Threat Thursday: Karma Ransomware
Summary
Karma is fast-acting ransomware designed to quickly encrypt data on compromised machines. In the wild since mid-2021, Karma initially used the stream cipher known as ChaCha20. Recent samples have swapped this out for Salsa20, suggesting the malware is still under development.
The Karma ransom group has created a leak site named “Karma Leaks,” which is hosted via an Onion page. This site has blog-like posts that allude to infiltration of an organization’s network before deploying their ransomware, a technique which allows them to get a better sense of the value of their victim’s data before setting a ransom amount. The group also uses this site as a double-extortion ploy. Affected organizations that refuse to pay the ransom demands or that do not pay within a specific time, have their data published.
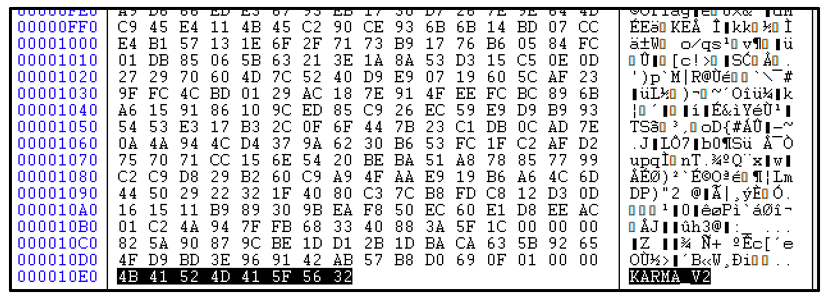
In October 2021, Karma ransomware went through an iterative change, showing rapid advancement including smaller sample-size and shifts in their encryption routine. Files encrypted by the newest version of the ransomware have the file-extension [.KARMA_V2] appended, rather than the initial [.KARMA] file-extension used in a previous version.
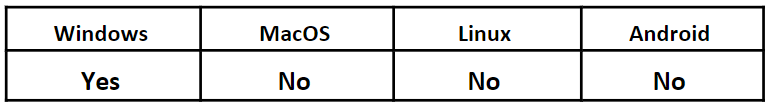
Operating System
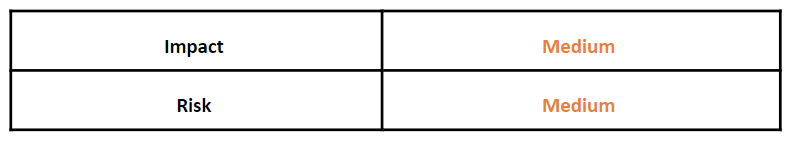
Risk & Impact
Technical Analysis
Infection Vector
The infection vector used by the Karma ransomware gang is unknown, but based on initial findings of reconnaissance performed on the victims by the threat group, it appears to vary. Once the group has established a foothold, they likely attempt to move laterally and exfiltrate any data of value. Once reconnaissance and information-stealing has concluded, they execute the Karma ransomware to encrypt victim systems that they have compromised.
File Analysis
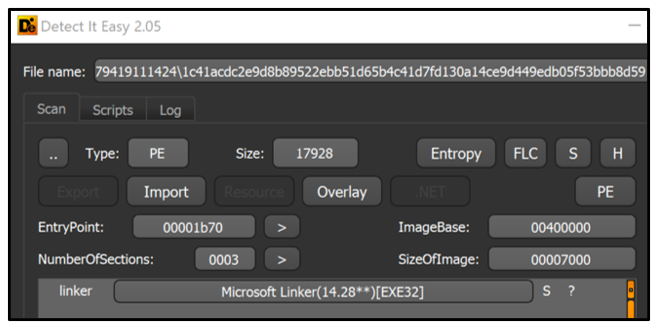
The ransomware file itself is small, with samples ranging between 15 KB and 130 KB. Despite their small size, none of the samples found in the wild were packed by digital software packers. The observed samples were all Windows® 32-bit Portable Executables (PE) with a compilation timestamp of 2021. All samples found in the wild were compiled in Microsoft® Visual C++.
Though most samples of Karma are unsigned, lacking digital certificates, at least one known sample was signed with a currently un-revoked digital signature.
