ARCrypter Ransomware Expands Its Operations From Latin America to the World
Summary
On August 25, 2022, Chile's government computer systems were attacked by a previously unseen ransomware variant. CSIRT of Chile’s government published a report which contained some Indicators of Compromise (IoCs) and recommendations for prevention measures.
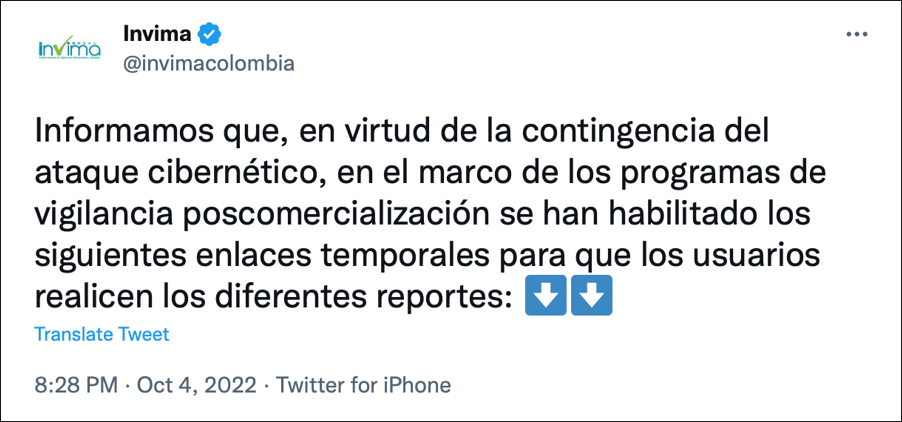
On October 3, 2022, Invima — The Colombia National Food and Drug Surveillance Institute — reported a cyberattack that led to a temporary shutdown of the organization's web services.
Through our threat hunting efforts, BlackBerry has identified additional samples of interest for this ransomware. Given the timeframe of the attack and the contents of the ransom note mentioning Invima, we believe with a high degree of certainty that this ransomware was used in the Invima cyberattack that took place in early October.
Based on the unique strings identified during the analysis, we have named this unknown ransomware variant “ARCrypter.”
Figure 1 – Invima reports a cyber-attack via Twitter.
(Translation: “Following the contingency of the cyberattack, and according to the established monitoring framework, we have enabled the following temporary links for users to fill out the different reports.")
While live and retro hunting on VirusTotal, we found submissions by apparently real victims from China and Canada. Based on the original file names, timelines, and type of submissions, it's highly likely that ARCrypter is no longer confined to LatAm only. It has now expanded its operations worldwide.
Weaponization and Technical Overview
Weapons
|
PE 64
|
Attack Vector
|
Unconfirmed
|
Network Infrastructure
|
Tor
|
Targets
|
Government organizations, miscellaneous
|
Technical Analysis
Context
Through effective hunting efforts, we were able to locate samples associated with the first ARCrypter campaign from early August 2022, which was three weeks before the incident that occurred in Chile. Unlike other ransomware variants, where a ransom note is dropped after the file encryption stage, this variant drops the ransom note before the files are encrypted, making this particular delivery mechanism unusual compared to what we have seen in other ransomware samples. Upon ransom note delivery, the dropper then proceeds to drop two batch scripts and the main payload encrypter.
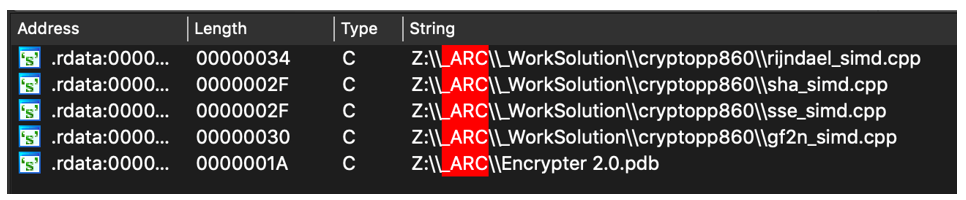
Since this was an undocumented ransomware family and the unique strings of “ARC” were found in all the samples we analyzed, we named this ransomware variant “ARCrypter.”
Figure 2 – ARCrypter strings
Attack Vector
The attack vector of the infection is unknown.
Weaponization
During our investigation, we uncovered two AnonFiles URLs facilitating the download of “win.exe” and “win.zip”. The “win.exe” file is a dropper file which we will discuss in more detail next. The “win.zip” file is a password-protected archive containing the “win.exe” file. It is important to note that AnonFiles provides anonymous file upload while hiding the IP address of the submitter. This method of file distribution is favored by many threat actors; however, it is unclear whether this particular method was used by the threat actor behind ARCrypter, or somebody else.
