How xLoader (AKA FormBook) Works
Background
xLoader is an information-stealing malware targeting both macOS® and Windows®. Previously sold on underground forums under the name FormBook, xLoader surfaced in early 2020 shortly after FormBook was shut down by its author.
xLoader is sold under a Malware-as-a-Service (MaaS) agreement. Subscribers have access to the administrative panel and executable builds for both Windows and macOS. The authors of xLoader retain full control of command-and-control (C2) infrastructure and malware builds for each target environment.
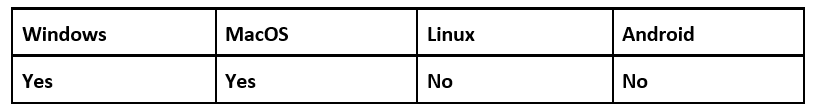
Operating System
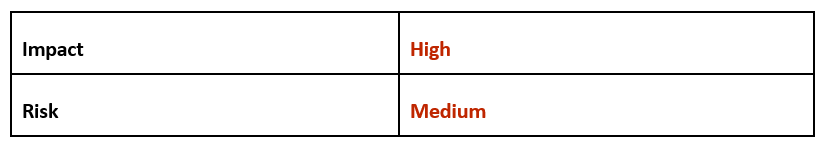
Risk & Impact
Technical Analysis
For this report, we analyzed a Windows build of xLoader.
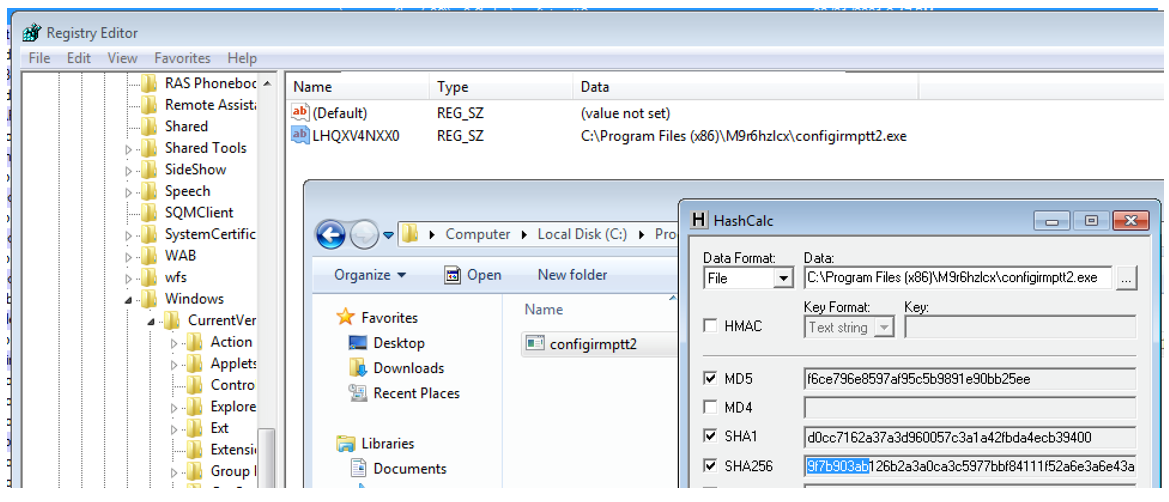
Sample hash: 9f7b903ab126b2a3a0ca3c5977bbf84111f52a6e3a6e43aa127763e1a46b8f2d
The file is a 32-bit Windows executable, which shows a compile timestamp in 2001. Given what we know of xLoader’s history, this is clearly a false date and an indication of this threat’s evasive behavior.
Basic static analysis reveals more abnormal features:
1. Zero imported libraries and functions
2. No data directory entries
3. A single executable “.text” section
4. A very small number of legible strings
This sample is a very feature-limited build. Perhaps the author adopted a “less is more” mindset, believing that a reduced analysis “surface” would help to avoid suspicion. When placed under the analysis microscope, this decision was largely counter-productive as the malware’s simplicity only serves to highlight its unusual features.
