Threat Thursday: PrintNightmare on Elm Street with Magniber Ransomware

Threat actors have recently been executing ransomware attacks that exploit the latest vulnerabilities in the Windows® Print Spooler (CVE-2021-34527). The exploit takes advantage of a class of vulnerabilities commonly known as “PrintNightmare.” One malware family that has been actively leveraging these attacks is Magniber ransomware.
Discovered in 2017, Magniber uses the Magnitude exploit kit. The latest version of Magnitude, found in July 2021, has been expanded to include new vulnerabilities including PrintNightmare. Its latest campaigns target South Korean victims through malicious ad campaigns via Internet Explorer.
Operating System
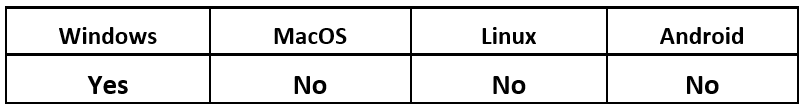
Risk & Impact

Technical Analysis
The vulnerability issues with the Windows® print spooler, initially discovered in June 2021, were believed to have been patched by Microsoft on July 6. Since then, various other bugs related to the print spooler have emerged and they remain unpatched at the time of writing.
Attacks have been mainly limited to South Korea thus far, with other APAC countries also being targeted. Security researchers anticipate that the exploitation of these bugs will become more widespread in other regions and commonly used by other attackers as time progresses.
The exploit allows attackers to perform remote code execution and achieve system privileges on targeted machines. This lets the threat actor install further programs, steal data, and create additional accounts with full user privileges.
The Nightmare Begins
Magniber’s PrintNightmare infection process begins when the victim clicks on a malicious advertisement, allowing a DLL loader to be dropped onto the target machine. The loader unpacks itself and drops a malicious payload that injects into legitimate Windows processes such as taskhost.exe (a host process for EXE and DLL files) and dwm.exe (which enables visual effects on the desktop).
Magniber performs encryption by generating a randomized 128-bit AES encryption key using a pseudo-random number generator. The malware will also create a random mutex and append it to the end of each encrypted file. In the case of this sample that is “.dstzaaeww”.
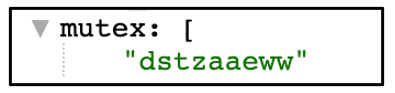
Figure 1: Mutex created
Upon execution, the malicious payload will create a registry key in the “HKCU\Software\Classes\mscfile\shell\open\command” directory, as seen below.

