BlackBerry AI Cybersecurity Effective Against Turla
BlackBerry, the pioneer of AI-based cybersecurity, is effective in MITRE Engenuity tests, preventing the Turla threat group’s objectives by disrupting malicious behaviors in early phases of the kill chain.
Today, MITRE Engenuity published the results of the fifth round of MITRE ATT&CK® Evaluations. Thirty-one vendors were tested on their ability to defend against the tactics, techniques, and procedures (TTPs) leveraged by one of today’s most notorious advanced persistent threat (APT) groups: Turla.
The evaluation took place over a period of four days, with three days focusing on detections, and one day examining protection capabilities. For detection, nineteen tests were executed using malicious techniques attributed to Turla. For protection, thirteen tests were conducted.
Highlights of BlackBerry Results
Here are some of the achievements of BlackBerry Cylance® AI during this evaluation:
- Actionable Alerts: CylanceENDPOINT™ generated effective alerts in key moments, with rich context to minimize false positives. This demonstrates the effectiveness and time savings achieved through BlackBerry’s AI-based endpoint protection platform (EPP).
- Enhanced Visibility: BlackBerry made substantial enhancements to the network sensors for both CylanceENDPOINT and BlackBerry’s cloud-native, AI-assisted ZTNA (zero trust network access) solution CylanceGATEWAY™, to ensure users can easily locate and review suspicious activity on the network traffic data source.
- Preventative Security: CylanceENDPOINT blocked multiple stages of Turla’s emulated behaviors in early phases of the kill chain, preventing lateral movement — one of the group’s key objectives.
Over time, evaluations have become more sophisticated, requiring vendors to “up their game” to keep pace with the market and surpass evaluation expectations. BlackBerry’s goal in participating is to fine-tune its products and share expertise, to continue to deliver the value customers both deserve and expect.
Getting to Know the Adversary: Turla
Active since at least the early 2000s, Turla is a sophisticated APT group believed to be operating out of Russia. The group has infected victims in over 45 countries, and has been known to target government agencies, diplomatic missions and military groups, as well as research and media organizations. Turla adopts novel and sophisticated techniques to maintain their own operational security, including the use of a distinctive command-and-control (C2) network in concert with their repertoire of open source and in-house tools.
Turla is well-known for executing highly targeted campaigns aimed at exfiltrating sensitive information from Linux and Windows infrastructure. The group relies on a variety of innovative and stealthy techniques to silently make their way through a target’s network. After establishing a foothold and conducting enumeration of its target, Turla persists with a minimal footprint through in-memory or kernel implants.
BlackBerry Results: In Depth
The MITRE evaluation provides us with an opportunity to showcase where BlackBerry’s portfolio stands out in terms of reducing alert fatigue and providing visibility into the system.
When an endpoint is under attack by an adversary, time is the most crucial element in the attack chain. A network breach can lead to progressively worse security outcomes the longer it remains undetected — especially for a threat group like Turla, whose tactics include dropping so-called "second-stage" malware, which is activated after a target’s initial infection and is used to establish a backdoor into the victim network.
The group then searches for sensitive information to steal and moves laterally within the network to gain access to other systems. BlackBerry Cylance AI “silences” cyberattacks through unique, preventative solutions that stop infections in the earliest stages of the kill chain, halting malware pre-execution. With Cylance AI, BlackBerry delivers prevention-first, predictive security with visibility across the enterprise to combat the most notorious and advanced cyberattacks.
It is important to note that MITRE does not rank or score as part of their evaluations. Although numbers can be useful from a security practitioner’s perspective to show how our products measure up, context and timing are the most relevant pieces of information brought to light by MITRE’s testing.
Alert Actionability
As evidenced by our test results, we have demonstrated the effectiveness of our portfolio’s detections by generating accurate alerts with rich context for security operations center (SOC) analysts to better understand malicious activities or potential risks.
