Hunter Becomes Hunted: Zebra2104 Hides a Herd of Malware
Executive Summary
The BlackBerry Research & Intelligence Team has uncovered an unusual connection between the actions of three distinct threat groups, including those behind financially-motivated ransomware such as MountLocker and Phobos, as well as the espionage-related advanced persistent threat (APT) group known as StrongPity. While it might seem implausible for criminal groups to be sharing resources, we found these groups had a connection that is enabled by a fourth; a threat actor we have dubbed Zebra2104, which we believe to be an Initial Access Broker (IAB).
In this post, we will discuss what led us to these findings, what an IAB is, and how each piece fits into the puzzle. Once we look at each piece in context, we can better assess the full ramifications of these discoveries, and project what is yet to come.
Introduction
When conducting research for our book, “Finding Beacons in the Dark: A Guide to Cyber Threat Intelligence,” we stumbled upon a domain that piqued our interest due to its similarity to a naming convention that we’d seen in a previous threat hunt.
This single domain led us down a path where we would uncover multiple ransomware attacks, and an APT command-and-control (C2). The path also revealed what we believe to be the infrastructure of an IAB: Zebra2104.
IABs typically first gain entry into a victim’s network, then sell that access to the highest bidder on underground forums located in the dark web. Later, the winning bidder will often deploy ransomware and/or other financially motivated malware within the victim’s organization, depending on the objectives of their campaign.
This discovery presented a great opportunity for us to understand the attribution of IABs. Performing intelligence correlation can help us build a clearer picture of how these disparate threat groups create partnerships and share resources to further enhance their nefarious goals.
As we delved into and peeled off each overlapping layer throughout our investigation, it appeared at times that we were merely scratching the surface of such collaborations. There is undoubtedly a veritable cornucopia of threat groups working in cahoots, far beyond those mentioned in this blog.
In this first installment, we will document the tip of this iceberg. A more comprehensive set of findings will come in a follow-up piece in the near future.
