How LockBit 2.0 Ransomware Works and Indicators of Compromise
Fortune 500 consulting and professional services company gets “LockBit” to the tune of $50M
June 30, 2022 update: Security researchers discovered a new LockBit 2.0 campaign using PDFs to hide ransomware executables. The social engineering premise of this attack is a claim that your organization owes money for using an unlicensed image.
February 10, 2022 update: The FBI recently published a flash bulletin with indicators of compromise (IoCs) for LockBit 2.0, including mitigation strategies for protecting against the ransomware.
Summary
The gang behind LockBit Ransomware-as-a-Service (RaaS) appears to have been quite busy lately, judging by their compromise of a top global consulting firm yesterday, reportedly taking encrypted data from the company and demanding $50 million in ransom not to publish it.
LockBit ransomware has gained huge popularity among threat actors since the first version of the ransomware family appeared in September 2019. It is distributed via various underground forums, and targets victims in the United States, Canada, Europe, Asia, and Latin America.
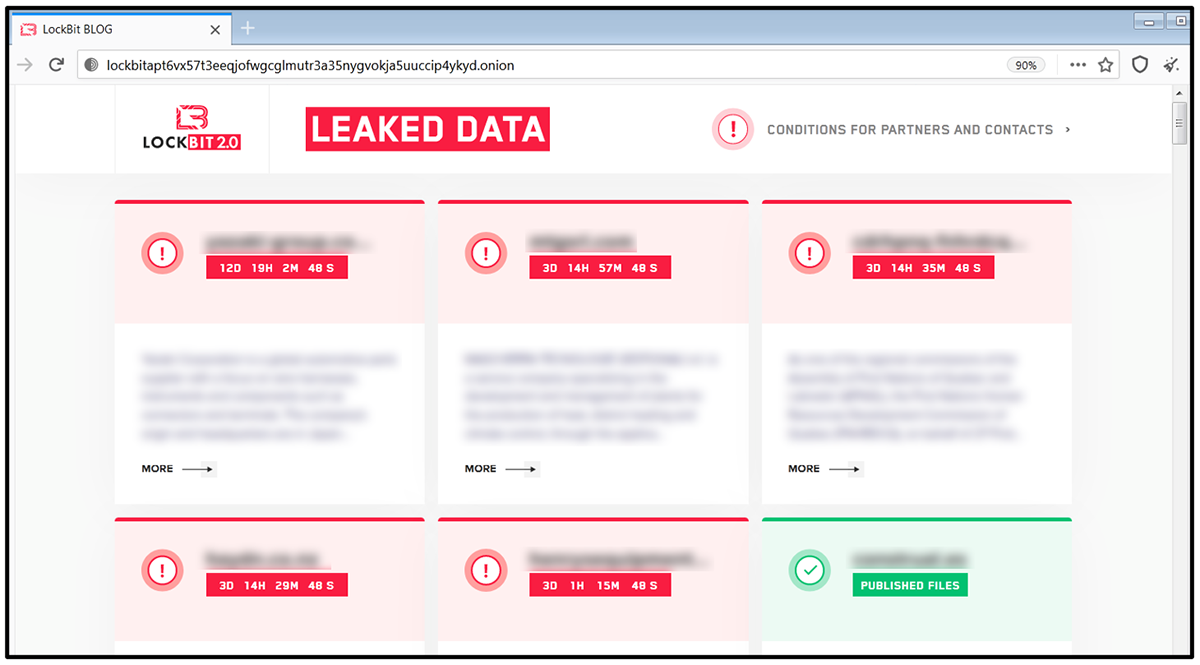
LockBit uses a double-extortion technique to force victims to pay the ransom as fast as possible, as data is both encrypted locally and exfiltrated to the malware operators before the ransom demand is made. If the victim refuses to cooperate with the threat actors, their data is published to LockBit’s leak site, titled "Leaked Data," which is currently located on the dark web at:
hxxp[:]//lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd[.]onion.
At the time of writing this blog, there were 61 victims listed on their TOR site. New victims are added to the list nearly every day.
Watch our demo video that shows BlackBerry going head-to-head with a live sample of LockBit ransomare.
