Inside the FBI and DOJ Takedown of Qakbot, the “Swiss Army Knife” of Malware
Following the takedown of Qakbot by international authorities, we dig deeper into this ubiquitous malware, and provide tips on how to stay safe in the aftermath.
When the U.S. Department of Justice (DoJ) and the FBI launched their joint takedown of Qakbot, one of the longest-running malware families and botnets, it sent ripples though worldwide law enforcement and cybercrime communities. The big question is: Will it stick?
Code-named Operation Duck Hunt, the coordinated international operation allowed authorities to seize control of Qakbot’s online infrastructure. The task force then obtained court orders to remotely remove the malware from infected devices, which at the time numbered some 700,000 machines globally, including 200,000 computers in the U.S.
The multinational operation invoved actions in the U.S., France, Germany, the Netherlands, the UK, Romania, and Lativa, to disrupt the botnet. The DoJ also announced the seizure of more than $8.6 million in illicit cryptocurrency profit.
“This is the most significant technological and financial operation ever led by the Department of Justice against a botnet,” said Martin Estrada, the U.S. attorney for the Southern District of California, at a press conference in Los Angeles.
Qakbot has been implicated in 40 ransomware attacks over the last 18 months, which have collectively cost victims more than $58 million in losses. The BlackBerry Research and Intelligence team identified Qakbot as one of the Trojans most frequently used against healthcare organizations in Q4 2022, but other sectors also suffered from Qakbot attacks. In fact, “Nearly ever sector of the economy has been victimized by Qakbot,” said Estrada.
Is Qakbot Down for Good?
While Operation Duck Hunt set new milestones in the law enforcement targeting of widespread cyberthreats, cybersecurity experts caution that any setback dealt to cybercrime actors would most likely be temporary. No arrests were made in conjunction with the takedown, and authorities did not disclose where the malware operators are thought to be located — although Russia has been implicated. The investigation is currently described as “ongoing.”
In this blog, let’s take a closer look at Qakbot, including new information on an unusual global campaign observed in the week prior to the high-profile takedown.
Meet Qakbot: a Modern Malware Shapeshifter
Following its first appearance in 2007, Qakbot became one of the most prevalent long-term cyber threats in modern history, dominating the threat landscape over the last decade and a half.
Also known as Qbot, Quakbot, and Pinkslipbot, the malware is modular in nature, enabling cyber crinimals to configure it to their specific needs. It has been updated, polished, and reshaped countless times over the years, with new capabilities regularly added. It’s simultaneously classified as a banking Trojan, a worm, and a remote access Trojan (RAT).
Described by researchers as the “Swiss Army knife” of malware, Qakbot was identified as one of the most prevalent malware threats during the first half of 2023.
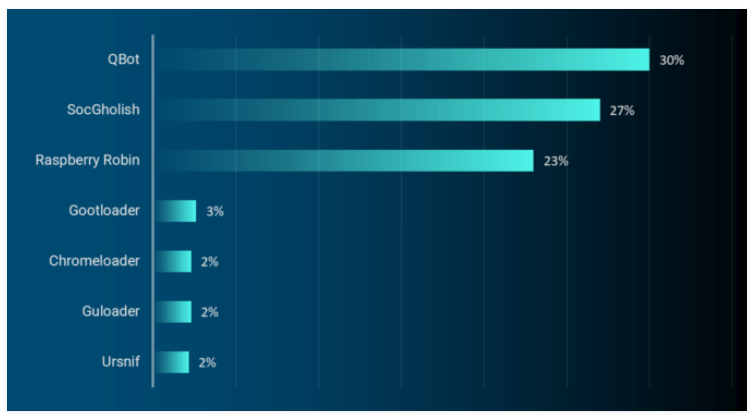
Figure 1: Qakbot was officially the top malware loader seen ‘in the wild’ in the first half of 2023, shown by percentage of all loaders observed (Source: ReliaQuest.com)
The financially motivated threat group Gold Lagoon is believed to have originally created and maintained Qakbot over the years, although it is not associated exclusively with any one threat actor or group. This means that a Qakbot infection is not conclusive proof that Gold Lagoon was behind that particular attack.