Figure 3 – Dropper file "win.exe" download link
First Stage – Dropper
ITW file name
|
win.exe
|
Compilation stamp
|
2022-09-30 18:21:53 UTC
|
File type/Signature
|
WIN x64 EXE
|
File size
|
884.50 KB (905728 bytes)
|
Compiler name/version
|
Microsoft Visual C++
|
Upon deeper analysis of the dropper file, we found that it contains two resources of interest – BIN and HTML. The HTML resource stores ransom note contents, and the BIN resource contains the encrypted data.
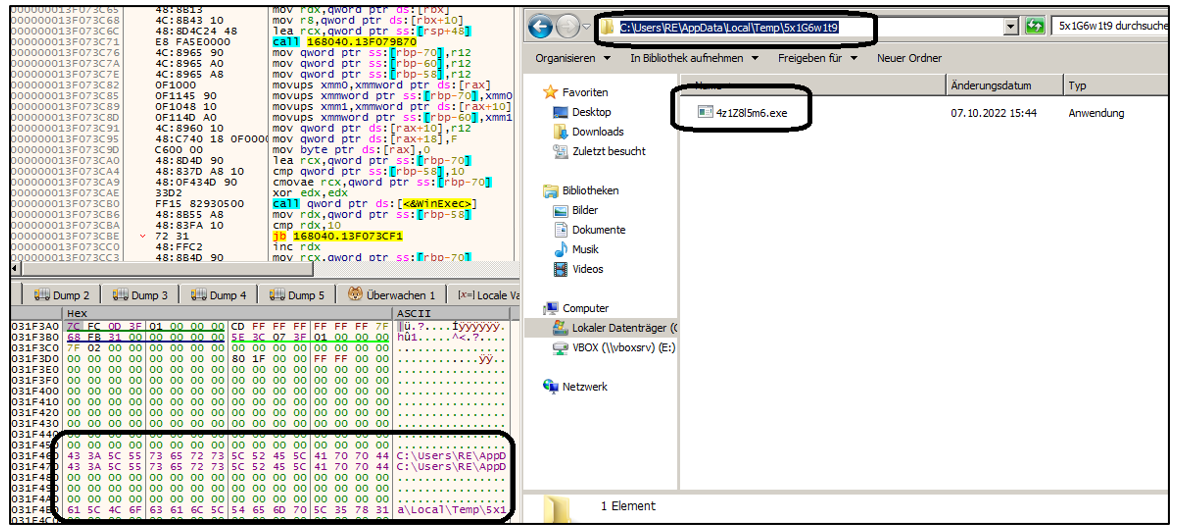
In order to decrypt the BIN resource, the dropper expects an argument “-p” followed by a password. Once the password is provided, the dropper proceeds by creating a random directory under one of the following environment variables:
- %TMP%
- %APPDATA%
- %ALLUSERSPROFILE%
- %HOMEPATH%
The purpose of this newly created directory is to store the second stage payload using alphanumeric characters, matching the following regular expression:
C:\Users\<username>\AppData\Local\Temp\[a-zA-Z0-9]{9}\[a-zA-Z0-9]{9}.exe
Figure 4 – Creation of the second stage payload
While we were unable to identify the correct decryption key used for decryption of the BIN resource, we believe with a high degree of certainty that the second payload is the ARCrypter ransomware.
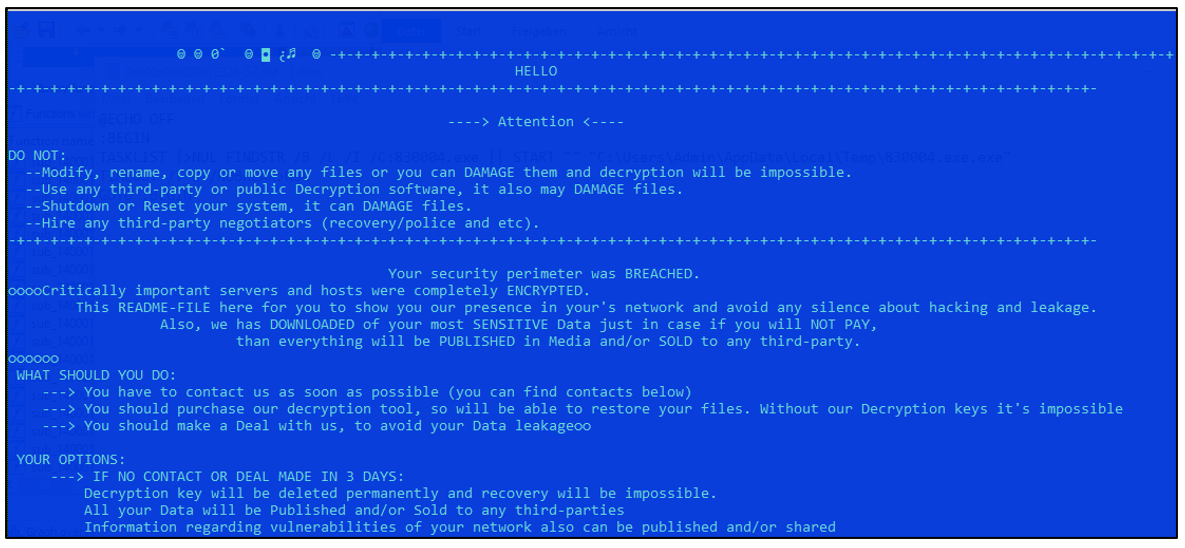
The ransom note is then extracted from the embedded resource of HTML type, and saved in %TMP%/readme_for_unlock.txt:
C:\Users\<username>\AppData\Local\Temp\readme_for_unlock.txt
Figure 5 – ARCrypter ransom note.
