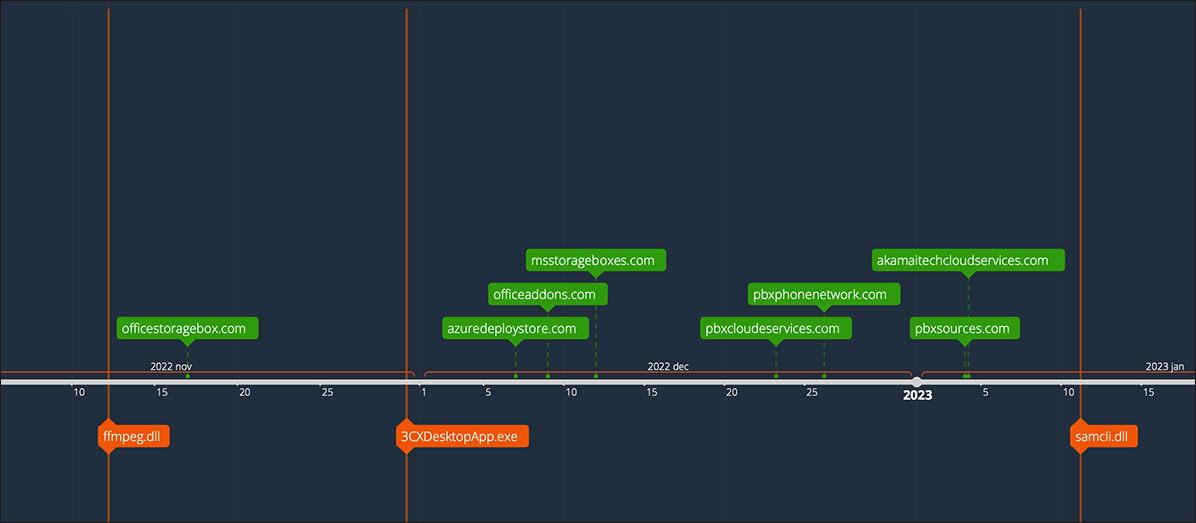
Query to detect “ffmpeg.dll” creation
|
{
"Name": "3CX ffmpeg File Create",
"Description": "Detects when ffmpeg.dll file is created",
"Id": "1cd91ca6-fbd4-4000-b4e1-2f1623e5a526",
"Version": 1,
"SchemaVersion": 1,
"RuleSource": "Cylance",
"ObjectType": "DetectionRule",
"Severity": "High",
"TBM": "High",
"Product": {"Name": "CylanceOPTICS"},
"Plugin": {"Name": "OpticsDetector"},
"OperatingSystems": [{"Name": "Windows"}],
"PostCompletionActions": ["GenerateDetectionEvent"],
"AlertVolume": "TBD",
"MaximumConcurrentActivations": 10,
"ActivationLifetimeLimit": "00:10:00",
"ActivationCanUtilizeDeviceStateEvents": false,
"AllowMultipleActivationsPerContext": true,
"States": [
{
"Name": "dllCreate",
"Scope": "Global",
"Function": "(a)",
"FieldOperators": {
"a": {
"Type": "Contains",
"OperandType": "String",
"Options": {"IgnoreCase": true},
"Operands": [
{
"source": "TargetFile",
"data": "Path"
},
{
"source": "Literal",
"data": "ffmpeg.dll"
}
]
}
},
"ActivationTimeLimit": "-0:00:00.001",
"Actions": [
{
"Type": "AOI",
"ItemName": "InstigatingProcess",
"Position": "PostActivation"
},
{
"Type": "AOI",
"ItemName": "TargetFile",
"Position": "PostActivation"
}
],
"HarvestContributingEvent": true,
"Filters": [
{
"Type": "Event",
"Data": {
"Category": "File",
"SubCategory": "*",
"Type": "Create"
}
}
]
}
]
}
|
Query to detect C2 communication attempts by ffmpeg.dll
|
{
"Name": "3CX ffmpeg DNS Request",
"Description": "Detects when ffmpeg.dll reaches out to known 3CX domains.",
"Id": "7638ba09-1254-4573-968d-fab9ee3f9396",
"Version": 1,
"SchemaVersion": 1,
"RuleSource": "Cylance",
"ObjectType": "DetectionRule",
"Severity": "High",
"TBM": "High",
"Product": {"Name": "CylanceOPTICS"},
"Plugin": {"Name": "OpticsDetector"},
"OperatingSystems": [{"Name": "Windows"}],
"PostCompletionActions": ["GenerateDetectionEvent"],
"AlertVolume": "TBD",
"MaximumConcurrentActivations": 10,
"ActivationLifetimeLimit": "00:10:00",
"ActivationCanUtilizeDeviceStateEvents": false,
"AllowMultipleActivationsPerContext": true,
"States": [
{
"Name": "domainRequest",
"Scope": "Global",
"Function": "(a&b)",
"FieldOperators": {
"a": {
"Type": "ContainsAny",
"OperandType": "String",
"Options": {"IgnoreCase": true},
"Operands": [
{
"source": "InstigatingProcess",
"data": "Name"
},
{
"source": "LiteralSet",
"data": [
"ffmpeg.dll",
"ffmpeg"
]
}
]
},
"b": {
"Type": "ContainsAny",
"OperandType": "String",
"Options": {"IgnoreCase": true},
"Operands": [
{
"source": "TargetDnsRequest",
"data": "Responses/A/1/QuestionName"
},
{
"source": "LiteralSet",
"data": [
"3cx",
"akamaicontainer",
"akamaitechcloudservices",
"azuredeploystore",