Now, let’s explore what we found!
It All Begins with Cobalt Strike
In April of 2021, we observed the domain trashborting[.]com serving Cobalt Strike Beacons. We also identified multiple Beacons containing differing configuration data that was reaching out to this same domain, during April and August of this year.
One such Beacon served from the IP 87.120.37[.]120 had trashborting[.]com specified as the C2 server in its configuration.
IP
|
Country
|
ASN
|
ASN Number
|
87.120.37.120
|
Bulgaria
|
Neterra Ltd
|
AS34224
|
Table 1 – Trashborting[.]com IP address
The domain trashborting[.]com had previously resolved to this IP address, as well as the neighboring IP 87.120.37[.]119.
These IP addresses had also hosted two domains with the .us Top Level Domain (TLD):
- lionarivv[.]us
- okergeeliw[.]us
Rediscovering Malicious Spam Infrastructure
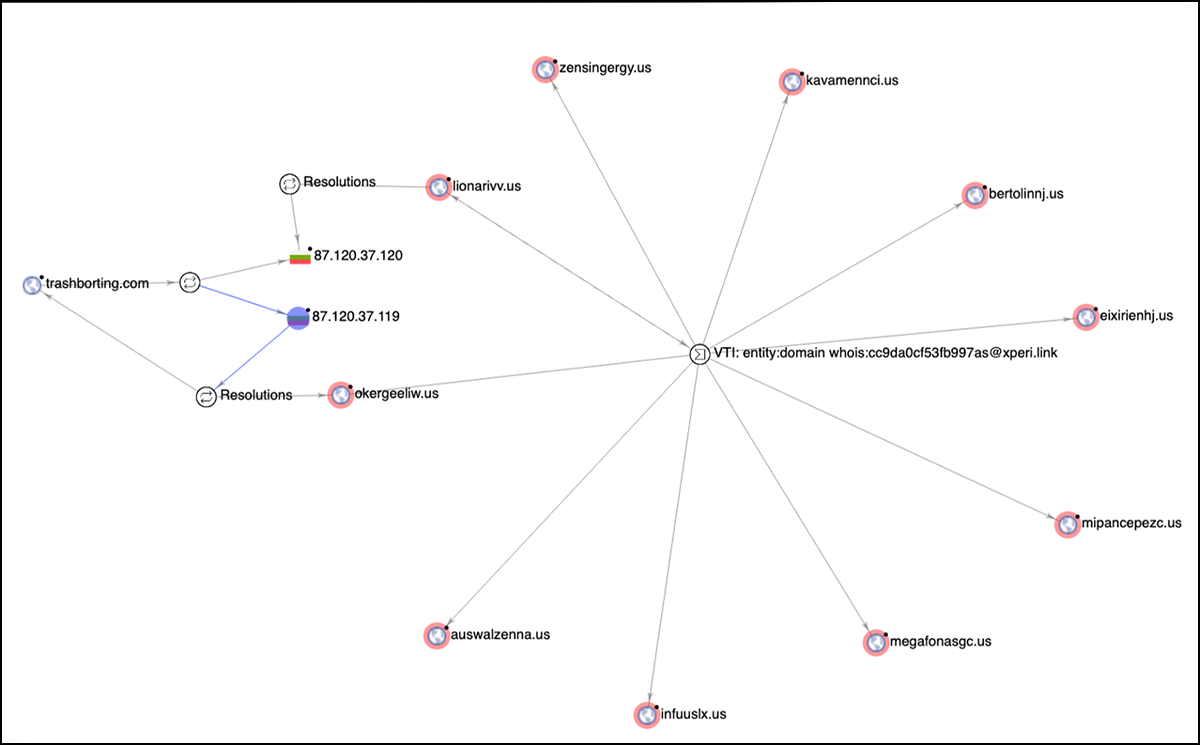
Each of the aforementioned domains had a mail server and associated MX record, meaning they had the capability to send emails en masse. By examining the WHOIS information for these servers, we discovered that both domains were registered on 2020-09-12 by the email address georgesdesjardins285[at}xperi[.]link. By digging into the domain registrant information, we found that this email address had registered eight additional .us domains on the same date.
These domains popped up previously in a Microsoft blog titled: “What tracking an attacker’s email infrastructure tells us about persistent cybercriminal operations.”
The Microsoft 365 Defender Threat Intelligence Team found that these servers had been serving malspam that resulted in varying ransomware payloads, such as Dridex, which we were able to corroborate.
Type
|
IOC
|
Domain
|
bertolinnj[.]us
|
Domain
|
eixirienhj[.]us
|
Domain
|
auswalzenna[.]us
|
Domain
|
megafonasgc[.]us
|
Domain
|
zensingergy[.]us
|
Domain
|
infuuslx[.]us
|
Domain
|
mipancepezc[.]us
|
Domain
|
kavamennci[.]us
|
Table 2 - Additional .us domains
The interlinking relationships between all these domains can be seen in Figure 1 below.
Figure 1 - Malspam distribution
Dridex Malspam
Two domains of particular interest to us were kavamennci[.]us and zensingergy[.]us. These were involved in a phishing campaign targeting Australian real estate companies and state government departments in September of 2020, which are evidenced as follows.
