
In May 2021, we observed that the malware had begun a significant shift in focus away from European victims towards natively English-speaking countries like Ireland and the United Kingdom. This switch has also generated concern that it could soon attempt to shift its attacks to the United States and Canada.
This prompted NCSC (National Cyber Security Centre) in the UK, as well as mobile phone carriers, to publish warnings and alerts related to this shift in tactics by FluBot. And in June 2021, national news headlines and articles from both Irish and UK national broadcasters warned the public of trends in relation to FluBot scam messages.
Deployment
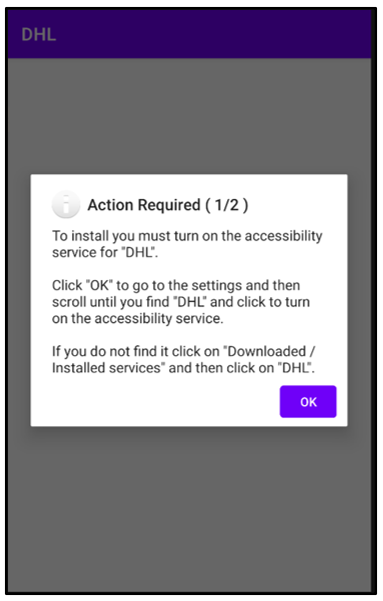
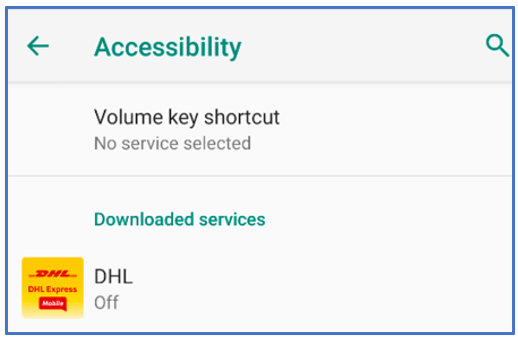
If a victim allows the malware to download, FluBot will launch, but it will require several further actions to be taken before it can achieve its core goals. When it is launched, the malware will inform the victim that there are further actions required to allow the service “DHL” or “FedEx” to operate on their Android device.
Waiving the following permissions will allow the malware to gain full access to the user’s device:
- Android Notifications.
- Accessibility Services.
- Download Services.
Figure 3: Initial Actions Required by 'DHL' (1/2)
Whether the malware masquerades as DHL or FedEx, it will operate identically from the victim’s perspective:
Figure 4: Giving the malware Accessibility permissions.
The malware initially requires the user to allow “Downloaded Services” to be enabled.
By giving the malware Accessibility access, the malware can also start as a background service, unnoticed by the victim:
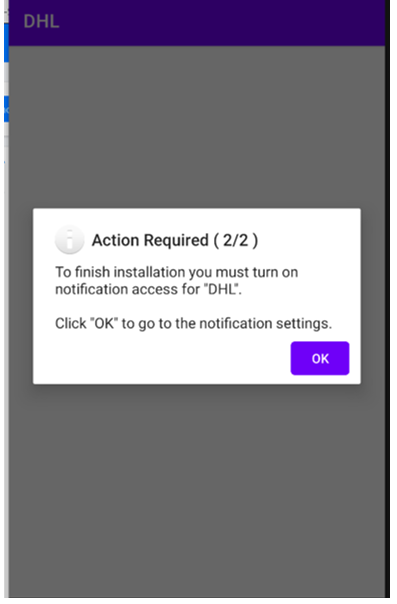
Figure 5: Action Required allowing Notification Access (2/2).
Next, the malware requires the victim to allow “Notification Access”.
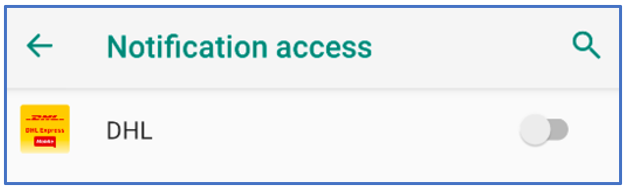
Notification Access grants this third-party malware the permissions to potentially read all notifications posted by the device and any other installed application:
Figure 6: Giving the malware Notification Access.
