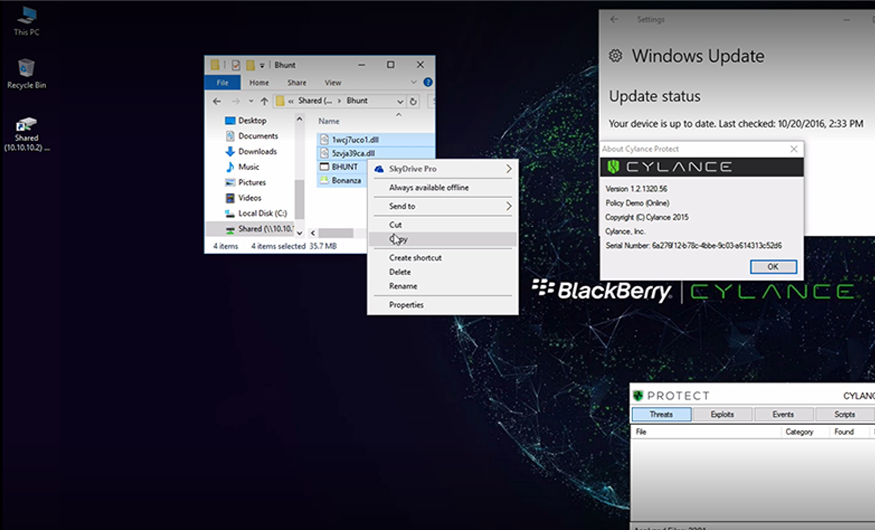
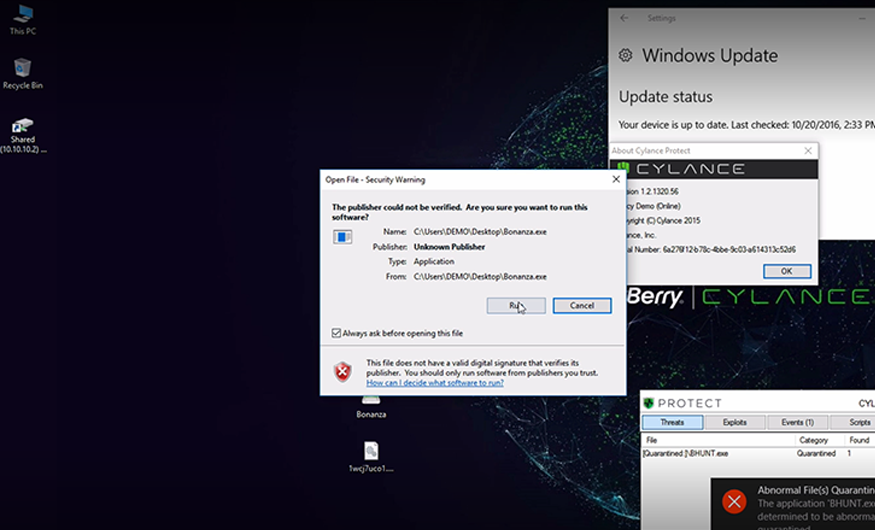
Hold onto your crypto wallets: BHunt Scavenger is among the latest threats targeting cryptocurrency holdings, while employing a variety of methods to avoid detection and slow analysis.
With its primary goal of harvesting victims' crypto wallets, BHunt also attempts to steal browser passwords. This is likely intended to help find login credentials stored for online crypto accounts, along with online banking or social media accounts that could be used for financial gains. In certain situations, BHunt can also deploy a cryptominer on the victim’s device or monitor their clipboard for security passphrases.
BHunt was initially discovered late last year by Bitdefender, who reported that the infection began with a dropper that was likely packaged with Key Management Service (KMS) cracking utilities. These utilities are popular tools designed to bypass Microsoft’s KMS, to illegally activate Microsoft® products such as Windows® 10.
BHunt’s strategy of dropping multiple files to disk is a devious way of spreading out the risk of detection across numerous components. Making use of legitimate tools such as Nirsoft’s WebBrowserPassView also makes it more difficult to detect these components of the malware on the victim’s system. Security products need to distinguish the context in which the legitimate binaries are being used, which is no easy feat for legacy antivirus software.
As cryptocurrencies continue to gain popularity, threat actors will continue to pursue this financial incentive with increasingly complex and stealthy crypto-stealers–keeping defenders on their toes.