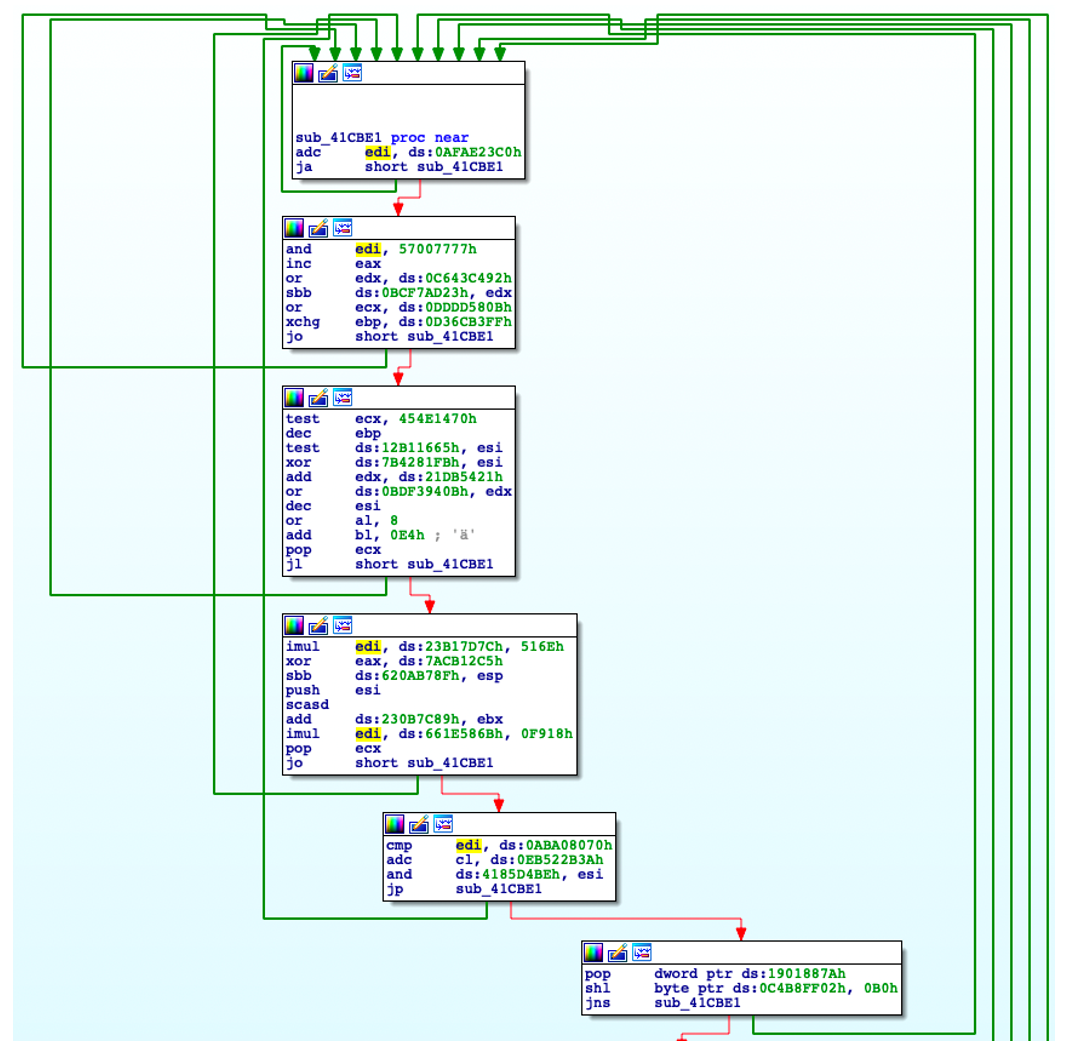
Disassembly shows the code is heavily obfuscated:
Figure 1: Obfuscated code flow within the xLoader binary
Turning to dynamic analysis, when xLoader is launched, it will first manually load ntdll.dll from disk. This approach of manual mapping is an evasive technique that aims to bypass hooks put in place by (poorly implemented) endpoint protection and automated malware analysis environments.
