Threat Thursday: Jennlog Malicious Loader
Summary
A malicious loader named Jennlog has recently been used by an Iranian threat actor called Agrius in a ransomware attack against a university in Israel. The malware was written in .NET assembly language and was designed to target Windows® machines.
The loader hides its payload as a resource that initially appears to be a log file. Instead, the resource contains both the malicious payload (in this case Orcus RAT) and the malware’s execution configuration. As an anti-analysis method, this loader checks for the presence of virtual machines (VMs) and sandboxes before unpacking its malicious payload, as this might indicate that it is being run on a researcher’s machine.
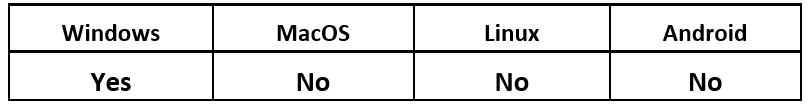
Operating System
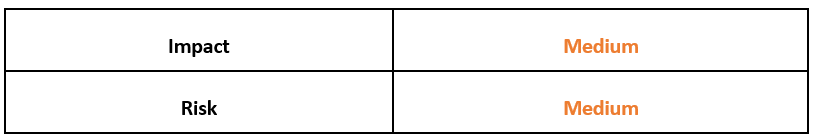
Risk & Impact
Technical Analysis
Two nearly identical variants of the loader have been uploaded to VirusTotal. The main difference between the two is that one loads the Apostle ransomware, and the other is used to load a variant of the Orcus RAT malware.
For this report, we analyzed a version of Jennlog that loads and executes the Orcus RAT Infostealer.
Sample Hash: 14659857df1753f720ac797a43a9c3f3e241c3df762de7f50bbbae00feb818c9.
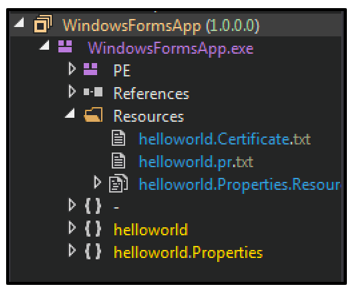
The loader is a 32-bit Windows executable whose name was chosen by SentinelLabs due to a feature of how it loads its payloads. These payloads are hidden as a resource, where they masquerade as log files, and are then extracted by searching for the keyword separator "Jennifer”. In the case of this sample, the payload is contained within the embedded resource called “helloworld.properties.resource”, as shown in the image below.
Figure 1 - Resources containing payload
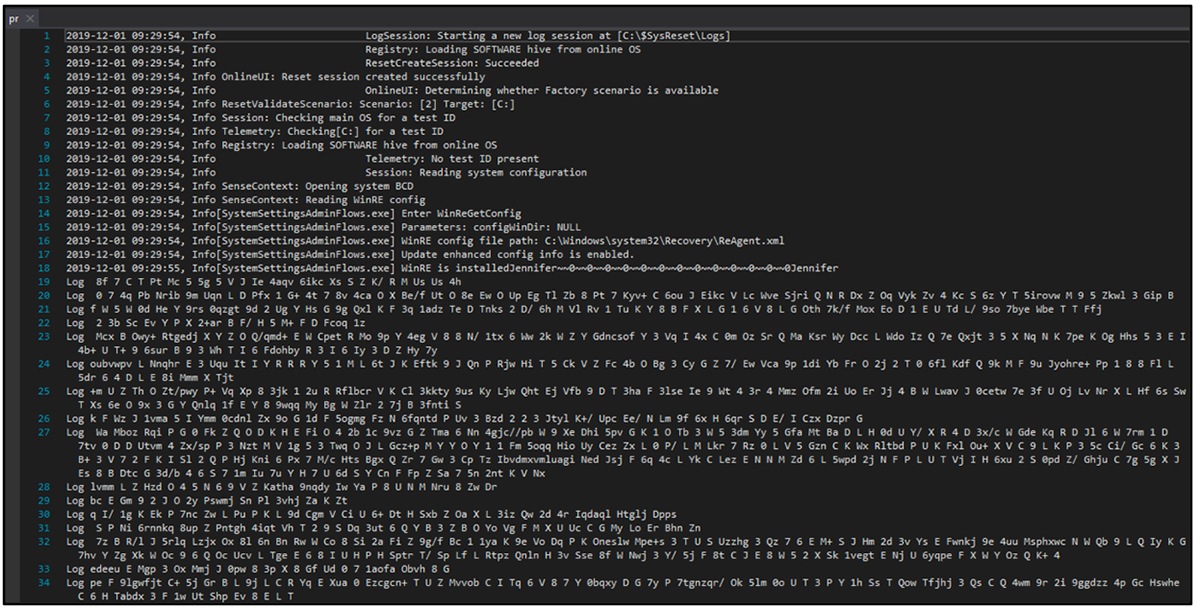
At first glance, the resource appears to be a log file, when in fact it contains both the malicious payload (Orcus RAT) and the malware’s execution configuration.
