Threat Analysis Insight: RisePro Information Stealer
Summary
RisePro is a multifunctional information-stealer often sold on underground forums as part of a Malware-as-a-Service (MaaS) offering. Although this malware family was initially observed in late 2022, a sharp increase of activity surrounding this malware was detected by BlackBerry during the latter end of 2023 and into early 2024, being highlighted in the March edition of our Global Threat Intelligence Report in the "Top Critical Infrastructure Threats" section.
RisePro has no specific infection vector and can be dropped onto a victim’s device in a plethora of ways, often relying on malicious links and lures to gain an initial foothold. In the past it has been deployed by PrivateLoader, a pay-per-install (PPI) malware often utilized by other threat actors as a malware distribution service, allowing threats like RisePro to be deployed onto unsuspecting victim devices. Researchers have uncovered indications that RisePro shares significant code overlaps with PrivateLoader, suggesting a connection between the two.
Once it has gained a foothold on a system, RisePro will check to see if it has an Internet connection and then reach out to communicate with its command-and-control (C2), which can send the malware a wide variety of commands. Like many other infostealer malware families, RisePro can fingerprint a victim’s system, steal data and exfiltrate it to the threat actor’s infrastructure.
Although no specific threat actor has been directly associated with RisePro to date, given the activities of the malware and the specific design features of RisePro’s control panel, we assess with a high degree of confidence that those associated with its development are Russian-speaking.
In this blog, we’ll delve deeper into RisePro and examine its infection chain and inner workings.
Affected Operating Systems
Technical Analysis
Infection Vector
RisePro utilises a subscription-based model, so the initial infection vector varies widely and is entirely dependent on the needs of its affiliates/operator(s). Operators of RisePro pay a licensing fee to the threat actor who developed the malware, giving the cybercriminal purchaser total freedom to generate new binaries, configure their own malware-builders, and customize various options depending on their own desires and motivations.
RisePro often uses deceit as an aid in its deployment. It regularly appears as a Trojanised version of commonly used legitimate software, positioning itself as something useful for unsuspecting victims to download. For example, in March 2024, a variant of RisePro leveraged GitHub to host malicious binaries masquerading as legitimate software downloads.
Throughout our investigations, BlackBerry researchers observed RisePro hiding behind numerous disguises, including everything from “cracked” versions of paid software to seemingly legitimate Microsoft files in early 2024.
According to a report published in March, RedLine, Vidar, and Raccoon are the most widely-utilized infostealers, with RedLine alone accounting for over 170 million compromised passwords in the six months between October 2023 and March 2024. Compromised accounts can be leveraged for further nefarious activities and even used as an attack vector to deliver ransomware, making any of these infostealers a potent threat.