Figure 1: Static information of Karma_V2 sample
As noted, Karma appears to be still under development. BlackBerry has observed a clear lateral progression between initial samples of Karma, leading up to KARMA_V2. Over a short period of time, the samples of Karma that have been analyzed became progressively smaller, shifted their encryption routine, and increased in complexity.
The initial samples of Karma contained a console pop-up box during encryption, meaning an attentive user could attempt to terminate the process before all their data was encrypted. However, given the speed of the malware’s encryption routine, it would have been difficult to act quickly enough to keep all data intact.
Figure 2: Initial console dialog box of Karma
More recently, samples contain the static string: Karma_V2. These samples share a lot of resemblance to the proceeding version, but the initial console box that was once displayed on the victim device is no longer visible. Its speed and method of encryption appear the same.
Karma Mutex
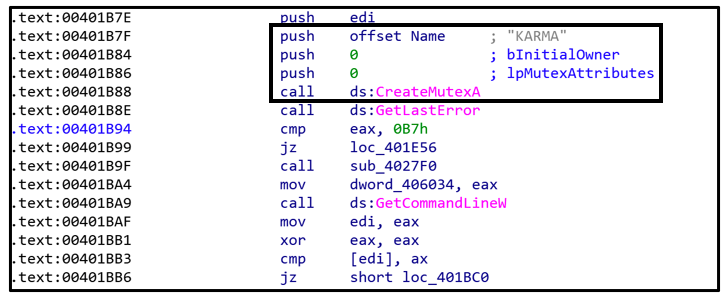
Karma_V2, like the original, initially creates a mutex called “KARMA.” This functions as a buffer to prevent another instance of the ransomware from being executed if one is already running. This is likely done to prevent re-infection, as well as double-encryption that might occur if the ransomware inadvertently executes twice.
If ransomware were to be executed twice on a system, doubly-encrypted data is likely to become un-recoverable and corrupt. This would defeat the purpose of such malware demanding a payment for decrypting and recovering the user’s data.
Figure 3: Formation of the "KARMA" mutex
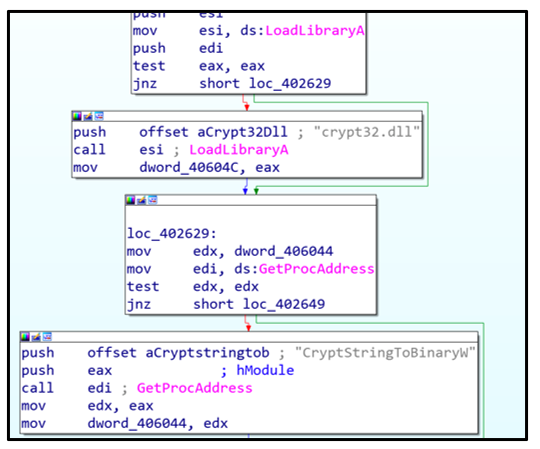
Karma calls on the use of crypt32.dll. This Dynamic-Link Library (.DLL) is a native module used to implement cryptographic messaging and certification functions with the Windows CryptoAPI. The DLL is used during encryption.
Figure 4: crypt32.dll being loaded
After loading the DLL, the malware will then iterate through all available drives connected to the victim’s device. If a logical drive is identified and verified, the malware will attempt to encrypt its contents.
Encryption
Not all samples of Karma have the same goals. Though they all operate the same, they can target different files and folders.