Domain Generation Algorithm
After successful installation and deployment, FluBot uses a Domain Generation Algorithm (DGA) to connect to its command-and-control (C2) infrastructure. A DGA is used to periodically generate a large number of domain names that can be used as points of connectivity to the malwares’ C2 infrastructure. Because taking down so many different domain names can be prohibitively difficult, this ploy is used by malware to make shutting down the FluBot’s malicious infrastructure more challenging.
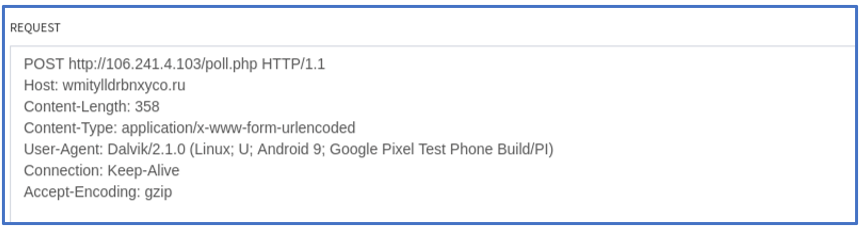
FluBot next sends a POST request to contact its C2. It will then wait for commands:
Figure 7: POST Request of data to C2.
C2 Commands
Once connected to its C2 infrastructure, the FluBot malware can receive multiple commands to carry out its malicious activities.
Functionality of core commands it can receive are related to:
- Blocking of notifications
- Redirection to a credit card phishing page
- Getting the device’s contact list
- Enabling SMS interception
- Uninstalling itself from a device
- Uploading the content of an SMS to the C2
Obfuscation
During analysis, samples of FluBot are obfuscated. They typically contain an internal file containing the malware’s internal Java class structure, which will be decrypted during runtime with the stream cipher RC4.
On locating the specific internal file and obtaining its decryption key, the file can be decrypted to its original .DEX format. These files can be random and do not follow a specific static naming convention.
This DEX file can be decompiled to a .JAVA file format and observed, confirming the class structure of the FluBot malware.
Some FluBot samples are further obfuscated with the use of APK Protector software to thwart analysis. The strings of observed samples are also obfuscated as a further anti-analysis and anti-detection techniques carried out by the malware:
Figure 8: Decrypted Class structure
Indicators of Compromise (IoCs)
At BlackBerry, we take a prevention-first and AI-driven approach to cybersecurity. Putting prevention first neutralizes malware before the exploitation stage of the kill-chain.
By stopping malware at this stage, BlackBerry solutions help organizations increase their resilience. It also helps reduce infrastructure complexity and streamline security management to ensure business, people, and endpoints are secure.
Operating System: APK
Network Commination:
Note: FluBot contains a Domain Generation Algorithm (DGA) to maintain C2 communication. Therefore, the networking varies greatly.
Request Type
|
URL
|
POST
|
hxxp://wenkgefmpgfumtk[.]com/poll[.]php
|
POST
|
hxxp://sahxadvcxwmiknn[.]ru/poll[.]php
|
POST
|
hxxp://aogedvhwqhuokpd[.]ru/poll[.]php
|
POST
|
……..
|
Domain Examples:
- elfeyiukixinahg[.]com
- luwardwlejahsbl[.]cn
- gbmsxoavsgkvkdh[.]ru
Android Permissions:
- android.permission.SEND_SMS
- android.permission.INTERNET
- android.permission.WRITE_SMS
- android.permission.CALL_PHONE
- android.permission.RECEIVE_SMS
- android.permission.READ_PHONE_STATE
- android.permission.READ_CONTACTS
- android.permission.READ_SMS
- android.permission.REQUEST_IGNORE_BATTERY_OPTIMIZATIONS
- android.permission.QUERY_ALL_PACKAGES
- android.permission.REQUEST_DELETE_PACKAGES
- android.permission.KILL_BACKGROUND_PROCESSES
- android.permission.ACCESS_NETWORK_STATE
- android.permission.WAKE_LOCK
- android.permission.FOREGROUND_SERVICE
|
BlackBerry Assistance
If you’re battling FluBot or a similar mobile threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.