Indicator Type
|
Indicator
|
MD5
|
b7e63b7247be18cdfb36c1f3200c1dba
|
SHA256
|
8af93bed967925b3e5a70d0ad90eae1f13bc6e362ae3dac705e984f8697aaaad
|
MD5
|
5efddbdcf40ba01f1571140bad72dccb
|
SHA256
|
a45258389a3c0d4615f3414472c390a0aabe77315663398ebdea270b59b82a5c
|
MD5
|
3b853ae547346befe5f3d06290635cf6
|
SHA256
|
bc9d4eb09711f92e4e260efcf7e48906dca6bf239841e976972fd74dac412e2f
|
MD5
|
666b2b178ce52e30be9e69de93cc60a9
|
SHA256
|
cd09bf437f46210521ad5c21891414f236e29aa6869906820c7c9dc2b565d8be
|
MD5
|
ef00004a1ebc262ffe0fb89aa5524d42
|
SHA256
|
a3283520e04d7343ce9884948c5d23423499fa61cee332a006db73e2b98d08c3
|
MD5
|
6c7d24b90f3c6b4383bd7d08374a0c6f
|
SHA256
|
4db0a2d4d011f43952615ece8734ca4fc889e7ec958acd803a6c68b3e0f94eea
|
MD5
|
73750f08265bbe80c3f235318bcef6fe
|
SHA256
|
bc3c6f9d51e2bdb37e03b01e2949f72836ecee4230e2320c5dc33a83b55b062f
|
MD5
|
16341fcff1bc7388387fd17b4b3a7a50
|
|
cf1f4ec1d7db6cf1fe8e15687b348a279889689fa9c387de4a2c310c34336f9f
|
MD5
|
1c62441de076eb5a5b2e1f8146767777
|
SHA256
|
75079e408ca9517825ffac396680a2d2169d691be3f1adbbd797e05e665c6fde
|
MD5
|
dacdb33b6e9de4c1fe8591bb5a65c55c
|
SHA256
|
cde768a4cf95e58f0e98e2bcca0663fd2c1a36510f6010065b4f54169a92e207
|
MD5
|
709e6a64735432c25cafb89951cc149c
|
SHA256
|
a2a9fd1db7f1dc196fa8af0669ea72d1f8ae48bf4775108ee746e0f83c5a7498
|
URL
|
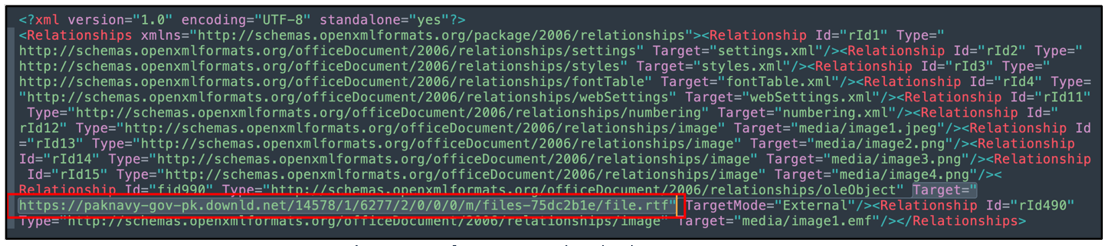
hxxps[:]//paknavy-gov-pkp[.]downld[.]net/14578/1/6277/2/0/0/0/m/files-75dc2b1e/file[.]rtf
|
URL
|
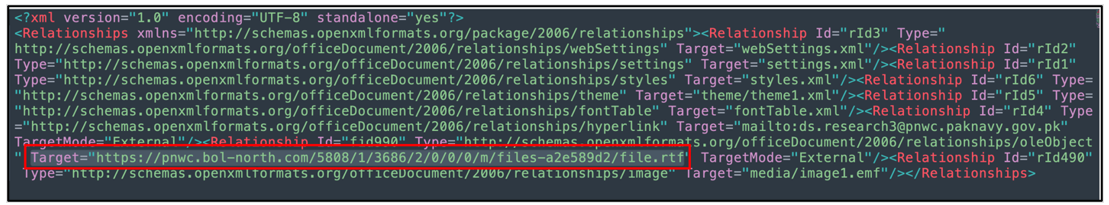
hxxps[:]//pnwc[.]bol-north[.]com/5808/1/3686/2/0/0/0/m/files-a2e589d2/file[.]rtf
|
IP
|
185.205.187[.]234
|
IP
|
5.230.73[.]106
|
URL
|
https[:]//cstc-spares-vip-163.dowmload[.]net/14668/1/1228/2/0/0/0/m/files-403a1120/file[.]rtf
|
URL
|
https[:]//mtss.bol-south[.]org/5974/1/8682/2/0/0/0/m/files-b2dff0ca/file[.]rtf
|
URL
|
https[:]//paknavy-gov-pk[.]downld[.]net/14578/1/6277/2/0/0/0/m/files-75dc2b1e/file[.]rtf
|
URL
|
hxxts[:]//paknavy-gov-pk[.]downld[.]net/14578/1/6277/2/0/0/0/m/files-75dc2b1e/file[.]rtf
|
URL
|
hxxts[:]//pnwc[.]bol-north[.]com/5808/1/3686/2/0/0/0/m/files-a2e589d2/file[.]rtf
|
URL
|
hxxts[:]//sl-navy[.]office-drive[.]live/45/1/334/2/0/0/0/m/files-fe9dade2/file[.]rtf
|
URL
|
hxxts[:]//forecast[.]comsats-net[.]com/5760/1/5041/2/0/0/0/m/files-dd96433f/file[.]rtf
|
URL
|
https[:]//forecast[.]comsats-net[.]com/5760/1/5039/2/0/0/0/m/files-d7c7dda1/file[.]rtf
|
URL
|
hxxts[:]//forecast[.]comsats-net[.]com/5760/1/5035/2/0/0/0/m/files-4a0480ae/file[.]rtf
|
URL
|
