Threat Thursday: SystemBC – a RAT in the Pipeline
Summary
SystemBC is a Remote Access Trojan (RAT) written in Russian, which was used as part of the attack chain involved in the DarkSide ransomware attack against major American oil pipeline system Colonial Pipeline. The malware has been observed initializing ransomware as a Service (RaaS) attacks such as Ryuk and Egregor. This threat was first spotted in early 2019, but it has evolved over time to carry out its communications more discreetly.
This malware has grown in popularity among threat actors for providing a persistent remote connection to a victim’s machine that allows them to drop additional malicious executables, Windows® commands, PowerShell scripts, and .bat/VBS scripts to the infected machine. It’s also popular among Ransomware-as-a-Service (RaaS) affiliates due to its use of the TOR browser’s anonymizing network, which encrypts and hides Command and Control (C2) network traffic performed in the attack.
Operating System
Risk & Impact
Technical Analysis
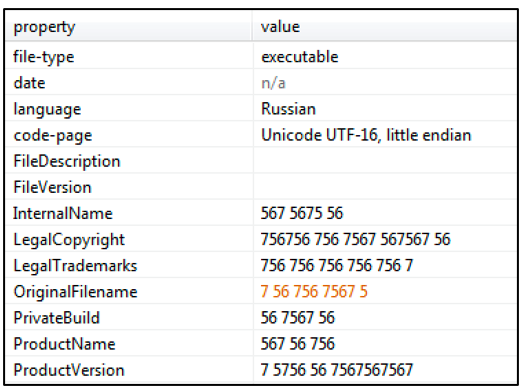
SystemBC has had numerous variants in its two-year life span. The latest version of the malware is a wrapper which contains the encrypted malicious payload within. The wrapper is written in Russian and contains interesting file metadata that could give clues as to the development environment used by the author:
Figure 1: Wrapper metadata.
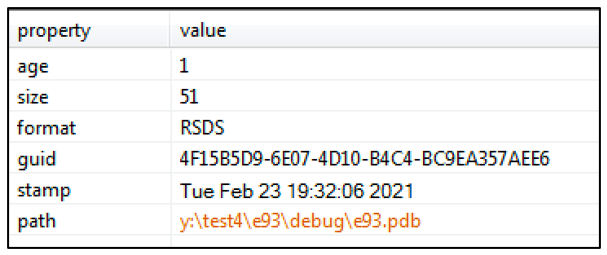
The file contains a timestamp from February 23rd 2021, and has a program database (PDB) path of ‘y:\test4\e93\debug\e93.pdb’. PDB files store debugging information and are created from source files during compilation; the debug path points to the location that this file is stored. As this debug path is shared with many other payloads found on VirusTotal including BazarLoader, this could suggest that the payloads were all wrapped within the same environment:
Figure 2: Timestamp and debug path.
The attack chain begins when the wrapper is executed, and process-hollowing is carried out. This involves decrypting the payload and injecting it into the memory of a child process, in this case “svchost.exe”. It is likely named this after the legitimate Windows systems process in an attempt to remain undetected.
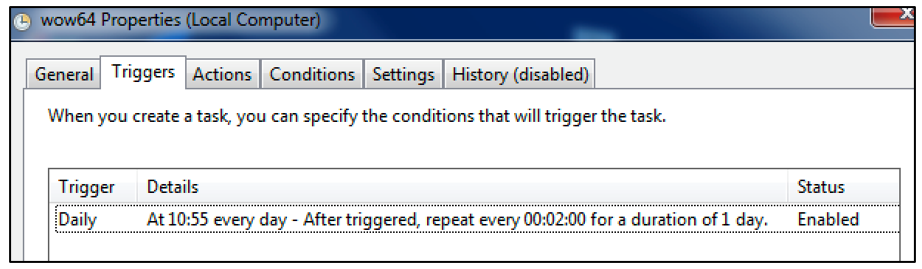
The malware gains persistence by creating a scheduled task on the infected machine called “wow64.job”:
Figure 3: scvhost creating scheduled task 'wow64.job'.
The scheduled task ensures that the malware is set to execute every two minutes after its initial launch:
Figure 4: Wow64 properties.
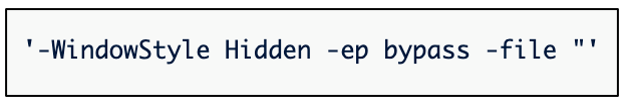
Additional malicious PE file and script payloads can be delivered remotely through the backdoor that is established by the malware. Any future payloads that are delivered via the C2 are stored within the %TEMP% directory, and they are also launched through the creation of a scheduled task. The exception to this rule is PowerShell scripts, which are launched with the command shown below:
Figure 5: Command to launch .PS1 files.
Initial variants of SystemBC relied on SOCK5 network proxy connections to perform encrypted communications between the host and victim machines. Later versions of the RAT evolved to use two networking functionalities to perform this C2 communication. One of these methods is TLS traffic carried out over the TOR anonymized network.