Analysis
RisePro uses a malware builder to generate its payloads, giving a high degree of flexibility and customization to those who utilise this infostealer. For example, when a payload is being crafted, the operator can specify the type of executable, the build name and even the specific service IP it wishes the malware to use for communication. RisePro can also employ various other features such as:
- Anti-Debugger Checks
- Anti-Virtual machine (VM) Checks
- Disable Windows Defender
- Residency
Upon execution, RisePro will initially drop a copy of itself onto the victim device as a means of persistence. Typically, RisePro will drop copies of itself via:
- %AppData%\Local\Temp
- %ProgramData%\
If the malware operator has the setting for “residency” enabled, RisePro binaries will create scheduled task(s) to run both hourly and on logon. This is achieved via schtasks(.)exe to ensure the malware has a foothold on the unsuspecting victim's device. Examples are below:
- C:\Windows\SysWOW64\schtasks.exe
schtasks /create /f /RU "Admin" /tr "C:\ProgramData\[RisePro].exe" /tn "%RisePro% HR" /sc HOURLY /rl HIGHEST
- C:\Windows\SysWOW64\schtasks.exe
schtasks /create /f /RU "Admin" /tr "C:\ProgramData\[RisePro].exe" /tn "%RisePro% LG" /sc ONLOGON /rl HIGHEST
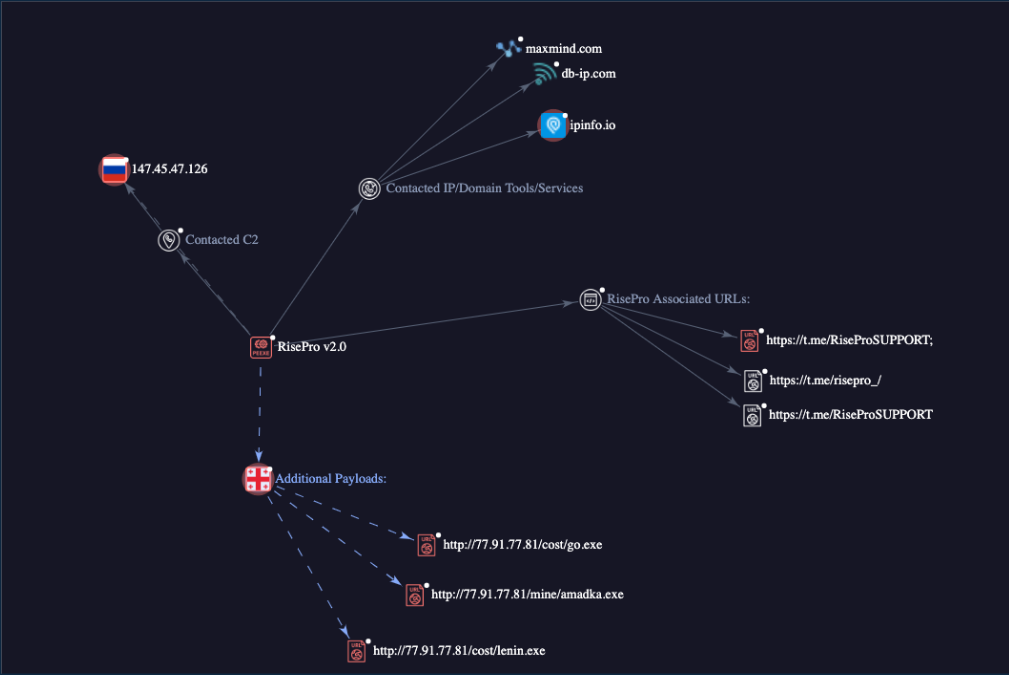
Once on a victim device, RisePro will attempt to contact its C2 infrastructure. Before doing so, the malware will complete a number of checks to see if it’s in an isolated or potentially virtualised environment. This is done through the malware reaching out to various IP information and location service provides such as:
- ipinfo(.)io
- db-ip(.)com
- maxmind(.)com
This information is utilised two-fold, both to determine if the malware is running in an analysis or isolated environment, and to gather the geographic and location information of the victim. Furthermore, RisePro can operate on different conditions depending on whether a victim is located in a specific region/nation.
Figure 1: Example of typical RisePro network communications.
Communication
It was previously revealed that RisePro formerly communicated over HTTP, using a basic byte-substitution cipher and XOR operations to obfuscate its true communications. However, it was reported in late 2023 that newer versions of the malware had transitioned over to using a custom protocol over TCP for network communication.
Though this indicates a complete overhaul in communications, the malware largely follows the same obfuscation for its communications/traffic. Throughout subsequent investigations into RisePro, frequent updates have been observed, with RisePro version 1.6 being commonly seen in the wild circa March 2024. However, communications between version 1.0 and 1.6 have remained largely unchanged, with both versions following the same structure as indicators, as observed here.
In June 2024, RisePro saw another update, moving to RisePro version 2.0 which brought minor iterative changes to its communications once again. RisePro still operates over TCP for network communications keeping its same byte-substitution cipher as per version 1.6. However, the malware now communicates through different TCP Port(s) and corresponding XOR logic.