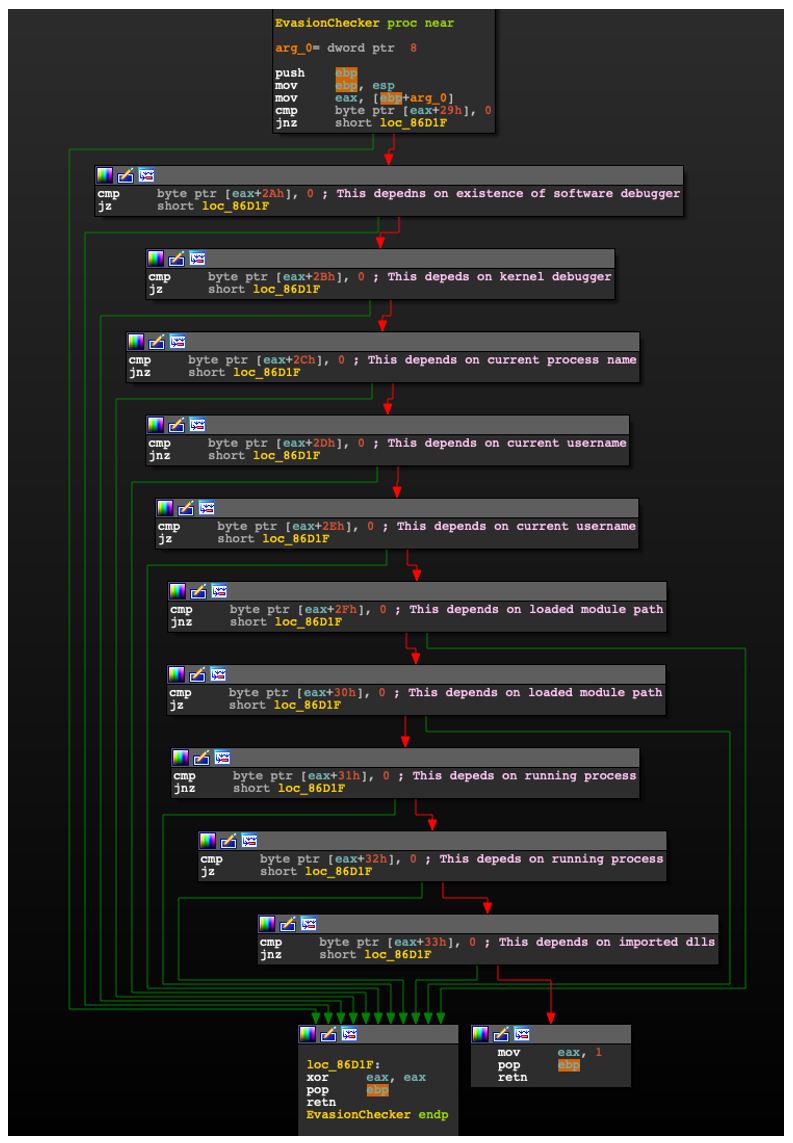
With access to ntdll, xLoader performs a battery of anti-analysis checks. This includes looking for the following conditions:
1. The presence of a user-mode debugger
2. The presence of a kernel-mode debugger
3. Execution timing checks (rdtsc)
4. The presence of blacklisted process names
5. The presence of blacklisted modules
6. The presence of blacklisted usernames
7. The Thread Environment Block (TEB) Wow32Reserved field points to a 64-bit module
As this last point is a bit more complicated, let’s investigate it a little further.
In this instance, xLoader is a 32-bit process. Under normal operation, Wow32Reserved in the TEB resolves to a function located in wow64cpu.dll. xLoader will validate the PE header of whatever Wow32Reserved points to, and confirm that the expected offset for PE “Magic Number” is 0x20B, indicating a 64-bit (PE32+) module.
Any naïve attempts to intercept API calls made by xLoader, by overwriting Wow32Reserved, would likely be met with having it point to a user allocated block of memory containing shellcode. This would lack the proper PE header and expected “Magic Number” value.
The success or failure of each of the seven anti-analysis checks listed above is recorded in a 16-byte field. Once all checks are completed, the hash value of this field is used to decrypt API strings. Rudimentary attempts to bypass the checks result in incorrect decryption and deliberate self-destruction by way of an unhandled exception.