Operating System
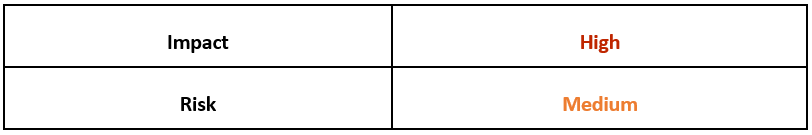
Risk & Impact
Technical Analysis
LockBit2.0 appeared in the wild in mid-2021. This threat avoids infecting machines in countries that used to be part of the Soviet Union.
Just like Conti, LockBit 2.0 is a ransomware that can spread within a target network using a worm-like functionality. Samples of this version of the threat are generally around 855KB in size.
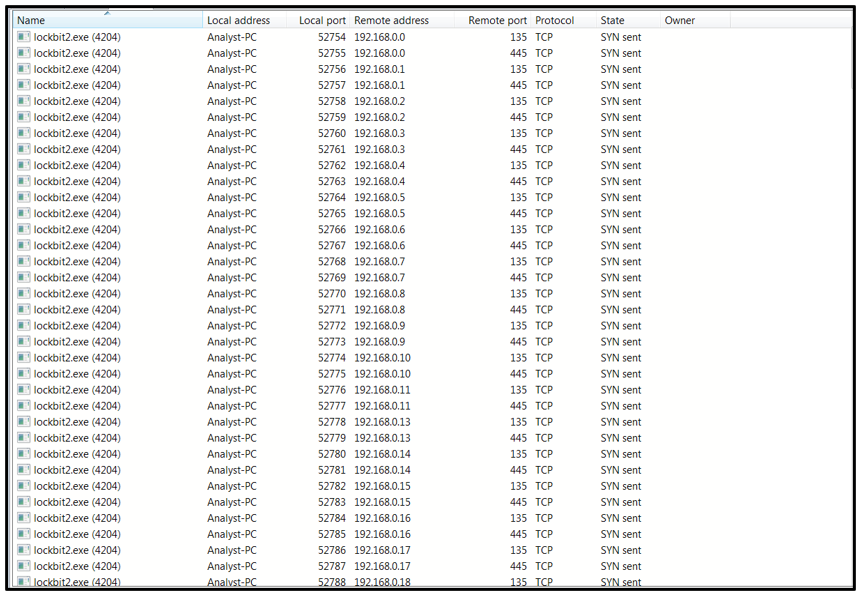
Upon execution, the malware will search for local subnetworks to try to spread laterally.
Figure 1: Self-spread on local subnetwork
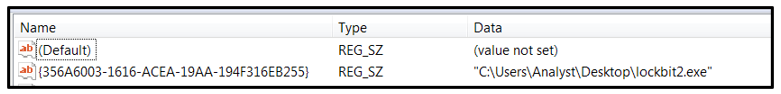
LockBit2.0 then creates the following registry Run key, which points to the location of the malware file: “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\{356A6003-1616-ACEA-19AA-194F316EB255}”
It does this as a way of achieving persistence, as this registry key will restart the threat upon reboot.
Figure 2: Registry run key creation
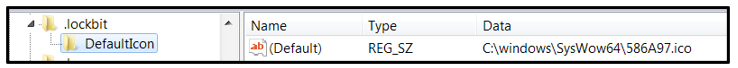
Then it creates two registry keys. The first one points to the location of the icon file that will be used for encrypted files:
- “HKEY_LOCAL_MACHINE\Software\Classes\.lockbit\DefaultIcon”
Figure 3: HKEY_LOCAL_MACHINE\Software\Classes\.lockbit\DefaultIcon registry key creation
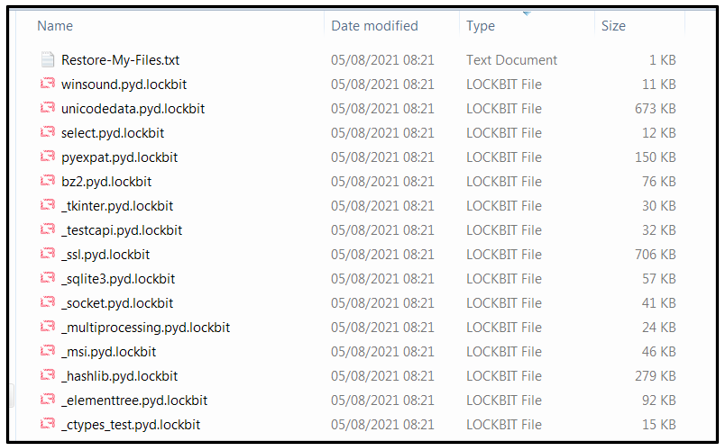
Affected files will be renamed with an appended file-extension of “.lockbit.”