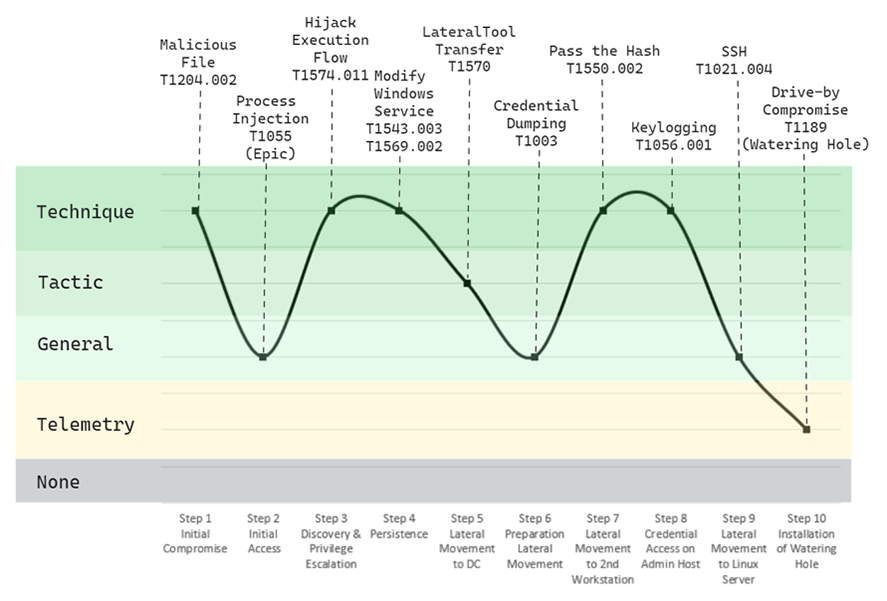
Figure 1 — Emulated Turla attack targeting both Windows and Linux infrastructure by deploying specific malware (EPIC, CARBON-DLL, and PENQUIN) on Day 1 of testing.
Evaluation Day 1:
During Day 1 of MITRE’s evaluation, we were able to provide solid visibility across key steps in the attack chain. As shown in the above graph, the initial compromise was fully detected, as well as the DLL injections intended as a stealth method to compromise the victim system.
CylanceENDPOINT excelled in detecting the privilege escalation attempt in which the registry was modified to facilitate persistence through the execution of a malicious masquerading service, providing alerts for this entire process.
Continuing along the chain, our emulated Turla intrusion next moves to the domain controller via a password-spray attack. Alerts were raised and complemented with contextual telemetry to give the analyst full visibility into the attempt at lateral movement. Towards the end of the first day of testing, CylanceENDPOINT also provided alerts for attempted lateral movement into the Linux server and served up additional context for the drive-by compromise attempt—installation of the watering hole.
Evaluation Day 2:
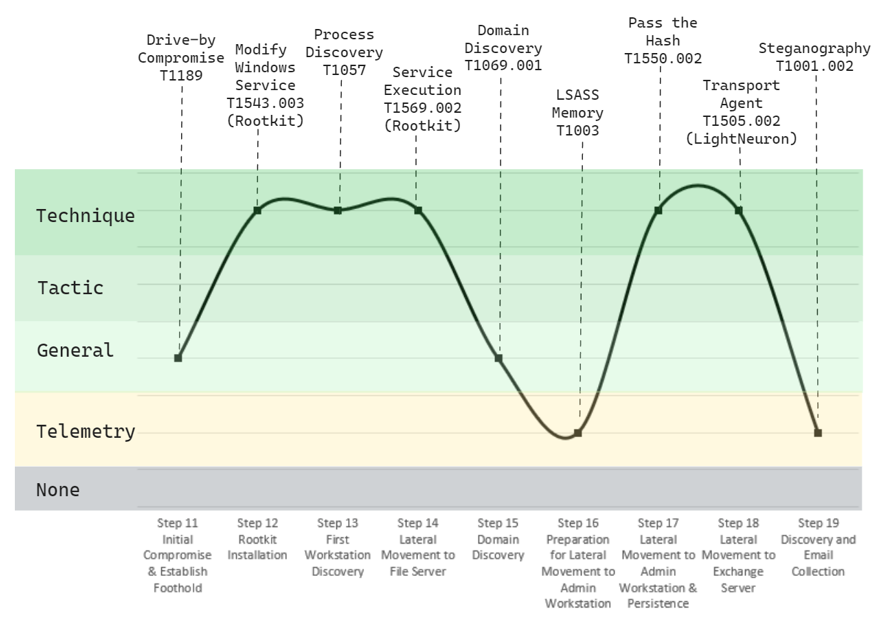
Figure 2 — Emulated Turla attack focusing on kernel and Microsoft Exchange exploitation using action-specific malware (EPIC, SNAKE, and LIGHTNEURON) on Day 2 of testing.
During Day 2 of the MITRE evaluation, CylanceENDPOINT provided full visibility into key parts of the attack chain. As shown in the graph above, Turla’s emulated steps from initial access to the installation of the watering hole — as well as rootkit installation and its subsequent execution — were detected with precise alerts intended to provide defenders with a clear picture of the simulated attack. With that initial context laid out before them, a SOC analyst would be able to quickly and accurately identify each of these threats.
