Threat Thursday: Avaddon Ransomware Uses DDoS Attacks as Triple Threat
UPDATE 6/17/2021: After recent attention due to several high-profile ransomware incidents, the ransomware group behind Avaddon seems to be shuttering their current operations. Law enforcement efforts to track down malware operators have visibly increased after the recent attack on Colonial Pipeline, operators of a major fuel pipeline system based in the Eastern U.S., which prompted DarkSide to shut down their own operations.
Avaddon has released the decryptors to the latest version their threat. While this may mean the end of this version of their creation, there are still many other ransomware groups still in full operation. Previous advice regarding prevention and mitigation of ransomware still applies, and can help protect you against threats by these and other groups.
Summary
The Avaddon ransomware variant first appeared in early 2020 and made international headlines due to recent attacks against Australian organizations and Asia-based cyber insurance company AXA. Both the Federal Bureau of Investigations (FBI) and the Australian Cyber Security Center (ACSC) have released warnings regarding an ongoing attack by this malware family.
Avaddon is distributed as a Ransomware as a Service (RaaS) for use in targeted attacks. The infection vector of Avaddon is phishing emails.
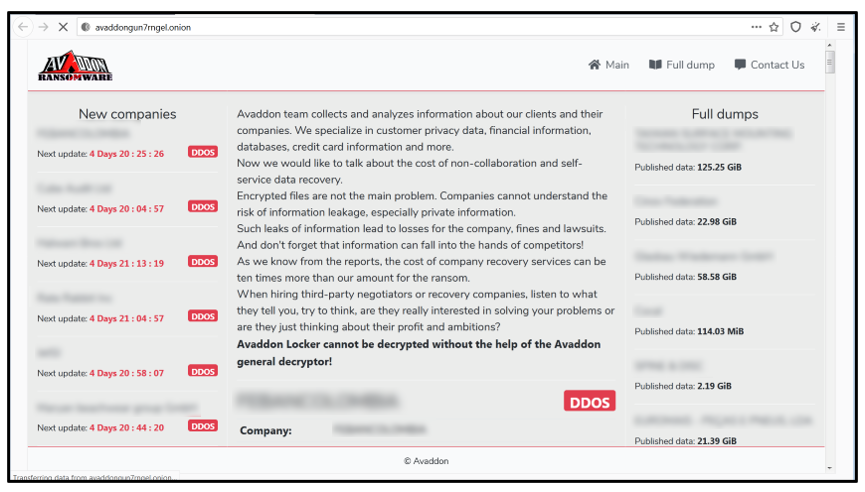
Like DarkSide and REvil ransomware, Avaddon also uses a double extortion scheme where data is both encrypted locally and exfiltrated before the ransom demand is made. If the victim refuses to pay, their data is published to a site located on the dark web at avaddongun7rngel[dot]onion.
Avaddon, however, goes one step further. To further ‘encourage’ victims to pay the ransom, attackers also subject them to a third threat - a Distributed Denial of Service (DDoS) attack – until the ransom is paid.
Visiting the dark web site, the current victims can be seen under “new companies” that Avaddon has infected. For example, they claim to have 3 TB of data from AXA, which is notably large compared to other victims. They also allege that some of the data making up this 3TB contains customer medical reports, customer claims, payments to customers, customer ID's, customer scanned bank account papers, hospitals and doctors reserved material, and more. The Avaddon gang have also attached a proof of stolen data screenshot for each affected victim.