"azureonlinecloud",
"azureonlinestorage",
"dunamistrd",
"glcloudservice",
"journalide",
"msedgepackageinfo",
"msstorageazure",
"msstorageboxes",
"officeaddons",
"officestoragebox",
"pbxcloudeservices",
"pbxphonenetwork",
"pbxsources",
"qwepoi123098",
"sbmsa",
"sourceslabs",
"visualstudiofactory",
"zacharryblogs"
]
}
]
}
},
"ActivationTimeLimit": "-0:00:00.001",
"Actions": [
{
"Type": "AOI",
"ItemName": "InstigatingProcess",
"Position": "PostActivation"
},
{
"Type": "AOI",
"ItemName": "TargetDnsRequest",
"Position": "PostActivation"
},
{
"Type": "AOI",
"ItemName": "TargetNetworkConnection",
"Position": "PostActivation"
}
],
"HarvestContributingEvent": true,
"Filters": [
{
"Type": "Event",
"Data": {
"Category": "Network",
"SubCategory": "DNS",
"Type": "Request"
}
}
]
}
]
}
|
Query to detect libffmpeg.dylib creation in the system (macOS)
|
{
"Name": "macOS 3CX ffmpeg File Create",
"Description": "Detects when libffmpeg.dylib file is created",
"Id": "5ef0fb47-2102-4351-9d3a-4872dd96734a",
"Version": 1,
"SchemaVersion": 1,
"RuleSource": "Cylance",
"ObjectType": "DetectionRule",
"Severity": "High",
"TBM": "High",
"Product": {"Name": "CylanceOPTICS"},
"Plugin": {"Name": "OpticsDetector"},
"OperatingSystems": [{"Name": "macOS"}],
"PostCompletionActions": ["GenerateDetectionEvent"],
"AlertVolume": "TBD",
"MaximumConcurrentActivations": 10,
"ActivationLifetimeLimit": "00:10:00",
"ActivationCanUtilizeDeviceStateEvents": false,
"AllowMultipleActivationsPerContext": true,
"States": [
{
"Name": "dylibCreate",
"Scope": "Global",
"Function": "(a)",
"FieldOperators": {
"a": {
"Type": "Contains",
"OperandType": "String",
"Options": {"IgnoreCase": true},
"Operands": [
{
"source": "TargetFile",
"data": "Path"
},
{
"source": "Literal",
"data": "libffmpeg.dylib"
}
]
}
},
"ActivationTimeLimit": "-0:00:00.001",
"Actions": [
{
"Type": "AOI",
"ItemName": "InstigatingProcess",
"Position": "PostActivation"
},
{
"Type": "AOI",
"ItemName": "TargetFile",
"Position": "PostActivation"
}
],
"HarvestContributingEvent": true,
"Filters": [
{
"Type": "Event",
"Data": {
"Category": "File",
"SubCategory": "*",
"Type": "Create"
}
}
]
}
]
}
|
Query to detect C2 communication attempts by libffmpeg.dylib (macOS)
|
{
"Name": "macOS 3CX libffmpeg DNS Request",
"Description": "Detects when libffmpeg.dylib reaches out to known 3CX domains.",
"Id": "0072eda0-c235-4345-aaf3-5905cb1c0806",
"Version": 1,
"SchemaVersion": 1,
"RuleSource": "Cylance",
"ObjectType": "DetectionRule",
"Severity": "High",
"TBM": "High",
"Product": {"Name": "CylanceOPTICS"},
"Plugin": {"Name": "OpticsDetector"},
"OperatingSystems": [{"Name": "macOS"}],
"PostCompletionActions": ["GenerateDetectionEvent"],
