Threat Thursday: Don't Let njRAT Take Your Cheddar
Summary
njRAT, also known as Bladabindi, is a remote access Trojan (RAT) which was first discovered in 2012. This tool was developed by a threat actor group known as Sparclyheason and used in attacks targeting organizations in Middle Eastern countries. The backdoor has been widely available since its source code was leaked in May 2013. The RAT is popular with both experienced threat actors and amateurs alike.
Most commonly, njRAT is delivered through weaponized documents as part of phishing campaigns. It can also be found masquerading as legitimate or cracked software on filesharing websites, or delivered through drive-by downloads.
Once deployed to a victim’s machine, njRAT can perform surveillance or take control of the infected system. The malware’s capabilities include logging keystrokes, capturing screenshots, password stealing, exfiltrating data, accessing web cameras and microphones, and downloading additional files.
Operating System
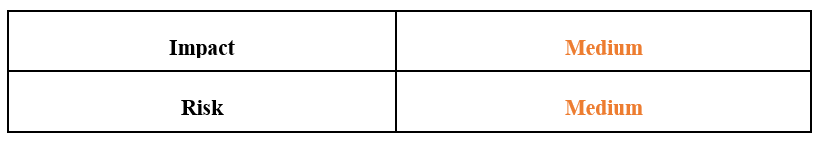
Risk & Impact
Technical Analysis
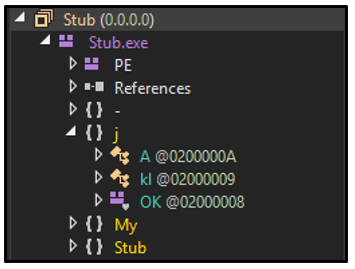
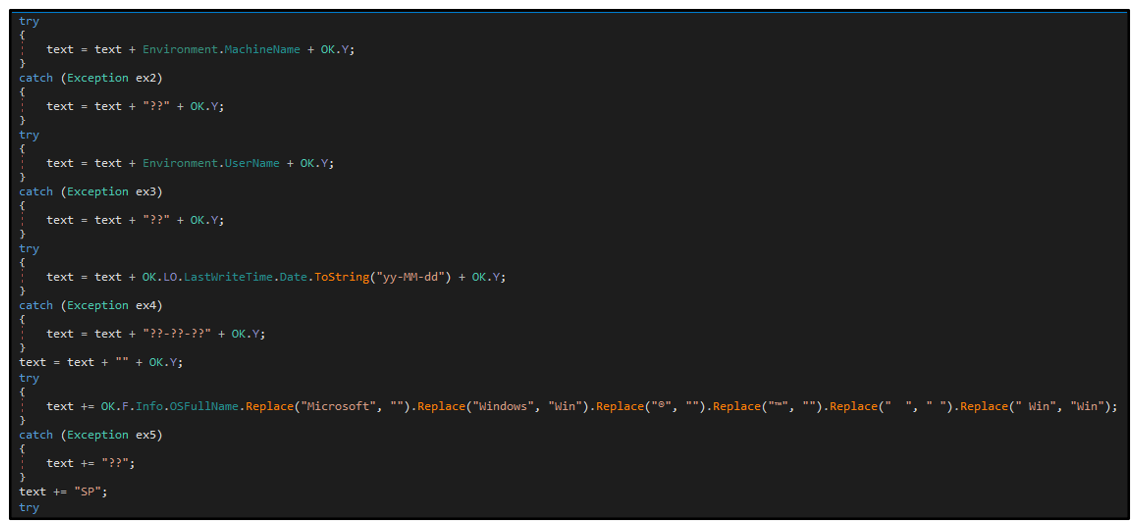
njRAT was developed using the Microsoft® .NET framework, so the binary's source code can be reviewed in a .NET decompiler such as dnSpy. The sample analyzed for this report, named “Tools.exe,” contains a project named "j" which includes two classes named "kl" and "OK." This is characteristic of executables generated by the njRAT tool.
