Threat Thursday: BoratRAT
While the name “BoratRAT” might bring a certain comedian to mind, this threat is nothing to laugh at. BoratRAT is an all-in-one malware toolkit that is capable of a variety of destructive activities, including acting as a ransomware, and performing credential theft.
BoratRAT was first analyzed by researchers at Cyble, which gave us our first deep dive into this malware’s full range of features. In researching this threat further, we discovered some intriguing connections between BoratRAT, SantaRAT, and AsyncRAT.
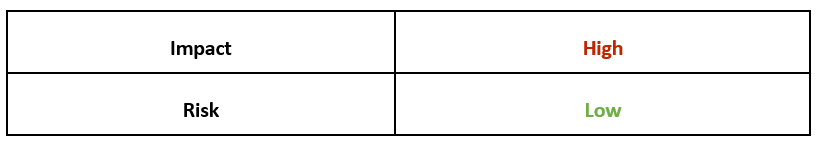
Operating System
Risk & Impact
Technical Analysis
BoratRAT’s name is taken from a satirical and fictional character (“Borat Sagdiyev”) played by comedian Sacha Baron Cohen. The malware author promotes this Trojan on the web as the “#1 Remote Administration Tool” and uses Cohen’s likeness in its icon.
BoratRAT was first seen by researchers on March 31, 2022. This new remote access trojan (RAT) proudly promotes itself as having a large feature set including the following:
- Direct Denial of Service (DDoS) attacks
- Ransomware capabilities
- Keylogging and data exfiltration
- Peripheral device manipulation (cameras, monitors, etc.)
- User Account Control (UAC) Bypass and Windows Defender deactivation
- Audio and Webcam Recording
- Browser credential and password theft
- Discord Token theft
- File system manipulation
- Remote Desktop capabilities
In the spirit of brevity, this post will analyze just two modules packaged with BoratRAT: keylogger.exe and information.dll. We will examine the modules’ functionality and compare them with a similar older threat, SantaRAT. There, we will aim to find a major set of commonalities between the two RATs.
BoratRAT Breakdown
BoratRAT is initially packaged as a zip file named Borat.zip (SHA256 D2ce3aa530ba6b6680759b79aa691260244ca91f5031aa9670248924cc983fb0). Inside the zip file is the BoratRAT.exe executable, a config file for BoratRAT, a server certificate, and a bin directory. All the feature-supporting modules are stored in the bin directory of the zip. For our purposes here, we will be focusing on the following three executables:
- BoratRAT.exe (b47c77d237243747a51dd02d836444ba067cf6cc4b8b3344e5cf791f5f41d20e)
- Keylogger.exe (16beb1ae2de2974ccc2371d9f619f492295e590abb65d3102e362c8ec27f2bbb)
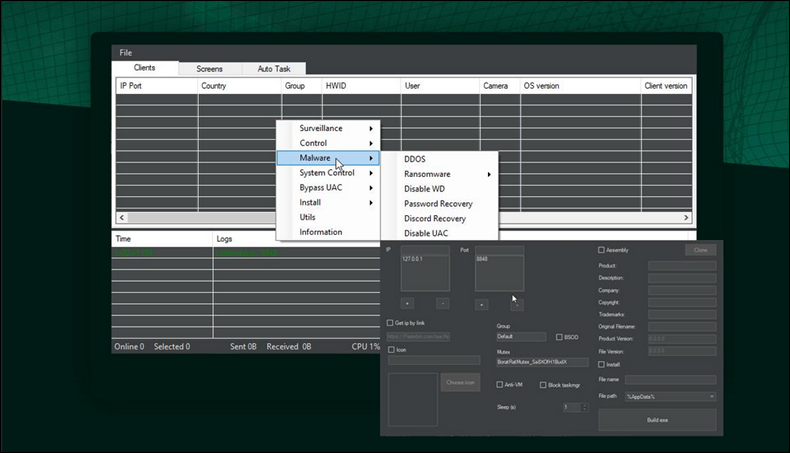
Running the BoratRAT.exe starts the user interface for the malware operator. From here, a threat actor can conduct all the malware’s capabilities on their target machine, as shown in Figure 1. The malware author packed BoratRAT.exe with Enigma Protector for obfuscation, to make it more difficult to analyze.