Figure 4: Files encrypted by LockBit 2.0
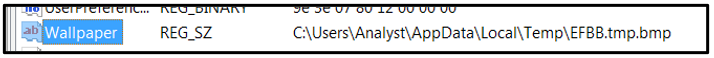
The second key points to the location of the image file that will be used to change the desktop wallpaper upon encryption:
- “HKEY_CURRENT_USER\Control Panel\Desktop\Wallpaper”
Figure 5: Registry key modification
The new desktop wallpaper can be seen in the image below.
Figure 6: Changed desktop wallpaper
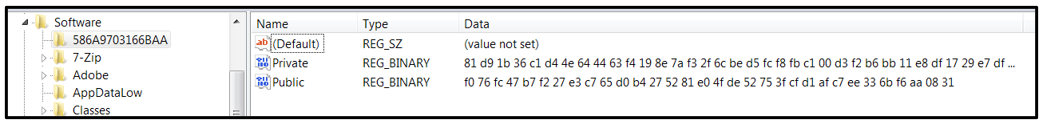
It also creates the following two registry keys:
- HKEY_CURRENT_USER\Software\586A9703166BAA\Private
- HKEY_CURRENT_USER\Software\586A9703166BAA\Public
Figure 7: Public and private registry key creation
These two registry keys are used as part of the encryption process.
LockBit 2.0 performs checks to see if specific processes are running, and it terminates them if they are found. Those processes include various tools that are commonly used to identify malware on a system, such as ProcMon, Wireshark, and Process Explorer.
This threat also carries out checks to find specific services and stop them. Those services include SQL or other database servers, browsers, Microsoft® Office applications and more. Stopping these services unlocks files that are in use, so they can be encrypted.
