Threat Thursday: CryptBot Infostealer Masquerades as Cracked Software
CryptBot is back. A new and improved version of the malicious infostealer has been unleashed via compromised pirate sites, which appear to offer “cracked” versions of popular software and video games.
Making news most recently for an outbreak in early 2022, the malware first appeared in the wild in 2019, and it is now actively changing its attack and distribution methods. Most notably, recent versions have been significantly streamlined to include only infostealing functionality, contained in a much smaller package than before.
CryptBot targets sensitive user data such as browser login information, cryptocurrency wallets, stored credit card information, passwords and more. The gathered information is sent back to a command-and-control (C2) address, to be used by the attacker for financial gain.
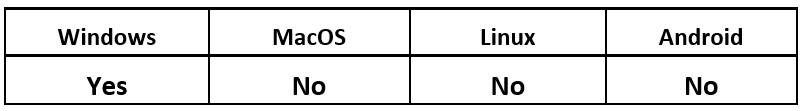
Operating System
Risk & Impact
Compromised and Cracked Websites
CryptBot has recently been hosted and distributed via compromised webpages that appear to offer cracked versions of popular video games and other software. Threat actors commonly bundle their Trojanized executables this way to lure their victims into unknowingly downloading and executing malicious code.
Cracked software typically refers to commercial software packages that have been modified to give people free access to functionality and features. Users seeking this pirated software tend to be less risk-conscious, making them particularly attractive targets for malware. Threat actors often use search engine optimization (SEO) techniques to help push these compromised websites to victims.
Technical Analysis
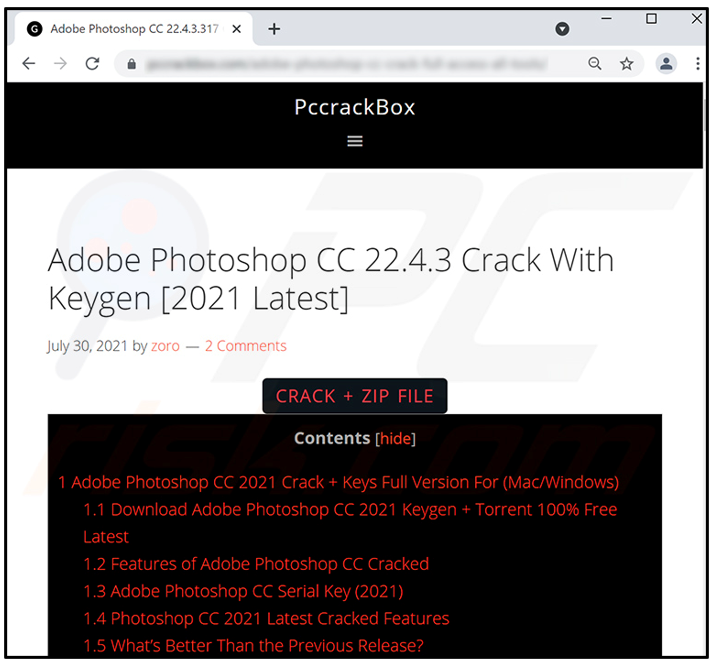
The attack chain for CryptBot begins when the victim visits a compromised webpage and is lured into downloading an SFX file, such as the one pictured in Figure 1, which is masquerading as the latest version of Adobe Photoshop.