hxxts[:]//moma[.]comsats-net[.]com/5753/1/4375/2/0/0/0/m/files-8062311a/file[.]rtf
|
URL
|
hxxts[:]//forecast[.]comsats-net[.]com/5760/1/5040/2/0/0/0/m/files-f3b20b30/file[.]rtf
|
URL
|
hxxts[:]//forecast[.]comsats-net[.]com/5760/1/5036/2/0/0/0/m/files-2ad09cbd/file[.]rtf
|
URL
|
hxxts[:]//moma[.]comsats-net[.]com/5753/1/4371/2/0/0/0/m/files-b62d382f/file[.]rtf
|
URL
|
hxxts[:]//srilanka-navy[.]lforvk[.]com/135/1/334/2/0/0/0/m/files-4fdaf6c7/file[.]rtf
|
URL
|
hxxts[:]//promotionlist[.]comsats-net[.]com/5756/1/8887/2/0/0/0/m/files-3d1dff0f/file[.]rtf
|
URL
|
hxxts[:]//dgms[.]paknavy-gov[.]com/5733/1/5051/2/0/0/0/m/files-73bdca4d/file[.]rtf
|
URL
|
hxxts[:]//mofadividion[.]ptcl-gov[.]com/5724/1/3268/2/0/0/0/m/files-11e30891/file[.]rtf
|
URL
|
hxxts[:]//ksew[.]kpt-gov[.]org/5663/1/3275/2/0/0/0/m/files-937950ad/file[.]rtf
|
URL
|
hxxts[:]//ministryofforeignaffairs-mofa-gov-pk[.]dytt88[.]org/14444/1/2454/2/0/0/0/m/files-9ba90b7f/file[.]rtf
|
URL
|
hxxt[:]//bdmil[.]alit[.]live/3398/1/50073/2/0/0/0/m/files-ac995f17/file[.]rtf
|
URL
|
hxxt[:]//navy-mil-bd[.]jmicc[.]xyz/5625/1/8145/2/0/0/0/m/files-b11074b7/file[.]rtf
|
URL
|
hxxts[:]//navy-mil-bd[.]jmicc[.]xyz/5625/1/8145/2/0/0/0/m/files-b11074b7/file[.]rtf
|
URL
|
hxxts[:]//paknavy[.]jmicc[.]xyz/5627/1/4367/2/0/0/0/m/files-9e0912cc/file[.]rtf
|
URL
|
hxxt[:]//bdmil[.]alit[.]live/3398/1/54346/2/0/0/0/m/files-491dc489/file[.]rtf
|
URL
|
hxxts[:]//paknavy[.]comsats[.]xyz/5552/1/5037/2/0/0/0/m/files-1b5c7556/file[.]rtf
|
URL
|
hxxts[:]//mofa-gov[.]interior-pk[.]org/14419/1/6/2/0/0/0/m/files-07b01f9b/file[.]rtf
|
URL
|
hxxt[:]//mofa-gov[.]interior-pk[.]org/14419/1/6/2/0/0/0/m/files-07b01f9b/file[.]rtf
|
URL
|
hxxts[:]//paknavy[.]paknavy[.]live/5516/1/4367/2/0/0/0/m/files-db71f6b3/file[.]rtf
|
URL
|
hxxts[:]//mofabn[.]ksewpk[.]com/5511/1/4993/2/0/0/0/m/files-18e5db65/file[.]rtf
|
URL
|
hxxt[:]//srilankanavy[.]ksew[.]org/5471/1/1101/2/0/0/0/m/files-cd6e6dbd/file[.]rtf
|
URL
|
hxxts[:]//srilankanavy[.]ksew[.]org/5471/1/1101/2/0/0/0/m/files-cd6e6dbd/file[.]rtf
|
URL
|
hxxt[:]//maritimepakistan[.]kpt-pk[.]net/5434/1/3694/2/0/0/0/m/files-ce32ed85/file[.]rtf
|
URL
|
hxxts[:]//maritimepakistan[.]kpt-pk[.]net/5434/1/3694/2/0/0/0/m/files-ce32ed85/file[.]rtf
|
URL
|
hxxt[:]//dgmp-paknavy[.]mod-pk[.]com/14325/1/10/2/0/0/0/m/files-5291bef6/file[.]rtf
|
URL
|
hxxts[:]//dgmp-paknavy[.]mod-pk[.]com/14325/1/10/2/0/0/0/m/files-5291bef6/file[.]rtf
|
URL
|
hxxt[:]//dgpr[.]paknvay-pk[.]net/5330/1/1330/2/0/0/0/m/files-4d9d0395/file[.]rtf
|
URL
|