The malware then deletes shadow copies and backups stored on the victim’s computer, to ensure the user can’t easily restore their encrypted files.
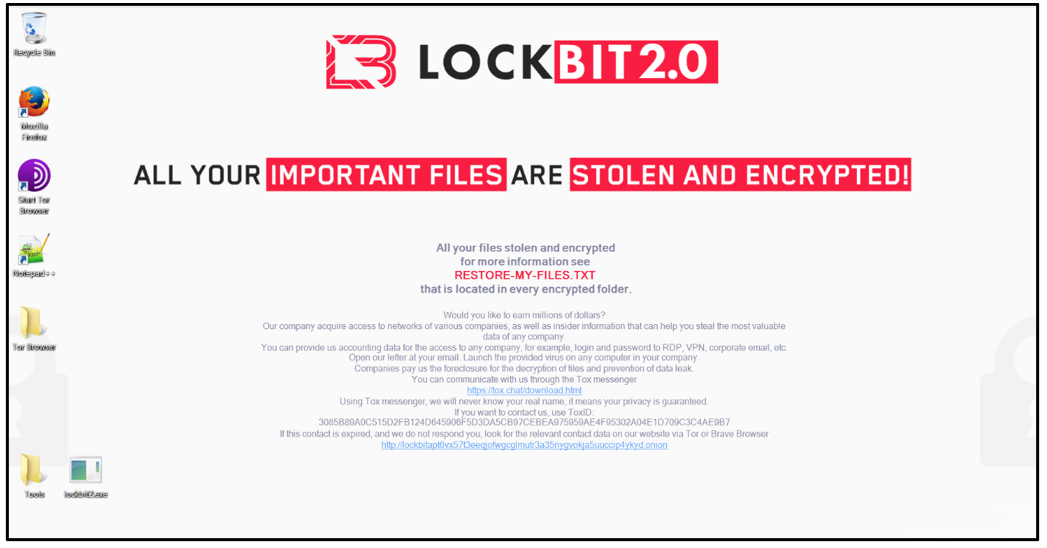
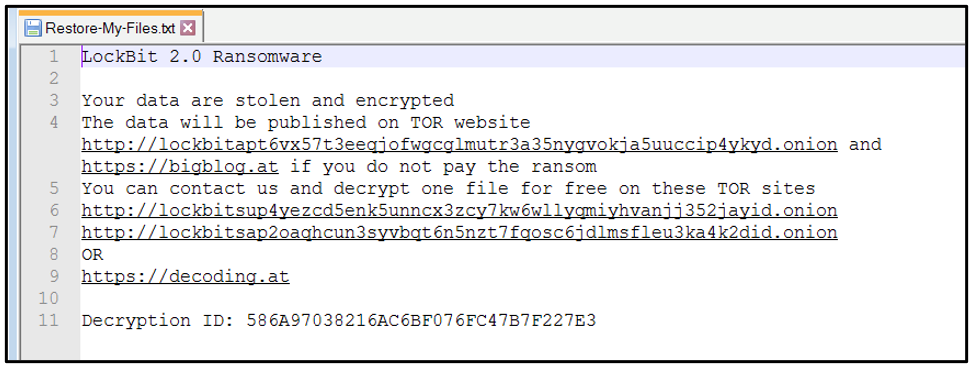
A ransom note titled “Restore-My-Files.txt” is dropped in each affected directory, as shown below:
Figure 8: LockBit 2.0 ransom note
The note states that the victim has been infected with LockBit 2.0, and that their files have been “stolen and encrypted.” If the victim refuses to cooperate, the note says, their data will be published on the malware operator’s “Leaked Data” site:
- hxxp[:]//lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd[.]onion
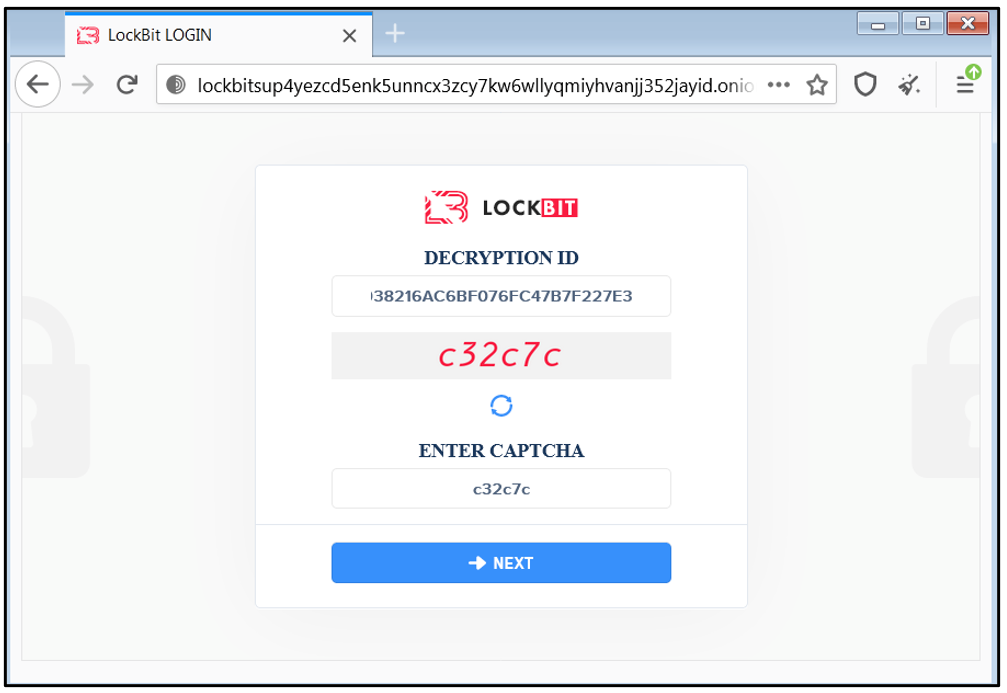
The LockBit2.0 threat actor offers the victim an option to decrypt one of the encrypted files, as a way of demonstrating that their tool can do as it promises. To do so, the victim is required to input their “decryption ID” at one of the following two TOR sites (as seen in Figure 10):