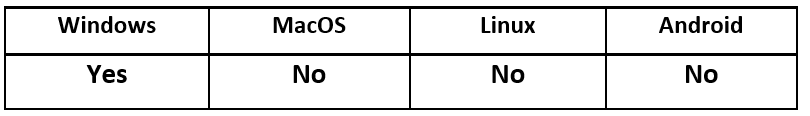
Operating System
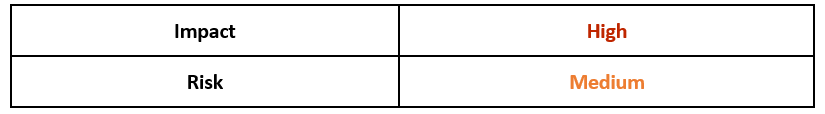
Risk & Impact
Technical Analysis
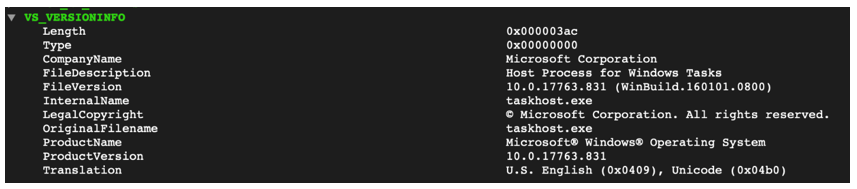
Avaddon ransomware masquerades as Microsoft® host process for Windows tasks called “taskhost.exe”.
This is a common method for malware writers to trick unwitting users into believing that the file is a trusted and legitimate Microsoft file:
Figure 1: Fake 'taskhost.exe' file information.
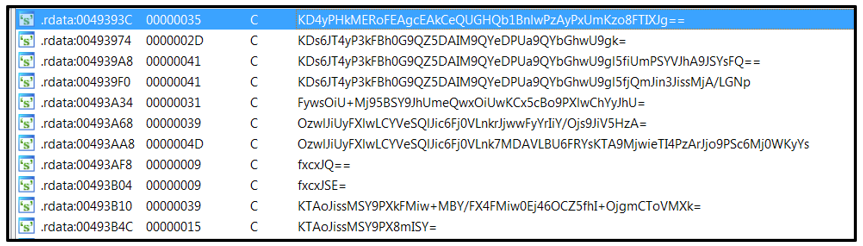
Avaddon samples are not packed, but some of the strings are obfuscated to hinder static detection and analysis:
Figure 2: Obfuscated strings.
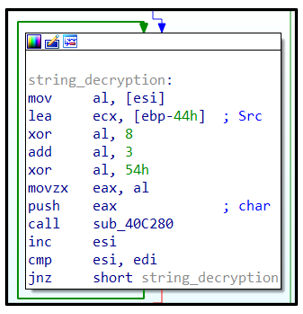
To de-obfuscate the strings, several steps must occur: a base64 decode must first be performed, followed by a XOR operation using a key in hexadecimal, then addition with a key in hex, and then a final XOR operation with a key in hex. The hex values required vary from sample to sample. It has also been observed that some Avaddon samples perform subtraction instead of addition:
Figure 3: String decryption.
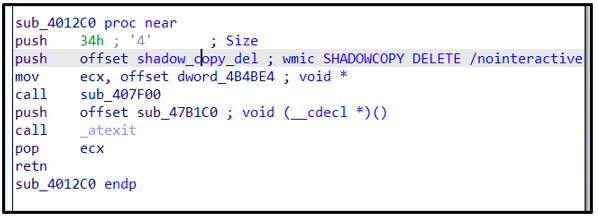
For example, upon de-obfuscation of those strings, a string “KD4yPHkMERoFEAgcEAkCeQUGHQb1BnlwPzAyPxUmKzo8FTIXJg==” decodes to “wmic SHADOWCOPY DELETE /nointeractive”.
The full list of de-obfuscated strings can be found in Appendix A.
Figure 4: Obfuscated string.
Figure 5: De-obfuscated string.
