Threat Thursday: Bee-ware of Hive Ransomware
Summary
First seen in June 2021, the Hive ransomware family most recently made headlines for attacking commercial real estate software company Altus Group. This threat favors the increasingly common attack technique of double extortion, where data is both locally encrypted and exfiltrated before a ransom demand is made.
If the victim refuses to cooperate with the threat actors, their data is published to Hive’s leak site, titled "Hive Leaks," which at the time of writing is located on the dark web at hxxp[:]//hiveleakdbtnp76ulyhi52eag6c6tyc3xw7ez7iqy6wc34gd2nekazyd[.]onion/
The current list of Hive leaks includes seven companies that have refused to cooperate with the Hive threat actors. As it is such a new threat, this number is likely to continue growing.
Operating System
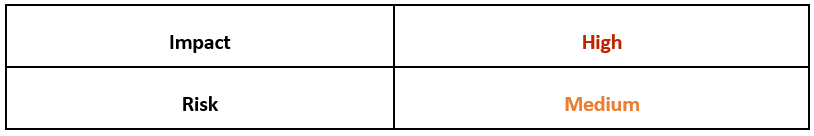
Risk & Impact
Technical Analysis
The very first sample of Hive was uploaded to VirusTotal on June 25, 2021. The file was named “encryptor_win32.exe.” The initial Hive ransomware binary discovery was made and announced via Twitter the next day by @fbgwls245, whose Twitter bio identifies them as a “ransomware hunter.”
The Hive samples are written in the Go programming language, and compiled for both 32-bit and 64-bit machines. The samples themselves are UPX packed to reduce their size, as Go binaries tend to get quite large.
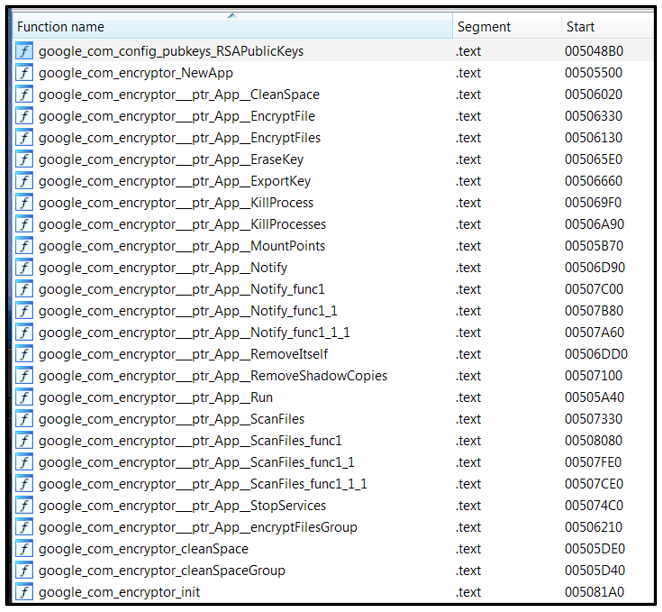
Once unpacked, the sample is not obfuscated, and the main functions that will be used by the Hive ransomware can be seen:
Figure 1: Main function of Hive
Upon execution, the malware performs checks on specific services (bmr, sql, oracle, postgres, redis, vss, backup, sstp) and if found, they are stopped. The malware then creates a snapshot of currently running processes and checks for the presence of “mspub” and “msdesktop” processes. If those processes are found, they are terminated. This is done to ensure that files are not in use, so they can be encrypted.
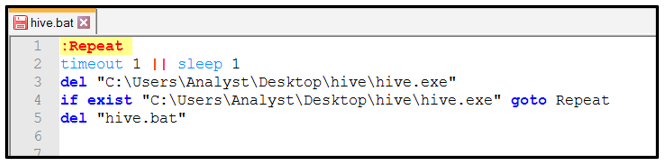
Continuing its execution, Hive then drops two files into the directory from which the initial sample was executed. The first file is called “hive.bat.” This batch script is used to enforce a timeout by execution delay of one second, then to perform cleanup after the encryption has finished by deleting the Hive executable and the “hive.bat” script. This is shown in the following image:
Figure 2: Timeout execution delay
The second file is called “shadow.bat.” This batch script is used to delete shadow copies by invoking cmd.exe and passing the following command-line argument: “vssadmin.exe delete shadows /all /quiet”. This deletes all shadow volumes without notifying the victim. Once that has been completed, the script then deletes the “shadow.bat” file.