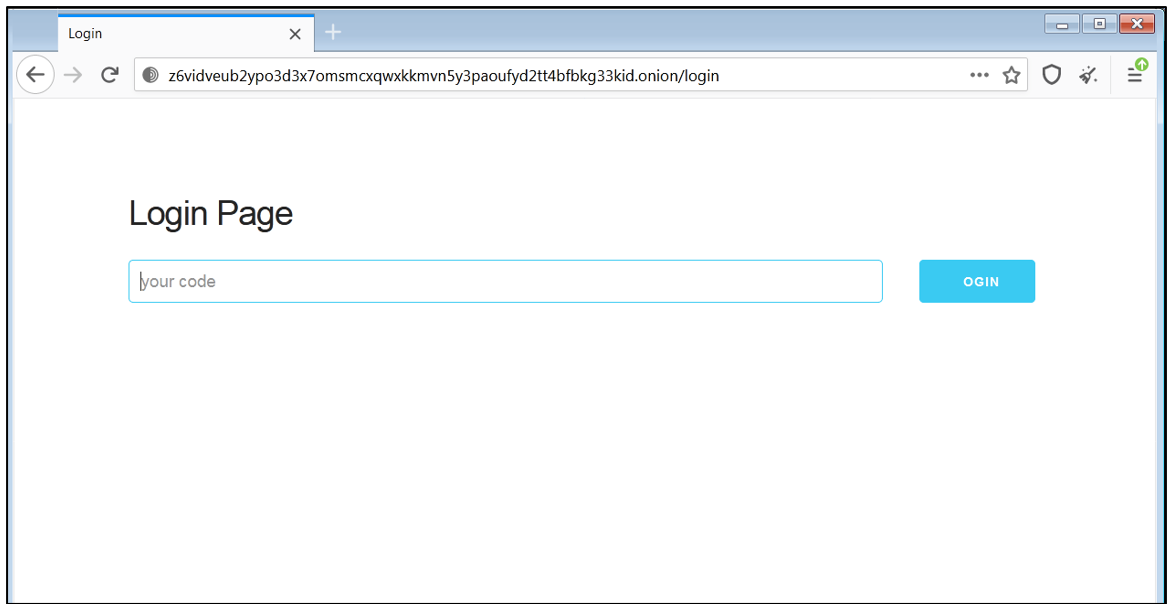
The ransom note contains the username and password required for the victim to log into the communication panel with the threat actors, which is hosted on the .onion site.
Figure 6 – Victims' communication panel with the threat actor
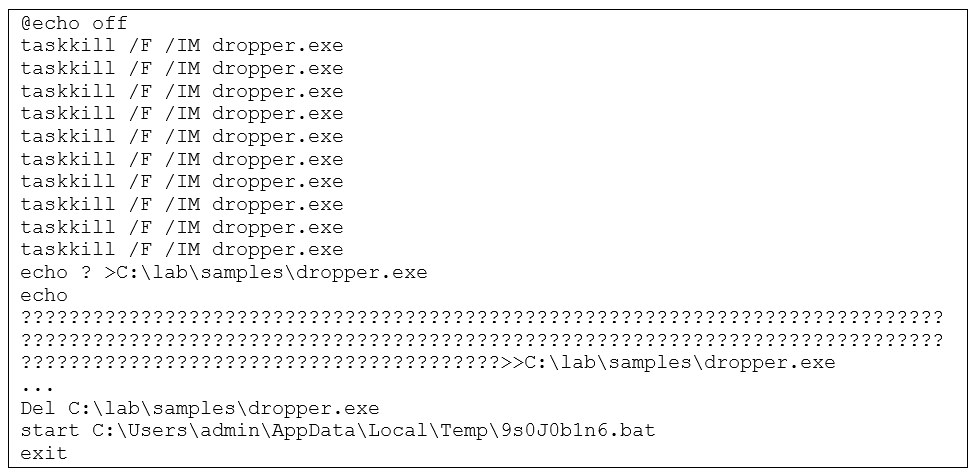
To perform a cleanup for the dropper, two bat files are created in the following location under the %TMP% directory:
C:\Users\<username>\AppData\Local\Temp\[a-zA-Z0-9]{9}.bat
The first bat file terminates the dropper process, overwrites its original file, and executes the second bat file.
