Video Transcript
In this video, we are going to look at how an attacker can compromise the system using the Eternity Malware-as-a-service kit. This is a multi-modular malware service that can provide many capabilities including information stealing functionality, crypto miner and clipper, a worm for malware propagation through popular instant messaging apps, and of course a ransomware module.
We have set up this machine with CylanceOPTICS in audit-only mode to allow malware execution.
We will start this demonstration by executing each one of the modules that come with this Eternity suite and are present in this folder ending with the ransomware piece. We will start with the clipper, then Eternity Infostealer, the worm, and finally with the ransomware.
When we first open these files, we don't see anything unexpected or evidently malicious. But behind the scenes, each module is executing several tasks, from information gathering and collection, to C2 communication for exfiltration and reporting, and it ends its malicious activities with the typical ransom note after a couple of minutes.
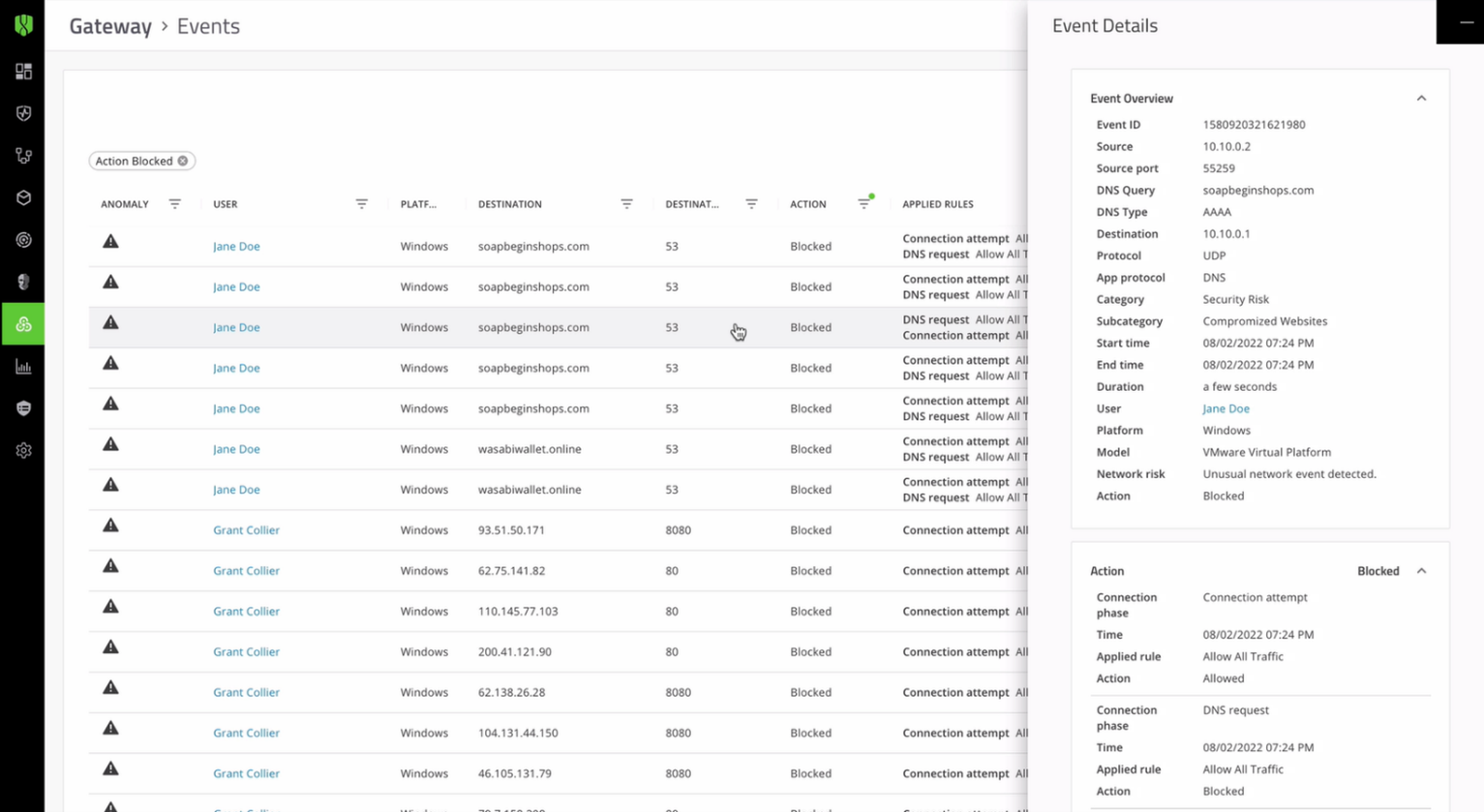
Let's go to our venue console to see what's happening. Through our root cause analysis capability, we can see all the steps taken by these modules. Let's take the clipper one as an example. We can see all the different steps taken by this module. How it starts the process from the app data folder, creates a scheduled task for additional persistence, as well as multiple values within the registry, and then establishes command and control connectivity.
If you look at the ransomware piece, we can see how it re-writes all the files present on the system from our PST (email archive) to all the remaining files present on the system.
CylanceGATEWAY can prevent C2 communications from each one of these modules if we execute these files again from our audit-only test system. But this time with traffic protection provided by our zero trust network access module, we can see how the malware never reaches its command-and-control. It stops the attacker from deploying any additional modules or instructions. If we go back to our venue console, we can see all the different attempts being blocked by CylanceGATEWAY.
In a real-world scenario, we would prefer to stop these attempts before any harm can be done. We can take a preventive approach with CylancePROTECT.
Here we have a machine with CylancePROTECT, with the protection policy enabled. Let's execute the same set of modules from Eternity, but this time we will have our preventative policy in place with no internet connectivity. We can see here that CylancePROTECT is able to prevent this malware suite in pre-execution, safeguarding both our system and our data.
Prevention is Possible, with BlackBerry.
|