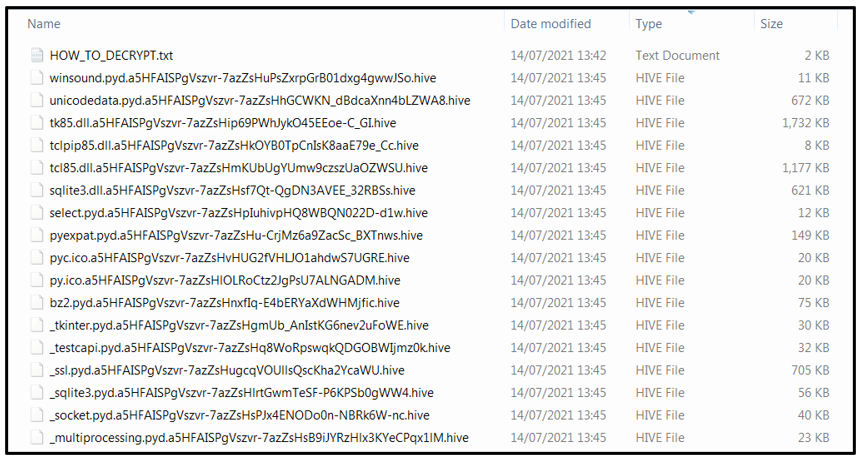
During the encryption process, Hive will ignore the “C:\Windows” drive and will not encrypt any files on it, to minimize the possibility of damaging the victim’s system to the point where they cannot get online to pay the threat actors. It will also skip over files that have “.lnk” file extensions, to avoid encrypting shortcut files. However, it will encrypt everything else by appending a “.hive” file extension to all files, as seen below:
Figure 3: Encrypted files
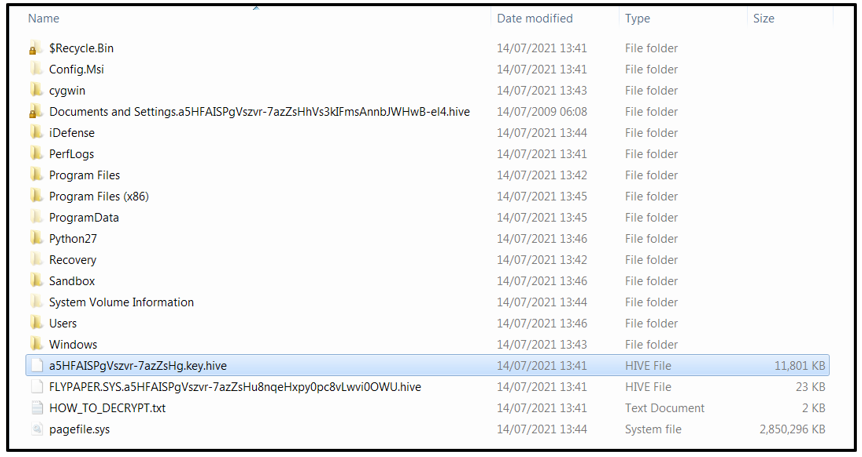
During the encryption process, a file with a double final extension of “*.key.hive” (e.g., “a5HFAISPgVszvr-7azZsHg.key.hive”) is dropped into the “C:\Windows\” directory, as shown in Figure 4. This file is always 11801 KB in size. The purpose of this file is unclear, but it’s possible that it is required when decrypting the files. The ransom note states that this file cannot be modified, renamed, or deleted, otherwise the encrypted files will be undecryptable:
Figure 4: "*.key.hive" file drop
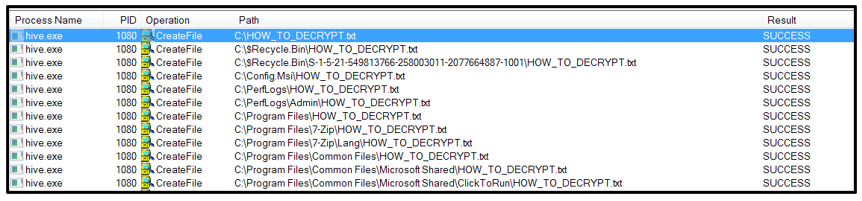