Figure 1 - Example of malicious webpage offering cracked software
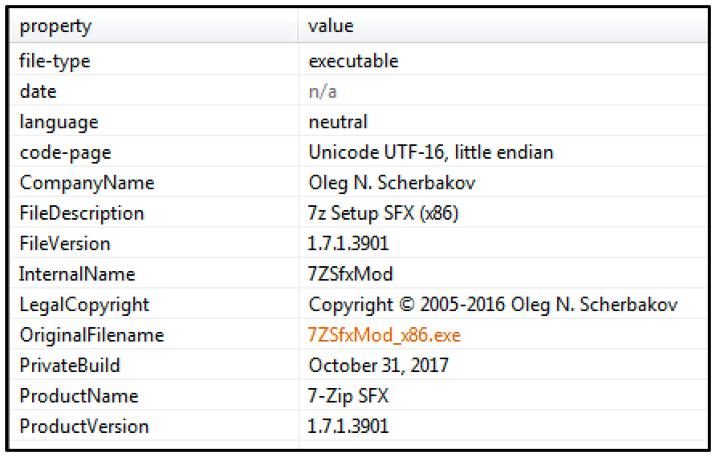
Once the victim downloads what they assume is cracked software, an SFX file called "7ZSfxMod_x86.exe” is dropped to their machine, as shown in Figure 2.
Figure 2 - Malicious SFX file retrieved from compromised webpage
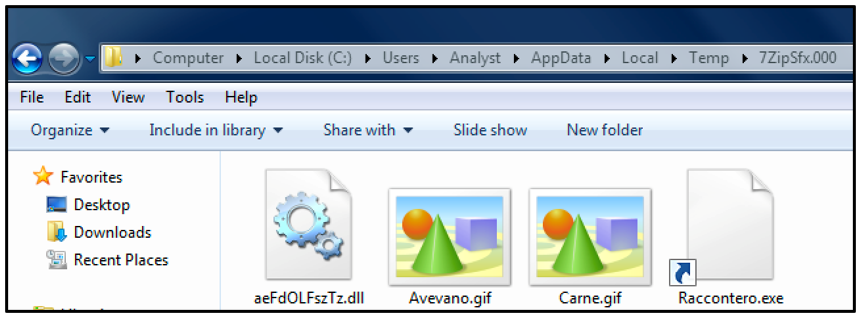
Once the archive file is launched, a folder with the naming scheme “7ZipSfx.000” is placed into the victim’s %Temp% directory, as seen in Figure 3. The numbers used in the naming scheme for this folder vary based on the number of times the malware has been launched. For example, executing the archive file a second time will result in an additional folder called “7ZipSfx.001” being placed in the same directory, with the same files included.
Figure 3 - Folder placed into user’s Temp directory post execution
This folder contains four files that are used to carry out the next stage of the attack:
- “aeFdOLFszTz.dll” – A legitimate copy of Microsoft® Windows® “ntdll.dll”
- “Avevano.gif” – A BAT script
- “Carne.gif” – An obfuscated AutoIT script
- “Raccontero.exe” – An AutoIT v3 executable compiler
As seen in Figure 3, two of these files are displayed as .GIF files. However, these files are in fact malicious scripts using the .GIF extension to masquerade as image files. The file extensions used vary, depending on the version of CryptBot downloaded by the victim. Different variants analyzed have also been observed using .MP3 and .WMV extensions.
A copy of “AutoITv3.exe” is also dropped to the folder as “Raccontero.exe.” This tool is an interpreter that is part of AutoIT, which is a freeware programming language for Windows-based devices. This tool is intended for use in automating services via scripts; however, it has frequently been abused by many different malware families.
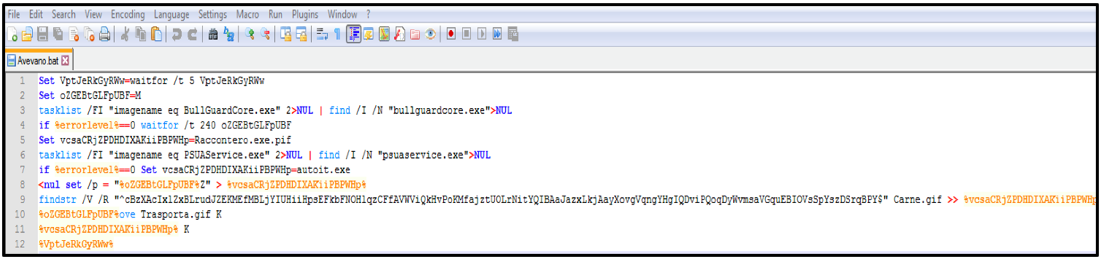
The structure and contents of the BAT script, such as obfuscated variables, can be seen in Figure 4 below. The script performs a scan against a task list referencing two antivirus (AV) products, “BullGuardCore” and “Panda Cloud Antivirus.” If the AV products are present, the malware will perform a “sleep” function to delay execution and aid in bypassing detection.