"AlertVolume": "TBD",
"MaximumConcurrentActivations": 10,
"ActivationLifetimeLimit": "00:10:00",
"ActivationCanUtilizeDeviceStateEvents": false,
"AllowMultipleActivationsPerContext": true,
"States": [
{
"Name": "domainRequest",
"Scope": "Global",
"Function": "(a&b)",
"FieldOperators": {
"a": {
"Type": "ContainsAny",
"OperandType": "String",
"Options": {"IgnoreCase": true},
"Operands": [
{
"source": "InstigatingProcess",
"data": "Name"
},
{
"source": "LiteralSet",
"data": [
"libffmpeg.dylib",
"libffmpeg"
]
}
]
},
"b": {
"Type": "ContainsAny",
"OperandType": "String",
"Options": {"IgnoreCase": true},
"Operands": [
{
"source": "TargetDnsRequest",
"data": "Responses/A/1/QuestionName"
},
{
"source": "LiteralSet",
"data": [
"3cx",
"akamaicontainer",
"akamaitechcloudservices",
"azuredeploystore",
"azureonlinecloud",
"azureonlinestorage",
"dunamistrd",
"glcloudservice",
"journalide",
"msedgepackageinfo",
"msstorageazure",
"msstorageboxes",
"officeaddons",
"officestoragebox",
"pbxcloudeservices",
"pbxphonenetwork",
"pbxsources",
"qwepoi123098",
"sbmsa",
"sourceslabs",
"visualstudiofactory",
"zacharryblogs"
]
}
]
}
},
"ActivationTimeLimit": "-0:00:00.001",
"Actions": [
{
"Type": "AOI",
"ItemName": "InstigatingProcess",
"Position": "PostActivation"
},
{
"Type": "AOI",
"ItemName": "TargetDnsRequest",
"Position": "PostActivation"
},
{
"Type": "AOI",
"ItemName": "TargetNetworkConnection",
"Position": "PostActivation"
}
],
"HarvestContributingEvent": true,
"Filters": [
{
"Type": "Event",
"Data": {
"Category": "Network",
"SubCategory": "DNS",
"Type": "Request"
}
}
]
}
]
}
|
Query to detect generic request to C2s used in the 3CX attack on Windows
|
{
"Name": "3CX DNS Request",
"Description": "Detects when a dns request is made to known 3CX domains.",
"Id": "6abb19ad-9490-488f-a9e0-dc51694d4b1b",
"Version": 1,
"SchemaVersion": 1,
"RuleSource": "Cylance",
"ObjectType": "DetectionRule",
"Severity": "High",
"TBM": "High",
"Product": {"Name": "CylanceOPTICS"},
"Plugin": {"Name": "OpticsDetector"},
"OperatingSystems": [{"Name": "Windows"}],
"PostCompletionActions": ["GenerateDetectionEvent"],
"AlertVolume": "TBD",
"MaximumConcurrentActivations": 10,
"ActivationLifetimeLimit": "00:10:00",
"ActivationCanUtilizeDeviceStateEvents": false,
"AllowMultipleActivationsPerContext": true,
"States": [
{
"Name": "domainRequest",
"Scope": "Global",
"Function": "(a)",
"FieldOperators": {
"a": {
"Type": "ContainsAny",
"OperandType": "String",
"Options": {"IgnoreCase": true},
"Operands": [
{
"source": "TargetDnsRequest",
"data": "Responses/A/1/QuestionName"
},
{
"source": "LiteralSet",
"data": [
"3cx",
"akamaicontainer",
"akamaitechcloudservices",
"azuredeploystore",