Figure 2 - "pr.txt” resource that masquerades as a log file
Before unpacking the malicious binary, the loader performs several checks. Its first action is to fingerprint the victim’s system, gathering information such as processor and video controller information, physical address, and system BIOS information.
The loader contains anti-VM and anti-sandbox functionality to impede analysis and avoid detection. In the function shown below, the malware will search the victim’s system for the presence of several popular virtual machine applications, such as the following:
- VMWare
- VirtualBox
- Virtual Machine Additions
If the presence of a virtual environment is detected on the infected machine, the process execution will be stopped.
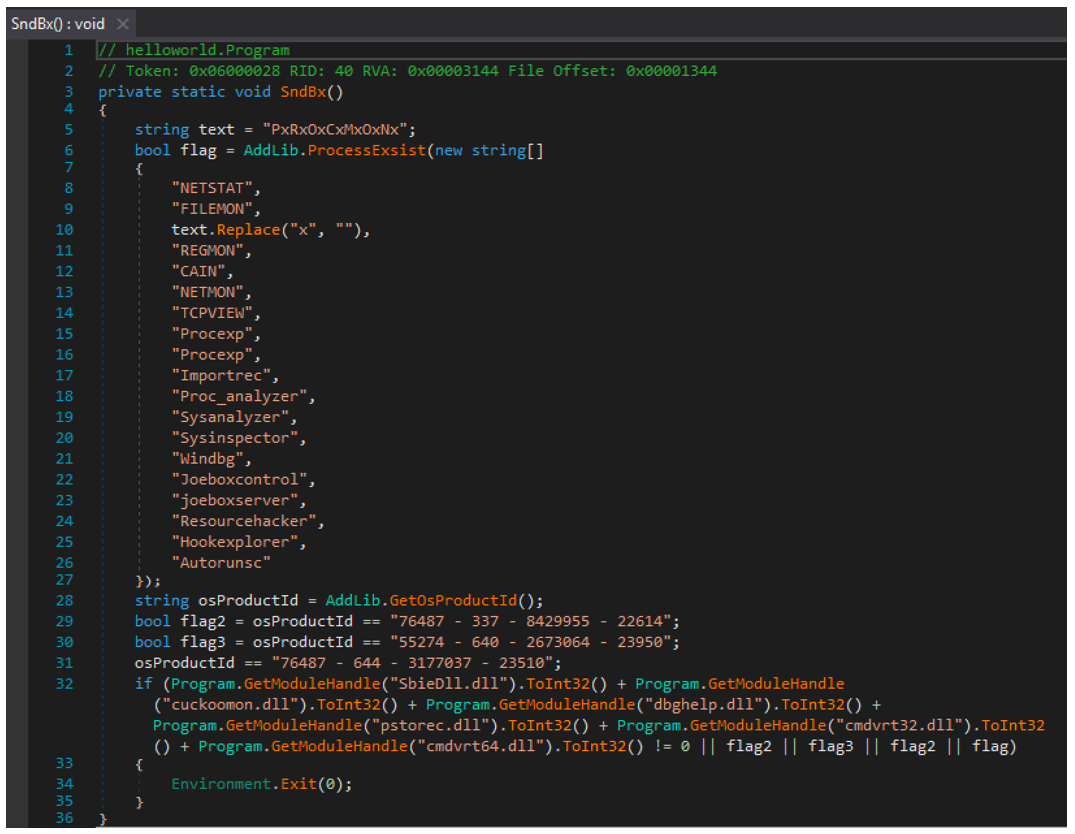
Similarly, the loader will then use the function "SndBx” to check the victim’s machine for indications that it is running within a sandbox environment, using indicative process names as well as handles for specific DLLs.