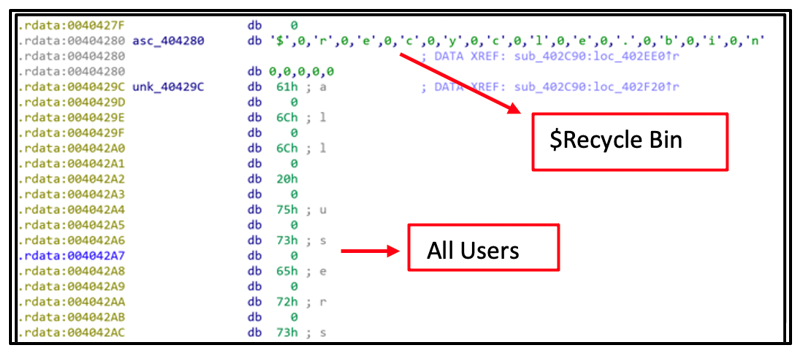
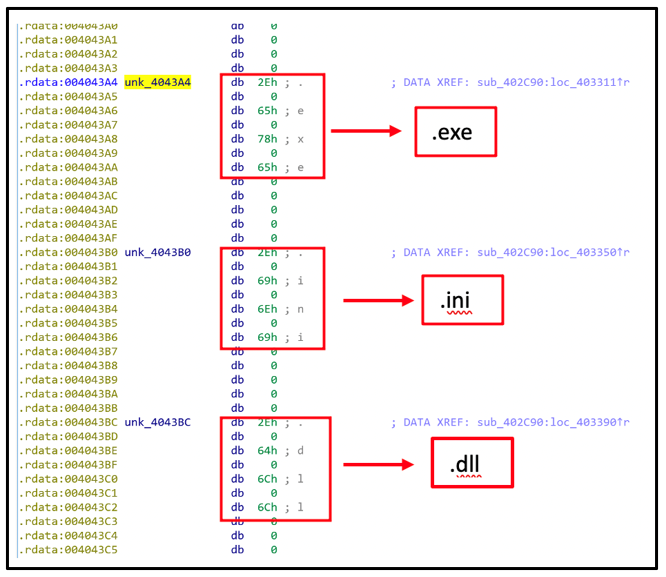
Karma samples vary in which file-extensions and folders they exclude from encrypting. This information is statically hard-coded into the malware, located in the .rdata section of each sample.
Figure 5: Static references to folder exclusions
Figure 6: These exclusions are then used by the malware when executing
These exclusions are likely included to avoid inadvertently encrypting core and critical Windows components.
Figure 7: File extension exclusion list
KARMA (ChaCha20)
SHA1:
|
a9367f36c1d2d0eb179fd27814a7ab2deba70197
|
File Size:
|
127 KB
|
Excluded Extensions:
|
- .EXE
- .LOG
- .BAT
- .INI
- .URL
- .PIF
- .MP4
- .MSI
- .LNK
|
Excluded Folder:
|
- Windows
- Program Files
- Program Files (x86)
- ProgramData
|
Ransom Extension
|
.KARMA
|
Ransom Note:
|
KARMA-AGREE.txt
|
KARMA (Salsa20)
SHA1:
|
08f1ef785d59b4822811efbc06a94df16b72fea3
|
File Size:
|
19 KB
|
Excluded Extensions:
|
|
Excluded Folder:
|
- Windows
- $Recycle Bin
- All Users
- Default User
- Public
- ProgramData
- AppData
- Program Files
- Program Files (x86)
- Default
- System Volume Information
- Searches
|
Ransom Extension:
|
KARMA
|
Ransom Note:
|
KARMA_ENCRYPTED.txt
|
KARMA_V2
SHA1:
|
338cff5f17663b7552fb0d687d3b67e9b47fca95
|
File Size:
|
18 KB
|
Excluded Extensions:
|
|
Excluded Folder:
|
- Windows
- $Recycle Bin
- All Users
- Default User
- Public
- AppData
- ProgramData
- Program Files
- Program Files (x86)
- Default
- System Volume Information
- Searches
|
Ransom Extension:
|
KARMA_V2
|
Ransom Note:
|
KARMA_V2_ENCRYPTED.txt
|
Once files are passed through the malware encryption routine, and the file-extension has been appended, the malware will add the 8 bytes of data shown below to signify successful encryption.
Figure 8: File encrypted by Karma_V2
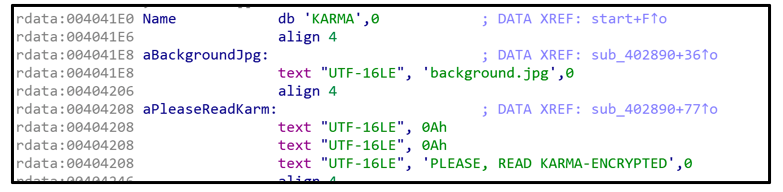
Background Change
In all samples of Karma ransomware analyzed to date, once encryption is completed, the malware creates a file called “background.jpg.” This file is generated and stored in the %Temp% directory.