The second bat file removes the first bat file from the system and then exits.
Second Stage – Payload
ITW File Name
|
3.exe
|
Compilation Stamp
|
2022-08-22 09:39:04 UTC
|
File Type/Signature
|
WIN x64 EXE
|
File Size
|
691.00 KB (707584 bytes)
|
Compiler Name/Version
|
Microsoft Visual C++
|
Upon execution, the malware proceeds in establishing persistence by invoking the reg.exe process. The purpose of this is to add the registry key “HKLM\Software\Microsoft\Windows\CurrentVersion\Run\SecurityUpdate” with value of path to the malware.
It also modifies two registry keys used to display the short date by adding a value called "ALL YOUR FILES HAS BEEN ENCRYPTED".
- HKCU\Control Panel\International\sShortDate
- HKLM\SYSTEM\ControlSet001\Control\CommonGlobUserSettings\Control Panel\International\sShortDate
To quietly delete all Shadow Volume Copies on the system, the malware invokes vssadmin.exe and runs the following command:
vssadmin delete shadows /All /quiet
Since ARCrypter also targets all the network drives that are connected to the system, the following command is used to ensure that they stay connected during downtime:
C:\Windows\system32\cmd.exe /c net config server /autodisconnect:-1
The ARCrypter ransomware will encrypt all the affected files, while skipping some predefined file extensions:
Whitelisted File Extension
|
.crypt
|
.blf
|
.regtrans-ms
|
.library-ms
|
.sys
|
.tmp
|
.log
|
.log.tmp
|
.exe
|
.bat
|
.msi
|
.dll
|
.ini
|
|
|
|
The malware will also avoid encrypting files in certain critical locations of the target system:
- All Users
- Boot
- Microsoft
- Local Settings
- $Win Reagent
- Application Data
- Windows
- Boot
- All Users
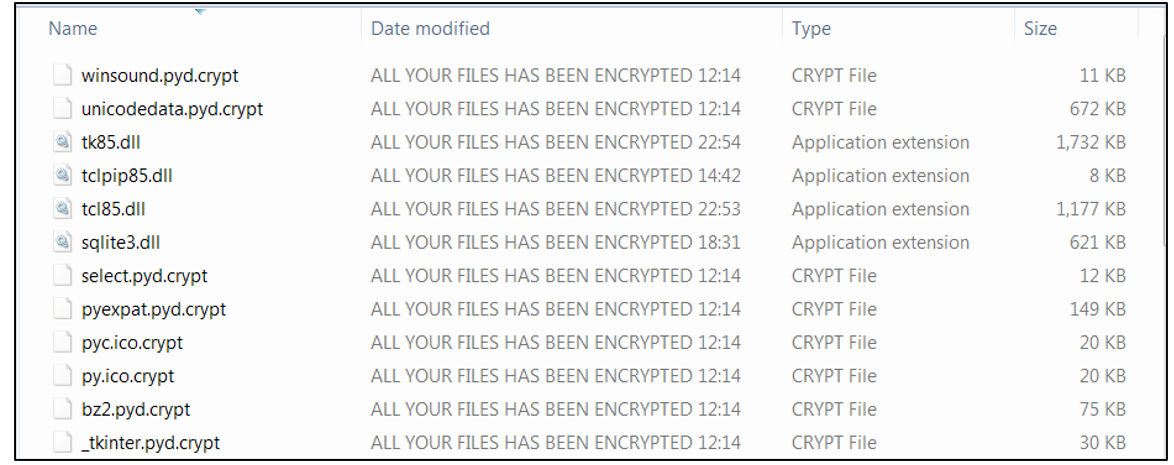
All of the files that are not on the whitelisted file extension list or whitelisted location get encrypted, and the “.crypt” file extension is appended.