CylanceOPTICS®, a component of CylanceENDPOINT, is the BlackBerry endpoint detection and response (EDR) solution. It collects and analyzes forensic data from devices to identify and resolve threats before they impact your organization. It also adds additional context to this data by facilitating the detection of discovery activities relevant to the attack. The solution provides timely alerts for covert malicious behavior such as application programming interface (API) call usage, or other less common discovery methods.
Another highlight of Day 2’s testing was the detection of stolen password hashes intended to facilitate the attacker’s lateral movement within a network. In a real-life attack, this action would be quickly detected by a SOC analyst thanks to CylanceENDPOINT alerts, allowing their teams to take immediate steps to prevent an attacker's lateral movement through the network.
As a grand finale to the simulated attack, Turla’s LightNeuron implant was covertly installed as a Microsoft Exchange Transport Agent, with the goal of exfiltrating the user’s emails. Light Neuron uses steganography to obscure its C2 communication. Even trained human observers can struggle to detect this technique, but CylanceENDPOINT provides immediate visibility and context so an analyst can take steps to halt this malicious activity.
Visibility: Key Data Sources
Having good visibility into the activity occurring in your environment is key for providing context to the story or flow behind certain suspicious or malicious actions. There is no need for the detection of all activity (such as simple discovery commands), but it’s important to have the right visibility or telemetry available if the security team wants to fully understand the details surrounding a meaningful detection.
Different sources of information, when put together, can provide the necessary details about any given action that takes place within your network. These data sources provide valuable information about events occurring both in the network and on individual endpoints, helping SOC analysts make better decisions, determine the cause of intrusion attempts, and to protect company assets by taking proactive measures.
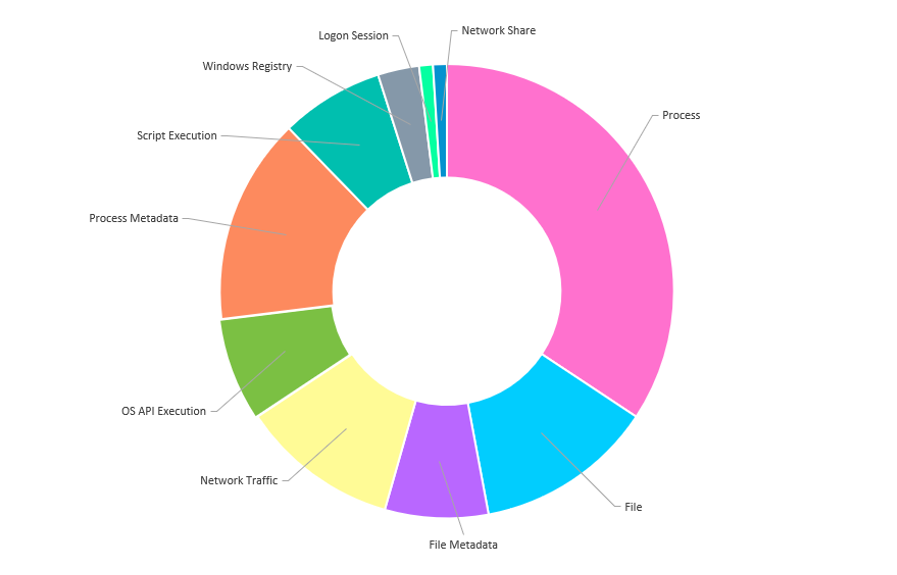
For the Turla emulation, BlackBerry’s visibility into the event was supported by a set of unique data sources. In the following graph, you can see the top 10 data sources used to provide human analysts with context on the simulated intrusion attempt:
Figure 3 — Top 10 data sources used to provide situational context to anomalies.
BlackBerry continuously innovates and enhances product capabilities. For example, this year our team enhanced network sensors for both CylanceOPTICS and CylanceGATEWAY™ to ensure users can easily view suspicious activity on the Network Traffic data source. CylanceOPTICS provides advanced endpoint threat visibility with investigation, response, and threat-hunting capabilities across devices. Thanks to this capability, we had additional visibility to easily view key command-and-control steps where the malicious activity was hidden inside HTTP traffic or encoded and/or encrypted in the MITRE tests.
The Importance of Time-Based Security
Time-based security is a critical concept to help organizations improve their security posture against attacks, helping analysts react quickly and therefore limit the scope of an attack.