Figure 1: Common classes belonging to njRAT
The “kl” class contains the functions GetAsyncKeyState, GetKeyboardLayout, GetKeyboardState, GetWindowThreadProcessId and MapVirtualKey to perform njRAT’s keylogging activities.
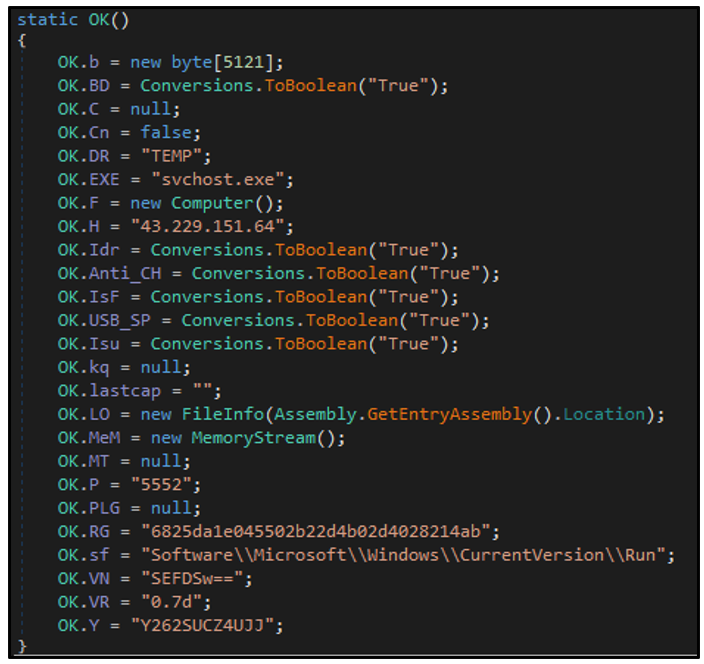
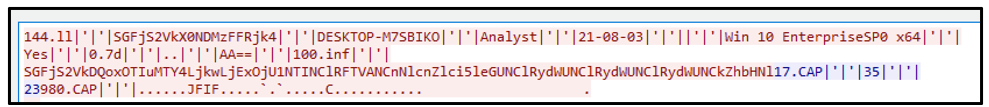
The rest of the malware’s functionality is contained in the “OK” class. This class also contains the hardcoded configuration information used by the RAT. For example, the configuration for this particular njRAT sample indicates that it was created with the njRAT builder version 0.7d:
Figure 2: Embedded configuration of njRAT
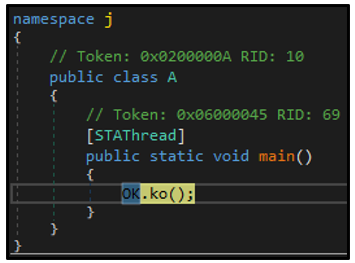
The sample’s entry point is located at j.A.main, and upon execution, the ko() function is called:
Figure 3: ko(), initial function called
This function checks to see if the sample is running in an emulated environment, or if any common analysis tools are also running on the system. The class CsAntiProcess will look for processes based on the list of predefined names detailed below. If any of the processes exist, then the malware will stop its execution:
procexp
|
SbieCtrl
|
SpyTheSpy
|
wireshark
|
apateDNS
|
IPBlocker
|
TiGeR-Firewall
|
Smsniff
|
xeinfoPE
|
NetSnifferCs
|
Sandboxie Control
|
Processhacker
|
dnSpy
|
CodeReflect
|
Reflector
|
ILSpy
|
VGAuthService
|
VBoxService
|
|
|
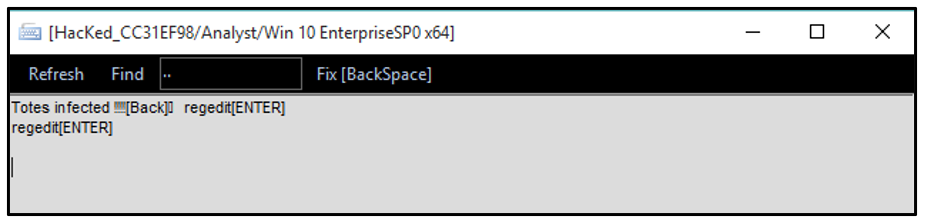
The sample then searches the system to check if a file exists under the path “C:\Tools.exe.” If not, it copies itself to this location.