Qakbot was commonly used by multiple cybercriminal groups to prep freshly compromised networks for ransomware infections. Researchers believe that it had become a key infiltration tool for many prolific ransomware groups in recent years, including Conti, ProLock, Egregor, REvil (aka Sodinokibi), DoppelPaymer, and MegaCortex. It may have even been used to deploy the infamous ransomware Clop.
Its most notable operator was Black Basta, a prolific Russian-language cybercriminal group believed to have spun off from the Conti ransomware group in 2022.
The Qakbot network was “literally feeding the global cybercrime supply chain,” said Donald Alway, assistant director in charge of the FBI’s Los Angeles office, who called it “one of the most devastating cybercriminal tools in history.”
Technical Analysis
Infection Vector
Qakbot uses a variety of files, including LNK, HTA, Batch, JavaScript or WSF files that, when executed, help the malware establish persistance on an infected device. Infected emails may also contain a URL that leads users to a ZIP file containing a malicious Visual Basic script (VBS). Once compromised, the victim’s machine may become part of Qakbot’s global botnet operation, infecting additional victims.
In its quest to trick users, Qakbot disguises its phishing lures to look like something familiar and time-sensitive to the intended victim, such as invoices or work orders. Its lures assume many forms, and it’s been known to infect via Microsoft Excel XLSX files, Microsoft OneNote files, DLL files, executables, JavaScript files, and many other formats, including DocuSign-encrypted spreadsheets. This shape-shifting malleability makes it difficult for enterprises to create simple blacklists, or to apply specific access controls or policies to prevent compromise.
The malware essentially functions as a loader, meaning it can hook into an infected network and drop new malware payloads – most commonly, the remote-access tools Atera or NetSupport, along with Cobalt Strike.
Once dug in, it can exfiltrate sensitive data, move laterally throughout the network, deploy ransomware, or facilitate remote code execution. It implements multiple encryption schemes, concealing its identity from both potential victims and security software. It’s also able to identify a virtual machine (VM) environment and so evade purposeful detonation during research to further elude defenders.
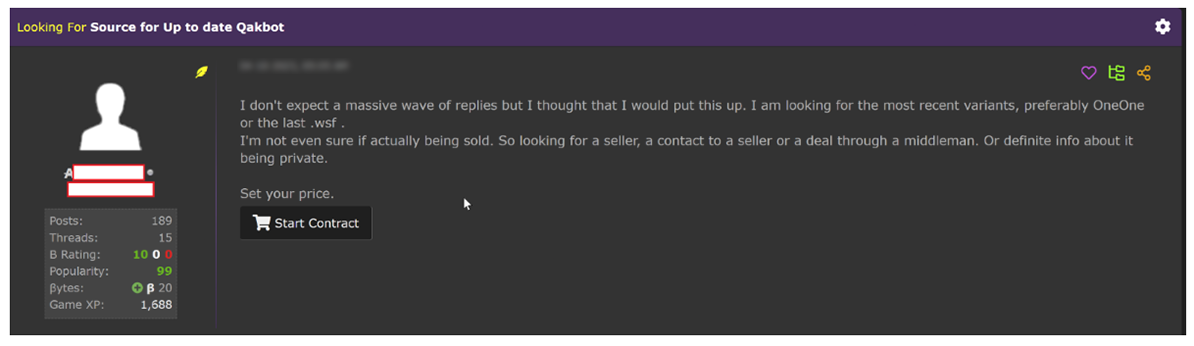
All of this makes Qakbot one of the most highly sought after pieces of malware within cybercrime communities, as evidenced in this typical post found on a popular hacking forum:
Figure 2: Post on a popular hacking forum seeking to purchase the most recent variants of Qakbot (post published prior to Qakbot's takedown)
Qakbot Tactics, Techniques, and Procedures (TTPs)
Delivery and Initial Infection
According to a paper by the Health Sector Cybersecurity Coordination Center (HC3), Qakbot propagates via multiple vectors, but malicious spam and hijacking its victims’ old email threads via Outlook are the most common. The initial infection often occurs when a user clicks on a malicious link or opens a weaponized document attached to a phishing email.
