Threat Thursday: CryptoMix Clop Ransomware
Summary
Clop is a ransomware variant of the CryptoMix family that is thought to have been developed in Russia. It targets victims in the United States, Canada, Latin America, Asia Pacific, and Europe. Last month, law enforcement authorities in a joint task force from Ukraine, South Korea, and the USA, arrested and charged six suspects believed to be members of the Clop threat actor gang.
This threat was the first ransomware to demand a payment of over $20 million when it infected Software AG, the second largest enterprise software firm in Germany, in October of 2020. Clop continues to be linked to a number of high-profile attacks, such as those on enterprise cloud file-sharing company Accellion and its clients, including investment banking company Morgan Stanley.
Even following the prominent arrests, this ransomware group continues to leak confidential information obtained from new victims. This means it’s likely that the individuals who were arrested were not key figures in the malware’s operations.
Operating System
Risk & Impact
Technical Analysis
Clop ransomware was first seen in the wild in 2019. Clop ransomware has been used in targeted attacks where the threat actors gain an initial foothold on a network by exploiting vulnerabilities, or by brute forcing desktop protocol.
Researchers have reported that Clop ransomware is a popular final payload for attacks conducted by FIN11. FIN11 is a financially-motivated Russian threat group responsible for a subset of the activity attributed to TA505. This group has been active since at least 2014, and is known for launching widespread, high-volume email phishing campaigns against targets in almost all sectors. Following an initial, indiscriminate phishing campaign, the FIN11 group will use the information gathered to evaluate which of their victims they wish to pursue.
In this blog, we’ll take a closer look at Clop ransomware. The malicious file reviewed as part of this report is a Win32 executable written in C++. The executable is packed and compressed to conceal its functionality.
Clop uses several methods to avoid detection and impede analysis. The malware includes anti-analysis and anti-virtual-machine (VM) techniques to ensure the file will not execute if it finds it is running in an emulated environment. The ransomware also attempts to disable Windows® Defender and uninstall Microsoft® Security Essentials.
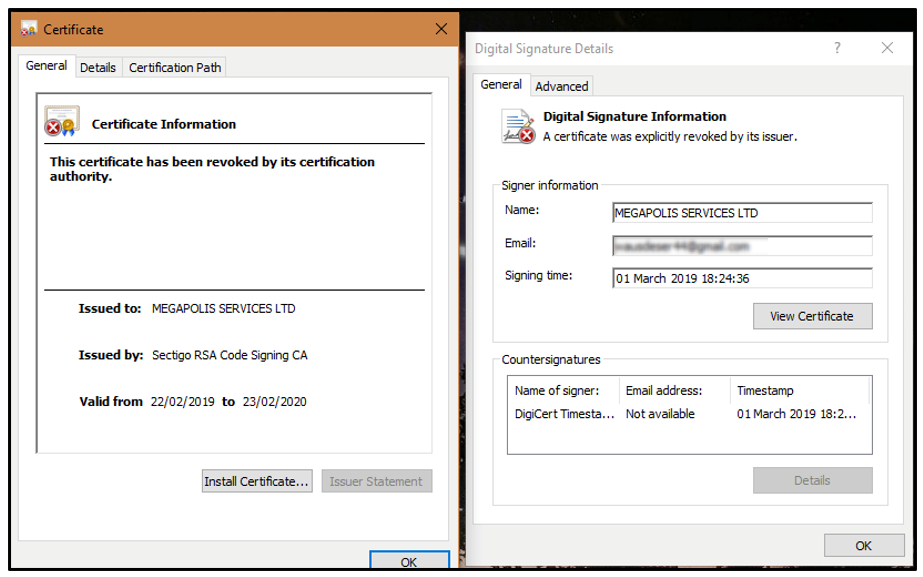
The binary is signed, giving the malicious file the appearance of legitimacy. But if you look closer, you’ll find that the signing certificate has been revoked, so it is no longer valid:
Figure 1 - Clop binary signed with revoked certificate.
Clop ransomware attempts to stop over 600 Windows® processes. By freeing up these processes, files running on them are no longer locked and can be encrypted by Clop. Security researcher Vitali Kremez provides a full list of the processes killed by Clop in his GitHub repository.