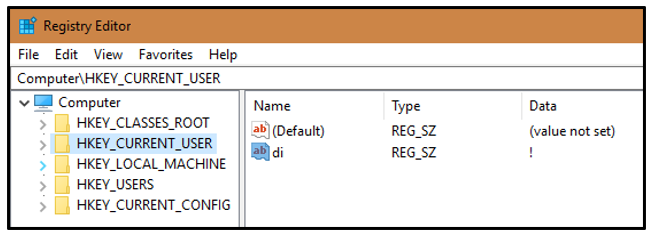
Next, njRAT creates a registry key under HKEY_CURRENT_USER named “di” with a value of “I”:
Figure 4: di registry key created
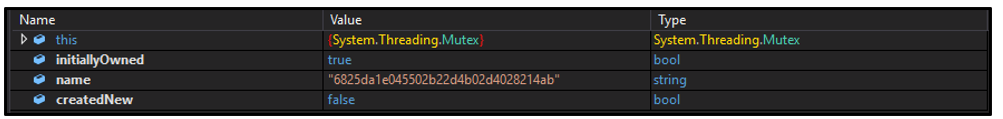
The threat will create a unique mutex to ensure only one instance of the backdoor is running on the system. The mutex name is defined by the value of "OK.RG" in the backdoor's configuration, as seen in Figure 2. If the mutex already exists, the process will exit:
Figure 5: Mutex created
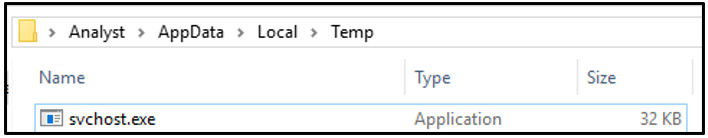
The sample then copies another instance of itself under the %TEMP% directory as svchost.exe:
Figure 6: njRAT executable dropped locally
Giving the njRAT binary the same (if fake) name as a common Windows utility helps the malicious process go unnoticed by the end user and many antivirus (AV) products. Once this is complete, the “Tools.exe” instance of njRAT exits and “svchost.exe” is launched.
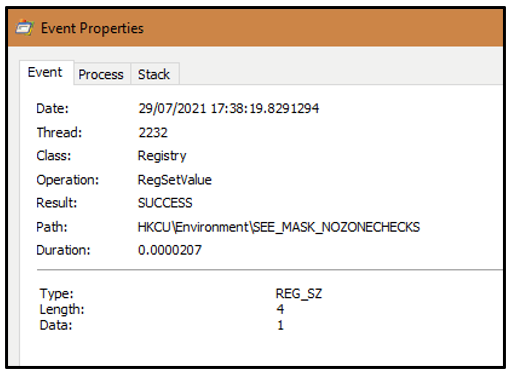
Next, the security settings of the affected system are lowered by setting the value of the environment variable SEE_MASK_NOZONECHECKS to 1. Processes are then allowed to execute without any zone-checking restrictions. This means that when files are downloaded and executed, the end user will not receive a dialog box with a security warning alert.