Figure 1 – BoratRAT UI snippet
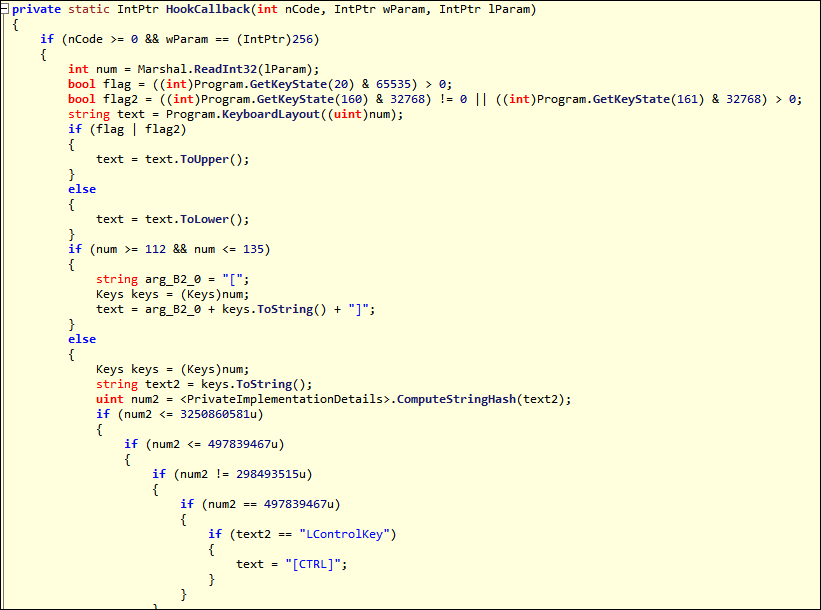
The keylogger.exe application module is called through BoratRAT’s user interface (UI). Keylogger.exe does exactly as the filename describes – it logs the victim’s keystrokes and saves the input to a file. The keylogging application starts with a main function, which passes a low-level keyboard procedure to a function called SetHook. SetHook receives the return value from HookCallback as shown in Figure 2 below, which uses a combination of GetKeyState and a decision structure to get key status.
Figure 2 - HookCallBack function with keystroke decision tree
Once the key state is recognized, a keystroke is then written to a string stream with StreamWriter. StreamWriter is a library native to the C# programming language, which is used to write characters to a stream in UTF-8 encoding.
At this point in the malware’s execution, a check is made with an IF ELSE statement against the GetActiveWindowTitle() function. Then the function makes a call to GetForegroundWindow() from winuser.h, to return a handle to the window that the victim is currently working in. This is done to properly label which active window the victim is in, as it writes keystrokes to the file.
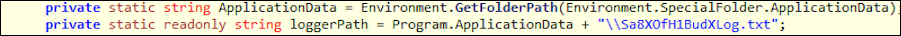
The output from this activity is then written to a file indicated by the program.loggerPath variable. LoggerPath is a static string used by the program that concatenates the working environment of the program to the output file, to give it a full environment path. In this instance, the file is named “\\Sa8X0fH1BudXLog.txt” and is written out to the environment folder path specified by the malware, as shown in Figure 3.