Figure 2: Registry key created
This registry key contains the command “vssadmin.exe Delete Shadows /all /quiet”, as pictured. This is used to delete shadow copies and backups stored on the victim’s computer, which ensures that the user can’t easily restore their encrypted files.
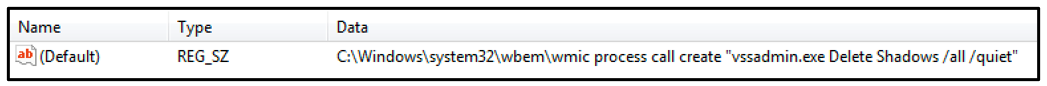
Figure 3: Command to delete shadow copies
The malware uses the Windows Computer Management Snapin Launcher file “CompMgmtLauncher.exe,” a process malware authors use to bypass User Account Controls. In this case, it is used to launch a command with escalated privileges.
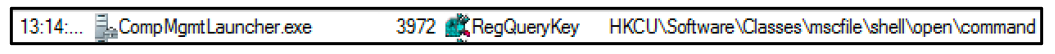
Figure 4: CompMgmtLauncher is used to run the command
This action spawns a command prompt window that uses VSSAdmin to delete shadow copies, which makes it more difficult for the victim to restore their encrypted files.
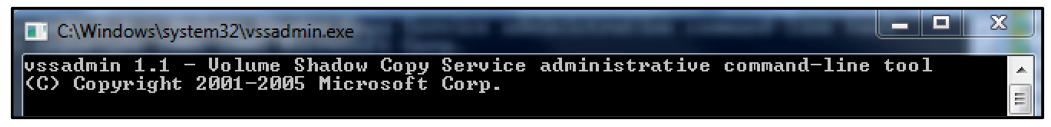
Figure 5: vssadmin launched in the cmd window
Next, Magniber drops a ransom note in the form of a text file named "readme.txt." It also appends a file extension that is unique to each variant – in this case, ".dstzaaeww" – to the victim’s encrypted files, as seen below.
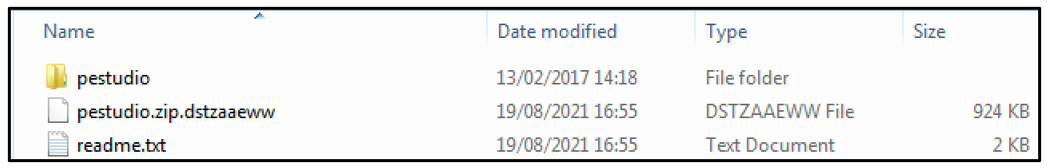
Figure 6: Appended file extension and ransom note post encryption
The process “taskhost.exe,” which contains the injected malicious payload, creates a copy of “readme.txt” in each encrypted directory, as seen in the image below. The malware also adds the ransom note to the task scheduler so that it will be displayed whenever the infected system is rebooted.
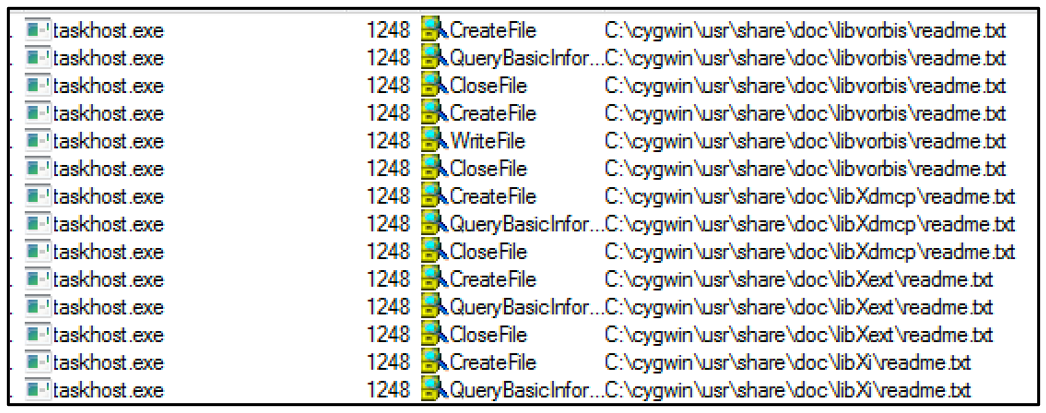
Figure 7: Malware dropping a copy of the ransom note into each encrypted directory
After encryption, the malware runs notepad.exe and displays a copy of the ransom note (see Figure 8). It states that the victim’s files have been encrypted and gives them instructions to restore their data.
The victim is given a web address to access via Tor browser, as well as four other addresses that can be accessed by a regular browser, to reach a payment page. These URLs are unique to each victim and expire after 30 minutes. The malware also automatically launches one of these payment sites in the victims’ default web browser.
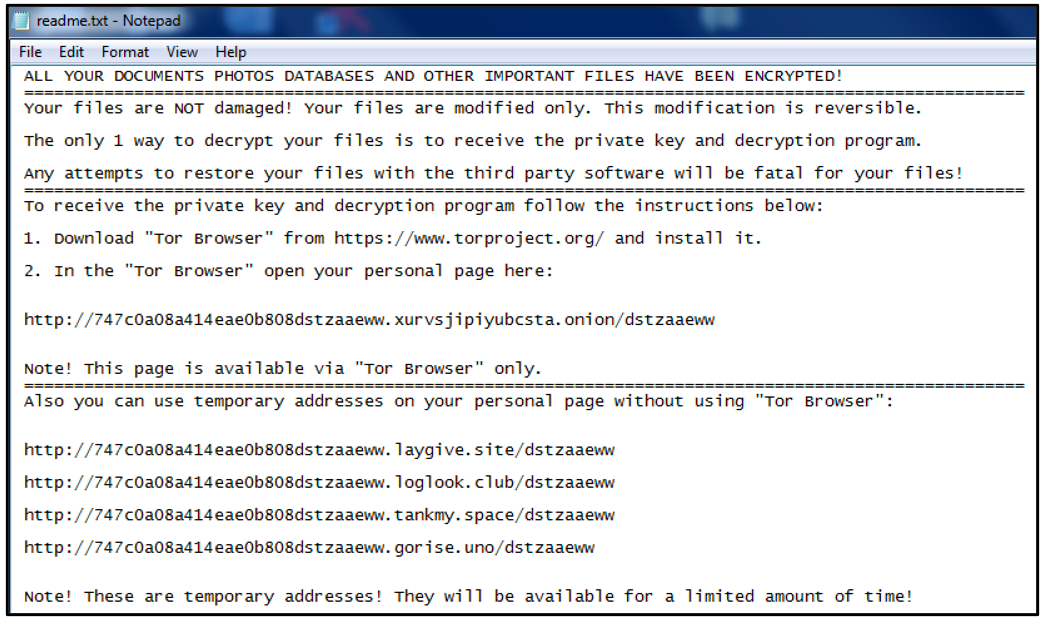
Figure 8: "Readme.txt" ransom note with payment instructions
During BlackBerry researchers’ analysis, going to a payment site resulted in a timeout, suggesting that the domains were no longer active.
Figure 9: Payment site unreachable
Analysis of one of the payment/decryption sites used by the ransomware was carried out through open source intelligence (OSINT). Upon reaching the site, the victim is alerted that their documents, photos, databases, and other important files have been encrypted.
The site instructs the victim to purchase software called “My Decryptor” to retrieve their files. All transactions are to be performed via bitcoin, with the charge being BTC 0.200 (approximately $10,000 USD at the time of writing). It alerts the victim that this is a “Special Price” and that after five days the charge will double to BTC 0.400.
The website also offers the victim the chance to decrypt one file for free, as a demonstration to prove that decryption is possible and to entice them into paying the ransom. The maximum file upload size for the free decryption demo is 2048 kilobytes.
YARA Rule
The following YARA rule was authored by the BlackBerry Research & Intelligence Team to catch the threat described in this document:
import "pe" rule Magniber_Ransomware { strings: condition: } |
Indicators of Compromise (IoCs)
Created
Deleted
SHA
Registry
Network URL
|
BlackBerry Assistance
If you’re battling Magniber ransomware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you with around-the-clock support, if required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