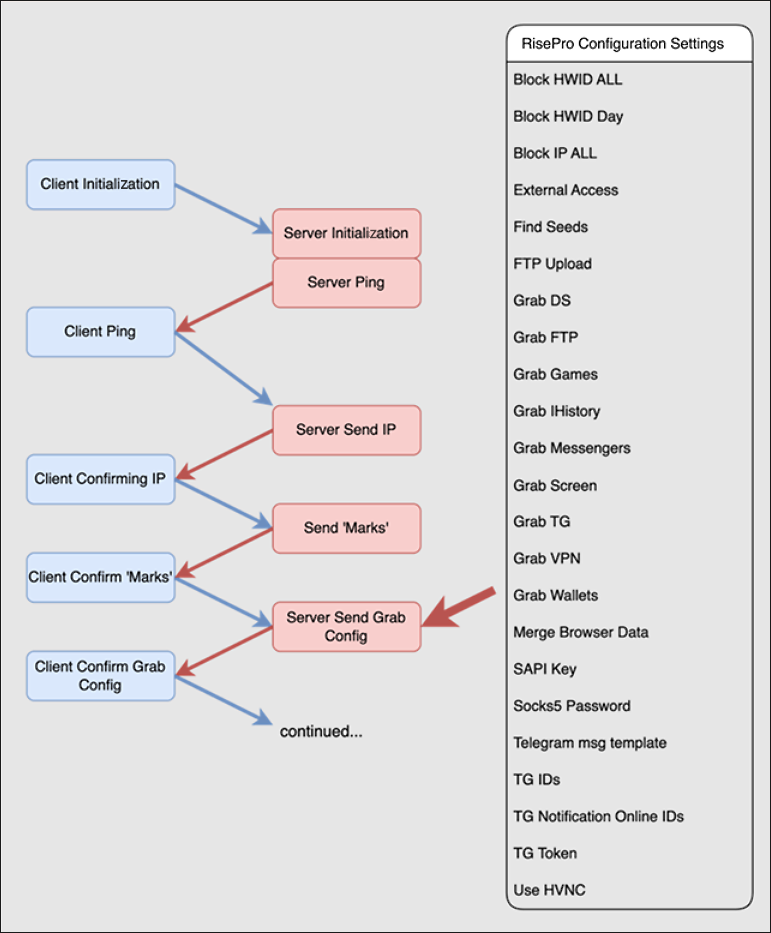
The malware will initialise communication with the C2 to confirm its connection. Additionally, via the builder, a RisePro operator can specify points of notoriety for their own malicious logging purposes called “marks”. These marks could be specific crypto-wallets, payment types, or credentials sought by the operator.
The C2 will send its “Grabber Config” command containing a set of instructions specifying what items of interest the operator wishes to exfiltrate from the target device. Most options in the configuration accept a Boolean value to enable/disable its ability. A Boolean value represents a truth value; that is, true or false, with a value of unknown represented by a null value. Therefore, operations of RisePro can be different sample to sample, or even operate differently in a specific region/geolocation, based on the array of customisation within its configuration.
Figure 2: RisePro C2 communication and initialisation.
Infostealing
RisePro’s primary goal is to conduct information stealing and exfiltrate victim information back to its malicious operator(s). Once the C2 sends its “Sever Send Grab Config” command, the malware will operate accordingly depending on the following settings.
In addition to sending the exfiltrated information back to its C2, the malware can be customised to send stolen data through other means, namely a Telegram bot.
Grab Config ID’s
|
Details
|
block_hwid_all
|
Blocks loading of hardware fingerprint if already met
|
block_hwid_day
|
Blocks loading of hardware fingerprinting if satisfied the last day
|
block_ip_all
|
Blocks additional downloading of logs whose IP has already satisfied
|
external_access
|
Enable external access to panel
|
find_seeds
|
-
|
ftp_upload
|
Sends logs via FTP
|
grab_ds
|
Exfiltrate Discord credentials
|
grab_ftp
|
FTP credentials
|
grab_games
|
Video game credentials
|
grab_ihistory
|
Internet history credentials
|
grab_messengers
|
Chat/Messenger service credentials
|
grab_screen
|
Take screenshot and exfiltrate
|
grab_tg
|
Telegram credentials
|
grab_vpn
|
VPN credentials
|
grab_wallets
|
Crypto-wallet data
|
merge_browser_data
|
Merge browser data together
|
sapi_key
|
SOCKS5 APT Key (Static)
|
socks5_password
|
SOCKS5 Password (Static)
|
static_marks
|
“Marks” customised by operator
|
tg_token
|
Operator’s Telegram token
|
use_hvnc
|
Initiate utilisation of Hidden Virtual Network Computing (HVNC) to startup
|
Figure 3: RisePro v1.6 configuration options.