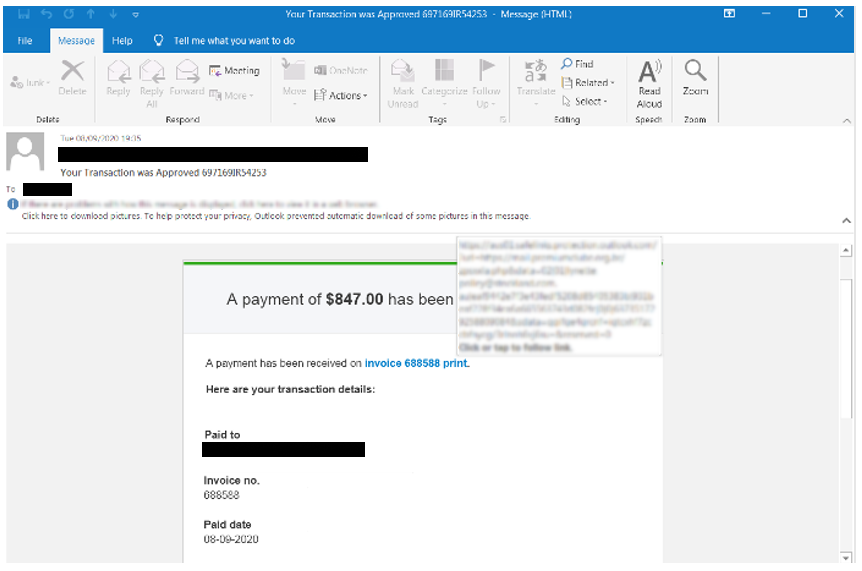
The first spam-mail was sent from an address coming from the kavamennci[.]us domain, and it appears to target employees at one of the Australia's largest property groups. The mail was titled “Your Transaction was Approved 697169IR54253” and it contained an embedded hyperlink that decoded to “hxxps[:]//mail[.]premiumclube[.]org[.]br/zpsxxla.php.”
Figure 2 - Phishing email targeting employees at one of Australia’s largest property groups
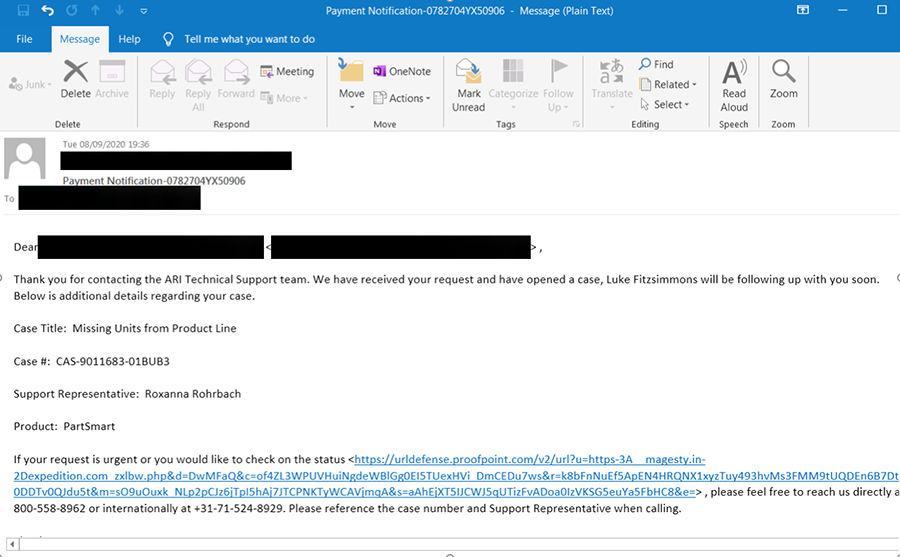
The second email was directed at an Australian government agency, and titled “Payment Notification-0782704YX50906.”
Figure 3 - Phishing email targeting an Australian Government Agency
Sent from an address originating from the “zensingergy[.]us” domain, this email contained a similar embedded link: “hxxps[:]//magesty[.]in-expedition[.]com/zxlbw.php.”
In addition, the last portion of the embedded malicious links — “zpsxxla.php” and “zxlbw.php” — also appear in the Microsoft blog, and are mentioned as part of a Dridex campaign from September 2020 that was described by Microsoft as follows:
“These Dridex campaigns utilized an Emotet loader and initial infrastructure for hosting, allowing the attackers to conduct a highly modular email campaign that delivered multiple distinct links to compromised domains. These domains employed heavy sandbox evasion and are connected by a series of PHP patterns ending in a small subset of options: zxlbw.php, yymclv.php, zpsxxla.php, or app.php.”