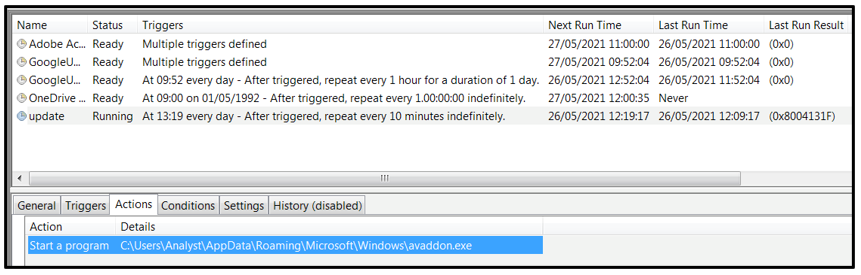
Upon execution, Avaddon creates a copy of itself in the “C:\Users\%user name%\AppData\Roaming\Microsoft\Windows” folder. The copied file is then used to create a scheduled task called “update” to maintain persistence:
Figure 6: Scheduled task called 'update'.
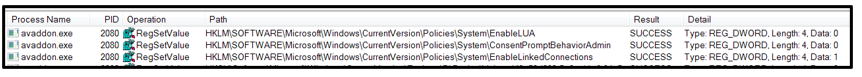
This threat also modifies the registry keys to bypass User Account Control (UAC). It also escalates privileges to obtain access to mapped network drives by setting the registry values of EnableLUA and ConsentPromtBehaviorAdmin to 0 and EnableLinkedConnections to 1:
Figure 7: Modified registry keys.
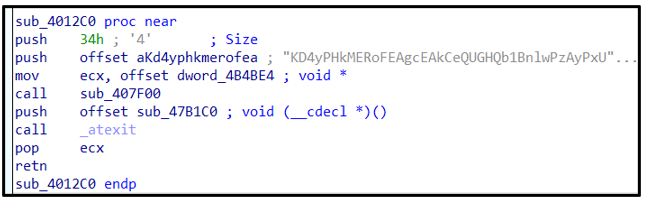
Avaddon then deletes shadow copies using the following commands:
wmic.exe:
- wmic SHADOWCOPY DELETE /nointeractive
vssadmin.exe:
- vssadmin Delete Shadows /All /Quiet
The malware also deletes system backups using the following commands, to ensure the victim can’t easily restore the encrypted files:
wbadmin.exe:
- wbadmin DELETE SYSTEMSTATEBACKUP
- wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest
- wbadmin DELETE SYSTEMSTATEBACKUP -keepVersions:0
bcdedit.exe:
- bcdedit /set {default} recoveryenabled No
- bcdedit.exe -> bcdedit /set {default} bootstatuspolicy ignoreallfailures
Avaddon will begin enumerating the infected system, ignoring certain locations to avoid encrypting files there. Those locations are the following:
- C:\$Recycle.Bin
- C:\Program Files
- C:\Program Files (x86)
- C:\ProgramData
- C:\Users\All Users
- C:\Users\%username%\AppData
- Folders containing the name "Tor Browser”
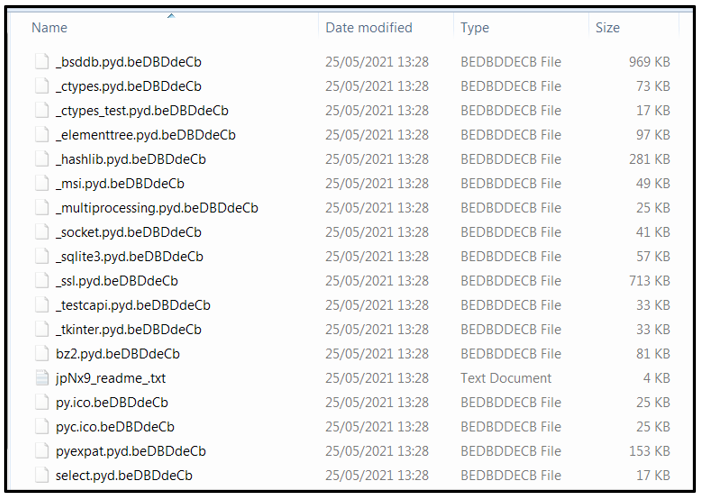
Avaddon will look in the “Program Files” and “Program Files (x86)” folders for the presence of Microsoft Exchange Server, Microsoft SQL Server, and MySQL. If those directories can be found, Avaddon will start encrypting the affected file types and append them with a “.beDBDdeCd” file extension.