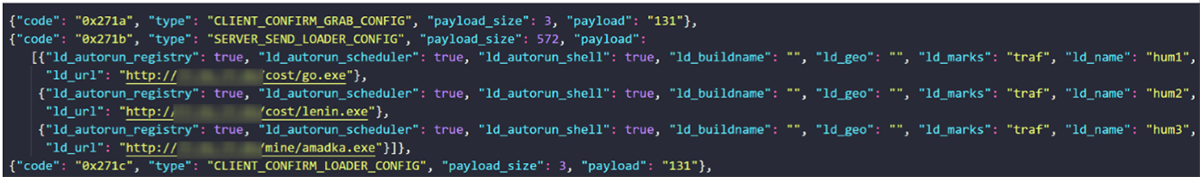
Once the malware receives its “Grab Config,” it confirms its commands before being issued another “Send Loader Config.” This configuration command is another feature of the malware, enabling it to act as a malware downloader. If enabled, RisePro will download additional payloads and even other malware at the request of the operator.
Figure 4: RisePro V2.0 Server Send Loader Config example.
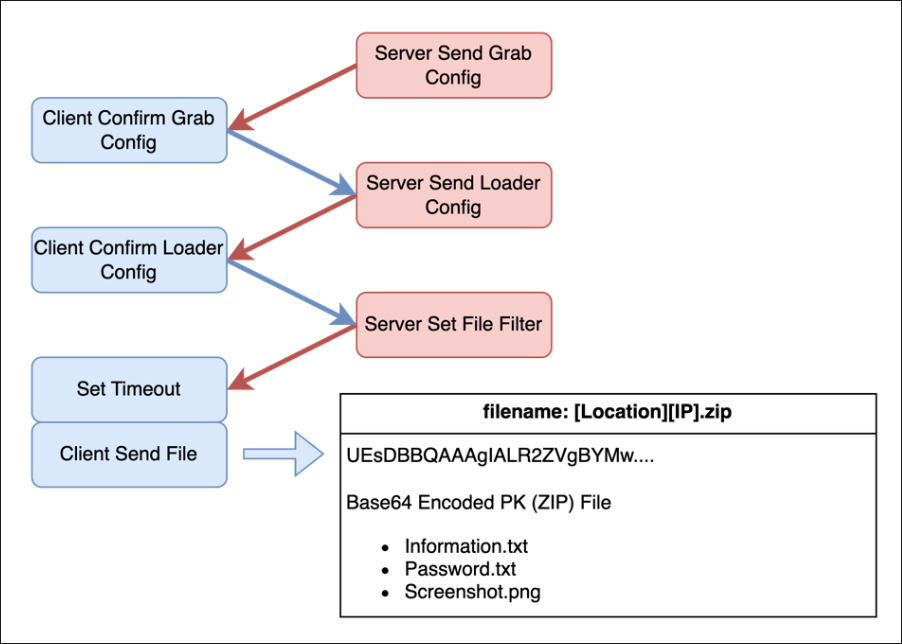
After both commands are received, the server sends a “Set File Filter” command to specify its exfiltration of victim data.
Throughout our investigations, we observed RisePro sending its communications via its custom TCP communications, with the exfiltrated data being a Base64 encoded ZIP file. The contents of this file vary depending on the settings of its configuration and valid information present on the victim device.
Figure 5: Exfiltration method of RisePro.