- Hxxp[:]//lockbitsup4yezcd5enk5unncx3zcy7kw6wllyqmiyhvanjj352jayid[.]onion
- Hxxp[:]//lockbitsap2oaqhcun3syvbqt6n5nzt7fqosc6jdlmsfleu3ka4k2did[.]onion
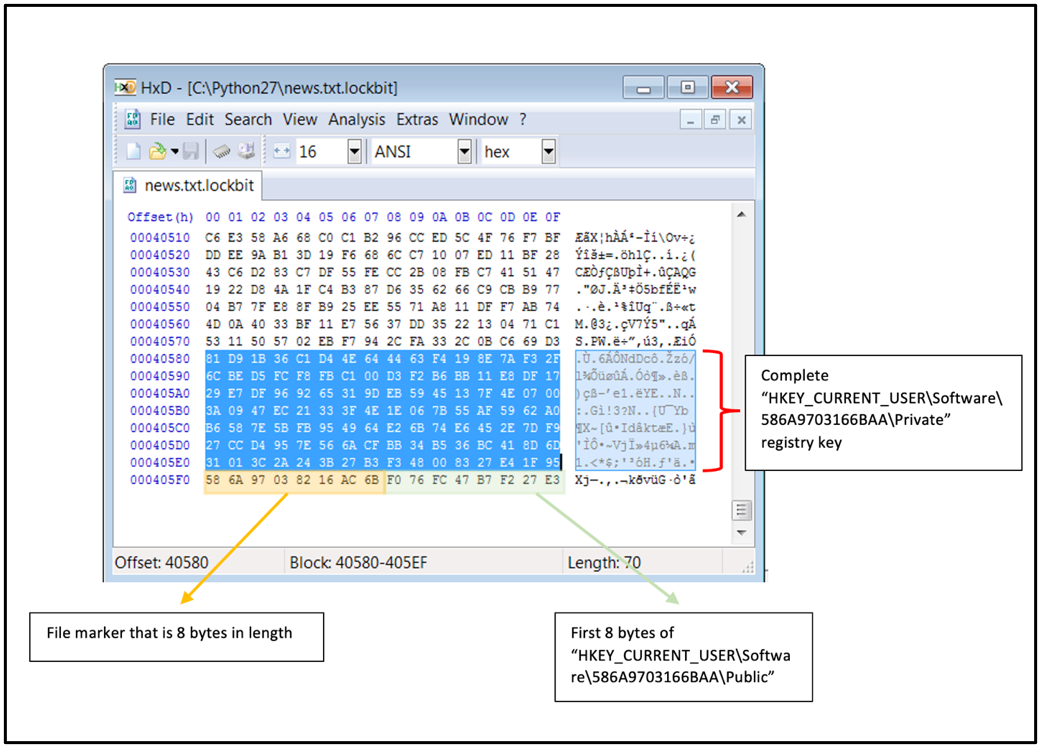
The decryption IDs are contained in each ransom note. The ID is a 16-byte-long string that is generated from the first 8 bytes of the “HKEY_CURRENT_USER\Software\586A9703166BAA\Public” registry key, and the 8-byte long file marker 586A9703166B (as seen in the image below) that is appended to each encrypted file:
Figure 9: Encrypted file structure
If the victim goes to the threat actor’s webpage, they are presented with the login screen shown in the image below:
Figure 10: LockBit login page
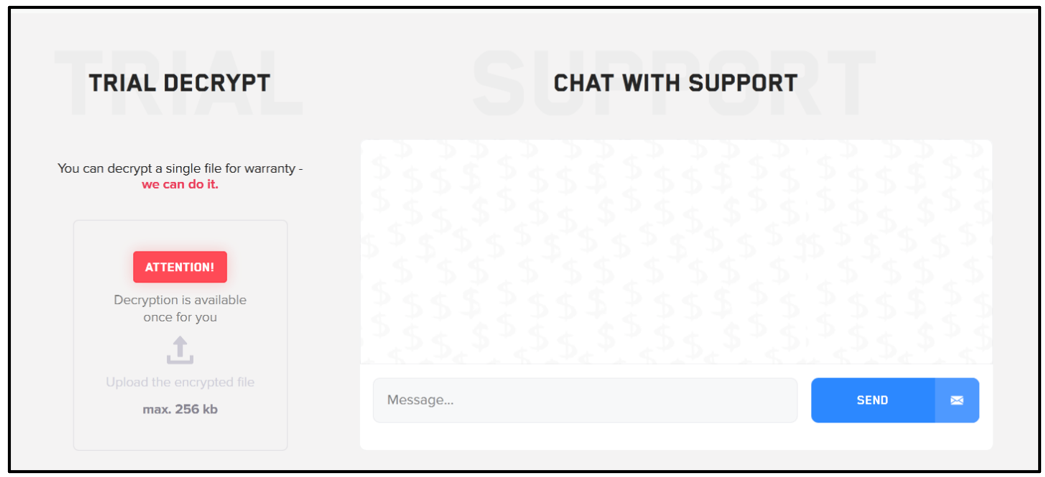
Upon login, the victim is presented with the message, “Your files are encrypted by LockBit.” This is followed by an explanation of how they got encrypted, and how to recover those files. The page also presents the victim with the option to decrypt a single file, and the ability to chat with their support team, which can be seen in the screenshot below.