Figure 7 – Files encrypted by ARCrypter
Targets
- Chilean government organizations
- The Colombian National Food and Drug Surveillance Institute
Attribution
We have not identified any evidence to attribute this malware to any previously known threat actor or threat group. While both campaigns targeted Latin American countries, currently there is no evidence in the code suggesting that a local threat actor could be the culprit.
Conclusions
In early August 2022, an unknown ransomware variant which BlackBerry named ARCrypter was found targeting Latin American institutions. At this point, we have witnessed that the threat actor behind it has expanded its operations to other countries like China and Canada. The research conducted for this report has helped uncover two sets of files – a malware dropper and file encryptor. A comprehensive list of IoCs as well as MITRE TTPs have been listed below, to help organizations and defenders detect this threat.
APPENDIX 1 – Indicators of Compromise (IoCs)
md5
sha256
|
6b402772ac82df77da8ead65636423da
8d40ac7ff823a82053b413326beba33bf94380a79c49165545fed3e92089b6eb
|
md5
sha256
|
bc288a88a43c5a6d4b9dee33d3ef70eb
cc0bd45536a6c15f8b76fe06fd637857e6fbb483dc620793aa3aa27e1ab75a62
|
md5
sha256
|
45299d77edb17dc48eccec70e928d9ea
eee0f2f6b2524498f8287f95dd184828a044677700d61e2c0a109866f3dd504d
|
PDB Path
|
Z:\_ARC\Dropper.pdb
|
Weapon type
|
Dropper
|
md5
sha256
|
b95059e7532f3548c0e0d4508f37ac81
32708c5d376f130b48bf3bd706879c1945a2d701036d94e25aceea41a4042052
|
md5
sha256
|
58aea2aac89947773dfae8e3859e20b0
39b74b2fb057e8c78a2ba6639cf3d58ae91685e6ac13b57b70d2afb158cf742d
|
md5
sha256
|
1acdaba338e67c748e56aa81a27a9831
b14cde376a8a7a9d7ad34cdfd07108c132ad8be7f60c5c0a0f17b6b63eb28b49
|
md5
sha256
|
1c4de7e0ebfbface2ff57ba5af6efde0
e1f01b2c624f705cb34c5c1b6d84f11b1d9196c610f6f4dd801a287f3192bf76
|
md5
sha256
|
09aaf431d8db13c6ebca277d918665d6
5634e4e97a71930c574b80e50ee479ab782b6888f5af31c7e7529fa651377f50
|
md5
sha256
|
33ee3a75a26856ac3db92baa57faa681
dacce1811b69469f4fd22ca7304ab01d57f4861574d5eeb2c35c0931318582ae
|
md5
sha256
|
d3d6993de967b18dbcd7da56f6bd3f29
9a58c306995e125d0d183865894f77a1eb16cc7ca536957b9f82ee9ce83d2ab8
|
PDB Path
|
Z:\_ARC\Encrypter 2.0.pdb
|
Weapon type
|
Payload
|
APPENDIX 2 – Applied Countermeasures
Sigma Rules
Payload
APPENDIX 3 – Detailed MITRE ATT&CK® Mapping
Tactic
|
Technique
|
Sub-Technique name
|
Initial Access
|
T1091
|
Replication Through Removable Media
|
Execution
|
T1059
|
Command and Scripting Interpreter
|
T1106
|
Native API
|
T1559.001
|
Component Object Model
|
T1569.002
|
Service Execution
|
T1047
|
Windows Management Instrumentation
|
T1064
|
Scripting
|
T1204.001
|
Malicious Link
|
T1059.003
|
Windows Command Shell
|
Persistence
|
T1543.003
|
Windows Service
|
T1547.001
|
Registry Run Keys / Startup Folder
|
Privilege Escalation
|
T1055
|
Process Injection
|
Defense Evasion
|
T1112
|
Modify Registry
|
T1218
|
System Binary Proxy Execution
|
T1497.003
|
Time Based Evasion
|
T1564.001
|
Hidden Files and Directories
|
T1564.003
|
Hidden Window
|
T1564.004
|
NTFS File Attributes
|
T1036
|
Masquerading
|
T1140
|
Deobfuscate/Decode Files or Information
|
T1070.004
|
File Deletion
|
Discovery
|
T1057
|
Process Discovery
|
T1082
|
System Information Discovery
|
T1083
|
File and Directory Discovery
|
T1120
|
Peripheral Device Discovery
|
T1010
|
Application Window Discovery
|
Collection
|
T1005
|
Data from Local System
|
Impact
|
T1486
|
Data Encrypted for Impact
|
|
T1490
|
Inhibit System Recovery
|
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.