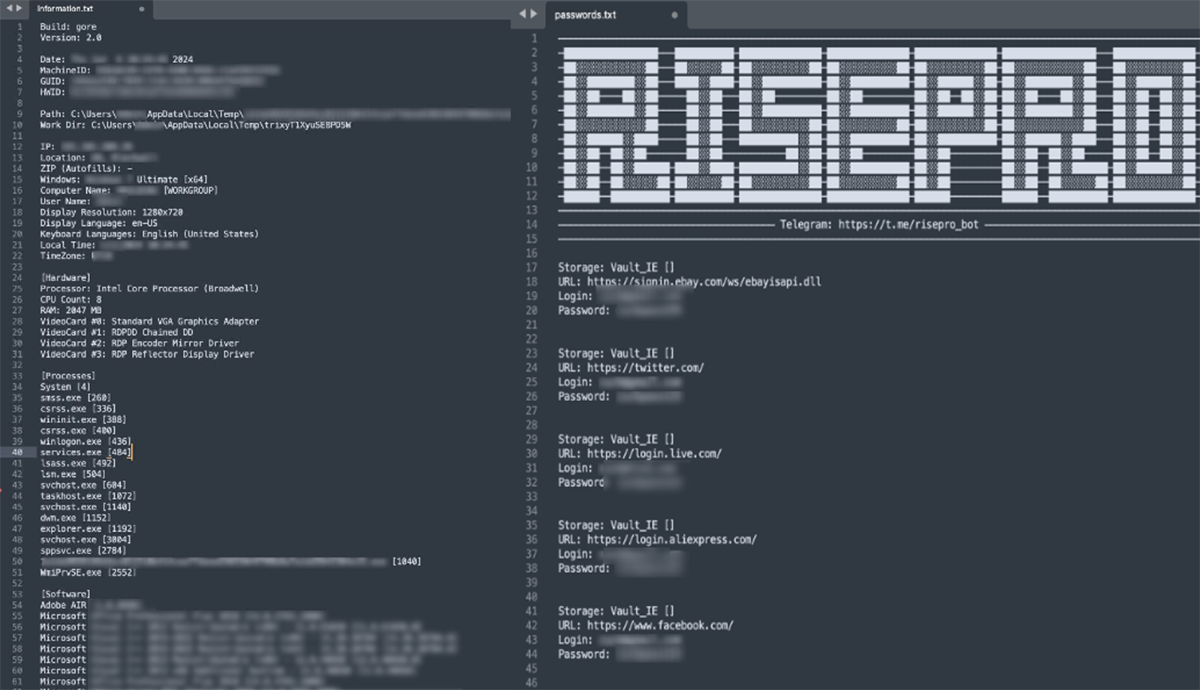
Two consistent files often observed during our investigations are:
- information.txt
- password.txt
Details gathered within “Information.txt” largely surrounds fingerprinting of the victim device. This includes:
Name:
|
Details:
|
Build
|
RisePro Build ‘ID’
|
Version
|
RisePro version
|
ID Information
|
Device identification information
|
Path
|
Path of malware
|
Working Dir
|
Path of secondary binary of RisePro
|
Device Information
|
Device Information:
- IP
- Location
- Windows version
- Computer Name
- Username
- Display Resolution
- Display Language
- Keyboard Language
- Local Time (of victim)
- Time Zone (of victim)
|
Hardware
|
Hardware information of victim device:
- Processor
- CPU Count
- RAM
- Video Card
|
Processes
|
Running processes (at time of exfiltration)
|
Software
|
Software on victim device
|
In addition to “information.txt,” another text-based file “passwords.txt” is often observed being generated and exfiltrated. Prior to its exfiltration, all passwords and account details obtained by the information stealer are populated into this file, per the available data on the victim’s device and previously selected configurations.
Figure 6: Redacted "information.txt" and "passwords.txt" from RisePro v2.0.
Distribution/Attribution
RisePro is often promoted on underground forums via the dark web. RisePro attracts new operators using a subscription-based MaaS model that enables operators/affiliates to create their own binaries and manage their own infrastructure.
Given the activities and design of both the malware and RisePro’s control panel, we assess with a high degree of confidence that those associated with its development are Russian-speaking. However, no specific threat actor has been directly associated with RisePro at time of writing.
Likewise, due to the nature of this being Malware-as-a-Service, the weaponization of the malware can be utilized by all who are willing to pay the subscription, resulting in countless operators worldwide.
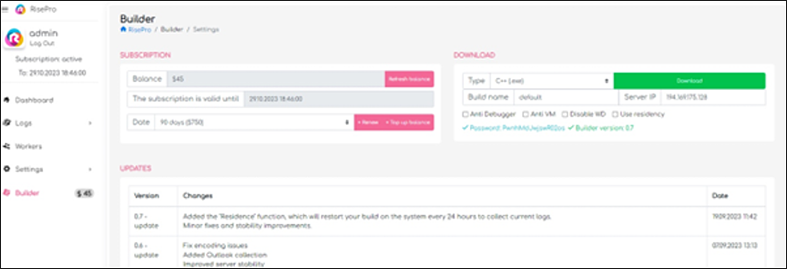
Figure 7: Example of an older RisePro (v0.7) Builder panel.