Figure 3 - Checks to see if file is being run in a sandbox environment
The loader also contains the functionality to disable Task Manager. This is done by modifying the registry key “Software\Microsoft\Windows\CurrentVersion\Policies\SystemDisableTskMgr” to the value of 1.
Payload
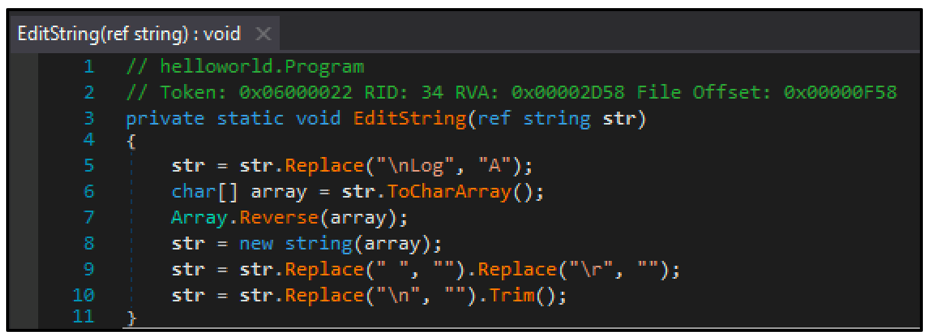
The loader decrypts the payload stored in the resource section using a unique technique, looking for the separator word “Jennifer”. To unpack the binary, the “EditString” function is used to perform string manipulation. As can be seen in the screenshot below, all string instances of “\nLog” are replaced with “A”. Strings are also reversed, and all whitespaces are removed.
Figure 4 - 'EditString' function is used to unpack binary
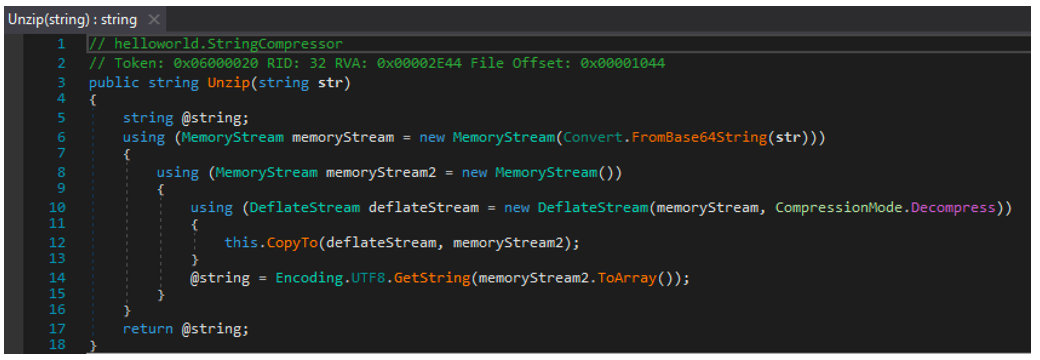
The result of this string manipulation leaves base64 encoded content, which is decompressed using the ”StringCompressor.unzip" function shown below. Following this, the “EditString” function is repeated and the remaining data is decrypted using the RC4 stream cipher and a predefined key.
Figure 5 - StringCompressor function
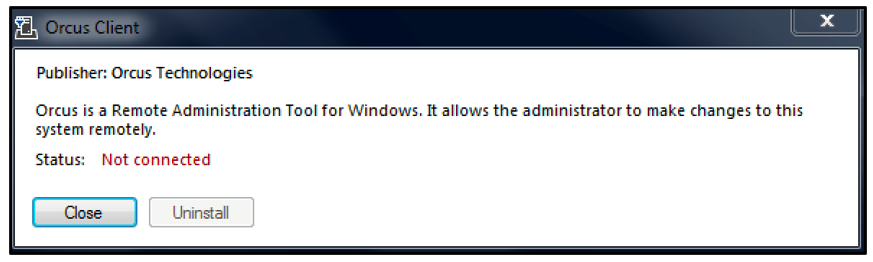
Once de-obfuscated and extracted, the malicious payload is loaded into memory. The victim is presented with the Orcus Client screen. Orcus portrays itself as a legitimate remote access utility, however, that is far from reality.