Figure 4 - Malicious BAT Script "Avevano.gif"
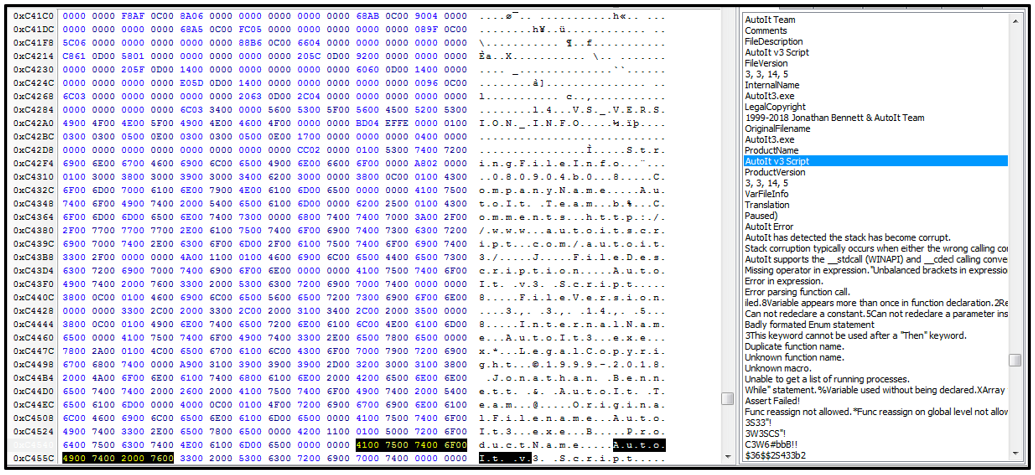
As part of the initial malware execution chain, the BAT script is used to decrypt the heavily obfuscated AutoIT script, "Carne.gif,” as seen in Figure 5. The BAT also copies the AutoIT script to the virtual memory area to run it.
Figure 5 - Obfuscated AutoIT script "Carne.gif”
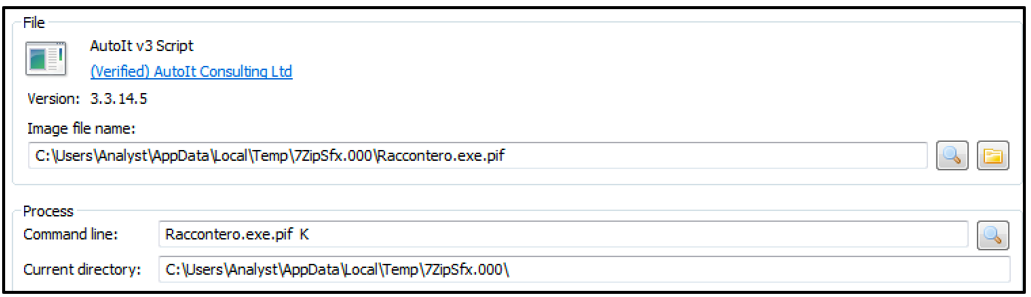
The AutoIT executable compiler “Raccontero.exe” is used to run "Carne.gif." The filename of the script is supplied as an argument, as shown in Figure 6.
Figure 6 - Launched AutoIT Process "Raccontero.exe.pif”
This spawns the AutoIT process “Raccontero.exe.pif,” which loads the malicious CryptBot binary into memory.
Capabilities
Once the malicious payload is executed, CryptBot can begin fulfilling its main function of harvesting and exfiltrating sensitive information from the victim’s machine. It begins by searching the machine for various user and system information to steal. Gathered data is stored in a directory within the user’s %Temp% folder. The information is saved in this directory until it is sent to the C2 server, then it is deleted.