Targets
RisePro does not have any specific victims or targets, given that it is a subscription-based malware and thus bound to do the bidding of its affiliates/operators. Those who use its paid services are free to leverage other malicious downloaders or host their crafted RisePro binaries on their own lure site.
In previous RisePro malware campaigns, other known commodity malware, such as PrivateLoader, has been seen dropping RisePro. RisePro has also been observed hosted as Trojanised files through various means. In a recent campaign, the latest versions of the malware were seen hosted on GitHub. However, RisePro is not limited in its delivery by any specific ways or means.
Conclusion
The malleable and robust features of RisePro underscore the continually evolving state of the cyber threat landscape, emphasizing the necessity for robust countermeasures. Commodity information stealer threats dominated the March edition of our BlackBerry Global Threat Intelligence Report and have been observed by our analysts in both commercial enterprise and critical infrastructure organizations.
Through the use of sophisticated techniques, which include evasion tactics, customization options and data exfiltration capabilities, RisePro poses a substantial risk to both individuals and organizations alike. As a result, it is imperative that organizations endeavor to employ proactive defense tactics wherever possible, including employee awareness training, continuous monitoring, the deployment of a modern and comprehensive endpoint security suite, and an up-to-date Threat Intelligence program.
By remaining alert and adaptive, it is possible for organizations to bolster their defenses against evolving threats like RisePro, to help shield their digital infrastructure and preserve the integrity of their data and systems.
Countermeasures
The good news is that BlackBerry customers are protected against the RisePro IoCs listed in this blog by endpoint protection solutions such as CylanceENDPOINT™, powered by Cylance® AI from BlackBerry.
CylanceENDPOINT leverages advanced AI to detect threats before they cause damage, minimizing business disruptions and the costs incurred during a ransomware attack.
MITRE ATT&CK® Matrix
Tactic
|
Technique ID
|
Technique Name
|
Details
|
TA0003: Persistence
|
T1053
|
Scheduled Task/Job
|
Malware triggers a scheduled job on logon for persistence
|
T1547.001
|
Registry Run Keys/Startup
|
Creates autorun registry key in Start Menu\Programs\Startup
|
T1547.001
|
Registry Run Keys/Startup
|
Stores file in Windows Startup Directory
|
TA005: Defense Evasion
|
T1140
|
Deobfuscate/Decode Files or Information
|
Most variants of RisePro are obfuscated or packed
|
T1564.003
|
Hidden Window
|
Malware generates a hidden window
|
T1036
|
Masquerading
|
Creates files in both system and user directory
|
T1112
|
Modify Registry
|
Adds Registry Keys to victim device
|
T1027.002
|
Software Packing
|
Malware contains packed/crypted code
|
T1497.001
|
System Checks
|
Attempts to determine if running on a virtual machine (VM)
|
TA0006: Credential Access
|
T1555
|
Credentials from Password Stores
|
Malware attempts to obtain sensitive password information from victim
|
T1056
|
Input Capture
|
Malware has the ability to determine input
|
T1003
|
OS Credential Dumping
|
Attempts to read system vault for password information
|
TA0007: Discovery
|
T1083
|
File and Directory Discovery
|
Searches for sensitive data
|
T1046
|
Network Service Discovery
|
Sends Simple Service Discovery Protocol (SSDP) broadcast queries
|
T1057
|
Process Discovery
|
Enumerates running processes to populate “information.txt”
|
T1012
|
Query Registry
|
Enumerates Registry
|
T1018
|
Remote System Discovery
|
Reads host file
|
T1518.001
|
Security Software Discovery
|
- Checks if running via a debugger
- Checks for process monitoring tooling
|
T1082
|
System Information Discovery
|
- Enumerates process, queries network configuration and collects hardware information.