This is significant because it demonstrates the power of open source intelligence (OSINT) and threat hunting. Initially, we started off with one domain (trashborting[.]com), which helped us to unravel other threat actors that we will look at in more detail later. Although Dridex is not the target of this paper, it is certainly a noteworthy find to mention.
Peering Down the Intelligence Rabbit Hole
The trashborting.com domain was registered with a ProtonMail email address (ivan.odencov1985[at]protonmail[.]com) and contained Russian WHOIS registrant information:
Type
|
IOC
|
Registrar
|
PDR Ltd. d/b/a PublicDomainRegistry.com
|
Domain Status
|
client delete prohibited
client update prohibited
client delete prohibited
client hold
|
Email
|
Ivan.odencov1985[at]protonmail[.]com (registrant, admin, tech)
|
Name
|
Ivan (registrant, admin, tech)
|
Organization
|
-
|
Street
|
-
|
City
|
Moscow (registrant, admin, tech)
|
State
|
Moscow (registrant, admin, tech)
|
Postal Code
|
123066 (registrant, admin, tech)
|
Country
|
RU (registrant, admin, tech)
|
Phone
|
+7.993216690 (registrant, admin, tech)
|
Name Servers
|
ns1.entrydns.net
ns2.entrydns.net
ns3.entrydns.net
ns4.entrydns.net
|
Table 3 - Trashborting WHOIS information
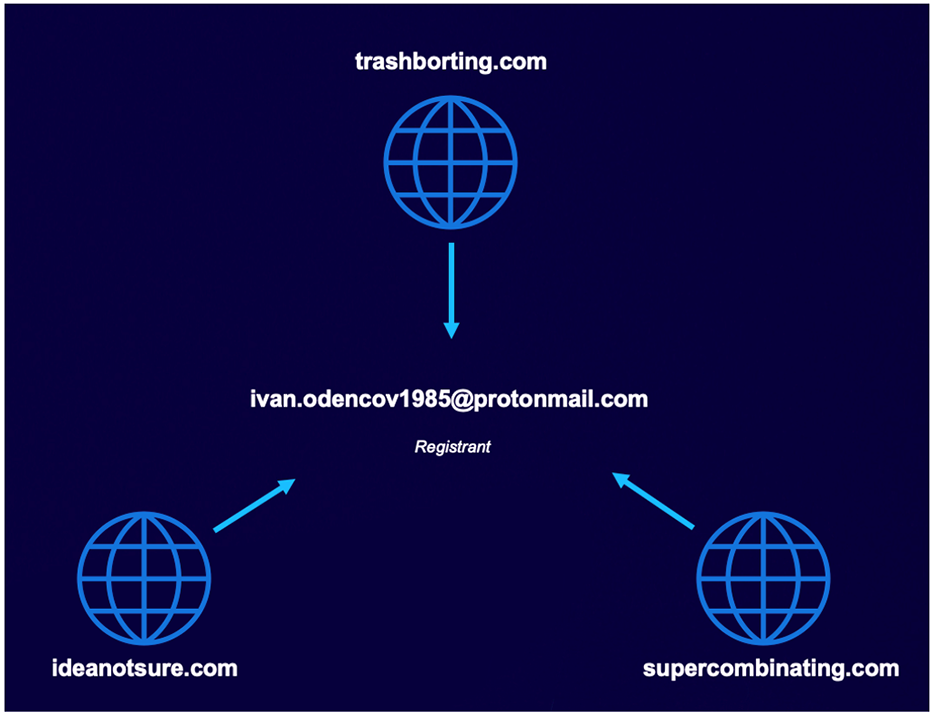
This email address was also used to register two additional sister domains on the same date: July 17, 2020. Both had been observed serving Cobalt Strike Beacon.