This ransom note is dropped in each affected directory, and named "HOW_TO_DECRYPT.txt", as shown below:
Figure 5: Ransom note drop
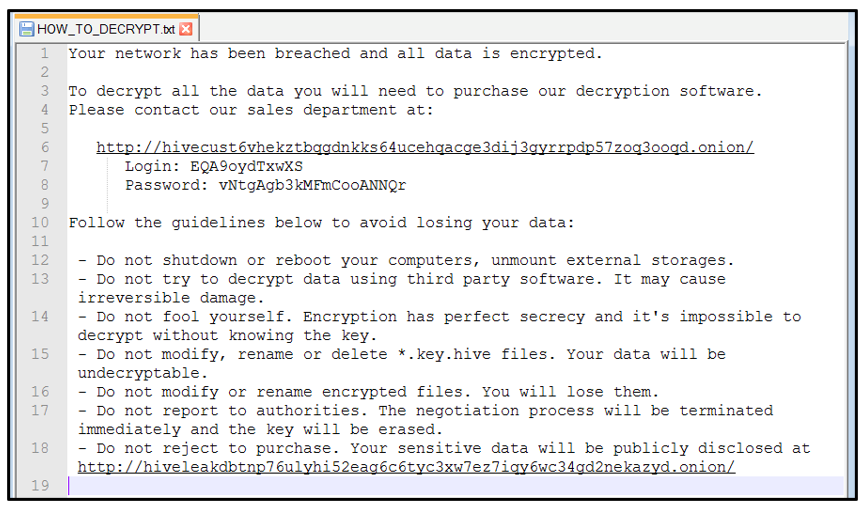
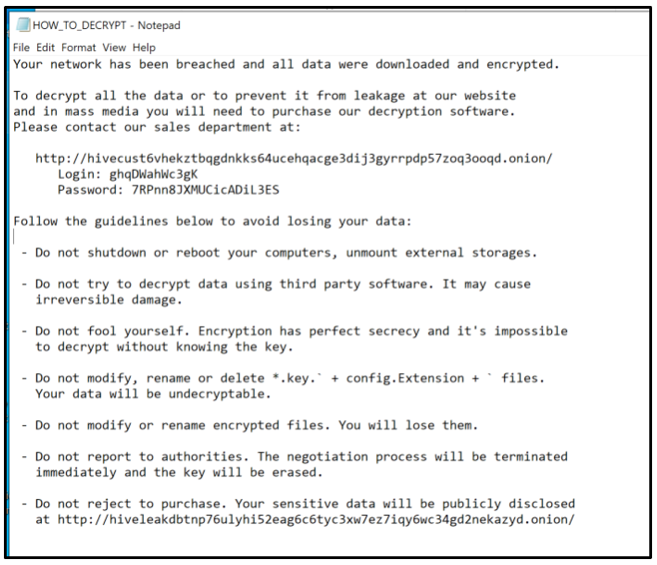
The ransom note informs the victim that their network has been breached and that their data is now encrypted, as shown below:
Figure 6: Hive ransom note
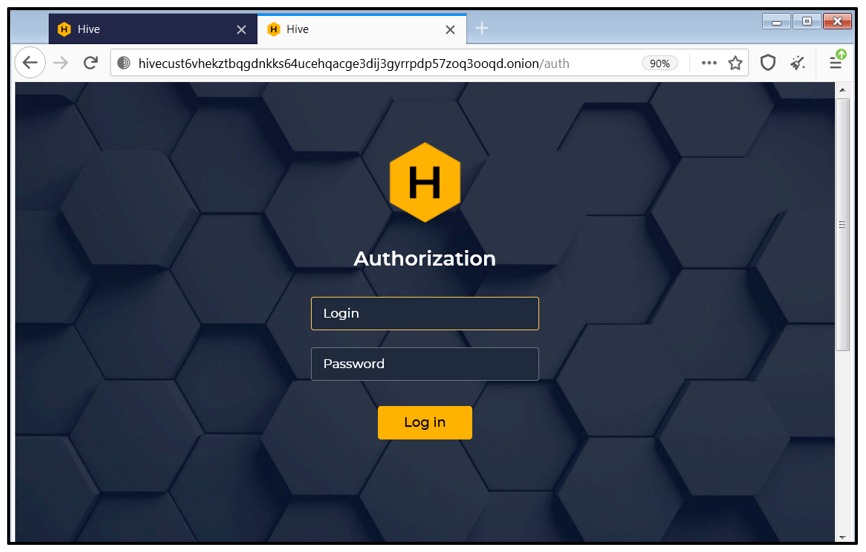
The victim is required to download a Tor browser to get in contact with Hive threat actors. In order to purchase the decryption software to recover their data, the victim needs to navigate to the Hive threat actors’ dark web site, located at the time of writing at: hxxp[:]//hivecust6vhekztbqgdnkks64ucehqacge3dij3gyrrpdp57zoq3ooqd[.]onion/
To obtain the decryption software, the victim first needs to get in to contact with Hive’s “sales department” to get an offer. The login credentials are the same for each victim, and they can be found in the ransom note. In the first sample we analyzed, the credentials were:
- Login: EQA9oydTxwXS
- Password: vNtgAgb3kMFmCooANNQr
Figure 7: Hive’s “customer service” login page