- Queries list of all running drives
- Collects volume information of device
|
T1016
|
System Network Configuration Discovery
|
- Enumerates processes
- Queries network configuration
- Collects hardware information for fingerprinting
|
T1124
|
System Time Discovery
|
Gathers system time information to populate “information.txt”
|
TA0009: Collection
|
T1119
|
Automated Collection
|
Searches for sensitive web browser data.
|
T1005
|
Data from Local System
|
- Searches for strings related to crypto-wallets
- Tries to harvest and steal browser information like history and passwords
|
T1114
|
Email Collection
|
Searches for email accounts and credentials
|
T1056
|
Input Capture
|
Creates a direct input object
|
TA0001: Command and Control
|
T1071
|
T1071: Application Layer Protocol
|
Has ability to download additional payloads from webservers via HTTP
|
T1573
|
T1573: Encrypted Channel
|
Uses crypted and XOR TCP traffic to send data
|
T1571
|
T1571: Non-Standard Port
|
By default, RisePro uses TCP Port 50500 for communications
|
TA0010: Exfiltration
|
T1041
|
Exfiltration Over C2 Channel
|
All information acquired by malware is sent back to its C2 infrastructure
|
T1567
|
Exfiltration Over Web Service
|
RisePro can exfiltrate its stolen data via other means like Telegram if enabled
|
Figure 6: Commonly observed RisePro MITRE Tactics/Techniques.
MITRE D3FEND™
Model
|
Name
|
ID
|
Definition
|
Detect – File Analysis
|
File Content Rules
|
D3-FCR
|
Employing pattern-matching rule language/signatures to analyse the content of file(s)
|
Detect – Identifier Analysis
|
URL Reputation Analysis
|
D3-URA
|
Analysing the reputation of a URL and blocking if negatively scored/classified
|
Detect – Platform Monitoring
|
Scheduled Job Analysis
|
D3-SJA
|
Analysis of unauthorised use of job scheduling
|
Detect – Process Analysis
|
File Creation Analysis
|
D3-FCA
|
Analysing the properties of a file create system call invocations
|
Isolate – Execution Isolation
|
Executable Allow Listings
|
D3-EAL
|
Use of digital signatures and fingerprinting to authenticate a file prior to opening/execution
|
Isolate – Network Isolation
|
Network Traffic Filtering
|
D3-NTF
|
Restricting network traffic originating from a location
|
Evict – File Eviction
|
File Removal
|
D3-FR
|
File removal technique deletes malicious artifices or programs from a computer system
|
Evict – Process Eviction
|
Process Termination
|
D3-PT
|
Terminating a running application process on a computer system
|
Figure 8: Recommended MITRE D3FEND Techniques related to RisePro.
Indicators of Compromise (IoCs)
SHA256
|
File Type
|
Details
|
2229327fa653ffd07f11773ee22eb00e580b6824ce122a1e788f19859aa9dca2
5e1a1b2e2c20bc50b54e02393fa6f26a2b8c2f4d87f2abdecaca73472b5c5dba
a36d5e790ca17fb6f70884942d868d29c6854054f2db79ed8f4e2d0d16ef1647
4f0e839393df72db99a05ade0848979ff375399b104e59a7cc3847d746c17e5c
56108c707fcaf87b2220c081db115171ff35811946b3ad2d76105715e8530fbe
b4ad80860c773c79c946c3a4df13e534153bd17ceebad6acedac3156dfe0144c
77e97faca59d8de34ddc7272791efac41da9ff5b7b175a99e09a255e2701d725
a78513831b47f4b35ee9063aa167bf5d05c61559b2ac7f8fb93fa966a36e34d2
30baf54d50379893b23b24203611da331d436dfc35f2d0a805bac4da0d310489
c48eb226b641b382fd4155f10c96aacc585c6e65814865cd762e88b8a5cffd14
6b82e6f228cbb8143b68e1739f3d083cf6ab0ba9c202ce1ec769bb12c9030619
