Unified Endpoint Management: What Security and IT Leaders Value Most
Mobile devices pose the weakest link in your security framework. That’s the conclusion reached by 68% of cybersecurity leaders, based on our recent report, “The Definitive Guide to Enterprise Mobile Security.”
Fortunately, there is cause for optimism. More leaders are taking action to address the problem by including mobile endpoints in their overall cybersecurity strategy — a vital step because increasingly, this is where valuable data resides. To accomplish this, CIOs and CISOs are turning to a unified endpoint management (UEM) focus on security, while maintaining minimal friction between cybersecurity, IT, and mobile teams. Through years of helping secure a wide range of organizations, BlackBerry customers have taught us what they value most in a UEM offering. In this blog, I share what we’ve learned.
The UEM Checklist
To help with your search for the UEM offering that best fits your organization’s needs, below is a quick checklist for you to consider as you shop.
1. Advanced Mobile Security Must Come “Standard”
The UEM must be able to flag jailbroken devices, detect insecure Wi-Fi, and come standard with AI-powered mobile threat defense (MTD) capabilities. These artificial intelligence-infused features must be able to block malware infections, prevent URL phishing attacks, and provide application integrity checks. Moreover, the UEM client must be able to perform these activities offline with no need for human intervention.
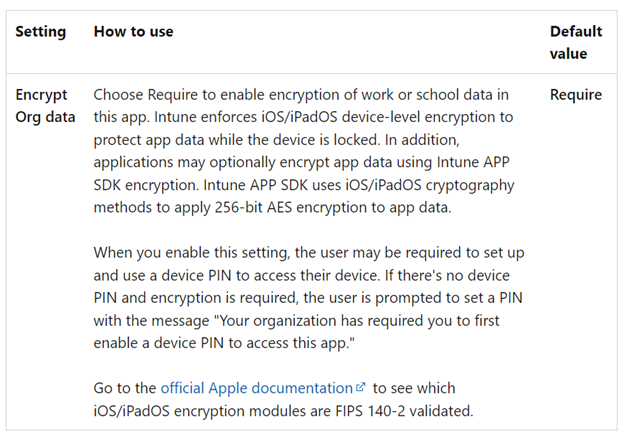
2. Containerization
Many vendors offer app containerization, but there are two concerns security leaders need to be aware of as they can undermine an organization’s security efforts. First, not all containerization solutions offer third-party app-level encryption independent of a mobile device’s operating system (OS), instead opting to rely on the OS’s device-level encryption to protect app data, see Figure 1. The need for concern is that in many cases OS encryption is only in place when the device is in a locked state. So, if a user has malware on their smartphone, it could be stealing data while they use their device.
The second concern is when a cryptographic vulnerability is found in a mobile device’s operating system – which is a regular occurrence. It depends on the vulnerability, but the priority level the OS vendor assigns the issue can be very different from what other organizations would want. It can be a matter of days or a matter of years before the problem is fixed. During that time, employees whose phones use the OS are more vulnerable targets of malicious activities such as information stealing, credential theft, and session hijacking. To achieve a higher and consistent level of security across devices, independence from the OS is vital.
Fortunately, advanced UEM offerings solve the issue, as they have their own data encryption capabilities, separate from the OS. This independence ensures that any work data that is saved is always encrypted. Independence from the operating system also helps protect sensitive work data from attacks leveraging the frequently discovered vulnerabilities on mobile device operating systems. Reporting from cvedetails.com for 2022 shows an average of one new vulnerability per day on iOS® and about two per day on Android™.
Containerization also makes BYOD (bring your own device) deployment easier because it can enable the creation of VPN (virtual private network) policies for specific apps. This feature is called “per-app VPN.” This allows a container to deliver per-app VPN without need of a separate mobile device management (MDM) solution. In BYOD deployments where the organization can’t deploy MDM, this is a valuable capability, because without it the organization loses the ability to control many security features. Proper containerization addresses this issue by allowing for full control of apps, connectivity, and data within the container — without an MDM solution.
3. Software Development Kits
The UEM should offer security-focused APIs in their software development kits (SDKs) and require third-party vendors to use them. Any app built using the SDK should be validated by the UEM vendor to ensure the app is using security-focused APIs rather than standard OS APIs, such as SecureSaveAs versus SaveAs, for example.
Final Thoughts
One of the biggest mistakes in mobile security is to assume that a bundled mobile device management platform, which you receive for little-to-no cost, will deliver the mobile security you need and want. Our CEO, John Chen, wrote about this in his article, “Bundled Mobile Security: Is It Enough?” The answer is a resounding “no,” and I think he explains it best.
He says that it may seem like you’re getting a great deal by bundling your mobile management, productivity suite, and perhaps even your endpoint security vendor all in one. But even if you paid nothing, you may still be shortchanging yourself in areas that are critical to your organization.
Instead, we recommend that you layer a highly secure and specialized UEM platform — such as BlackBerry® UEM — on top of your existing MDM or MAM (mobile application management) solution. This can augment and add value to what you already have, and more specifically, eliminate gaps in your mobile security that may otherwise leave your organization vulnerable.
For similar articles and news delivered to your inbox, please subscribe to the BlackBerry blog.
Related Reading