At the time of writing, these login credentials are no longer accepted.
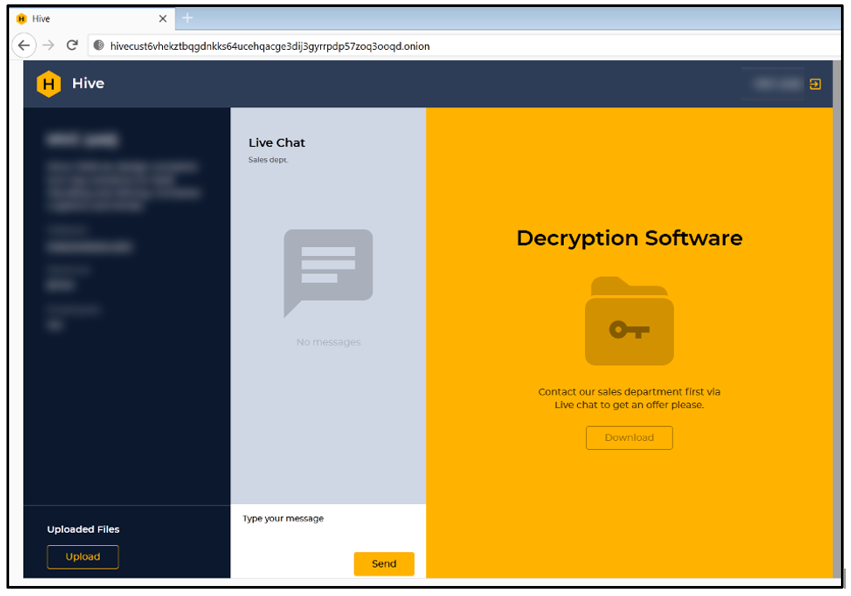
As Hive is still under development, newer samples may require different credentials. In a newer sample, login credentials were as follows:
- Login: ghqDWahWc3gK
- Password: 7RPnn8JXMUCicADiL3ES
Figure 8: Customer service page – live chat
In this newer sample, the ransom note had also changed slightly:
Figure 9: Updated ransom note
If the victim does not complete Hive’s demands, the threat actors disclose their sensitive data on the “Hive Leaks” page located at the following site:
hxxp[:]//hiveleakdbtnp76ulyhi52eag6c6tyc3xw7ez7iqy6wc34gd2nekazyd[.]onion/
At the time of writing, there are seven victims whose data has been leaked, presumably after refusing to cooperate with Hive threat actors. The data that was stolen from Altus Group on June 23, 2021, was disclosed on June 26, 2021. However, the download link that contained a sample of this data has expired.
There currently seems to be little in common between the initial victims. They are in different industries, based in a variety of countries, and vary widely in size.
