BlackBerry Prevents Purple Fox Rootkit
Purple Fox rootkit bundles itself with legitimate installers to gain access to a victim’s machine, bringing a new level of creativity to the way cyber intrusions are performed.
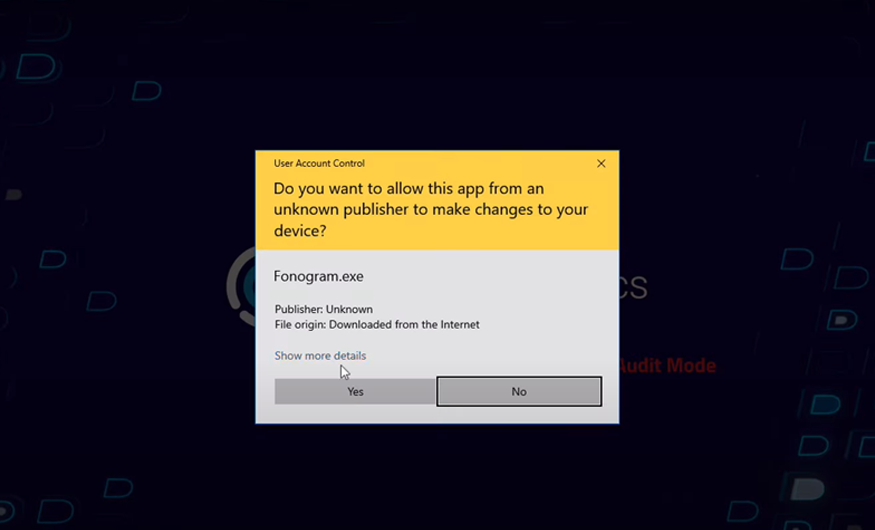
Active since early 2022, Purple Fox is a malware campaign distributed using a fake Telegram installer. The malware attempts to stay under the radar by breaking its attack chain into multiple, discrete stages. Each stage of the attack is carried out by a different file, with each file being useless without the entire file set.
The malware accomplishes its primary goal of gaining access to targeted Windows® systems by loading a rootkit planted beyond the reach of antivirus (AV) products. This helps Purple Fox remain hidden from detection as the rootkit provides attackers with a backdoor to the victim's machine to carry out further malicious activity.
While using legitimate installers is already a popular technique currently used by threat actors, choosing such a popular application as Telegram is certainly notable, as is breaking up the malware's functionality to make analysis by threat researchers more difficult.
DEMO VIDEO: BlackBerry vs. Purple Fox Rootkit
Learn more about Purple Fox in our deep dive blog: Threat Thursday: Purple Fox RootKit
In the video above, we demonstrate stage one and two of Purple Fox, a rootkit that masquerades as the well-known messaging app Telegram.
We configured this system with CylanceOPTICS® in Audit-Only Mode, to allow the malware to run.
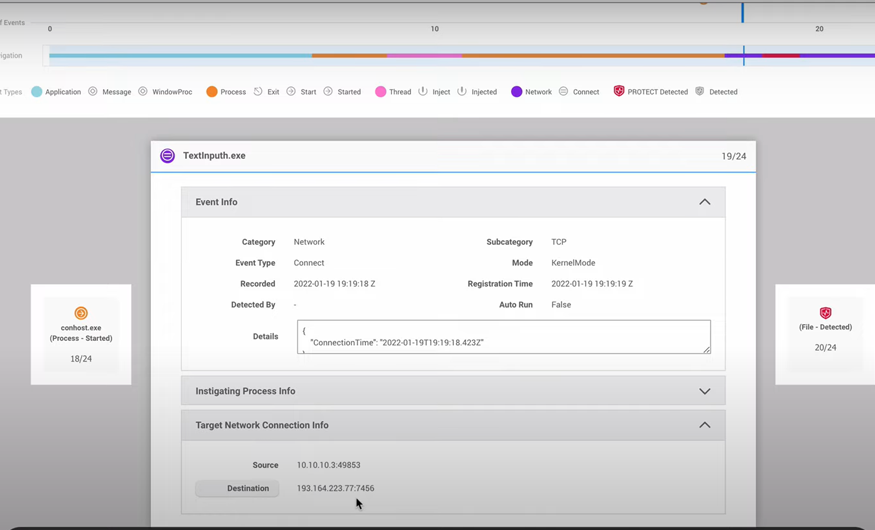
Upon execution, Purple Fox installs a legitimate version of the app, but it does not get executed right away. Instead, the file “TextInputh.exe” acts as the main malicious downloader that will later continue with other stages of the compromise.
We can see the command-and-control (C2) communication by observing the root-cause analysis in CylanceOPTICS and how it tries to connect to the attacker’s IP address. We can also get a list of all the threat indicators, with the capabilities of these files, for better understanding of the threat overall.
Note that our Cylance® AI model is from October 2015, with no Internet connectivity or system updates, and it is still able to detect these types of rootkits in milliseconds and prevent them from executing.
Our Prevention-First Philosophy
At BlackBerry, we take a prevention-first and AI-driven approach to cybersecurity. Putting prevention first neutralizes malware before the exploitation stage of the kill chain.
By stopping malware at this stage, BlackBerry® solutions help organizations increase their resilience, reduce infrastructure complexity, and streamline cybersecurity management to ensure businesses, people, and endpoints are secure.
Prevention is possible, with BlackBerry.