Figure 3 – Text file “Sa8XofH1BudXLog.txt” location in Keylogger.exe
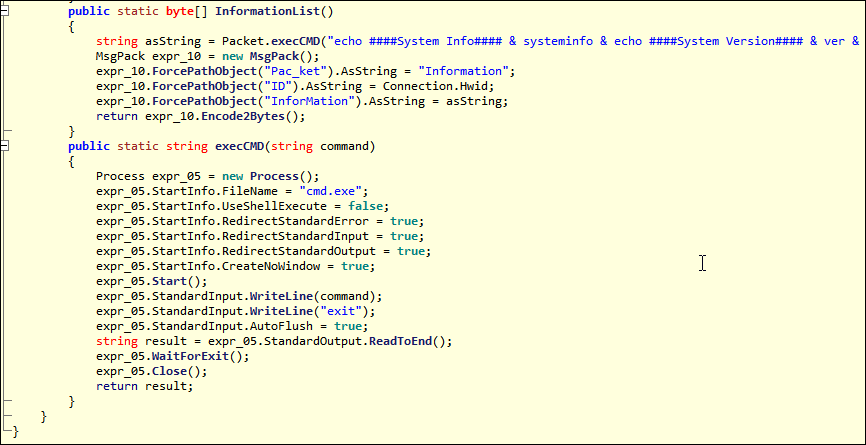
The Information.dll module contains commands to exfiltrate system information to the attacker. The function execCMD starts a command prompt with the “cmd.exe” application, which is launched in CreateNoWindow mode with standard output, input and error redirected. This redirection is done to hide the execution of the command prompt from the desktop.
At that point, the InformationList() function calls execCMD(). A command string is passed that writes a long stream of system information out to the command line, as seen in Figure 4. The information is then packeted and sent back to the threat actor. The string of echo commands is a full dump of environment, OS version, hardware, hosts, user/administrator information, and network information.
Figure 4 – Information.dll “InformationList” and “execCMD” functions
It is likely that the initial inspiration for BoratRAT was an earlier threat called AsyncRAT, which first appeared two years ago. Evidence supporting this origin was found by BleepingComputer, which pointed out similarities between these two threats. This assertion has also been backed up through string analysis using the Intezer Analyze tool.
This is not the only RAT that was inspired by this threat – SantaRAT was also built on AsyncRAT, and it could have been another starting point for BoratRAT’s development. In fact, on the main page of the GitHub repository for SantaRAT, the owner gives a personal “thank you” to the author of the AsyncRAT library.
From the starting point of AsyncRAT’s functionality, SantaRAT added modules like audio recording and file system modifications. But SantaRAT’s last change was made five months ago. BoratRAT began with a feature set that is closer to that of SantaRAT.
The two modules we will analyze in this section are just a fraction of this RAT’s capabilities, to show a representative example of the links between the SantaRAT source code and BoratRAT’s module code.
On a high level, the similarities are quickly apparent. For instance, both threats are written in C#. They have a very similar feature set; they are both capable of ransoming a victim, stealing credentials, and obtaining remote access, to name but a few examples.
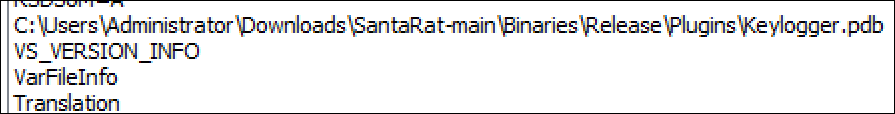
When we get down to the modules, the similarities continue. Whenever source code files (legitimate or otherwise) are compiled, each module contains a directory path that references a program database file. Program database files are used to store debugging information about a compiled source code file.
In BoratRAT’s path, we see a reference to SantaRAT, which is shown in Figure 5. This shows that SantaRAT modules were downloaded, compiled, and were in use in the same environment. This pathway with “SantaRat-main” is seen in BoratRAT’s information.dll library as well.