"azureonlinecloud",
"azureonlinestorage",
"dunamistrd",
"glcloudservice",
"journalide",
"msedgepackageinfo",
"msstorageazure",
"msstorageboxes",
"officeaddons",
"officestoragebox",
"pbxcloudeservices",
"pbxphonenetwork",
"pbxsources",
"qwepoi123098",
"sbmsa",
"sourceslabs",
"visualstudiofactory",
"zacharryblogs"
]
}
]
}
},
"ActivationTimeLimit": "-0:00:00.001",
"Actions": [
{
"Type": "AOI",
"ItemName": "InstigatingProcess",
"Position": "PostActivation"
},
{
"Type": "AOI",
"ItemName": "TargetDnsRequest",
"Position": "PostActivation"
},
{
"Type": "AOI",
"ItemName": "TargetNetworkConnection",
"Position": "PostActivation"
}
],
"HarvestContributingEvent": true,
"Filters": [
{
"Type": "Event",
"Data": {
"Category": "Network",
"SubCategory": "DNS",
"Type": "Request"
}
}
]
}
]
}
|
Query to detect generic request to C2s used in the 3CX attack on macOS
|
{
"Name": "macOS 3CX DNS Request",
"Description": "Detects when a dns request is made to known 3CX domains.",
"Id": "a2ca3af8-778d-4a6e-ac05-400ee2bf2ae6",
"Version": 1,
"SchemaVersion": 1,
"RuleSource": "Cylance",
"ObjectType": "DetectionRule",
"Severity": "High",
"TBM": "High",
"Product": {"Name": "CylanceOPTICS"},
"Plugin": {"Name": "OpticsDetector"},
"OperatingSystems": [{"Name": "macOS"}],
"PostCompletionActions": ["GenerateDetectionEvent"],
"AlertVolume": "TBD",
"MaximumConcurrentActivations": 10,
"ActivationLifetimeLimit": "00:10:00",
"ActivationCanUtilizeDeviceStateEvents": false,
"AllowMultipleActivationsPerContext": true,
"States": [
{
"Name": "domainRequest",
"Scope": "Global",
"Function": "(a)",
"FieldOperators": {
"a": {
"Type": "ContainsAny",
"OperandType": "String",
"Options": {"IgnoreCase": true},
"Operands": [
{
"source": "TargetDnsRequest",
"data": "Responses/A/1/QuestionName"
},
{
"source": "LiteralSet",
"data": [
"3cx",
"akamaicontainer",
"akamaitechcloudservices",
"azuredeploystore",
"azureonlinecloud",
"azureonlinestorage",
"dunamistrd",
"glcloudservice",
"journalide",
"msedgepackageinfo",
"msstorageazure",
"msstorageboxes",
"officeaddons",
"officestoragebox",
"pbxcloudeservices",
"pbxphonenetwork",
"pbxsources",
"qwepoi123098",
"sbmsa",
"sourceslabs",
"visualstudiofactory",
"zacharryblogs"
]
}
]
}
},
"ActivationTimeLimit": "-0:00:00.001",
"Actions": [
{
"Type": "AOI",
"ItemName": "InstigatingProcess",
"Position": "PostActivation"
},
{
"Type": "AOI",
"ItemName": "TargetDnsRequest",
"Position": "PostActivation"
},
{
"Type": "AOI",
"ItemName": "TargetNetworkConnection",
"Position": "PostActivation"
}
],
"HarvestContributingEvent": true,
"Filters": [
{
"Type": "Event",
"Data": {
"Category": "Network",
"SubCategory": "DNS",
"Type": "Request"
}
}
]
}
]
}
|