Figure 9: Creating 'background.jpg'
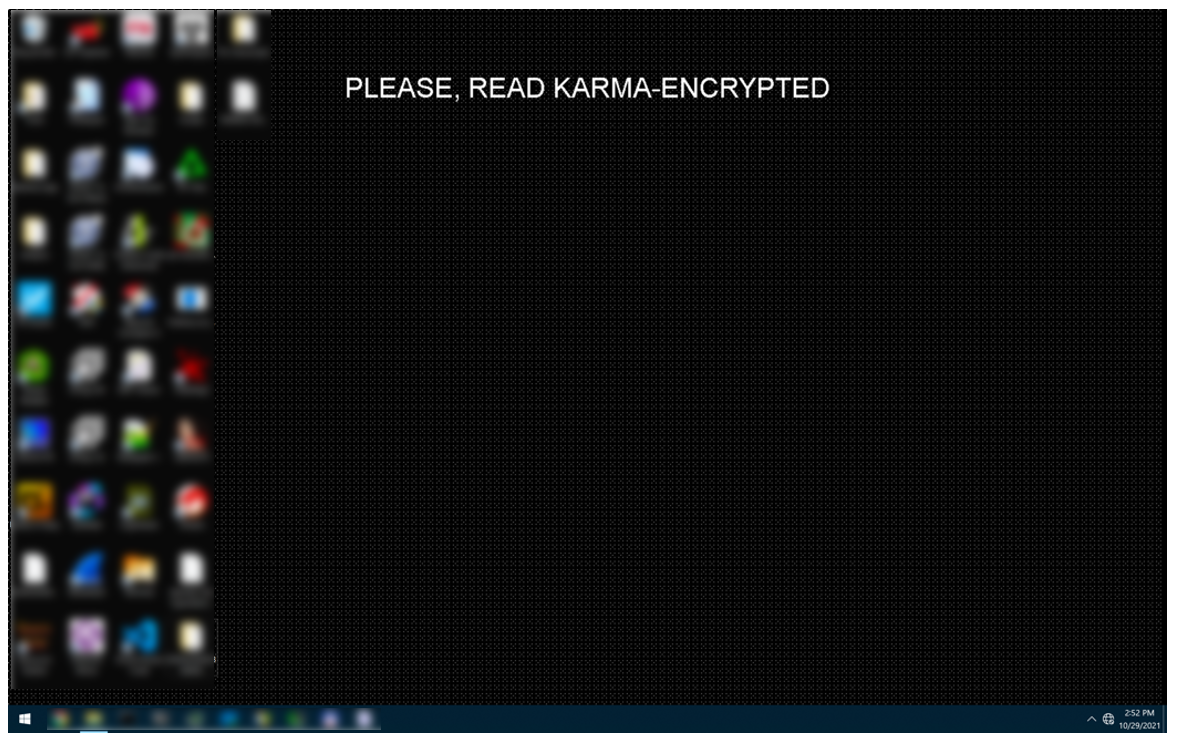
Once the malware has carried out its encryption, it will change the victim’s desktop image as shown below.