Figure 5 – SantaRAT-main library path string in BoratRAT’s packaged Keylogger.exe
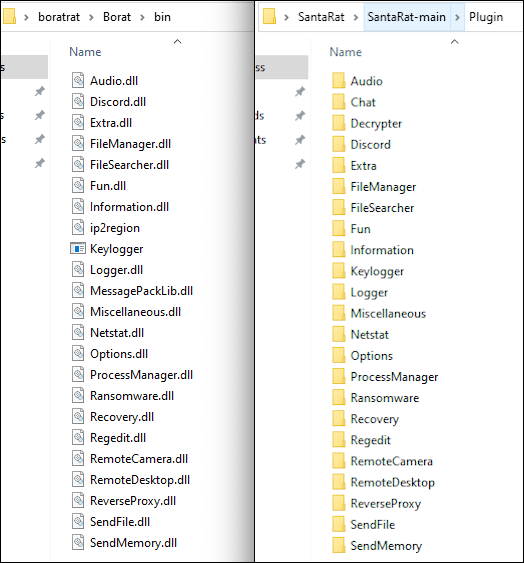
Beyond that, the structured code and module names also nearly mirror each other. With the exclusion of a few modules in SantaRAT, the module packages are nearly identical when compared side by side, as seen below in Figure 6. The missing directories are Chat, Decryptor, and messagepacklib. This could be due to the author refactoring some code functionality into similar libraries.
Figure 6 – BoratRAT bin and SantaRAT plugin
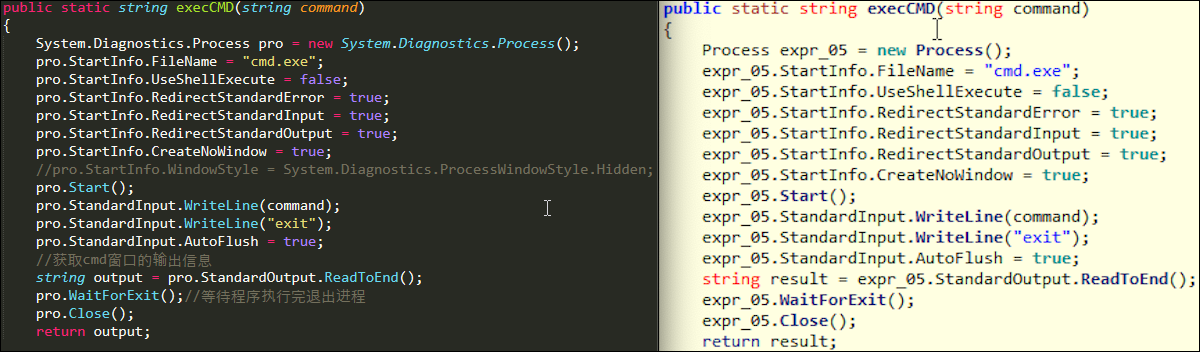
Almost all the module code from both RATs is identical. Information.dll shares the exact same code as packet.cs in the SantaRAT repository on GitHub. A snippet of the execCMD taken from SantaRAT and BoratRAT, seen in Figure 7, shows almost a line-for-line copy between the two. This type of code reuse is found in the keylogger.exe application and packaged in BoratRAT and program.cs from SantaRAT’s repository as well.
Figure 7 – SantaRAT execCMD function (left) BoratRAT execCMD function (right)
Conclusion
It’s clear from the supporting analysis that the malware author of BoratRAT used SantaRAT as a development reference. In every module we analyzed there is obvious code reuse. Some of the modules have been exact line-for-line copies.
So, what does this mean? We think that BoratRAT’s code reuse could indicate a continuation of development and rebranding of SantaRAT. It is entirely possible that a new author could take over the evolution of this malware, or it could be that BoratRAT is meant to be yet another short-lived development. Time will tell where this threat is headed.
Despite BoratRAT’s comical name, the versatility of this RAT makes it a dangerous threat that both private individuals and companies should be wary of. The impact of BoratRAT obtaining entry to a system (either an individual or an organization) could be catastrophic, and proper security practices should be observed to help mitigate threats such as this.