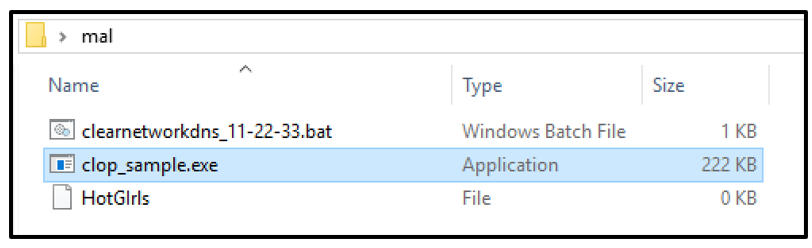
The malware creates an empty file named "HotGIrls" in the current directory where it is running. It also creates a batch script named "clearnetworkdns_11-22-33.bat", as seen in the image below:
Figure 2 - Files dropped to the current directory.
Before beginning the encryption process, this batch file deletes the volume shadow copies and then resizes the shadow copy storage. It also disables Windows repair features so the system cannot be easily restored, as seen in the image below:
Figure 3 - Contents of clearnetworkdns_11-22-33.bat.
The ransomware creates a mutex called "^_-HappyLife^_-" to ensure only one instance of the malware is running. Clop then searches the connected drives and the local file system, using the APIs FindFirstFile and FindNextFile, and begins its encryption routine. The threat includes a list of filenames and extensions to bypass during encryption.
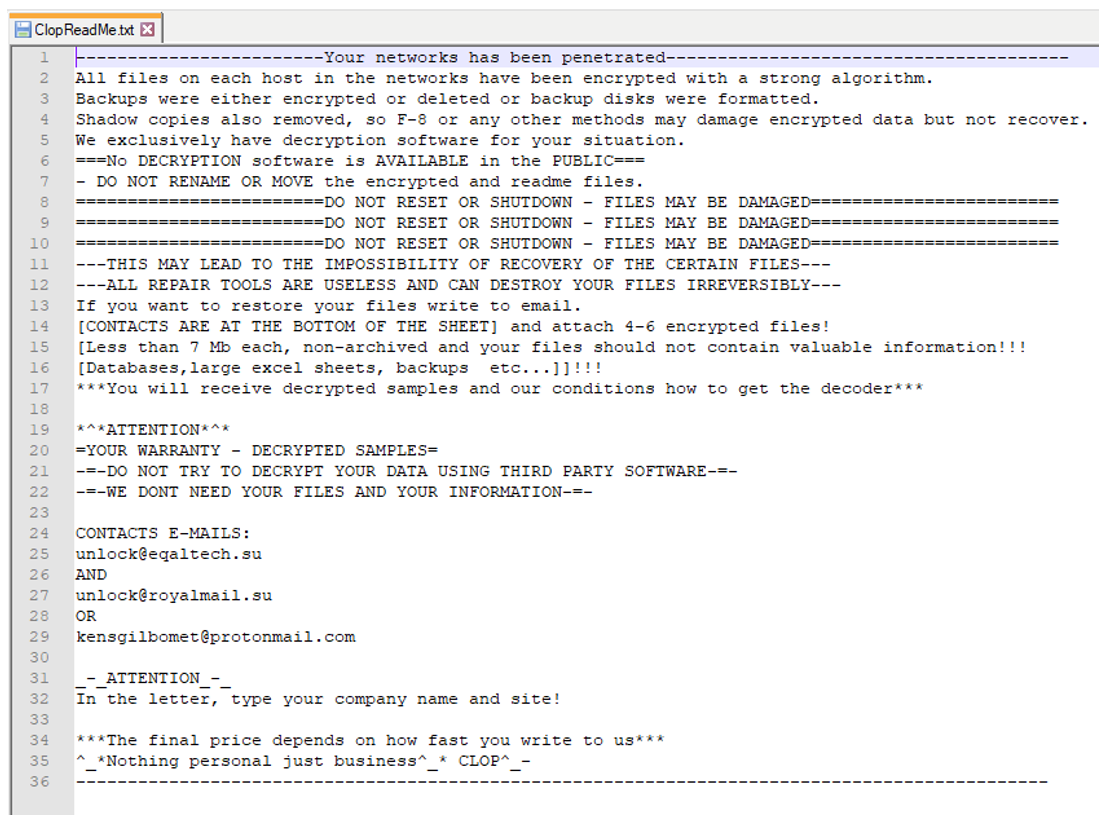
Next, Clop drops a ransom note in a text file named "CIopReadMe.txt". It also appends the file extension ".Clop" to the victim’s encrypted files, as seen below:
Figure 4 - Encrypted file and ransom note.