hxxts[:]//cabinet-gov-pk[.]ministry-pk[.]net/14300/1/1273/2/0/0/0/m/files-68ebf815/file[.]rtf
|
URL
|
hxxts[:]//dgpr[.]paknvay-pk[.]net/5330/1/1330/2/0/0/0/m/files-4d9d0395/file[.]rtf
|
URL
|
hxxts[:]//careitservices[.]paknvay-pk[.]net/5359/1/4586/2/0/0/0/m/files-266ad911/file[.]rtf
|
URL
|
hxxts[:]//defencelk[.]cvix[.]live/3023/1/54082/2/0/0/0/m/files-0c31ed2d/file[.]rtf
|
URL
|
hxxt[:]//mohgovsg[.]bahariafoundation[.]live/5320/1/13/2/0/0/0/m/files-1ddf5195/file[.]rtf
|
URL
|
hxxts[:]//mohgovsg[.]bahariafoundation[.]live/5320/1/13/2/0/0/0/m/files-1ddf5195/file[.]rtf
|
URL
|
hxxts[:]//sppc[.]moma-pk[.]org/5281/1/4265/2/0/0/0/m/files-d2608a99/file[.]rtf
|
URL
|
hxxps[:]//mailrta.mfagov[.]org/3818/1/53382/2/0/0/0/m/files-c78a6966/file[.]rtf
|
URL
|
http[:]//mailnavybd.govpk[.]net/5845/1/12/2/0/0/0/m/files-ca78574e/file[.]rtf
|
URL
|
hxxts[:]//mailaplf[.]cvix[.]live/2968/1/50390/2/0/0/0/m/files-7630e91a/file[.]rtf
|
URL
|
hxxt[:]//slpa[.]mod-gov[.]org/5946/1/5775/2/0/0/0/m/files-fca3cc50/file[.]rtf
|
URL
|
hxxt[:]//slpa[.]mod-gov[.]org/5946/1/5780/2/0/0/0/m/files-20bba5af/file[.]rtf
|
URL
|
hxxt[:]//slpa[.]mod-gov[.]org/5946/1/5795/2/0/0/0/m/files-c9dddc54/file[.]rtf
|
URL
|
hxxt[:]//slpa[.]mod-gov[.]org/5946/1/5797/2/0/0/0/m/files-875e140b/file[.]rtf
|
URL
|
hxxt[:]//slpa[.]mod-gov[.]org/5946/1/5771/2/0/0/0/m/files-5995311a/file[.]rtf
|
URL
|
hxxt[:]//slpa[.]mod-gov[.]org/5946/1/5784/2/0/0/0/m/files-94153639/file[.]rtf
|
URL
|
hxxt[:]//slpa[.]mod-gov[.]org/5946/1/5770/2/0/0/0/m/files-2d21c32e/file[.]rtf
|
URL
|
hxxt[:]//slpa[.]mod-gov[.]org/5946/1/5778/2/0/0/0/m/files-27d5c7d3/file[.]rtf
|
URL
|
hxxt[:]//mailnavymilbd[.]govpk[.]net/5848/1/13/2/0/0/0/m/files-57d837e4/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5792/2/0/0/0/m/files-da7756e4/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5776/2/0/0/0/m/files-175c56e7/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5783/2/0/0/0/m/files-a26663eb/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5780/2/0/0/0/m/files-20bba5af/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5785/2/0/0/0/m/files-76f11745/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5788/2/0/0/0/m/files-3acec3be/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5782/2/0/0/0/m/files-78d7e141/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5796/2/0/0/0/m/files-97e02960/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5795/2/0/0/0/m/files-c9dddc54/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5790/2/0/0/