Figure 7: Disabling zone-checking restrictions
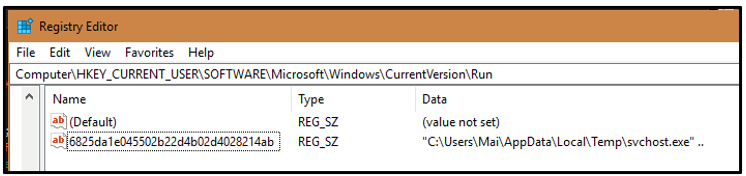
For persistence, the malware creates an autorun key in the registry to execute with each boot of the system. This key is also named after the OK.RG value in the configuration:
Figure 8: Autorun key
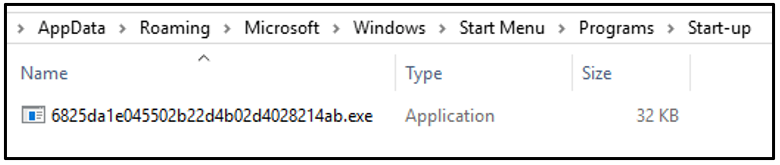
Additionally, the executable copies itself to the Windows Startup folder with the filename as the value of OK.RG:
Figure 9: njRAT executable dropped to StartUp location
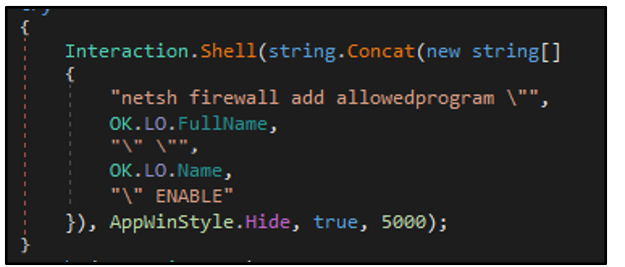
The executable then invokes “netsh.exe” to modify the system’s firewall rules and add the njRAT file as an allowed program:
Figure 10: Permitting njRAT to bypass firewall restrictions
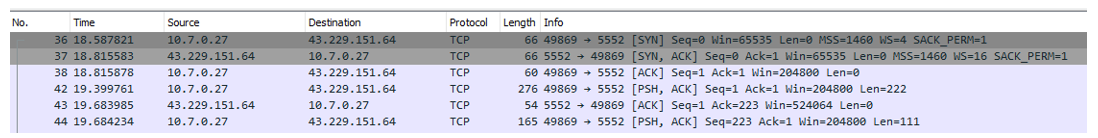
The OK.H value as seen in Figure 2, which is included in njRAT’s configuration, refers to the host address of the command and control (C2) server. The OK.P value defines the port number to connect to:
Figure 11: njRAT reaching out to its C2 server
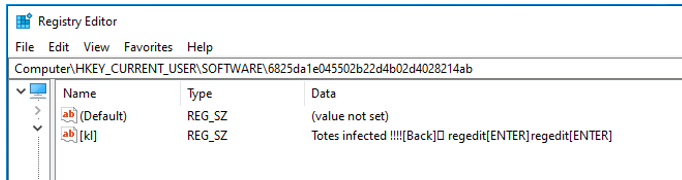
To allow the malware’s keylogging activity to begin, a registry key is created under HKEY_CURRENT_USER. All keystrokes entered by the user are recorded here:
Figure 12: Registry key which logs keystrokes
Data that has been collected is base64 encoded and formatted for exfiltration by the inf() method:
Figure 13: Snippet of inf() method
Figure 14: Formatted data for exfiltration
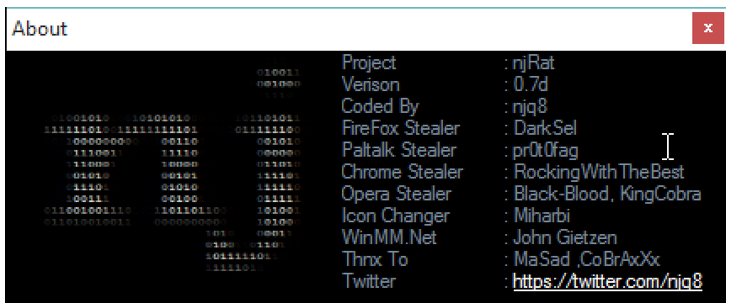
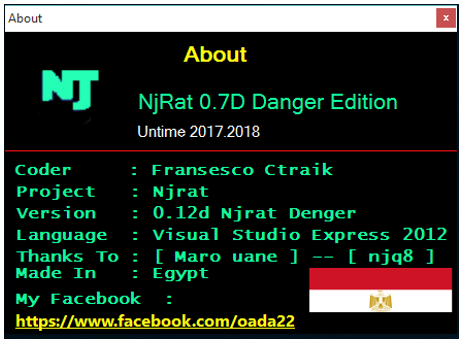
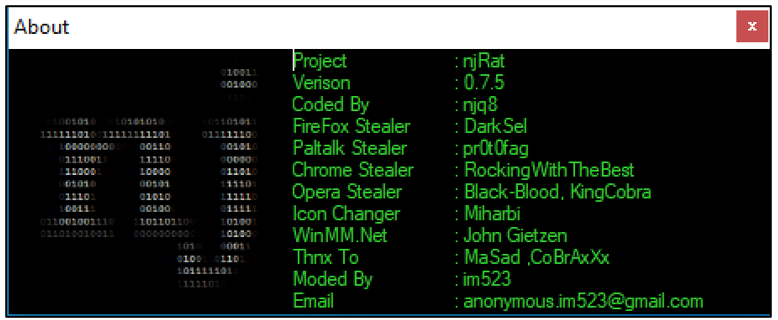
njRAT version 0.7d by njq8 was examined as part of this report:
Figure 15: njRAT v0.7d “About” information
The njRAT application provides a clean interface for an attacker to create their payload and to interact with infected machines.