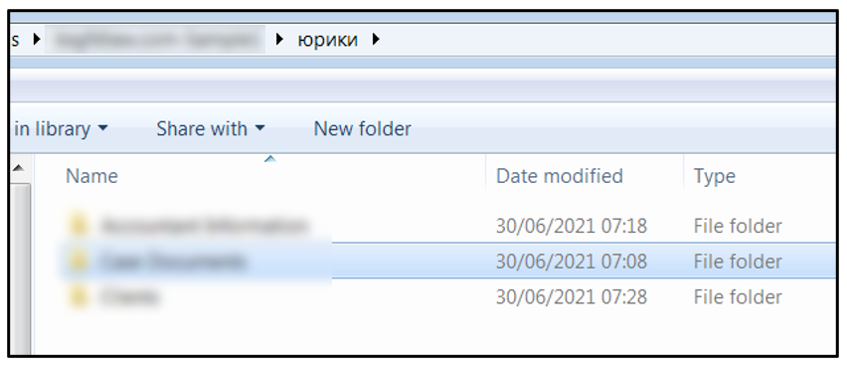
Investigating the contents of the stolen data, we noticed that one of the folders is named “юрики,” which is a Russian slang term that refers to lawyers. This could indicate that threat actors behind Hive ransomware are Russian-speaking.
Figure 10: Sample data
YARA Rule
The following YARA rule was authored by the BlackBerry Research & Intelligence Team to catch the threat described in this document:
import "pe"
rule Mal_Ransom_Hive_2021_unpacked
{
meta:
description = "Detects unpacked Hive ransomware"
author = "Blackberry Threat Research team"
date = "2021-06-07"
strings:
//google.com/encryptor.(*App).KillProcesses
$h = {676f6f676c652e636f6d2f656e63727970746f722e282a417070292e4b696c6c50726f636573736573}
//google.com/encryptor.(*App).StopServices
$h1 = {676f6f676c652e636f6d2f656e63727970746f722e282a417070292e53746f705365727669636573}
//google.com/encryptor.(*App).RemoveShadowCopies
$h2 = {676f6f676c652e636f6d2f656e63727970746f722e282a417070292e52656d6f7665536861646f77436f70696573}
//google.com/encryptor.(*App).EncryptFiles
$h3 = {676f6f676c652e636f6d2f656e63727970746f722e282a417070292e456e637279707446696c6573}
//google.com/encryptor.(*App).encryptFilesGroup
$h4 = {676f6f676c652e636f6d2f656e63727970746f722e282a417070292e656e637279707446696c657347726f7570}
//google.com/encryptor.(*App).ScanFiles
$h5 = {676f6f676c652e636f6d2f656e63727970746f722e282a417070292e5363616e46696c6573}
//google.com/encryptor.(*App).EraseKey
$h6 = {676f6f676c652e636f6d2f656e63727970746f722e282a417070292e45726173654b6579}
//google.com/encryptor.(*App).RemoveItself
$h7 = {676f6f676c652e636f6d2f656e63727970746f722e282a417070292e52656d6f7665497473656c66}
//http://hivecust6vhekztbqgdnkks64ucehqacge3dij3gyrrpdp57zoq3ooqd.onion/
$h8 = {687474703a2f2f6869766563757374367668656b7a74627167646e6b6b7336347563656871616367653364696a33677972
7270647035377a6f71336f6f71642e6f6e696f6e2f}
//http://hiveleakdbtnp76ulyhi52eag6c6tyc3xw7ez7iqy6wc34gd2nekazyd.onion/
$h9 = {687474703a2f2f686976656c65616b6462746e703736756c796869353265616736633674796333787737657a3769717936
776333346764326e656b617a79642e6f6e696f6e2f}
condition:
uint16(0) == 0x5a4d and
all of ($h*)
}
|
Indicators of Compromise (IoCs)
File System Actions
Created:
- hive.bat
- shadow.bat
- HOW_TO_DECRYPT.txt
- ‘.hive’ encrypted files
- “*.key.hive” e.g., a5HFAISPgVszvr-7azZsHg.key.hive
Modified:
- All affected files post encryption
Deleted:
Processes
Created:
- cmd /c hive.bat >NUL 2>NUL
- cmd /c shadow.bat >NUL 2>NUL
- vssadmin.exe delete shadows /all /quiet
|
BlackBerry Assistance
If you’re battling Hive ransomware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) incidents.
Our global team is standing by to assist you with around-the-clock support, whenever and wherever it is required. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment.
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.