Qakbot’s other components and post-infection functions include:
Payload Dropper: Once the user's system is compromised, Qakbot's payload dropper is executed. The payload dropper is responsible for downloading and installing the main Qakbot banking Trojan (or the payload of the operator’s choice) onto the victim’s machine.
Persistence: Qakbot uses an assortment of slippery techniques to achieve persistence on the now-infected system, ensuring that it can survive system reboots and remain active for an extended period. This may involve creating registry entries, scheduled tasks, or using other methods to launch itself automatically at startup.
Command-and-Control Communication: Qakbot next establishes communication with its command-and-control (C2) servers, which are operated by the attackers. Through these channels, Qakbot malware receives instructions, updates, and sends stolen data back to the attackers. The C2 servers play a crucial role in managing the botnet and coordinating its malicious activities.
Information Stealing and Banking Fraud: Qakbot's primary goal is to steal sensitive information, especially banking credentials. It does this by intercepting web traffic, capturing keystrokes, and taking screenshots. Qakbot is well-known for using web injects, which allow it to modify web pages on the victim's browser to prompt them for additional login details or other sensitive information.
Propagation: Qakbot can also attempt to spread across the network by exploiting known vulnerabilities or using stolen credentials to move laterally to other machines. This capability makes it even more dangerous in corporate environments.
Spreading Through Further Spam Campaigns: Once Qakbot infects a system, it may use the compromised machine to send out phishing emails to other potential victims, further propagating the malware.
Digging Deeper
Examining Qakbot’s Modular Components
Defeating modern enterprise security requires enterprising techniques, and prior to the takedown operation, Qakbot malware seemed to be the cybercriminal’s weapon of choice when seeking to breach enterprise environments.
Highlighted in the Q1 2023 BlackBerry Global Threat Intelligence Report as one of the cyberweapons most commonly used by criminals, Qakbot didn’t need to be all that novel in its methods, because even modern enterprise security solutions generally don’t protect the entire attack surface; even known vulnerabilities can still persist on internet-connected servers, allowing Qakbot to persist much longer than should be possible.
In the past, Qakbot campaigns were mainly distributed through “pray-and-spray” spam campaigns, but it was Qakbot’s modular nature that really helped it bring in the dinero — or cryptocurrency, as the case may be — via the following optional modules:
Email Collection Module: This popular add-on extracts all emails from the local Outlook client; the collected email addresses are then funneled into new phishing campaigns. A secondary email function enables extra infections by replying to an infected host’s existing email threads with a malicious attachment or link, leading the new victim to unintentionally download Qakbot malware.
Universal Plug-and-Play (UPuP) module: This module is able to transform infected hosts that didn’t have direct Internet connectivity into intermediate command-and-control (C2) servers for use by the botnet.
Cookie Grabber Module: This module does exactly what it says on the box; it steals cookies from popular browsers.
Web-Inject Module: Qakbot provides the malware injector module with a specific list of “poisoned” and/or malicious websites (many of which were distributed via Qakbot’s spam campaigns) and JavaScript code that will be injected should the intended victim visit any of these websites. This module was typically used when targeting financial institutions.
Qakbot Global Spam Campaigns: a Recent Example
My team and I track dozens of known threat actors at any given time, with Qakbot among them. We observed an external global Qakbot campaign in the month prior to Operation Duck Hunt, where the malware operators combined a highly automated phishing and spam campaign with server-side watering hole attacks — a type of attack that exploits zero-day vulnerabilities to infect popular webpages with malware.