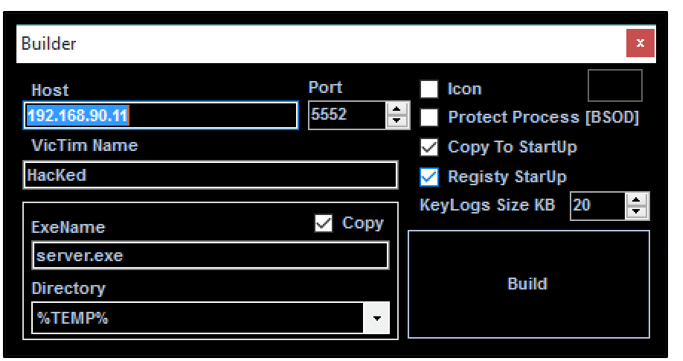
The builder even provides options to customize the backdoor payload:
Figure 16: njRAT builder
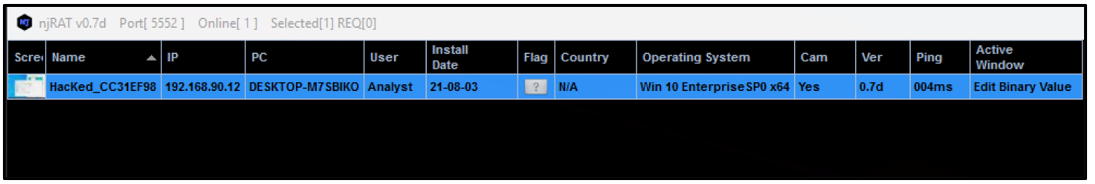
Any infected machine can be managed from the dashboard:
Figure 17: njRAT dashboard
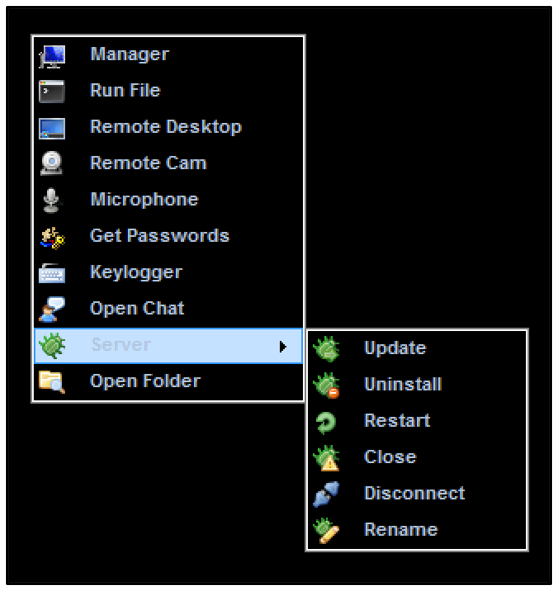
Here, we can see options available to the attacker:
Figure 18: njRAT functions
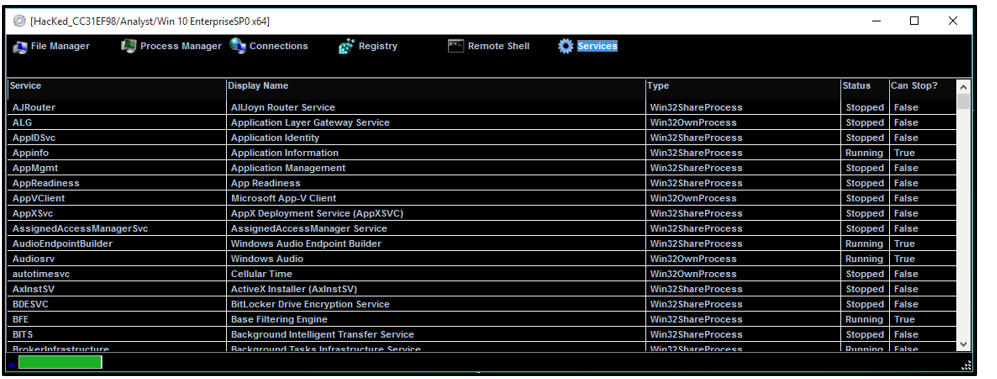
The manager component permits the user to modify or delete files, processes, connections, registry keys or services. A remote shell can also be launched:
Figure 19: njRAT manager
The keylogger option displays any exfiltrated keystrokes captured:
Figure 20: njRAT displaying keystrokes logged
“Open Chat” opens a dialogue box between the attacker and the victim:
Figure 21: njRAT chat function
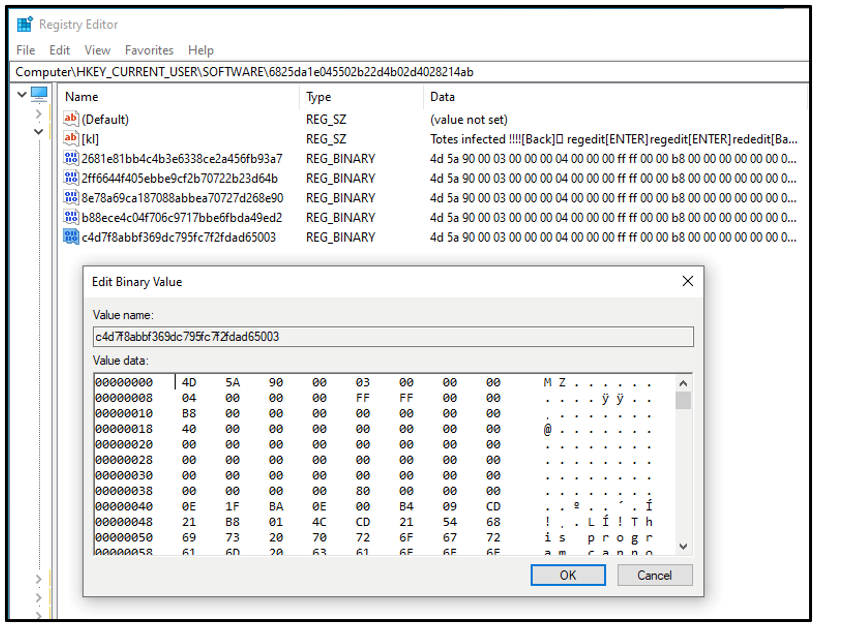
To engage with the client machine, .NET compiled Portable Executable (PE) files are deployed by the C2 server. The malicious components are stored in the victim’s registry to help evade detection:
Figure 22: PE files stored in registry
The registry keys in the image above correspond to the following filenames and functions
- b88ece4c04f706c9717bbe6fbda49ed2 - pw.dll - password grabber
- 2681e81bb4c4b3e6338ce2a456fb93a7 - sc2.dll - remote desktop
- c4d7f8abbf369dc795fc7f2fdad65003 - cam.dll - remote camera
- 2ff6644f405ebbe9cf2b70722b23d64b - mic.dll - remote microphone
- 8e78a69ca187088abbea70727d268e90 - ch.dll - chat function
The attacker can also choose to uninstall the njRAT backdoor if they so wish. This will remove all files dropped and registry keys created, eliminating any trace of the infection.