Figure 4 - Trashborting and sister domains
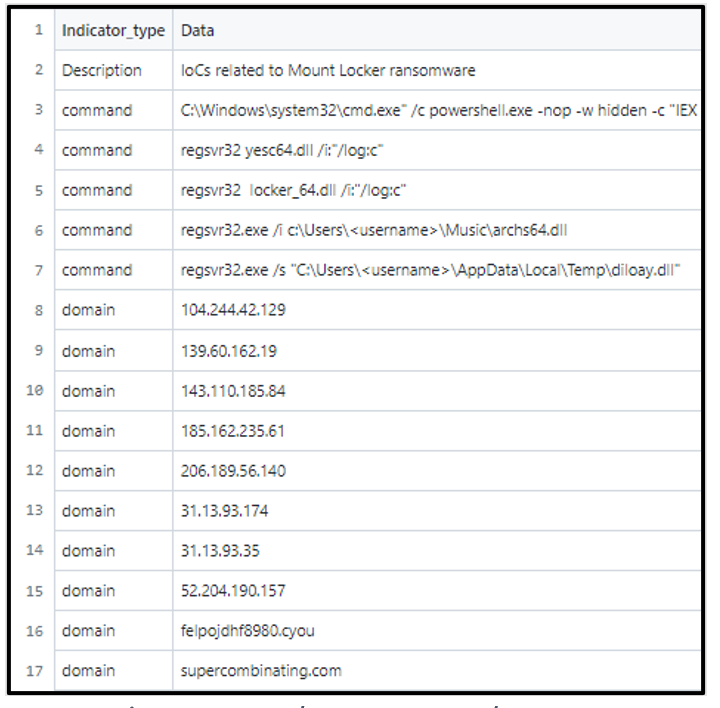
In March of 2021, Sophos listed supercombinating[.]com as an indicator of compromise (IOC).
Figure 5 - Sophos MountLocker IOCs
The MountLocker group is a financially motivated threat group that offers a Ransomware-as-a-Service (RaaS) model; they have been active since July of 2020. As has become the trend with recent ransomware operators, MountLocker employs double extortion tactics. This means that the malware operators exfiltrate sensitive documents and data from the victim prior to encryption, then threaten to publish said data on the dark web should their ransom demands not be met.
Such attacks typically leverage Cobalt Strike Beacon to both spread laterally and propagate the MountLocker ransomware within the victim network. In this instance, this is done via supercombinating[.]com.
Sophos has supposed that the MountLocker group has links to, or has in fact become, the recently emerged AstroLocker group. This is because one of the group’s ransomware binaries has been linked to a support site of AstroLocker. It’s possible that this group is trying to shed any notoriety or baggage that it had garnered through its previous malicious activities.
For additional information, you can check out our blog on MountLocker, which sheds further light on affiliate operations and double extortion capabilities.
MountLocker Activity
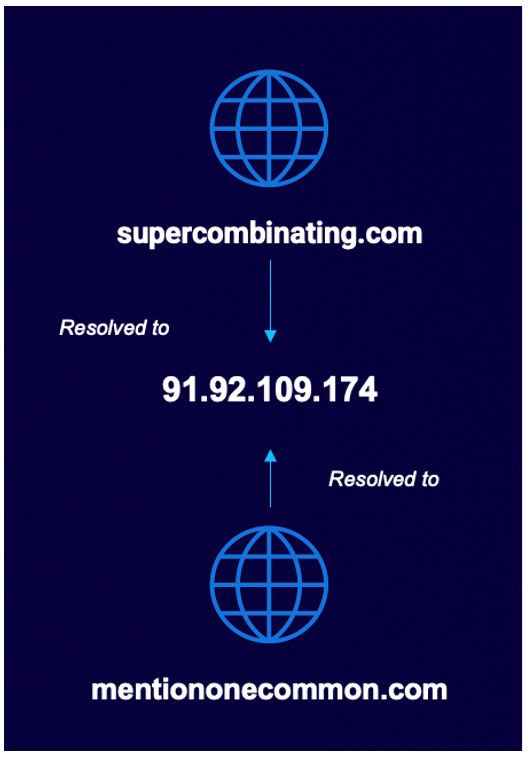
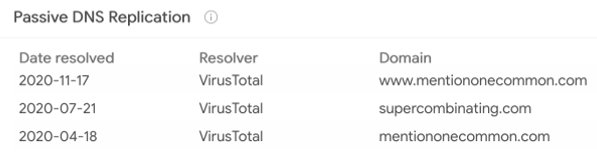
At this point, we noticed that supercombinating[.]com had also resolved to the IP address 91.92.109[.]174, which itself had hosted the domain mentiononecommon[.]com. Both domains resolved to this IP in an alternating fashion between April and November of 2020, as illustrated in the image below.