Figure 11: Trial decryptor and chat options
The ransom note also specifies that if the victim refuses to cooperate, their data will be publicly disclosed on their dark web site:
- hxxp[:]//lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd[.]onion
Figure 12: LockBit leaked data TOR site
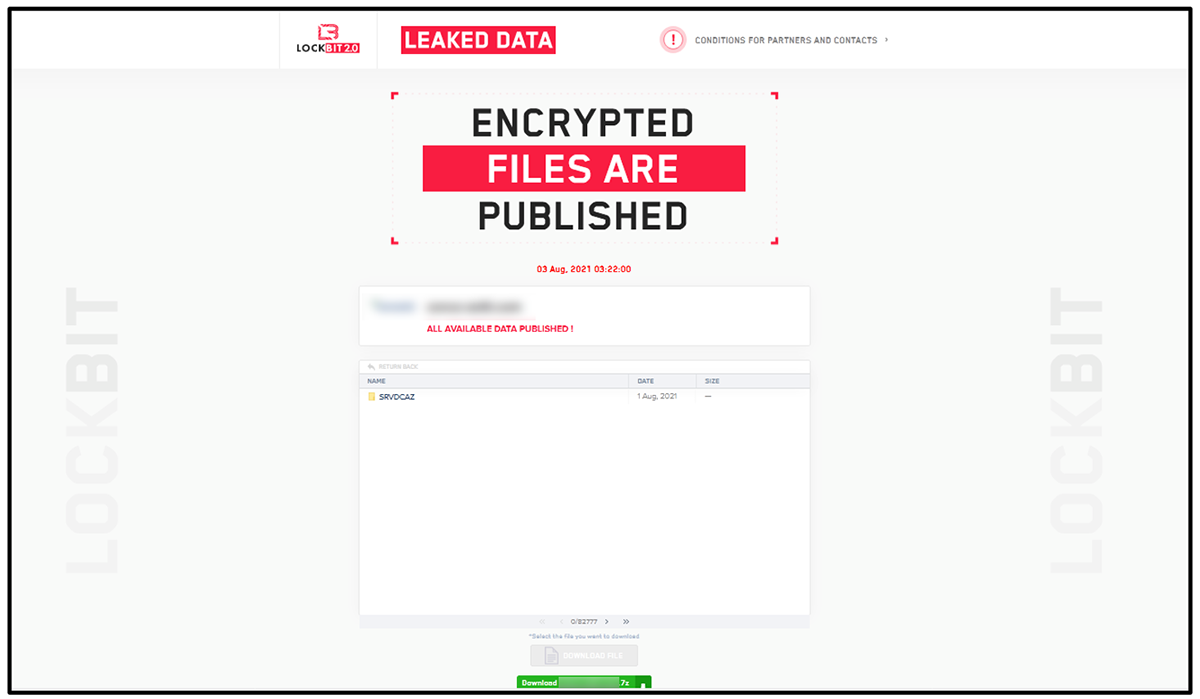
The “Leaked Data” site includes both newly infected victims who still have time left to cooperate, as well as victims who refused to pay the ransom, and whose data has since been leaked and is available for download.