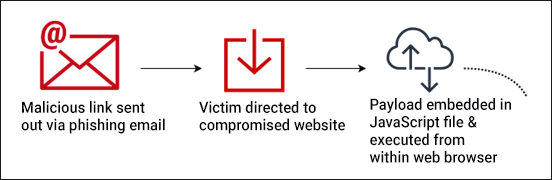
Figure 3: Typical Qakbot attack chain “startup” flow, showing web-injection module
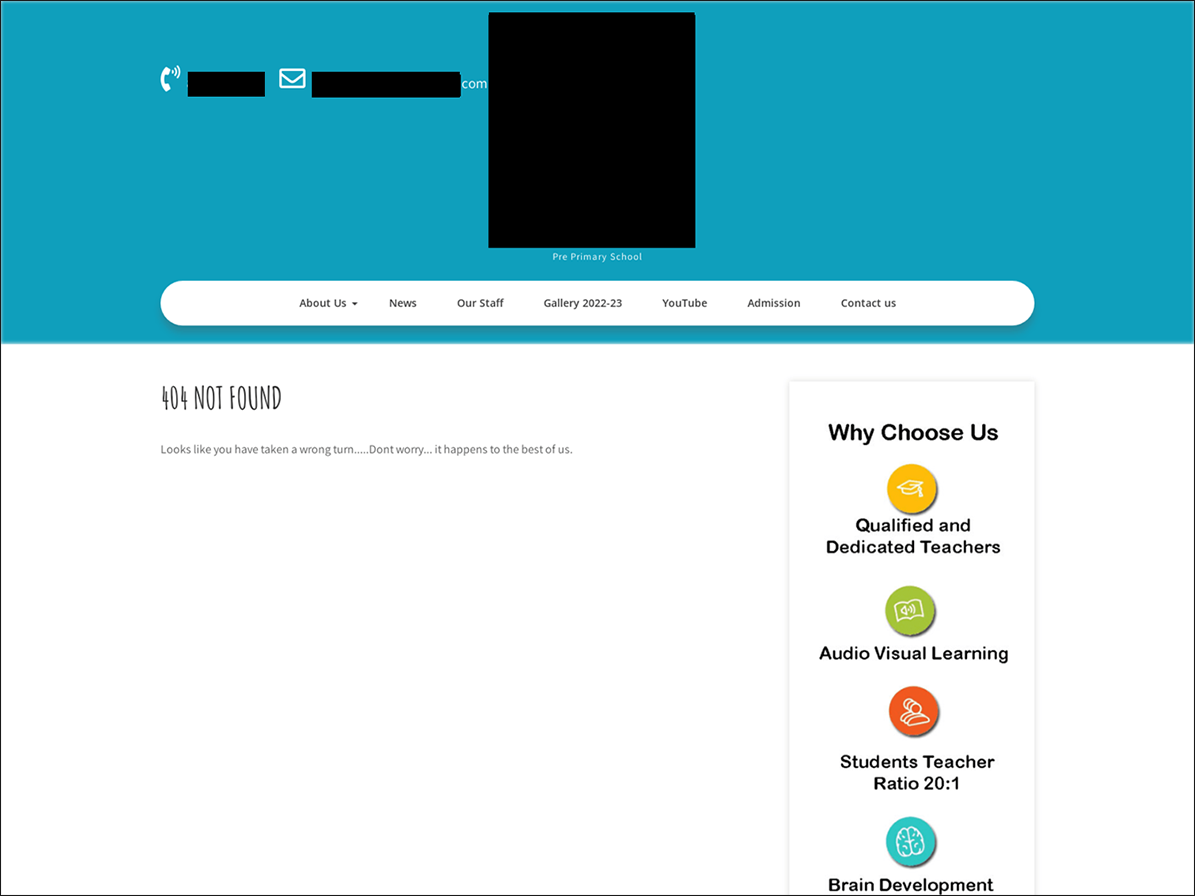
The poisoned websites we discovered (now taken offline) did not display any unusual content, or anything that appeared to be a scam, when visited by the user/potential victim. In most cases, a 404 error was displayed, as in the example shown below.
Figure 4: Seemingly innocent website “poisoned” by Qakbot operators
From the website visitors’ perspective, nothing seemed to be happening. However, in the background, a JavaScript (JS) code hosted on the threat actor’s server was executed as soon as the visitor arrived on the site, triggering the download of a malicious payload.