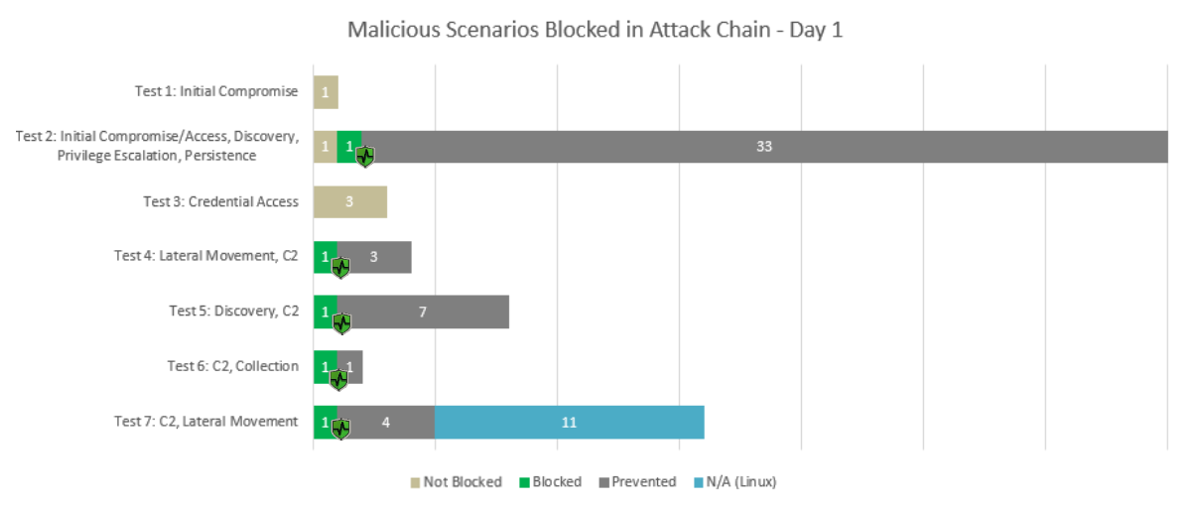
During the MITRE evaluation, BlackBerry demonstrated its protection efficacy across its portfolio, blocking eleven steps in the very early stages of the attack chain.
Figure 4 — On Day 1 of MITRE testing, the graph above shows the types of malicious scenarios blocked and at what stage of the attack chain they were prevented.
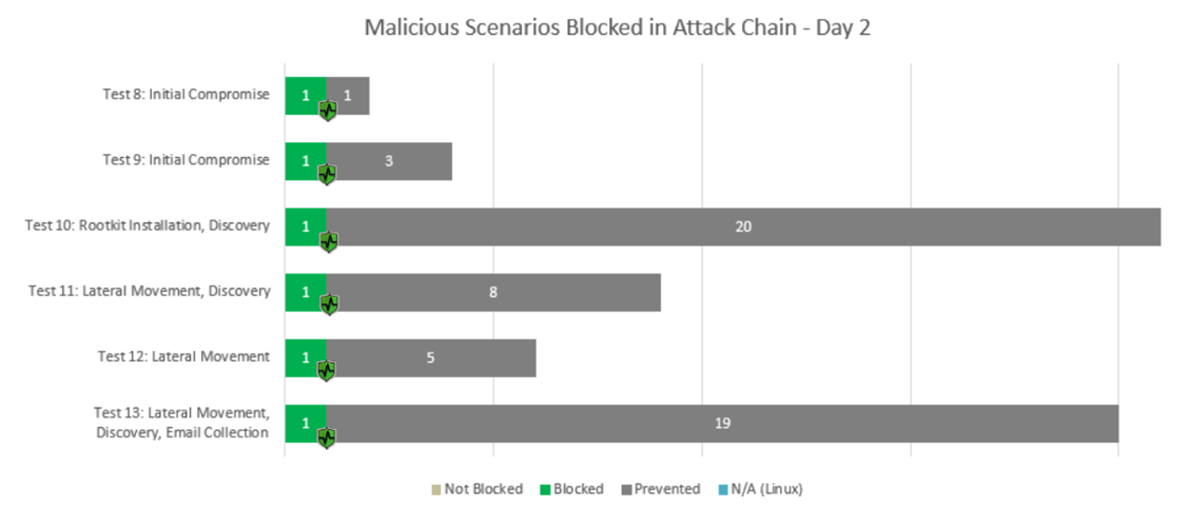
Figure 5 — On Day 2 of MITRE testing, the graph above shows the types of malicious scenarios blocked and at what stage of the attack chain they were prevented.
As seen in both examples above, Cylance AI stopped the most relevant emulated attacks in their initial stages. During Test 10, for instance, BlackBerry prevented rootkit installation, effectively blocking one of the foundational pillars of a typical Turla attack.
