Windows® systems are being exploited by a new zero-day attack known as “Follina.” This attack takes advantage of a vulnerability in the Microsoft® Windows® Diagnostic Tool (MSDT), a utility which troubleshoots issues on an endpoint. The attack employs a malicious file to advance its attack, activating a payload when the host opens it, or even when their computer pre-loads the document. In fact, a victim can unknowingly activate the attack by simply hovering their mouse over a malicious file to preview it, for instance if they want to view the details of a Microsoft® Word document.
Researchers at Huntress recently verified the Follina vulnerability. Because the malicious file does not require the victim to manually enable macros, it won’t trigger warning notifications and can bypass security restrictions currently provided by Microsoft. When the file is in rich text format (RTF), the malicious code will run via the “Preview” tab in Explorer without ever being opened. This flies in the face of what many people have been taught in company security training, which was (previously) to check that the file is a real document by hovering their mouse over it to preview it.
On Monday May 30, 2022, Microsoft issued CVE-2022-30190 regarding the Microsoft Support Diagnostic Tool (MSDT) in Windows vulnerability. On Tuesday June 14, 2022, Microsoft issued Windows updates to address this vulnerability. Microsoft recommends installing the updates as soon as possible. According to Microsoft, a successful execution of this exploit can allow the attacker to manipulate the victim’s data, install programs on their computer, and even create new accounts. These changes lay the groundwork for lateral movement within the victim’s environment, a tactic often used in ransomware, advanced persistent threats (APTs) and other invasive cyberattacks.
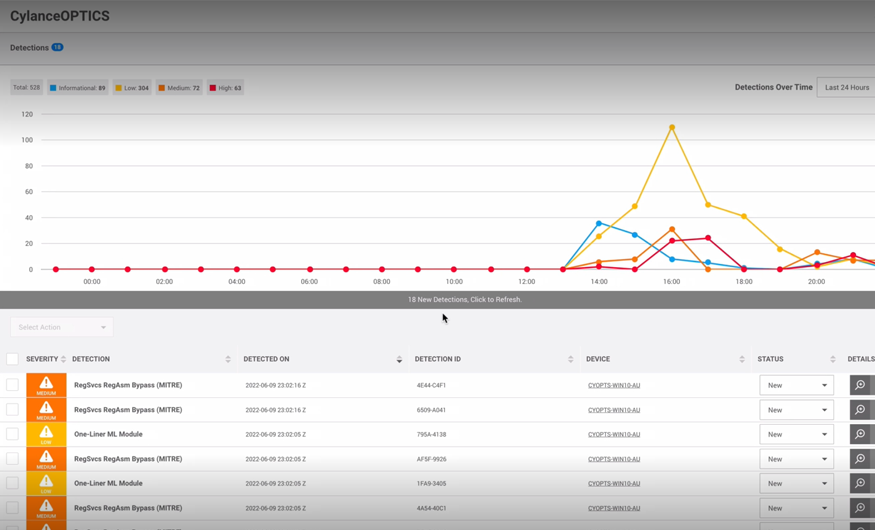
See how BlackBerry prevents Follina zero-day attacks in our demo video below, which shows BlackBerry® product CylanceOPTICS® going head-to-head with a live sample of Follina.