The only concerning visual indicator, should the user examine the page in greater depth, was the suffix of page URL (shown in bold below):
URL
|
Filename
|
Sha256
|
hxxps://[REDACTED]criticos[.]com/la/?1
|
lyntp.js
|
75716f1e6cd2c675a4350165989062f3cb98b8899dd27a01cba6c21244d44eff
|
hxxps://[REDACTED]consultants[.]co.za/tt/?1
|
nqr.js
|
e42f50128022327960f438484e5894b1fdf661b96e265336d98cbce9dfc34190
|
hxxps://milestone[REDACTED].com/smie/?1
|
wefex.js
|
2e58d291e2b56440d48b2a542599910cdba10e9f2dc829e298ad5922a2be56a4
|
Table 1: IoCs from the Qakbot campaign analyzed in August, a week prior to the FBI takedown
A quick search on the popular malware scanning website urlscan.io returns more than 5,000 examples of URLs that are in line with this pattern. And the pattern is always the same: A subdirectory exists on a domain that seems to typically have a short lifespan. The subdirectory is named with two to four random letters and queried with the "1" parameter. It returns a consistently sized .js file named with two to four random letters. The files we downloaded were detected by many online scanning engines as malicious.
The "/?1" part of the suffix in a URL could potentially be used to trigger the execution of JavaScript code hosted on the server. The character following an exclamation point in a URL typically represents query parameters, and can be used to pass data to the server-side script. Depending on the server configuration, the server will interpret these parameters and respond accordingly.
The URL that carries the payload was being named in a random, but consistent manner. Filenames are likely automatically generated, as are the variable names within the script. Our conclusion is that it may have been one of the tradecraft indicators for this global QakBot distribution campaign.
Although the real-life campaign detailed above has currently been halted by Qakbot’s takedown, the team and I will continue tracking it, and will provide an update if it resurfaces in the future.
Qakbot: Tools of the Trade
One of the most concerning features of Qakbot is that it can self-propagate using an SMB brute-force module that contains a list of the most commonly-used passwords.
As you can tell from this list of the top 100 most commonly used passwords in 2023, too many people are still complacent when it comes to setting passwords, with an alarming number using (or re-using) just one or two passwords for all their accounts. This means that if one of your employees’ personal accounts gets hacked, it’s possible that their corporate account may soon fall into unfriendly hands, as well.
Another method of self-propagation used by Qakbot leveraged two very particular tools:
PowerShell: This is a command-line tool used for general system and file manipulation. It can be used to decode, embed and inject a Mimikatz binary into memory.
Mimikatz: This open-source tool can be used for many purposes, including lateral movement, certificate and credential theft, reconnaissance, and a fun game (although not for the victim) called “Pass the hash.”
Once a victim is infected by Qakbot, their computer is compromised and becomes an immediate threat to others in their local network, because of the malware’s capability for lateral movement. In some cases, the malware may exploit an organization’s software vulnerabilities or take advantage of newly discovered zero days to gain access to the full network.
This was demonstrated just under a year ago, when threat actors leveraged a Windows zero-day vulnerability to deploy Qakbot malware. After a Microsoft patch made the malware harder to deploy, threat actors switched to exploiting this zero-day vulnerability by distributing JavaScript (and other) files with altered signatures that were able to bypass the telltale Mark-of-the-Web (MOTW) security warning that would have usually alerted users to the attack.
You can read more about this attack — and learn how BlackBerry provides protection against Qakbot — by reading their blog on the subject, which can be found here.
In Part 2 of this blog, I’ll be covering mitigations to protect against some of the techniques used by Qakbot, teach you a quick and easy way to find out if you've ever been compromised by Qakbot in the past, and answer that all-important question: Now that Qakbot’s botnet has been taken offline, am I safe?
Related Reading
About Pete Herzog
Guest Research Contributor at BlackBerry
Pete Herzog knows how to solve very complex security problems. He's the co-founder of the non-profit research organization, the Institute for Security and Open Methodologies (ISECOM). He co-created the OSSTMM, the international standard in security testing and analysis, and Hacker High School, a free cybersecurity curriculum for teens. He's an active security researcher, investigator, and threat analyst, specializing in artificial intelligence (AI), threat analysis, security awareness, and electronic investigation.