Cylance AI also stopped a key part of the attack chain in Test 2, by blocking attempted malicious injections. And Test 13 reveals that it prevented lateral movement attempts.
In all, BlackBerry successfully identified key phases of the emulated attack in their preliminary stages. Our timely detections complemented with contextual telemetry will help security teams identify and understand the situation they are facing as well as identifying how to proceed.
MITRE Engenuity Evaluations: Providing Protection from Within
In preparation for each year’s evaluation, there is a coordinated effort led by the MITRE Readiness team, consisting of members of departments across the company.
We utilize a methodology that is focused on positive security outcomes and designed to help customers protect their organizations. This methodology is supported by monthly purple teaming exercises where we test our product capabilities in a wide variety of different scenarios, using these exercises as opportunities to prepare for the MITRE evaluation.
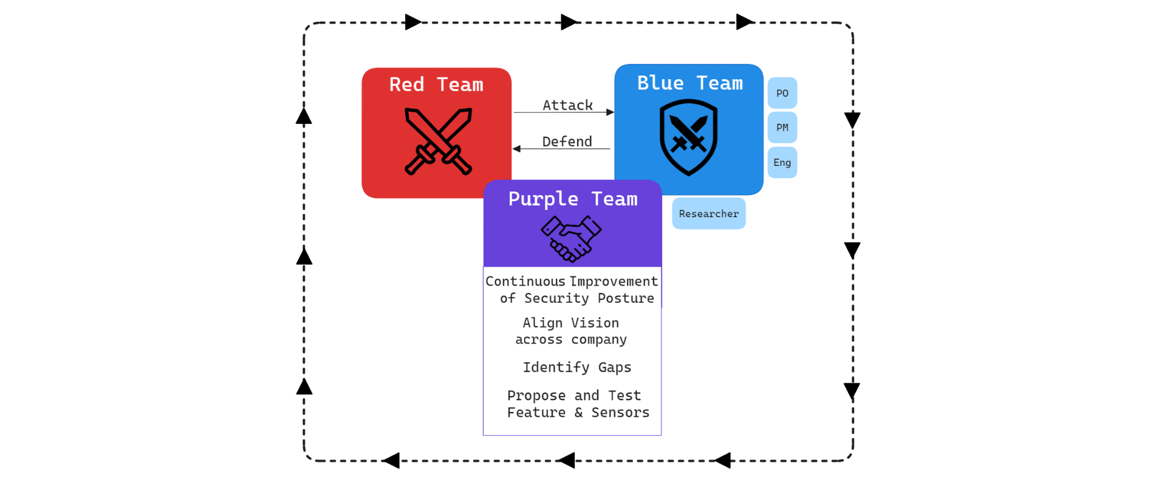
This is a classical “Think red, act blue” style in which BlackBerry creates four teams:
- Blue Team: Including product owners, project managers, engineers, and researchers. This helps stakeholders understand the individual strengths of each product, since they are using them as real customers under attack would. This process also helps to align our vision of products and features.
- White Team: This is the team that creates the initial group research, proposes operational flows, drives improvement of content and features, and coordinates all efforts. During Purple Team exercises, one member is the moderator, and during the real evaluation, that member is the Blue Team lead.
- Red Team: An internal Red Team which develops the operational flow proposed by the White Team.
- Infrastructure Team: Experts from each product team who help install and configure every feature to maximize capabilities.
Figure 6 — Team chart showing the functions of our Red, Blue, and Purple teams
Conclusions
It might be tempting to think that data is safe if your organization has expensive security products and technologies deployed. But if those technologies are immature or fail to provide visibility into the increasingly sophisticated attack chains utilized by every grade of threat actor — from common spam campaigns right up to targeted nation-state attacks — they may be set to fail.
This is why BlackBerry applies the strictest possible methodologies to our continuing product development. Our in-house teams work around the clock to improve our portfolio’s defenses and empower customers to protect their most vital assets, and to preemptively prevent damaging attacks.
A Note of Thanks
We want to publicly thank the MITRE Engenuity team — in particular the ATT&CK Evaluation team — for their continuous support, and for helping all vendors elevate their products and services to the next level, for the common benefit of the security industry.
Related Reading
Disclaimer: The views and opinions expressed in this blog are those of BlackBerry, and do not necessarily reflect the views or positions of any entities they represent.
Join BlackBerry for a day of inspiring keynotes, presentations, and discussions at the BlackBerry Summit, Tuesday, Oct. 17, 2023, in New York.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.