YARA Rules
The following YARA rule was authored by the BlackBerry Research & Intelligence team to catch the threat described in this document:
rule BoratRAT{
meta:
description = "Detects BoratRAT.exe"
author = "BlackBerry Threat Research Team"
date = "2022-04-13"
license = "This Yara rule is provided under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0) and open to any user or organization, as long as you use it under this license and ensure originator credit in any derivative to The BlackBerry Research & Intelligence Team"
strings:
$s1 = "enigma1"
$s2 = "enigma2"
$s3 = "Server.Forms.FormFileManager.resources"
$s4 = "Server.Forms.FormFileSearcher.resources"
$s5 = "Server.Forms.FormKeylogger.resources"
$s6 = "Server.Forms.FormNetstat.resources"
$s7 = "Server.Forms.FormFun.resources"
$s8 = "Server.Forms.FormWebcam.resources"
$s9 = "BoratRat"
$s10 = "Keylogger.exe"
condition:
uint16(0) == 0x5a4d and all of them
}
rule BoratRATKeylogger{
meta:
description = "Detects BoratRAT Keylogger"
author = "BlackBerry Threat Research Team"
date = "2022-04-13"
license = "This Yara rule is provided under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0) and open to any user or organization, as long as you use it under this license and ensure originator credit in any derivative to The BlackBerry Research & Intelligence Team"
strings:
$s1 = "Sa8XOfH1BudXLog.txt" wide
$s2 = "[CAPSLOCK: ON]" wide
$s3 = "[CAPSLOCK: OFF]" wide
$s4 = "[SPACE]" wide
$s5 = "[ENTER]" wide
$sp = { 43 3A 5C 55 73 65 72 73 5C 41 64 6D 69 6E 69 73 74 72 61 74 6F 72 5C
44 6F 77 6E 6C 6F 61 64 73 5C 53 61 6E 74 61 52 61 74 2D 6D 61 69 6E
5C 42 69 6E 61 72 69 65 73 5C 52 65 6C 65 61 73 65 5C 50 6C 75 67 69
6E 73 5C 4B 65 79 6C 6F 67 67 65 72 2E 70 64 62 }
condition:
uint16(0) == 0x5a4d and all of them
}
rule BoratRATInformation{
meta:
description = "Detects BoratRAT Information Module"
author = "BlackBerry Threat Research Team"
date = "2022-04-13"
license = "This Yara rule is provided under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0) and open to any user or organization, as long as you use it under this license and ensure originator credit in any derivative to The BlackBerry Research & Intelligence Team"
strings:
$s1 = "set_UseShellExecute"
$s2 = "execCMD"
$s3 = "hostname" wide
$s4 = "ipconfig" wide
$s5 = "tasklist" wide
$s6 = "arp -a" wide
$sp = {43 3A 5C 55 73 65 72 73 5C 41 64 6D 69 6E 69
73 74 72 61 74 6F 72 5C 44 6F 77 6E 6C 6F 61
64 73 5C 53 61 6E 74 61 52 61 74 2D 6D 61 69
6E 5C 42 69 6E 61 72 69 65 73 5C 52 65 6C 65
61 73 65 5C 50 6C 75 67 69 6E 73 5C 49 6E 66
6F 72 6D 61 74 69 6F 6E 2E 70 64 62}
condition:
uint16(0) == 0x5a4d and all of them
}
|
Indicators of Compromise (IoCs)
b47c77d237243747a51dd02d836444ba067cf6cc4b8b3344e5cf791f5f41d20e – BoratRAT.exe
16beb1ae2de2974ccc2371d9f619f492295e590abb65d3102e362c8ec27f2bbb – Keylogger.exe
a15d72d990686d06d89d7e11df2b16bcd5719a40298c19d046fa22c40d56af44 – Information.dll
D2ce3aa530ba6b6680759b79aa691260244ca91f5031aa9670248924cc983fb0 – Borat.zip
|
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you, providing around-the-clock support where required, as well as local assistance. Please contact us here.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.