Figure 13: Stolen data is available for download
The leak site also has a section on “Conditions for partners and contacts.” The page states that LockBit 2.0 is an affiliate program experiencing “temporarily [sic] relaunch to intake of partners,” which presumably means that they are now accepting new partners after having paused this program for a period of time.
Figure 14: LockBit2.0 feature list
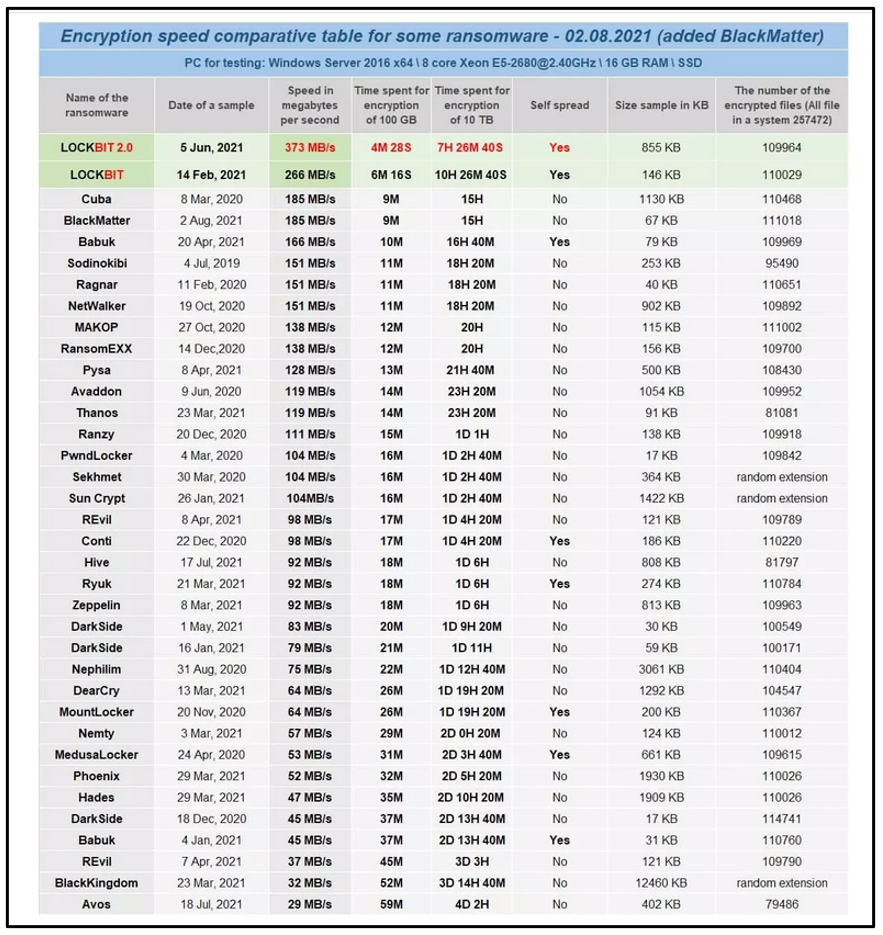
The LockBit authors claim to have the fastest encryption speed of any current ransomware. They provide a comprehensive list of other ransomware families for comparison, as seen in the image below, including information such as their (purported) encryption speed and their sample size.
Figure 15: Ransomware family encryption speed* table (*accuracy not verified)
The threat actors also include a link for potential partners to download each ransomware and test for themselves.
On their website, the LockBit2.0 gang has provided a variety of different methods to contact them.
Figure 16: LockBit2.0 contact information
Having performed open source intelligence (OSINT) on the Tox ID, we can see that the user who goes by the alias of “LockBitSupp” is quite active on the Russian hacking forum xss[.]is.