5719a862d5a32ec56328f8e066a83b6b0577a6965074ca671d0cecce681d5f79
9d540839e75daf4f31eb36271fef6eb16a913446384d07e4d8dbb2602f18bf0f
15dfbd2df433c9725239d6602bdfc56d00db62f88a1769a534d98cad50536c27
c7a40fb4aa017a0d17b535c1857d51f95b7ed8684a1ea860294bf5d897667839
6113bc3f3f972393acff5022f5ba95fb96c3d9038386ada49ccf244fa5f885fa
ce930238a02a55d7b6f13fdf9b3306de61c5c25513ed396c7e9a8dbd4c45dbd9
19c98cba0d8037a36b00d2c11cc24d25e1f388ba5093a4b6e9017508371fb34b
d2cbb7a5ef2ecdf7c6f8c965df5886a18ea0e630009cdedb3692ed1b8c77b487
078b3f37483cfc697fbd67120311e6109843804f5cae9c46f04fa1b51ba7120a
d435d7cf9077533a7c23129a8d7462e7596505e3990664dd5888fce40652bb14
d7c3c01d62fb59e186b2256894fb089c01e1aeda5dbd86a3004f1857a13313ad
0d5bb8b8da18abd1f3934103c501abf9b9cd3a6e1656853359a568dca3229765
cb21be437c800875400a94b2442bbe02ccaf31ee49e1f440aac378fc2b0b756d
f87dd2b6a63e850b6c2128ec139c6334b572b1c80698fcc30de6f39ffc788f4f
|
PE/EXE
|
RisePro Binary (Selection)
|
IP/Domain
|
Details
|
5[.]42[.]92[.]73:8081
185[.]196[.]9[.]38:8081
147[.]45[.]47[.]116:8081
101[.]99[.]92[.]169:8081
147[.45[.]47[.]80:8081
37[.]120[.]237[.]196:8081
95[.]216[.]41[.]236:8081
185[.]221[.]198[.]67:8081
194[.]33[.]191[.]159:8081
94[.]156[.]8[.]188:8081
|
Recently active RisePro C2s
|
ipinfo(.)io
db-ip(.)com
maxmind(.)com
|
IP Geolocation Services utilized by RisePro
|
hxxp://185[.]215[.]113[.]46/mine/plaza[.]exe
hxxp://185[.]215[.]113[.]46/cost/ladas[.]exe
hxxp://77[.]91[.]77[.]81/cost/go[.]exe
hxxp://77[.]91[.]77[.]81/cost/lenin[.]exe
hxxp://77[.]91[.]77[.]81/mine/amadka[.]exe
|
Example of secondary downloads via “Send Loader Config”
|
Yara Rule
import "pe"
import "math"
import "hash"
rule Mal_Infostealer_RisePro_v1.6
{
meta:
description = "Detects RisePro v1.6 Infostealer"
author = "BlackBerry Threat Research"
date = "2024-03-20"
license = "This Yara rule is provided under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0) and open to any user or
organization, as long as you use it under this license and ensure originator credit in any derivative to The BlackBerry Research & Intelligence Team"
strings:
$s0 = {3231F531F52DF52DF5CBCBA57DFD7DCBCBCB363231312E312DF5F52DF5CB09AF08D4080908090909F5CBCBCB59FD7DCBCBCB
82F6D4080809090809090DCB82F6AFAFAFAFAF08D4090DCBCBCB59FD81CBCBCB86B3AFAFAFAF08AFD409F5CB09F6AF0EAF0EAF0AAF0931
CBCBCB7DFD7DCBCBCB09D1AF0AAF0EAF0AAF0832CF86D1B3AFAFAFAFAFAF0832CBCBCB59FD81CBCBCB86F6D1F6AFAFAFAFAFD431CC09F
FF60AF60AB30AAF}
$s1 = {565AEAEAEAEA565AEAEAEAB2BEAEAEA56445AEAEAEA56445AEAEAEB2BA}
$s2 = {4321FFD9F4FFFFE1733AFFCF6630FFB75A2BFF9D4E27FF8A4321FF7FD1FDFF507791DA000000007496A9B081D1FDFF95D9FEFFA
9E1FEFFD66931FFCCEFFEFFDAF4FFFFE4F8FFFFDAF4FFFFCCEEFFFFD66B34FFA9E0FEFF95}
$s3 = {5642FF6C533EFF6A503BFF684D39FF664B36FF654934FF634833FF64C6FDFFC4AEA1FFFBF1EBFFE5CFC4FFE4CEC1FFE3CBBFFFE3CABCFF
E3C7B9FFE2C6B6FFE2}
$s4 = {537465616C6572436C69656E742E657865}
condition:
// Must be MZ file
uint16(0) == 0x5a4d and
// Resource in Russian
pe.resources[2].language == (0x0419) and
// Must contain exact number of resources
pe.number_of_resources == 9 and
// Section Permissions
pe.sections[pe.section_index(".taggant")].characteristics&pe.SECTION_MEM_WRITE and
// Must have all strings
all of ($s*)
}
|
Related Reading:
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.