The appended file extension varies from sample to sample, but it typically follows a pattern of 9-10 lower/upper case letters [a-eA-E]{9,10}. In earlier versions of Avaddon, the appended file extension was ‘.avdn’:
Figure 8: Encrypted files.
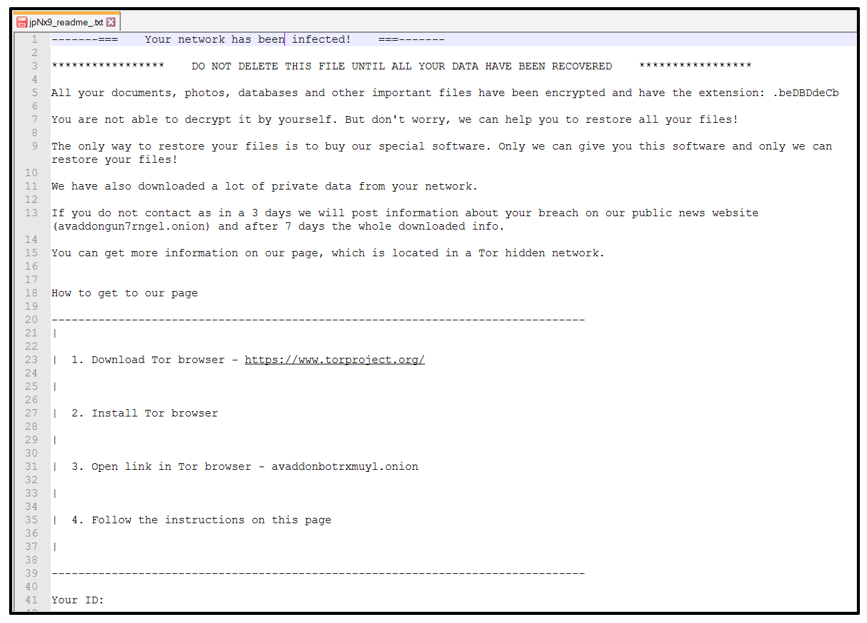
This threat drops a ransom note titled ‘jpNx9_readme_.txt’ in each affected directory. The random lower-and-upper-case letters and numbers used for naming the readme text file also vary from sample to sample.
The ransom note informs the infected user that all documents, photos, databases, and other file of importance have been encrypted:
Figure 9: Avaddon ransom note.
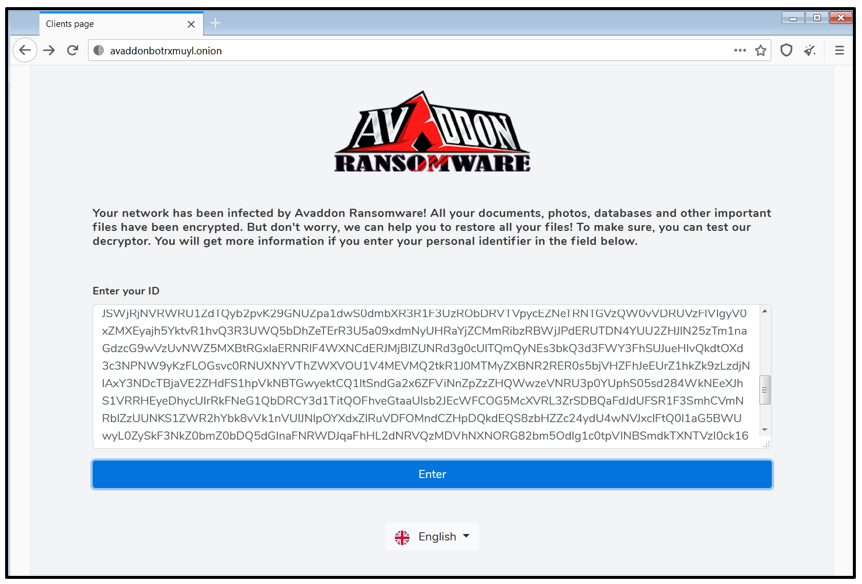
To access the Avaddon’s dark web page, the victim is required to download a Tor browser and navigate to the attacker’s dark web site to input the key. This key can be found in the ransom note:
Figure 10: Avaddon URL for key input.