Figure 17: LockBitSupp xss.is account
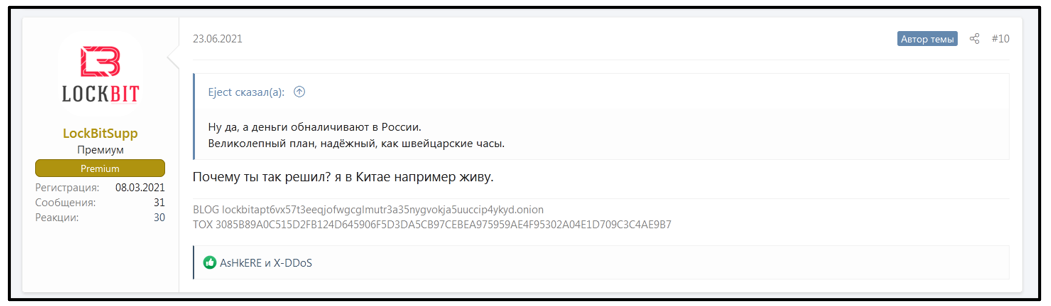
Looking at this user’s activity, they mention in one thread that they live in China. However, this user has restricted access to view their profile.
Figure 18: LockBitSupp claims to live in China
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry blog.
YARA Rule
The following YARA rule was authored by the BlackBerry Threat Research Team to catch the threat described in this document:
import "pe"
rule Mal_Ransom_W32_LockBit2
{
meta:
description = "Detects W32 LockBit 2.0 ransomware"
author = "Blackberry Threat Research team "
date = "2021-08-05"
strings:
//\Registry\Machine\Software\Classes\.lockbit
$x0 = {5c00520065006700690073007400720079005c004d0061006300680069006e0065005c0053006f006600740077006100720065005c
0043006c00610073007300650073005c002e006c006f0063006b00620069007400}
//http://lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd.onion
$x1 = {68007400740070003a002f002f006c006f0063006b0062006900740061007000740036007600780035003700740033006500650071
006a006f00660077006700630067006c006d0075007400720033006100330035006e007900670076006f006b006a006100350075007500630063
0069007000340079006b00790064002e006f006e0069006f006e00}
//LockBit 2.0 Ransom
$x2 = {4c006f0063006b00420069007400200032002e0030002000520061006e0073006f006d00}
//If you want to contact us, use ToxID:
3085B89A0C515D2FB124D645906F5D3DA5CB97CEBEA975959AE4F95302A04E1D709C3C4AE9B7
$x3 = {49006600200079006f0075002000770061006e007400200074006f00200063006f006e0074006100630074002000750073002c002000
75007300
6500200054006f007800490044003a00200033003000380035004200380039004100300043003500310035004400320046004200310032003400
4400360034003500390030003600460035004400330044004100350043004200390037004300450042004500410039003700350039003500390
0410045003400460039003500330030003200410030003400450031004400370030003900430033004300340041004500390042003700}
///C ping 127.0.0.7 -n 3 > Nul & fsutil file setZeroData offset=0 length=524288 "%s" & Del /f /q "%s"
$x4 = {2f0043002000700069006e00670020003100320037002e0030002e0030002e00370020002d006e002000330020003e0020004e00750
06c00200026002000660073007500740069006c002000660069006c00650020007300650074005a00650072006f00440061007400610020006f
00660066007300650074003d00300020006c0065006e006700740068003d0035003200340032003800380020002200250073002200200026002
000440065006c0020002f00660020002f00710020002200250073002200}
condition:
uint16(0) == 0x5a4d and
all of ($x*)
}
|
Indicators of Compromise (IoCs)
File System Actions
Created:
- Restore-My-Files.txt → ransom note
- .lockbit → appended file extension
- C:\Windows\SysWOW64\172375.ico → Lockbit icon
- C:\Users\<username>\AppData\Local\Temp\5347.tmp.bmp → Lockbit wallpaper
Modified:
- All affected files post-encryption
Registries
Created:
- HKEY_CURRENT_USER\Software\172375D3E3B45C\Private
- HKEY_CURRENT_USER\Software\172375D3E3B45C\Public
- HKEY_LOCAL_MACHINE\Software\Classes\.lockbit\DefaultIcon
Modified:
- HKEY_CURRENT_USER\Control Panel\Desktop\Wallpaper
Processes
Created:
- vssadmin delete shadows /all /quiet
- wmic shadowcopy delete
- bcdedit /set {default} bootstatuspolicy ignoreallfailures
- bcdedit /set {default} recoveryenabled no
|
BlackBerry Assistance
If you’re battling LockBit malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.