Figure 2: Roll-call of completed anti-analysis checks employed by xLoader to ward off unwanted attention
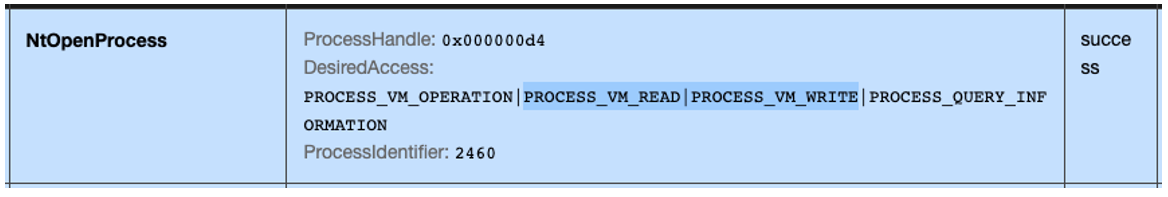
Once environmental checks are completed, xLoader obtains a process handle to Windows’ explorer.exe (ID 2460 in the below image). The open process request specifically includes permission to read or write memory, which is a tell-tale sign of imminent remote code injection:
Figure 3: Request to open a process with read and write access rights
In this scenario, code injection is performed by way of section objects and shared memory views, as well as API calls to NtOpenThread, SetThreadContext, and NtResumeThread.
The goal of code injection is to spawn a new, legitimate Windows process that will act as an unwitting host for a second round of code injection. Legitimate Windows processes launched by a user during regular operations will have explorer.exe as the parent, thus xLoader is doing its best to “blend in.”
xLoader chooses a process at random from an internal list:
svchost.exe
msiexec.exe
wuauclt.exe
lsass.exe
wlanext.exe
msg.exe
lsm.exe
dwm.exe
help.exe
chkdsk.exe
cmmon32.exe
nbtstat.exe
spoolsv.exe
|
cmstp.exe
colorcpl.exe
cscript.exe
explorer.exe
WWAHost.exe
ipconfig.exe
msdt.exe
mstsc.exe
NAPSTAT.EXE
netsh.exe
NETSTAT.EXE
raserver.exe
wscript.exe
|
taskhost.exe
rundll32.exe
systray.exe
audiodg.exe
wininit.exe
services.exe
autochk.exe
autoconv.exe
autofmt.exe
wuapp.exe
cmd.exe
rdpclip.exe
control.exe
|
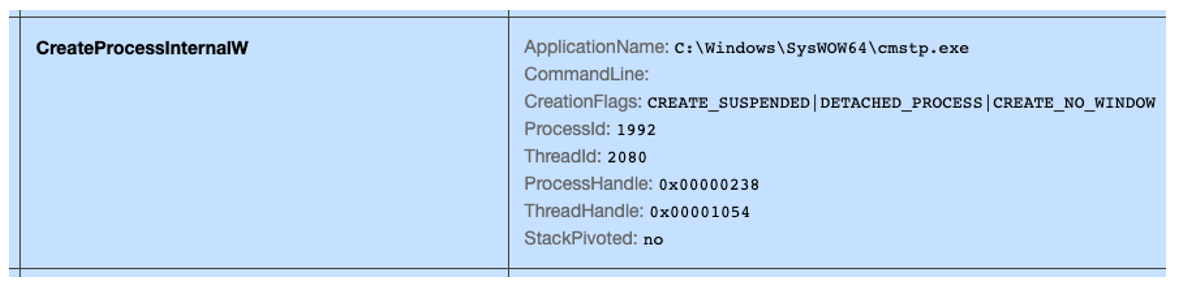
Adopting a similar approach as before, the launched process is created in a suspended state. It is then appropriated through use of a section object and a shared view, as well as API calls to SetThreadContext and NtResumeThread:
Figure 4: The final benign process launched in a suspended state
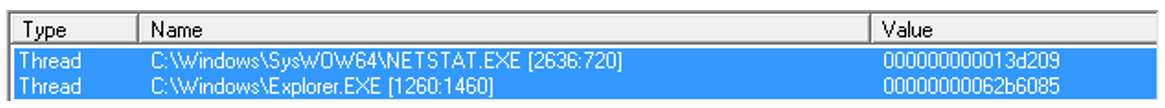
Under a separate invocation of xLoader, a scan of the active processes in the analysis environment reveals two suspicious instances, with threads of execution having an unusual origin:
Figure 5: Injected threads with suspicious origins
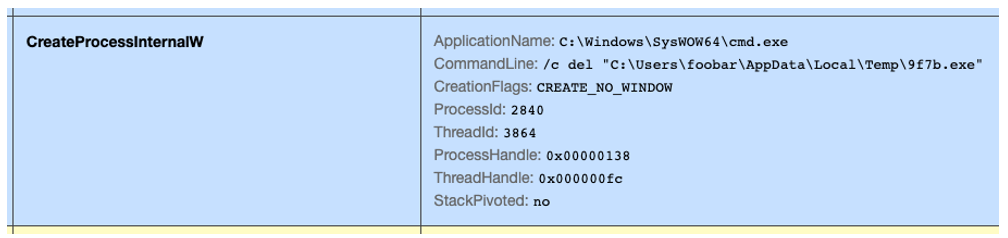
With the chain of startup process-injection completed, xLoader deletes itself from disk by invoking cmd.exe:
Figure 6: Self-deletion using cmd.exe
Persistence
Persistence is achieved using the Windows registry, by creating an entry in the HKey_Current_User hive: HKCU\Software\Microsoft\Windows\CurrentVersion\Run\<RANDOM> REG_SZ
This entry points to a copy of itself dropped in a randomly-named subfolder of C:\Program Files (x86):
Figure 7: Persistence via Windows Registry HKCU hive
Command & Control:
Handling of C2 requests remains the responsibility of the first-stage code running inside explorer.exe. The initial check-in with the channel comprises the following basic host information:
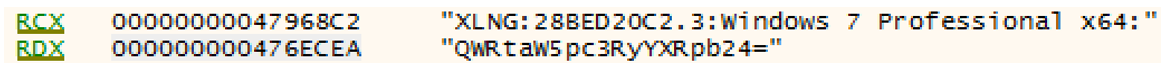
1. Handshake bytes (“XLNG”)
2. Hash of the user’s Windows Security Identifier (SID) (“28BED20C”)
3. Version of xLoader (“2.3”)
4. Operating system version and “bitness” (x64)
5. Username, Base64 encoded
Figure 8: Execution context included in the initial C2 POST check-in
This host “fingerprint” is encrypted and Base64 encoded prior to transmission.
Repeated sandbox analysis shows xLoader randomly selecting 16 C2 domains from an embedded pool of 43, with only one being the genuine C2 host. Other domains may be included, to make C2 traffic less obvious, or harder to identify against a backdrop of benign HTTP requests. Each domain in the set is contacted an equal amount in a round-robin fashion. Check-in attempts are made at five-second intervals and continue indefinitely.
The campaign ID for the analyzed build is “ipa8,” which is included in the GET request:
Figure 9: GET request to xLoader C2 with encoded host identification
When check-in succeeds, xLoader can be instructed to:
- Download and launch additional payloads
- Upload screenshots
- Intercept and steal user credentials or cookies
- Commence keystroke logging
- Terminate and uninstall
- Steal clipboard contents
One Tool to Bind Them
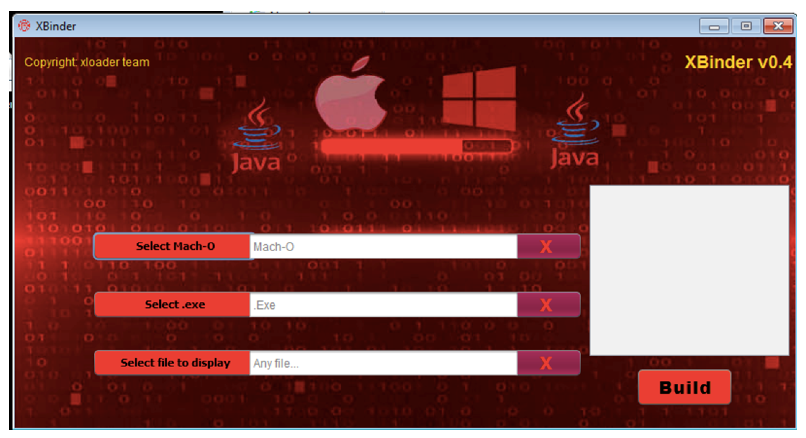
Subscription to xLoader includes access to a free Java-based tool called xBinder, that combines Windows and macOS executables into a single, portable .jar file. Given Java’s prevalence, this is an attractive feature. It makes crafting email attachments for social engineering or watering hole downloads possible avenues for attack.