The ransom note alerts the victim that many files have been downloaded by the threat actor. They then have three days to get in contact with the Avaddon group, otherwise the sensitive data will be published on the attacker’s dark web site at avaddongun7rngel[dot]onion.
Figure 11: Avaddon victims (company names obscured for privacy).
To ensure that the ransom is paid in a timely fashion, Avaddon DDoSes the victim’s website, rendering it unusable and inaccessible. The page also contains a list of all new companies that have become Avaddon’s latest victims. Attackers also publish some screenshots of the material that has been stolen from each victim. For example, the screenshots may include copies of passports, ID cards, and other private documents.
The “Full dump” section of the website contains a list of data dumps from victims who have refused to cooperate with the Avaddon gang. Those “dump” files can be downloaded by anyone who accesses the site. These files are compressed, and no password was required to extract the contents:
Figure 12: unzipped data dump contents.
Yara Rule
The following Yara rule was authored by the BlackBerry Threat Research Team to catch the threat described in this document:
import "pe"
import "hash"
rule Mal_Ransom_Win32_Avaddon_2021
{
meta:
description = "Detects W32 Avaddon 2021 ransomware"
author = " Blackberry Threat Research team "
date = "2021-13-05"
strings:
//"ext":"
$x1 = {22657874223a22}
//"rcid":"
$x2 = {2272636964223a22}
//"hdd":
$x3 = {22686464223a}
//"name":"
$x4 = {226e616d65223a22}
//"size":
$x5 = {2273697a65223a}
//"type":"
$x6 = {2274797065223a22}
//"lang":"
$x7 = {226c616e67223a22}
condition:
uint16(0) == 0x5a4d and
hash.md5(pe.rich_signature.clear_data) == "d1bea2a661ac41ee1e80a607afed3f89" and
pe.imphash() == "b56503b8c4f46a3a086734c09c6bd0f3" and
pe.number_of_sections == 5 and
filesize < 777KB and
all of ($x*)
}
|
Indicators of Compromise (IoCs)
At BlackBerry, we take a prevention-first and AI-driven approach to cybersecurity. Putting prevention first neutralizes malware before the exploitation stage of the kill-chain.
By stopping malware at this stage, BlackBerry solutions help organizations increase their resilience. It also helps reduce infrastructure complexity and streamline security management to ensure business, people, and endpoints are secure.
File System Actions
Created:
- C:\Users\%user name%\AppData\Roaming\Microsoft\Windows\<avaddon_sample.exe>
- [a-zA-Z0-9]{5}_readme_.txt ← ransom note.
- Example: E8Jmg_readme_.txt
- .aEEeadBBD ← appended file extension, varies from sample to sample.
Deleted:
- Shadow volume copies.
- Backups.
Modified:
- All targeted files post-encryption.