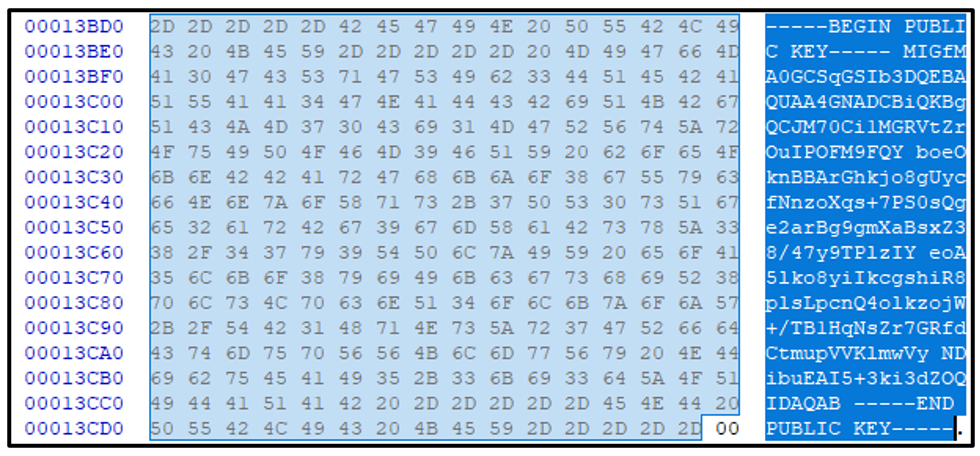
The Clop binary contains a hardcoded RSA public key, which is viewable in a hex editor in the unpacked image, as seen below:
Figure 5 - Hardcoded RSA public key.
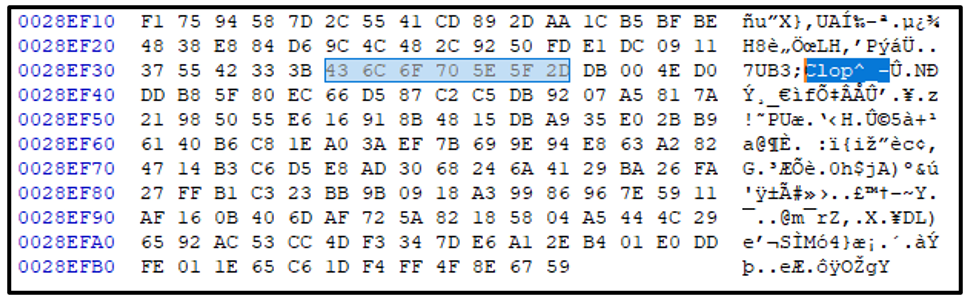
During the encryption routine, Clop generates a random AES key for encryption. It then adds a marker - "Clop^_-" to the end of the encrypted file. The key used is ciphered with the hardcoded master RSA key, and is added after this marker:
Figure 6 - Clop marker added to encrypted files.
In the ransom note seen below, the user is instructed to email the threat actors to obtain a price for the Clop decryptor tool. They are warned that "the final price depends on how fast you write to us". The ransom note signs off with " ^_*Nothing personal just business^_* CLOP^_- ".
Figure 7 - CIopReadMe.txt ransom note.