Figure 10: System affected by Karma
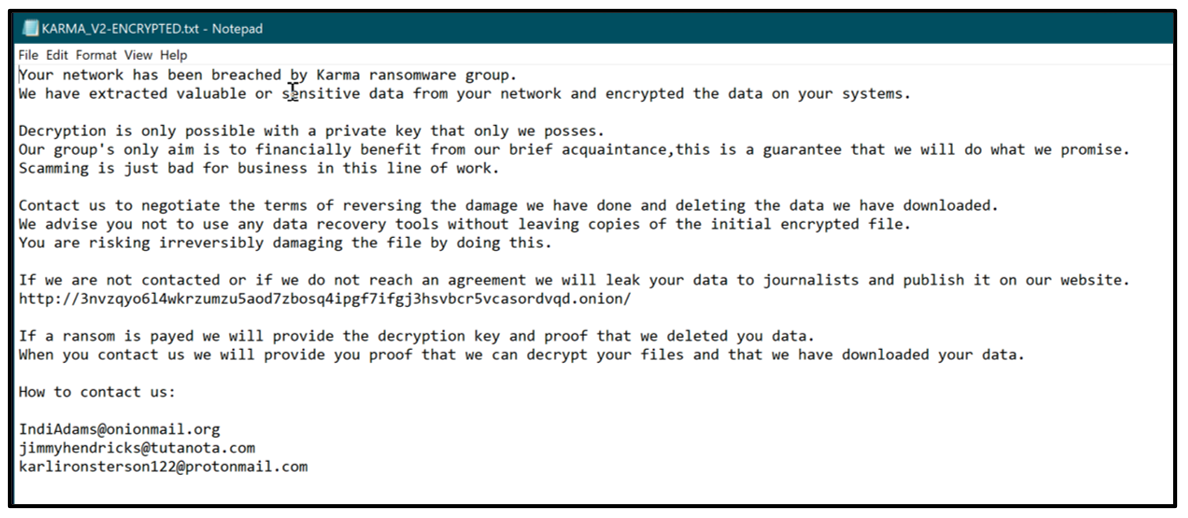
Ransom Note
Figure 11: Example of Karma ransom note
There are few deviations in the Karma ransom note. However, the formatting is generally the same across all versions.
Typically, the contents of these notes are Base-64 encoded and contained within the file’s static strings. The contents are decoded into memory before being placed into the text file KARMA-ENCRYPTED.txt or KARMA-AGREE.txt. These ransom notes are created and dropped in all folders where the malware has encrypted files.
The note contains an Onion link to the threat actor’s leak site. It also contains unique email addresses related to that specific sample of Karma.
These addresses often follow a pattern of containing at least one of each of the following email services:
- OnionMail
- Tutanota
- ProtonMail
Leak Site
While other prevalent ransomware threats have been observed selling their malicious code to other threat actors as Ransomware-as-a-Service offerings, Karma appears to be used solely by its own creators.
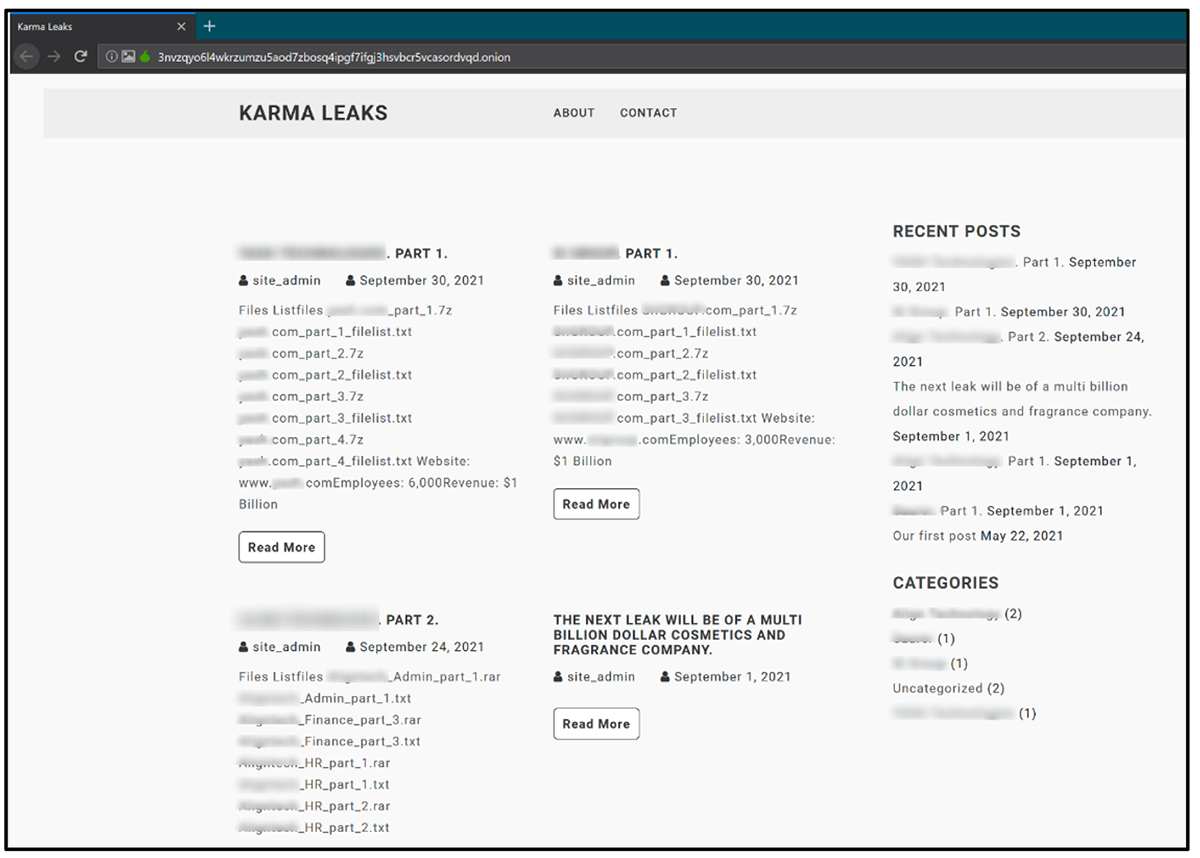