0/m/files-a3d0041a/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5773/2/0/0/0/m/files-5a31d681/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5799/2/0/0/0/m/files-03dd18bd/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5781/2/0/0/0/m/files-62caea91/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5804/2/0/0/0/m/files-c43dece3/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5794/2/0/0/0/m/files-60cb1621/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5775/2/0/0/0/m/files-fca3cc50/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5778/2/0/0/0/m/files-27d5c7d3/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5787/2/0/0/0/m/files-fb528413/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5786/2/0/0/0/m/files-5def1d52/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5798/2/0/0/0/m/files-c3178f3d/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5779/2/0/0/0/m/files-2f2e186d/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5789/2/0/0/0/m/files-8822f8ff/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5777/2/0/0/0/m/files-7f2e758b/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5791/2/0/0/0/m/files-bda6f896/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5769/2/0/0/0/m/files-2f6b9c9a/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5774/2/0/0/0/m/files-12eca223/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5772/2/0/0/0/m/files-84c4942a/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5771/2/0/0/0/m/files-5995311a/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5797/2/0/0/0/m/files-875e140b/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5784/2/0/0/0/m/files-94153639/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5770/2/0/0/0/m/files-2d21c32e/file[.]rtf
|
URL
|
hxxts[:]//slpa[.]mod-gov[.]org/5946/1/5793/2/0/0/0/m/files-f2d0617e/file[.]rtf
|
URL
|
hxxts[:]//mailrta[.]mfagov[.]org/3818/1/53382/2/0/0/0/m/files-c78a6966/file[.]rtf
|
URL
|
hxxt[:]//promotionlist[.]comsats-net[.]com/5756/1/8887/2/0/0/0/m/files-3d1dff0f/file[.]rtf
|
URL
|
hxxts[:]//mailnavymilbd[.]govpk[.]net/5848/1/13/2/0/0/0/m/files-57d837e4/file[.]rtf
|
URL
|
hxxt[:]//mailnavybd[.]govpk[.]net/5845/1/12/2/0/0/0/m/files-ca78574e/file[.]rtf
|
Domain
|
slpa.mod-gov[.]org
|
IP
|
62.113.255[.]80
|
Domain
|
mailrta.mfagov[.]org
|
IP
|
194.61.121[.]216
|
Domain
|
promotionlist.comsats-net[.]com
|
IP
|
5.255.104[.]32
|
Domain
|
mailnavybd.govpk[.]net
|
IP
|
5.255.112[.]194
|
Domain
|
mailnavymilbd.govpk[.]net
|