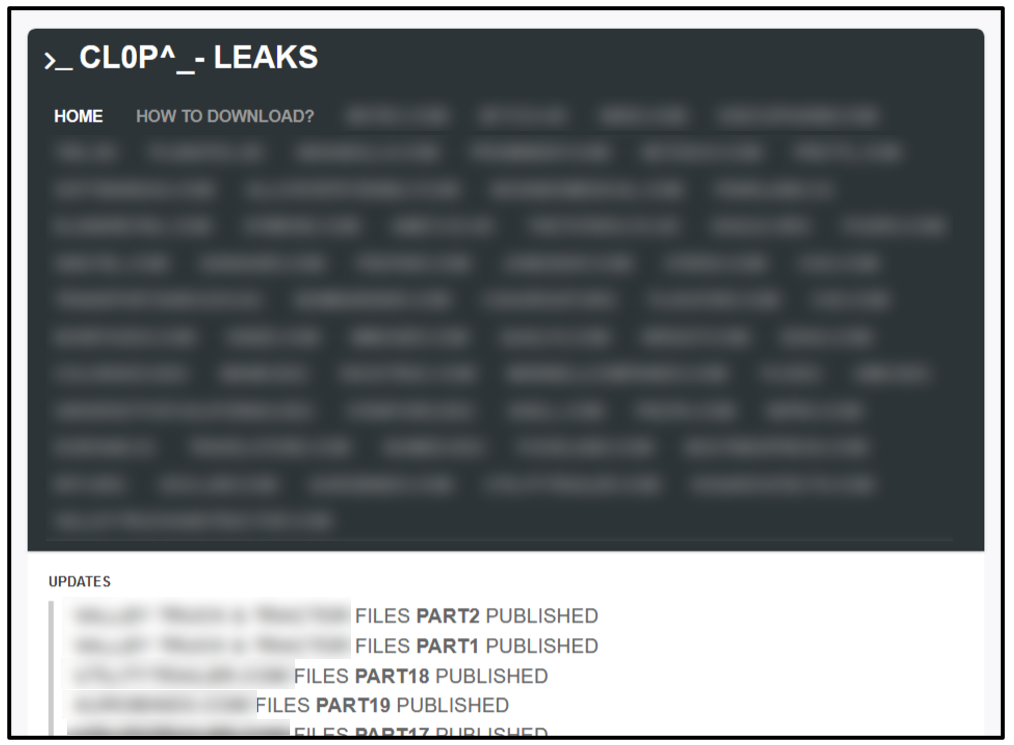
Clop ransomware updated its methods in March 2020 to include double extortion tactics. Sensitive data is first exfiltrated from the target before their files are encrypted. The attackers created a .onion website on the dark web called “Cl0p^_- Leaks” (shown in the image below), to serve as a platform to publicly leak confidential data belonging to victims who refused to pay their ransom:
Figure 8 - Cl0p^_- Leaks homepage.
The website additionally provides an updated list of organizations infected and links to their published data. This includes a guide to assist visitors in downloading large files with the Tor browser.
The threat actors take the opportunity here to provide more information on their operation and motivations. The full text of this is shown below:
Figure 9 - Cl0p^_- Leaks ‘About Us’ page.
Since emerging from the threat landscape, Clop has proven to be a profitable endeavor for the threat actors behind it. The ransomware has been actively distributed by established threat actors. Despite the efforts of authorities to disrupt their activities, the Clop ransomware group appear to be well resourced.
Their malware continues to evolve, finding and developing new ways in which to bypass security measures and infect more victims.
YARA Rule
The following YARA rule was authored by the BlackBerry Research & Intelligence Team to catch the threat described in this document:
import "pe"
rule Mal_Win_Ransom_Clop
{
meta:
description = "Clop ransomware sample"
author = "Blackberry Threat Research"
date = "2021-06"
strings:
$s1 = "you_offer.txt" ascii
$s2 = "ClopReadMe.txt" wide
$s3 = "autoexec.bat" wide
$s4 = "ntdetect.com" wide
$s5 = "GetKeyboardLayout" nocase ascii
$s6 = "CryptDestroyKey" nocase ascii
condition:
//32-bit PE File
pe.is_32bit() and
// All Strings
all of them
}
|
Indicators of Compromise (IoCs)
At BlackBerry, we take a prevention-first and AI-driven approach to cybersecurity. Putting prevention first neutralizes malware before the exploitation stage of the kill-chain.
By stopping malware at this stage, BlackBerry® solutions help organizations increase their resilience. It also helps reduce infrastructure complexity and streamline security management to ensure business, people, and endpoints are secure.
Dropped Files:
%CurrentDirectory%\Clearnetworkdns_11-22-33.bat
%CurrentDirectory%\HotGIrls (0 KB)
Mutex:
^_-HappyLife^_-
Appended File Extension:
.Clop
Ransom note:
CIopReadMe.txt
|
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment.
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.