Within the .jar file, the macOS and Windows executables are bundled and encrypted using AES with a static key. When launched, a runtime probe identifies the host operating system. It then drops and executes the corresponding payload.
A version of xBinder can be found in VirusTotal, indicating a possible leak or accidental upload. A handful of analyzed xBinder-generated .jar files contained benign macOS command line tools, such as “/bin/ls,” together with malicious Windows executables from these different families:
- Azorult (info stealer)
- Snake (info stealer)
- Neshta (file infector)
- Guloader (downloader)
This mismatched bundling of benign files together with malicious code from disparate malware families suggests unsanctioned use of xBinder by groups or individuals, rather than paying subscribers.
Figure 10: xBinder tool for creating Mac and Windows .jar files
Conclusion
xLoader promotes itself among the rank-and-file of underground MaaS offerings as cheap, highly functional and resilient. With its evasive and mature binaries for both macOS and Windows, together with the provision of a free binding tool that caters to more indiscriminate targeting, xLoader’s offering has appeal for both fledgling cyber criminals and larger, more organized groups.
YARA Rule
The following YARA rule was authored by the BlackBerry Research & Intelligence Team to catch the threat described in this document:
import "pe"
rule xLoaderInfoStealer
{
strings:
$hx_enc_buff = { 57 50 E8 B0 E6 FF FF 8B F8 83 C4 04 80 3F 55 75 79 80 7F 01 8B 75 73 }
condition:
pe.is_pe and
pe.number_of_imported_functions == 0 and
pe.number_of_imports == 0 and
all of ($hx*)
}
|
Indicators of Compromise (IoCs)
Network:
www[.]abolad[.]com
www[.]addisonbleu[.]com
www[.]am-conseil-communication[.]com
www[.]askaboutaduhelm[.]com
www[.]astyaviewer[.]com
www[.]bainrix[.]com
www[.]beaumontcycleworks[.]com
www[.]blockchainhub360[.]com
www[.]calerie[.]coffee
www[.]calvarirumba[.]com
www[.]celiktarim[.]com
www[.]dailygame168[.]com
www[.]desarrollosolucionesnavarro[.]com (legitimate C2 domain)
www[.]edwardsrealtyfl[.]rentals
www[.]golfwifi[.]net
www[.]guapandglo[.]com
www[.]hydrarobuxobby[.]com
www[.]instrumentum[.]store
www[.]kinnonstudio[.]com
www[.]lanerbo[.]com
www[.]littlescampers[.]com
www[.]mapopi[.]com
www[.]miotir[.]com
www[.]mnavn[.]com
www[.]northwayenterprise[.]com
www[.]okwideus[.]com
www[.]oqity[.]com
www[.]pastelpastrybakery[.]com
www[.]plastings[.]com
www[.]poolsnation[.]com
www[.]privedenim[.]com
www[.]registernowhd[.]xyz
www[.]rixmusic[.]com
www[.]royalposhpups[.]com
www[.]rwaafd[.]com
www[.]sazekav[.]com
www[.]serialmixer[.]icu
www[.]tailored2fit[.]online
www[.]thebandaiderepair[.]com
www[.]therightmilitia[.]com
www[.]theutahhomestore[.]com
www[.]visions-agency[.]com
www[.]votekellykitashima[.]com
www[.]xiang-life[.]net
Registry:
HKCU\Software\Microsoft\CurrentVersion\Run\<RANDOM> (REG_SZ)
File system:
C:\Program Files (x86)\<RANDOM>\<Random>.exe
SHA256:
9f7b903ab126b2a3a0ca3c5977bbf84111f52a6e3a6e43aa127763e1a46b8f2d (xLoader PE)
693d6f0ac1e3f5e3e5b68c45d2a77bcc9d8976f7b091d5bfa1e719ad8b97fd25 (xBinder JAR)
|
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you by providing around-the-clock support, if required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
For more information about this threat, watch our new demo video, BlackBerry vs. xLoader Infostealer.
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.