The data that CryptBot searches for includes the following:
- Cryptocurrency wallet details
- Login credentials
- Form data saved to the browser
- Cookies
- Browser history
- Credit card details
- Files containing sensitive data
- OS and hardware information
- A list of installed programs
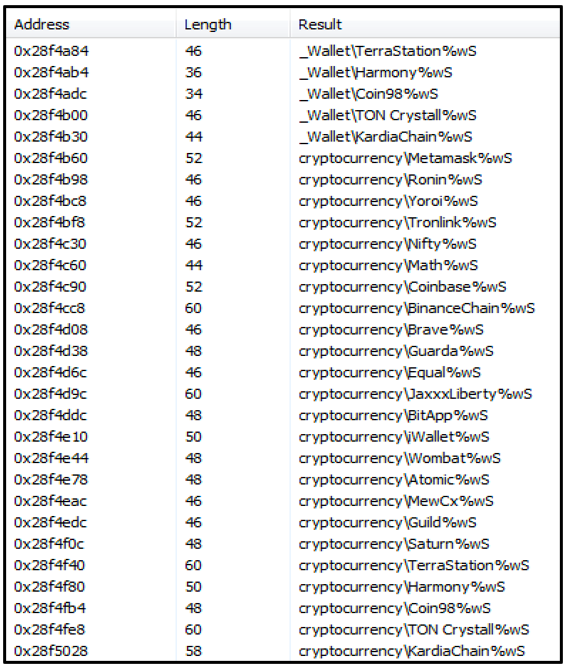
Figure 7 below shows a list of cryptocurrency directories and wallets that CryptBot scans for.
Figure 7 - List of Cryptocurrency directories scanned for by CryptBot
The victim’s data is stored in a zipped TXT file within the %Temp% directory. The malware then reaches out to the C2 server, which in the case of this sample, is located at "rygvpi61[.]top/index.php.” The stolen data is exfiltrated back to the attacker and the folder containing the sent information is wiped from the victim’s machine.
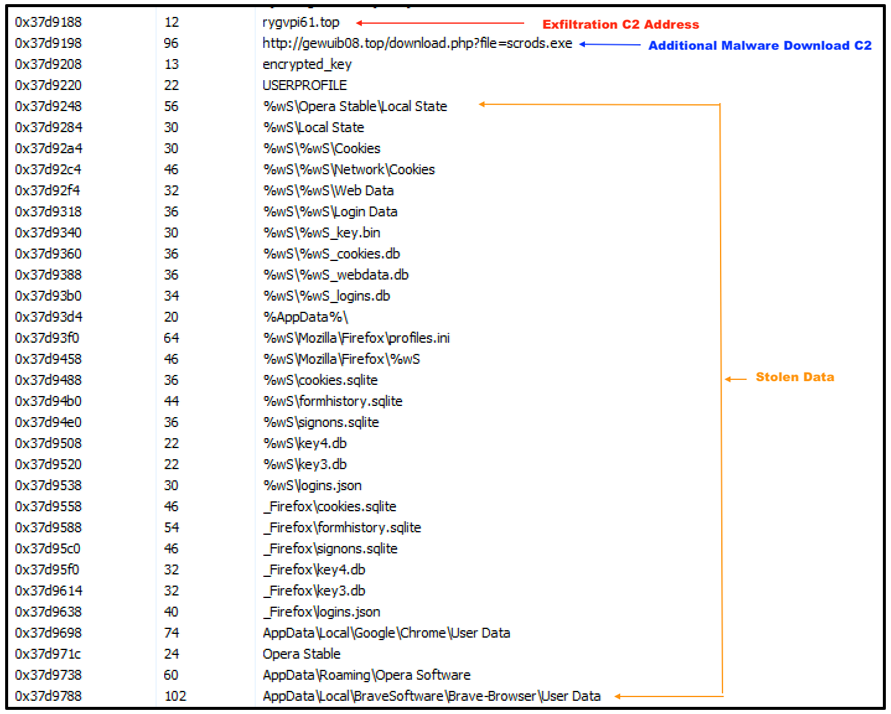
CryptBot contains a second hardcoded C2 that can be used for downloading additional malware. This address can be seen in Figure 8 below, along with several of the directories that are targeted for data exfiltration, including cookies, login data, web profiles and browser form history.