However, in the latest variation of the malware, the malicious payload is smaller in size and does not contain the TOR client functionality. Instead, the RAT relies on communication through hard-coded addresses over IPV4 TCP traffic on non-standard ports.
In the figure below, the malware reaches out to the first of two hard-coded C2 addresses, 23[.]227[.]202[.]22. The connection is carried out over TCP traffic on port 4142. The malware maintains an open connection with the C2 server after sending its initial packet:
Figure 6: TCP connection over port 4142 to first hardcoded C2 address.
Below is the packet that was sent to the above domain. The initial packet is 62 bytes in size:
Figure 7: Packet sent to first hardcoded C2 address.
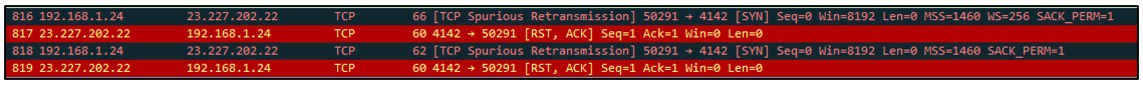
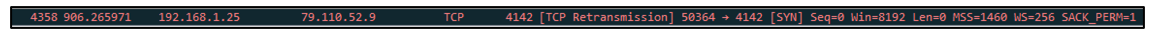
A similar connection is also created with the second hardcoded domain, 79[.]110[.]52[.]9:
Figure 8: TCP connection over port 4142 to second hardcoded C2 address.
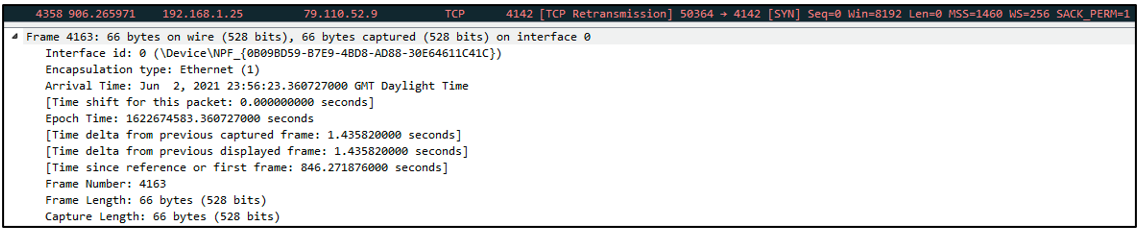
The initial packet sent to the second domain is 66 bytes in size:
Figure 9: Packet sent to second hardcoded C2 address.
These connections to remote servers allow attackers to drop malicious payloads such as the Ryuk and Egregor payloads, as seen in the DarkSide ransomware attack on the Colonial Pipeline. These connections, along with the RAT’s persistence, offers threat actors avenues to perform additional malicious activity beyond their initial campaign.
The evolution of SystemBC since its initial discovery shows no signs of halting, as the malware adapts and incorporates different techniques to facilitate malicious campaigns. With the rise in ransomware attacks across the globe in recent months, it will come as no surprise if SystemBC reappears as a part of the delivery of future newsworthy attacks.
Yara Rule
The following Yara rule was authored by the BlackBerry Threat Research Team to catch the threat described in this document:
import "pe"
import "hash"
rule Mal_Backdoor_Win32_SystemBC_2021
{
meta:
description = "Detects Win32 SystemBC RAT"
author = " Blackberry Threat Research team "
date = "2021-01-06"
strings:
$x1 = "(\"inconsistent IOB fields\", stream->_ptr - stream->_base >= 0)"
$x2 = "f:\\vs70builds\\3077\\vc\\crtbld\\crt\\src\\sprintf.c"
$x3 = "y:\\test4\\e93\\Debug\\e93.pdb"
$x4 = "7 56 756 7567 5"
condition:
uint16(0) == 0x5a4d and
pe.imphash() == "18c64388b1cd2a51505e0d24460c1ed7" and
pe.number_of_sections == 6 and
filesize < 800KB and
3 of ($x*)
}
|
BlackBerry Strategy
At BlackBerry, we take a prevention-first and AI-driven approach to cybersecurity. Putting prevention first neutralizes malware before the exploitation stage of the kill-chain. By stopping malware at this stage, BlackBerry solutions help organizations increase their resilience. It also helps reduce infrastructure complexity and streamline security management to ensure business, people, and endpoints are secure.
Indicators of Compromise (IoCs)
File System Actions
Created:
- C:\Windows\Tasks\wow64.job
SHA256:
- 2dc93817039e6fa4fae014e1386cffa7ac35b89feac59d8abe7f51be1c089580
- 9916d1369c9d2d0e64a8d5d9bb185a63386c27949b46fcec479ff024f3326340
Hard-Coded C2s:
- 79.110.52.9 – TCP - 4142
- 23.227.202.22 – TCP - 4142
PowerShell Command:
- WindowsStyle Hidden -ep bypass -file “
Registry Key:
- HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\CompatibilityAdapter\Signatures\wow64.job
|
BlackBerry Assistance
If you’re battling SystemBC or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you providing around-the-clock support, where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment.
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.