Figure 6 - Domain resolution
This alternating resolution timeline can be seen below:
Figure 7 - Alternating IP resolution
So, what does this mean, and where does mentiononecommon[.]com fit into the puzzle? The answer to this question requires a little more background information to paint a clearer picture.
Additional OSINT led to us uncover links between mentiononecommon[.]com and the APT group known as StrongPity. Before we discuss those connections, let’s look at who the StrongPity group are, and what they are known for.
Why Hello There, StrongPity!
StrongPity, aka Promethium (Microsoft), is an APT group that has been operational as far back as 2012. It was previously alleged that this group is Turkish state-sponsored, though this is unconfirmed.
Their modus operandi has typically been to use watering hole attacks to deliver Trojanized versions of various commonly used utilities. To accomplish these attacks, a combination of imitation websites and redirects are employed to lure the victim into a false sense of security. Utilities such as WinRAR, Internet Download Manager, and CCleaner have all been victimized in the past to deliver the group’s malware.
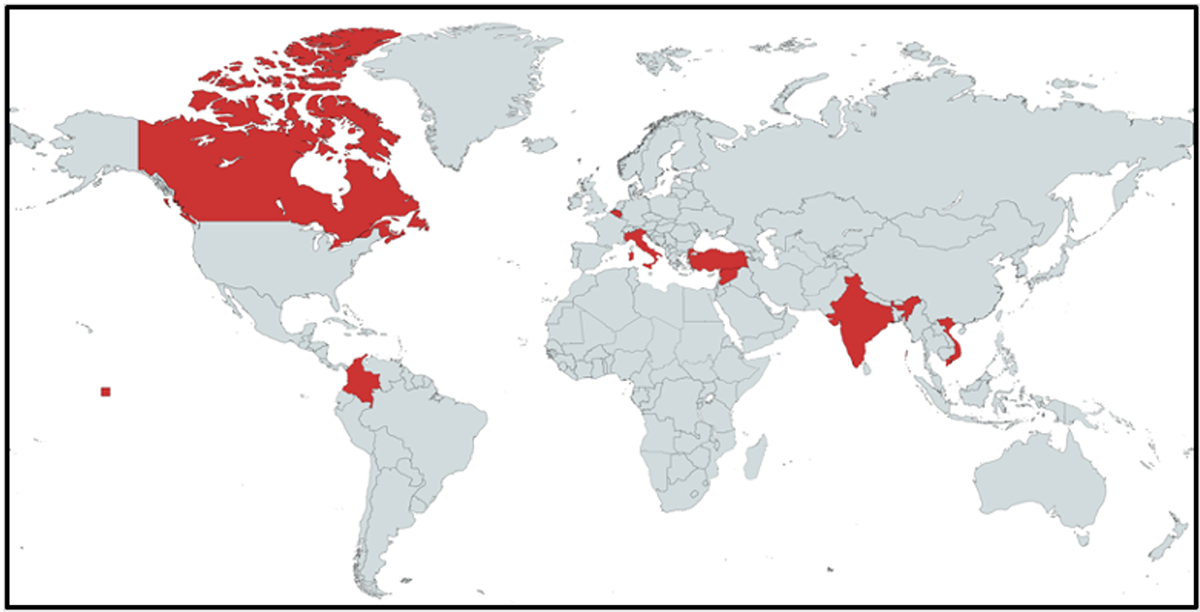
The scope of their activities includes victims based across several continents, as seen in Figure 8 below.