Mutex:
- Global{A86668A3-8F20-41F3-97D1-676B2AD6ADF7}
Processes
Created:
- wmic SHADOWCOPY DELETE /nointeractive
- wbadmin DELETE SYSTEMSTATEBACKUP
- wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest
- wbadmin DELETE SYSTEMSTATEBACKUP -keepVersions:0
- vssadmin Delete Shadows /All /Quiet
- bcdedit /set {default} recoveryenabled No
- bcdedit /set {default} bootstatuspolicy ignoreallfailures
Services
Terminated:
- DefWatch, ccEvtMgr, ccSetMgr, SavRoam, dbsrv12, sqlservr, sqlagent, Intuit.QuickBooks.FCS, dbeng8, sqladhlp, QBIDPService, Culserver, RTVscan, vmware-usbarbitator64, vmware-converter, VMAuthdService, VMnetDHCP, VMUSBArbService, VMwareHostd, sqlbrowser, SQLADHLP, sqlwriter, msmdsrv, tomcat6, QBCFMonitorService
|
Appendix A
base64 decode -> XOR 0x8 -> ADD 0x3 -> XOR 0x54
|
Deobfuscated strings
|
DBAH9QgaCwYNHjI8KzAsMCcVDQgyPyUwKCwNHBYrKyY/FfcmKywyMD8NCTA9MjwyJiwNDCIsFSY+
|
SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
|
Bj86Oz0mHTI/NCYlHDA/PyY8FTIwPyw=
|
EnableLinkedConnections
|
Bj86Oz0mHfYa
|
EnableLUA
|
HDA/LCY/FQkrMD4pFRsmMToXMjArGiU+Mj8=
|
ConsentPromptBehaviorAdmin
|
DAIM9QYeBQsS9wY=
|
SYSTEMDRIVE
|
CQsQGAsaHgcSHQYMcSFhV3I=
|
PROGRAMFILES(x86)
|
9gwGCwkLEAcSHQY=
|
USERPROFILE
|
CSswOCs6PgU6FTo=
|
ProgramData
|
CSswOCs6PnkHMj0mLA==
|
Program Files
|
Gh0d9gwGCwwJCxAHEh0G
|
ALLUSERSPROFILE
|
GikpBToVOg==
|
AppData
|
CfYbHRIc
|
PUBLIC
|
9R4J
|
TMP
|
9TAreRsrMCgsJis=
|
Tor Browser
|
BgcS
|
EF
|
HgwQHDo8MSY=
|
MSOCache
|
DQgyPyUwKCw=
|
\Windows
|
DQkrMDgrOj55BzI9Jiw=
|
\Program Files
|
DfYsJissDRo9PXn2LCYrLA==
|
\Users\All Users
|
DRopKQU6FTo=
|
\AppData
|
DR4yPCswLDAnFQ0IMj8lMCgs
|
\Microsoft\Windows
|
KD4yPHkMERoFEAgcEAkCeQUGHQb1BnlwPzAyPxUmKzo8FTIXJg==
|
wmic SHADOWCOPY DELETE /nointeractive
|
KDs6JT4yP3kFBh0G9QZ5DAIM9QYeDPUa9QYbGhwU9gk=
|
wbadmin DELETE SYSTEMSTATEBACKUP
|
KDs6JT4yP3kFBh0G9QZ5DAIM9QYeDPUa9QYbGhwU9gl5fiUmPSYVJhA9JSYsFQ==
|
wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest
|
KDs6JT4yP3kFBh0G9QZ5DAIM9QYeDPUa9QYbGhwU9gl5fjQmJin3JissMjA/LGNp
|
wbadmin DELETE SYSTEMSTATEBACKUP -keepVersions:0
|
FywsOiU+Mj95BSY9JhUmeQwxOiUwKCx5cBo9PXlwChYyJhU=
|
vssadmin Delete Shadows /All /Quiet
|
OzwlJiUyFXlwLCYVeSQlJic6Fj0VLnkrJjwwFyYrIiY/Ojs9JiV5HzA=
|
bcdedit /set {default} recoveryenabled No
|