Since Karma began posting to its Onion webpage in May 2021, the ransomware threat actors have been busy populating their basic WordPress site with the names and data of victims who have refused to pay their ransom.
Figure 12: Current content of “Karma Leaks” website (redacted)
As of November 2021, the site hosts the data of four victims who have not engaged or contacted the group and therefore have had their data publicly leaked. Each post shown in Figure 12 contains multiple links to download confidential information stolen by the threat actors. The site suggests that these “double-extortion” posts would be removed if a fee is paid, which means that the true number of victims who have fallen to Karma may extend beyond this initial tally.
It appears that the Karma ransomware gang tends to target large multinational organizations; in particular, those with more than 1,000 employees and around $1 billion in revenue.
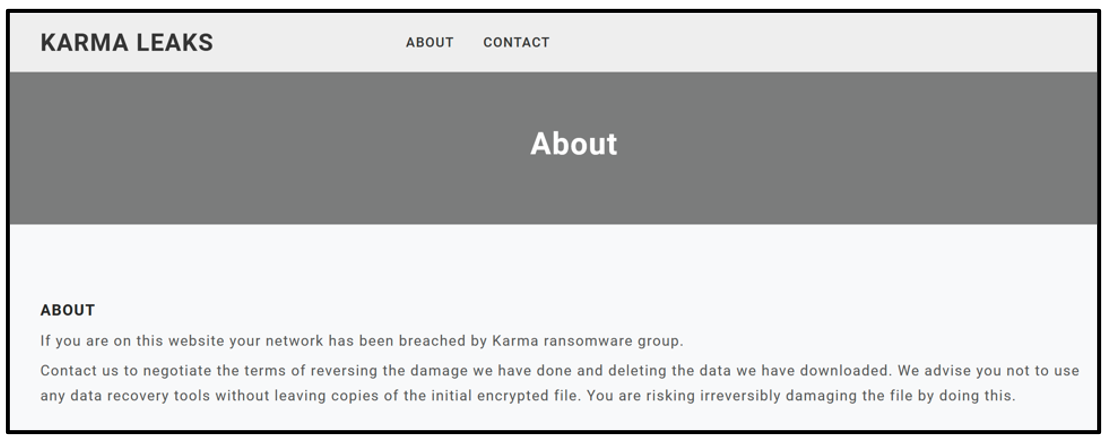
Figure 13: Karma leak site’s “About” page text
Karma’s website has a few blog-like posts about potential victims they intend to leak data from soon, and further ways to contact the gang. The “About" page shares a few additional pieces of information, as seen in Figure 13.