Figure 8 - Countries targeted by StrongPity
In June of 2020, Cisco’s Talos Intelligence reported mentiononecommon[.]com as a StrongPity C2 server. The domain also served three files related to StrongPity, one of which was the previously mentioned Trojanized version of the Internet Download Manager utility.
SHA256
|
Filename
|
c936e01333e3260547a8c319d9cfc1811ba5793e182d0688db679ec2b30644c5
|
Installer.exe
|
e843af007ac3f58e26d5427e537cdbddf33d118c79dfed831eee1ffcce474569
|
SecurityHost.exe
|
8844d234d9e18e29f01ff8f64db70274c02953276a2cd1a1a05d07e7e1feb55c
|
SecurityHost.exe
|
Table 4 - mentiononecommon[.]com StrongPity samples
Furthermore, the domain mentiononecommon[.]com was registered to the email address timofei66[at]protonmail[.]com, which also has WHOIS registrant information pointing to Russia.
While this is far from definitive evidence, it is certainly a notable similarity.
Type
|
IOC
|
WHOIS Server
|
whois.namecheap.com
|
Registrar
|
NameCheap, Inc.
|
Domain Status
|
clientTransferProhibited
|
Email
|
Timofei66[at]protonmail[.]com (registrant, admin, tech)
|
Name
|
Timofei Solomin (registrant, admin, tech)
|
Organization
|
-
|
Street
|
YU.gagarina, bld. 12/2, appt. 76 (registrant, admin, tech)
|
City
|
Ufa (registrant, admin, tech)
|
State
|
Respublika Bashkortostan (registrant, admin, tech)
|
Postal Code
|
49875 (registrant, admin, tech)
|
Country
|
RUSSIAN FEDERATION (registrant, admin, tech)
|
Phone
|
77347382066 (registrant, admin, tech)
|
Table 5 - mentiononecommon[.]com WHOIS registrant information
Figure 9 - mentiononecommon[com] serving StrongPity binaries
At this point, we started to suspect that MountLocker and StrongPity may have worked together in some capacity. This theory seemed unlikely, as their motivations did not appear to align. Despite the improbability of the hypothesis, we set out to see whether we could prove it, and we stumbled upon yet another curious find.
Three Groups — Is That All?
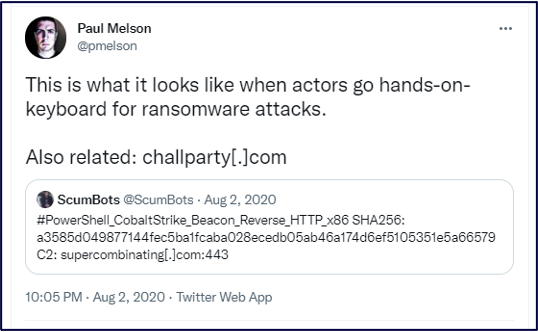
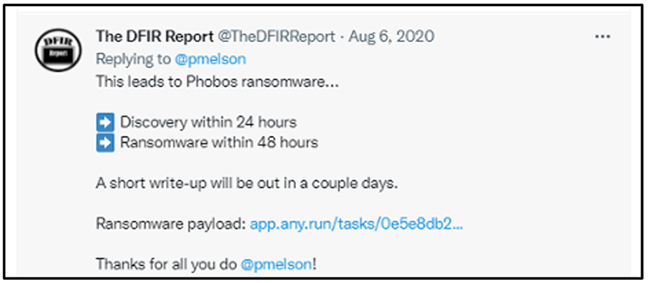
Through a tweet from The DFIR Report, we saw that more ransomware was deployed from supercombinating[.]com, but it was not MountLocker as we had seen previously. This time, Phobos ransomware took its place, which we confirmed through the linked Any.Run sandbox report.