OzwlJiUyFXlwLCYVeSQlJic6Fj0VLnk7MDAVLBU6FRYsKTA9MjwieTI4PzArJjo9PSc6Mj0WKyYs
|
bcdedit /set {default} bootstatuspolicy ignoreallfailures
|
fxcxJQ==
|
.vhd
|
fxcxJSE=
|
.vhdx
|
KTAoJissMSY9PXkFMiw+MBY/FX4FMiw0Ej46OCZ5fhI+OjgmCToVMXk=
|
powershell Dismount-DiskImage -ImagePath
|
KTAoJissMSY9PX8mISY=
|
powershell.exe
|
ACsmOiU+JgB/FSEV
|
_readme_.txt
|
ERAeBgULEvcG
|
HOMEDRIVE
|
ERAeBgka9RE=
|
HOMEPATH
|
BSYsNBUwKQ0=
|
Desktop\
|
HDA/FSswPXkJOj8mPQ0FJiw0FTAp
|
Control Panel\Desktop
|
CDo9PQk6KSYr
|
WallPaper
|
JCQyJS4u
|
{{id}}
|
JCQmIRUuLg==
|
{{ext}}
|
FiklOhUm
|
update
|
GD0wOzo9DSQaYVdXV2EabH5hB2tpflVqB2x+YmgFan5XaFcbaxoFVxoFB2gu
|
Global\{A86668A3-8F20-41F3-97D1-676B2AD6ADF7}
|
DQkrMDgrOj55BzI9JiwNHjI8KzAsMCcVDQYhPDE6PzgmeQwmKxcmKw==
|
\Program Files\Microsoft\Exchange Server
|
DQkrMDgrOj55BzI9Jix5cSFhV3INHjI8KzAsMCcVDQYhPDE6PzgmeQwmKxcmKw==
|
\Program Files (x86)\Microsoft\Exchange Server
|
DQkrMDgrOj55BzI9JiwNHjI8KzAsMCcVeQwKHXkMJisXJis=
|
\Program Files\Microsoft SQL Server
|
DQkrMDgrOj55BzI9Jix5cSFhV3INHjI8KzAsMCcVeQwKHXkMJisXJis=
|
\Program Files (x86)\Microsoft SQL Server
|
DQkrMDgrOj55BzI9JiwNPiIsKj0=
|
\Program Files\mysql
|
DQkrMDgrOj55BzI9Jix5cSFhV3INPiIsKj0=
|
\Program Files (x86)\mysql
|
CxAQ9Q0cEh73aw==
|
ROOT\CIMV2
|
CAod
|
WQL
|
DAYdBhz1eXN5BwsQHnkIMj9sawAJJisnBzArPjoVFSYlBToVOgAJJisnCSswPAAJKzA8Jiws
|
SELECT * FROM Win32_PerfFormattedData_PerfProc_Process
|
Hzo+Jg==
|
Name
|
EgUJKzA8Jiws
|
IDProcess
|
CSYrPCY/FQkrMDwmLCwwK/UyPiY=
|
PercentProcessorTime
|
LBc8MTAsFQ==
|
svchost
|
PCwrLCw=
|
csrss
|
LCYrFzI8Jiw=
|
services
|
PSw6LCw=
|
lsass
|
KDI/PTA4MD8=
|
winlogon
|
LCkwMD0sFw==
|
spoolsv
|
JiEpPTArJis=
|
explorer
|
CxY/FTI+JhsrMDQmKw==
|
RuntimeBroker
|
DCIsFSY+
|
System
|
KTAoJissMSY9PQ==
|
powershell
|
KCw8KzIpFQ==
|
wscript
|
HCsmOhUm
|
Create
|
CDI/bGsACSswPCYsLA==
|
Win32_Process
|
HDA+Pjo/JR0yPyY=
|
CommandLine
|
fiw6JyY=
|
-safe
|
DBAH9QgaCwYNHjI8KzAsMCcVDQgyPyUwKCx5H/UNHBYrKyY/FfcmKywyMD8NCDI/PTA4MD8=
|
SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
|
JiEpPTArJit/JiEmfQ==
|
explorer.exe,
|
DDEmPT0=
|
Shell
|
OzwlJiUyFXlwLCYVeSw6JyY7MDAVeT8mFSgwKzQ=
|
bcdedit /set safeboot network
|
OzwlJiUyFXlwJSY9JhUmFzo9FiZ5LDonJjswMBU=
|
bcdedit /deletevalue safeboot
|
BlackBerry Assistance
If you’re battling Avaddon ransomware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.