The Prevalence of njRAT
Although njRAT is nearly a decade old, it is still one of the most prevalent backdoor tools in the threat landscape. Numerous tutorials and YouTube videos about njRAT exist, making the tool accessible to users of all skill levels. The RAT provides a solid feature set, and as it was developed using the Microsoft .NET framework, it benefits from the high availability of .NET obfuscators.
Over time, several modified versions of the njRAT tool have been released. These versions offer additional functionality. Popular variants of this backdoor (“collect ‘em all!”) include:
- njRAT 0.7d Danger Edition
- njRAT 0.7d Golden Edition
- njRAT 0.7d Green Edition
- njRAT Lime Edition
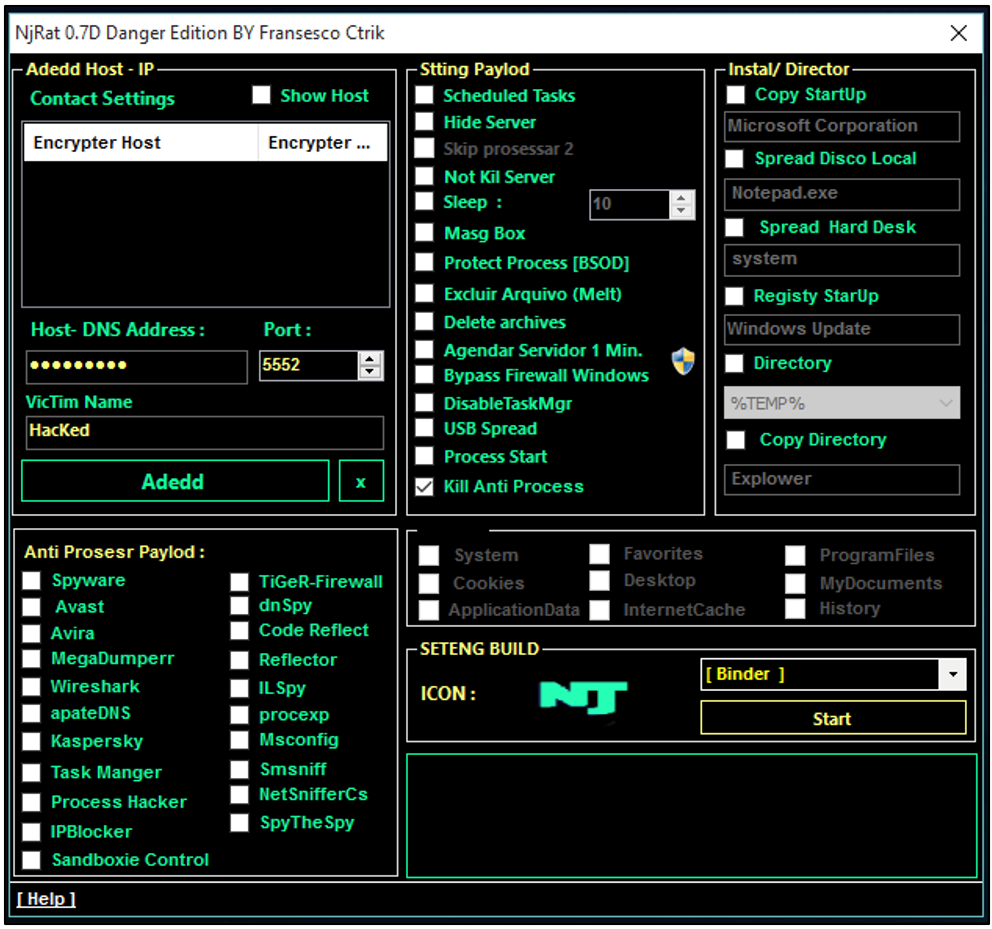
Figure 23: njRAT Danger Edition
Figure 24: njRAT v0.7d Danger Edition, displaying additional functionality
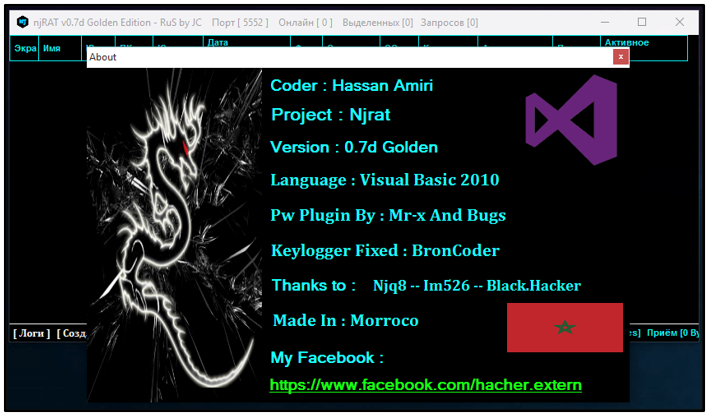
Figure 25: njRAT 0.7d Golden Edition
Figure 26: njRAT 0.7d Green Edition
YARA Rule
The following YARA rule was authored by the BlackBerry Threat Research Team to catch the threat described in this document:
import "pe"
rule Mal_Win_Backdoor_NjRAT {
meta:
description = "NjRAT backdoor"
author = "BlackBerry Threat Research"
date = "2021-07"
strings:
$s1 = "Software\\Microsoft\\Windows\\CurrentVersion\\Run" wide
$s2 = "[ENTER]" wide
$s3 = "netsh firewall add allowedprogram" wide
$s4 = "cmd.exe /c ping 0 -n 2 & del" wide
$s5 = "SEE_MASK_NOZONECHECKS" wide
$s6 = "apateDNS" wide
$s7 = "TiGeR-Firewall" wide
$s8 = "processhacker" wide