Neither the ransom note nor the website publicly discloses a specific ransom amount. Typically, ransomware would immediately demand a victim-specific fee or a flat-rate fee for the decryption of files.
As the Karma ransomware gang likely infiltrates organizations directly, as opposed to an RaaS model, fees could vary based on not just on the damage caused by the ransomware, but on the victim’s ability to pay and criticality of the affected data.
Conclusion
Karma ransomware is a quickly evolving and ruthless operation. Though Karma shares a lot of similarities with other known ransomware families, its rapid development and advancement in techniques makes both the malware and the threat actor behind it extremely dangerous. The use of “Karma Leaks” as a double-extortion ploy shows the threat group’s willingness to expose victims who do not pay.
With both the activity on “Karma Leaks” and the development of KARMA_V2, it appears this threat actor is spinning up its operations, and that it is actively looking for large organizations to target next.
YARA Rule
The following YARA rule was authored by the BlackBerry Research & Intelligence Team to catch the threat described in this document:
import "pe"
rule Mal_Ransom_Win32_Karma_2021
{
meta:
description = "Detects Karma Ransomware 2021"
author = "Blackberry Threat Research Team "
date = "2021-10"
license = "This Yara rule is provided under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0) and open to any user or organization, as long as you use it under this license and ensure originator credit in any derivative to The BlackBerry Research & Intelligence Team"
strings:
$s1 = "WW91ciBuZXR3b3JrIGhhcyBiZWVuIGJyZWFjaGVkIGJ5IEthcm1hIHJhbnNvbXdhcmUgZ3JvdXAu" ascii wide
$x2 = "crypt32.dll" nocase
$x3 = "KARMA" ascii wide
$x4 = "Sleep" nocase
condition:
//PE File
uint16(0) == 0x5a4d and
//Base64 Karma Note
all of ($s*) and
//All Strings
all of ($x*)
}
|
Indicators of Compromise (IoCs)
Ransom Note:
KARMA-AGREE.txt
KARMA-ENCRYPTED.txt
Encrypted Files:
*.KARMA
*.KARMA_V2
Mutex:
Global\KARMA
Malware Digital Cert:
Serial: {00 C4 CD EE EB 36 88 DA 08 1F 95 D6 AA 33 7E 93 D1}
Payment Email IoC’s:
JamesHoopkins1988[@]onionmail[.]com
Leslydown1988[@]tutanota[.]com
ollivergreen1977[@]protomail[.]com
IndiAdams[@]onionmail[.]org
Jimmyhendricks[@]tutanota[.]com
karlironsterson122[@]protomail[.]com
Leak Site:
hxxp://3nvzqyo6l4wkrzumzu5aod7zbosq4ipgf7ifgj3hsvbcr5vcasordvqd[.]onion/
SHA256:
KARMA_V2
1c41acdc2e9d8b89522ebb51d65b4c41d7fd130a14ce9d449edb05f53bbb8d59
6c98d424ab1b9bfba683eda340fef6540ffe4ec4634f4b95cf9c70fe4ab2de90
KARMA
0d037ee0252e4f26800bcf7c750f61d0c549b7ba0a522c75e8d96dcf4f689e27
84d24a16949b5a89162411ab98ab2230128d8f01a3d3695874394733ac2a1dbd
124f3a5caf6eb464027f2865225a6a1238c3639e5b4a399f0f7f2dda7bd75aec
3ff1b90dbad5d78397fdc731c3a3c080d91fc488ac9152793b538b74a1e2d8f3
ad841882052c3f9d856ad9a393232e0a59d28e17c240d23258f1dac62f903ab8
19417c0a38a1206007a0cc82c0fc2e19db897214d27d0998bc4dbac53cc2788d
a63937d94b4d0576c083398497f35abc2ed116138bd22fad4aec5714f83371b0
34629751d8202be456dcf149b516afefc980a9128dd6096fd6286fee530a0d20
|
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
Want to learn more about cyber threat hunting? Check out the BlackBerry Research & Intelligence Team’s new book, Finding Beacons in the Dark: A Guide to Cyber Threat Intelligence, now available for pre-order here.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.