Figure 8 - C2 addresses and a selection of targeted directories
Latest Variant
The very latest version of CryptBot was first spotted in the wild in early 2022, with a few notable differences from previous variations.
Overall, it appears that the threat actor has decided to trim the file, so it only includes the core functionality necessary for successful data exfiltration. One of the features removed is the anti-sandbox capabilities used in previous versions.
The latest version of CryptBot also does not steal screenshots of the victim’s desktop, nor does it perform self-deletion of the malicious files used. The current version deletes only gathered data after successfully performing data exfiltration, rather than its own files.
The obfuscation methods used in this version also differ from older variants of CryptBot. The malicious BAT script now in use contains a higher level of obfuscation, using encrypted variables to help impede analysis by threat researchers.
Previous versions of this infostealer contained two C2 addresses that were used for data exfiltration and one address used to retrieve additional malware, whereas the version analyzed here has been limited to one dedicated address for exfiltration and one for additional downloads.
The latest version of CryptBot has also been modified to target all versions of Google Chrome™, including the newest version, Chrome™ v96.
Conclusion
CryptBot has thus far only been observed targeting Windows devices. This is likely because the malware’s infection vector uses pirated websites offering cracked software, which is not as common on other operating systems such as Mac OS X and Linux®. These other operating systems make a less lucrative target for threat actors who use this particular distribution method.
So why did the malware’s author decide to cut some features from the latest version of CryptBot? This decision could have been made in attempt to simplify the attack overall, and to ensure that focus is solely placed on the vital functionalities. As a result of this paring down, the size of the malicious archive files being downloaded from the compromised pages are roughly half the size. This could benefit the attackers by allowing more frequent and quicker infection processes.
The best mitigation tactic against CryptBot is for users to be extra vigilant when visiting websites to download new software, and only trusting download links from legitimate vendors rather than third-party or pirate websites.
YARA Rule
The following YARA rule was authored by the BlackBerry Research & Intelligence Team to catch the threat described in this document:
import "pe"
rule CryptBot {
meta:
description = "Detects 2022 CryptBot Through Imphash"
author = "BlackBerry Threat Research Team"
date = "2022-02-26"
license = "This Yara rule is provided under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0) and open to any user or organization, as long as you use it under this license and ensure originator credit in any derivative to The BlackBerry Research & Intelligence Team"
strings:
$s1 = "7z SFX"
condition:
(
//PE File
uint16(0) == 0x5a4d and
//Imphash
pe.imphash() == "e55dbecdaf2c7cc43f3d577e70c6c583" or
pe.imphash() == "27fc501de77f5768cac058a2a9512c3a" or
pe.imphash() == "fda990324138bdc940f9020ce3e8d5fc" or
pe.imphash() == "997edafa1e226ba6317ec804803f9a57" or
pe.imphash() == "4b3cfc81e94566bb0e35b6156e51fbd5" and
//All Strings
all of ($s*) )
}
|
Indicators of Compromise (IoCs)
Hash
53d8d466679a01953aab35947655a8c1a2ff3c19ac188e9f40e3135553cf7556
Filenames
- 7ZipSfx.000 – Initial folder dropped into Temp directory
- aeFdOLFszTz.dll – A legitimate copy of Microsoft Windows “ntdll.dll"
- Avevano.gif – BAT Script
- Carne.gif – Obfuscated AutoIT Script
- Raccontero.exe – AutoIT Executable Compiler
C2
rygvpi61[.]top/index[.]php – Exfiltration address
gewuib08[.]top/download.php?file=scrods[.]exe – Download address
|
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.