$s9 = "Download ERROR" wide
$s10 = "Update ERROR" wide
$s11 = "ToBase64String" ascii
$s12 = "Monitor" ascii
$s13 = "get_Info" ascii
$s14 = "TcpClient" ascii
$s15 = "get_Client" ascii
$s16 = "get_ProcessName" ascii
$s17 = "get_CtrlKeyDown" ascii
$s18 = "get_Application" ascii
$s19 = "get_WebServices" ascii
$s20 = "GetAntiVirus" ascii
$s21 = "USB_SP" ascii
condition:
// all strings
all of them and
// 32bit PE file
pe.is_32bit() and
// .NET compiled
pe.imports("mscoree.dll", "_CorExeMain") and
// unsigned binary
pe.number_of_signatures == 0 and
// with three sections
pe.number_of_sections == 3
|
Indicators of Compromise (IoCs)
Files Created:
- C:\%USERNAME%\svchost.exe
- C:\Users\%USERNAME%\AppData\Local\Temp\tools.exe
- C:\Users\%USERNAME%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\6825da1e045502b22d4b02d4028214ab.exe
Registry Keys Created:
- HKEY_CURRENT_USER\
Value name: di
Value data: !
- HKEY_CURRENT_USER\SOFTWARE\[A-Za-z0-9]{32}\[kl]
e.g. HKEY_CURRENT_USER\SOFTWARE\6825da1e045502b22d4b02d4028214ab\
Value name: [kl]
Value data: <logged keystrokes>
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Value name: 6825da1e045502b22d4b02d4028214ab
Value data: "C:\Users\Analyst\AppData\Local\Temp\server.exe" ..
- Computer\HKEY_CURRENT_USER\Environment
Value name: SEE_MASK_NOZONECHECKS
Value data: 1
Mutex:
- [A-Za-z0-9]|
e.g 6825da1e045502b22d4b02d4028214ab
IP:
|
BlackBerry Assistance
If you’re battling njRAT malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry® Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.