Orcus RAT is a Remote Access Trojan that, apart from having the usual RAT functionality, also has a modular aspect that enables attackers to create their own plugins via a custom development library. This modular functionality makes it one of the most powerful and dangerous threats in its class.
Figure 6 – Orcus RAT Client
Upon execution, Orcus RAT can grab screenshots of user activity, activate the webcam, log keystrokes, scrape passwords, record audio, perform real-time scripting, and steal user data.
The functionality that most clearly separates this malware from a legitimate remote access utility is the incorporation of a set of command modules dubbed “FunActions”. These commands include the functionality to swap mouse buttons, trigger a bluescreen on the victim’s machine, turn off the monitor, change desktop wallpaper, and block user input.
A full list of Orcus RATs malicious functionality is contained in the following table.
Reverse Proxying to use host’s Internet connection
as a proxy
|
Enumerate host to obtain OS version, language, privileges, network Settings, processer, drives, BIOS, etc.
|
Load custom plugins to add additional functionality on infected host
|
List all active
TCP/UDP connections on host and process
that is running
them
|
Steal passwords from Chrome,
Firefox, FileZilla,
Internet Explorer,
WinSCP, Opera,
Thunderbird
|
Steal cookies from web browsers (Chrome,
Firefox, Yandex)
|
Play different audio files on infected host
|
Show/Hide
taskbar/desktop/clock
|
Swap/Restore mouse buttons
|
Disable/Enable Task Manager
|
Block user input
|
Change desktop wallpaper
|
Turn off the monitor
|
Trigger blue screen
|
Log
off/Shutdown/Restart host
|
Rotate monitor
|
Change keyboard layout (QWERTY,
QWERTZ,
AZERTY)
|
Open chat window to infected host
|
Execute code (C#, VB.Net, Batch) on infected host
|
Text-to-speech functionality
|
Activate microphone
|
Activate webcam
|
Take screenshots
|
Keylogging
|
Enumerate/Modify/Delete files and folders
|
Enumerate/Modify/Delete Registry keys
|
Display/Restore/Create system restore points
|
Change Windows
settings
|
Remote desktop
ability
|
Download and execute files
|
Figure 7 - Malicious functionality of Orcus RAT
Conclusion:
The customizability and evasiveness provided by the Jennlog loader make it a useful tool for any malicious threat actor. It would not come as a surprise if more attackers chose this method of malware loading in the future.
YARA Rule
The following YARA rule was authored by the BlackBerry Research & Intelligence Team to catch the threat described in this document:
import "pe"
rule Jennlog_Loader {
meta:
description = "Detects Jennlog Loader"
author = "BlackBerry Threat Research Team"
date = "2021-10-16"
license = "This Yara rule is provided under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0) and open to any user or organization, as long as you use it under this license and ensure originator credit in any derivative to The BlackBerry Research & Intelligence Team"
strings:
$s1 = "Jennifer"
$s2 = "helloworld.Certificate.txt"
$s3 = "helloworld.pr.txt"
$s4 = "0Jennifer"
$s5 = "ExecuteInstalledNodeAndDelete"
$s6 = "helloworld.Properties"
condition:
(
//PE File
uint16(0) == 0x5a4d and
// Sample is a DotNet file
pe.imports("mscoree.dll", "_CorExeMain") and
// PE Sections
pe.number_of_sections == 3 and
// Checksum is not set and does not match
pe.checksum != pe.calculate_checksum() and
//All of Strings
all of ($s*) )
}
|
Indicators of Compromise (IoCs)
SHA256:
14659857df1753f720ac797a43a9c3f3e241c3df762de7f50bbbae00feb818c9 – Jennlog loader
069686119adc13e1785cb7a425611d1ec13f33ae75962a7e50e00414209d1809 – OrcusRAT
Mutex:
\Sessions\1\BaseNamedObjects\94433e5fecd54eeea6cc9ac279093f12
Embedded URL:https://fkpageintheworld342[.]com
|
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response Team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and advanced persistent threat (APT) cases.
We have a global consulting team standing by to assist you, providing around-the-clock support where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
Want to learn more about cyber threat hunting? Check out the BlackBerry Research & Intelligence Team’s new book, Finding Beacons in the Dark: A Guide to Cyber Threat Intelligence - now available for pre-order here.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.