This raised more questions. Were MountLocker and Phobos possibly related? Were two different ransomware groups operating from the same infrastructure? Was this a delivery system? Was an IAB playing a part in all this?
Figure 10 – Tweet by Paul Melson re: Cobalt Strike Beacon relating to supercombinating[.]com
Figure 11 – Tweet by The DFIR Report re: Cobalt Strike Phobos deployment via supercombinating[.]com
Phobos is a ransomware variant that was first seen in early 2019. It is thought to be based on the Dharma ransomware family. Unlike a lot of other ransomware operators that cast for larger “whale”-sized organizations, Phobos has been seen angling for small-to-medium-sized organizations across a variety of industries, with its average ransom payment received being around $54,000 in July of 2021.
A possible insight as to why the authors chose the name for their ransomware is that Phobos was the god of fear in ancient Greek mythology. Few malware groups are so direct about the feeling they seem to want to instill in their victims.
A Mysterious Fourth Group Emerges
This new information presented a bit of a conundrum. If MountLocker owned the infrastructure, then there would be a slim chance of another ransomware operator also working from it, although it has happened before.
Back in June 2020, the Maze threat actor group added stolen files to its leak site. However, upon visiting the leak site, the stolen data was actually provided by the LockBit threat actor group. When Bleeping Computer reached out to Maze for more information regarding the implied partnership between them and LockBit, the Maze group replied with the following:
"In a few days another group will emerge on our news website, we all see in this cooperation the way leading to mutual beneficial outcome, for both actor groups and companies. Even more, they use not only our platform to post the data of companies, but also our experience and reputation, building the beneficial and solid future. We treat other groups as our partners, not as our competitors. Organizational questions is [sic] behind every successful business.”
In several instances, a delay was observed between an initial compromise using Cobalt Strike and further ransomware being deployed. Based on these factors, we can infer that the infrastructure is not that of StrongPity, MountLocker, or Phobos, but of a fourth group that has facilitated the operations of the former three. This is either done by providing initial access, or by providing Infrastructure as a Service (IaaS).
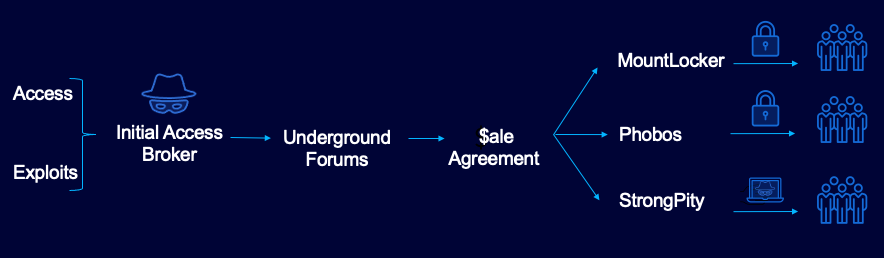
IABs: the Lowdown
An IAB performs the first step in the kill chain of many attacks; this is to say they gain access into a victims' network through exploitation, phishing, or other means.
Figure 12 - IAB’s operation workflow
Once they have established a foothold (i.e., a reliable backdoor into the victim network), they then list their access in underground forums on the dark web, advertising their wares in hopes of finding a prospective buyer.
The price for access ranges from as little as $25, going up to thousands of dollars. Typically, the more annual revenue that the target organization generates, the higher the price an IAB charges for “access.”
Upon successful sale agreement, the winning bidders will generally deploy their malware of choice. This can be anything from ransomware to infostealing malware, and everything in between.
We believe that our three threat actors – MountLocker, Phobos and StrongPity, in this instance – sourced their access through these means.
Additional IAB Infrastructure?
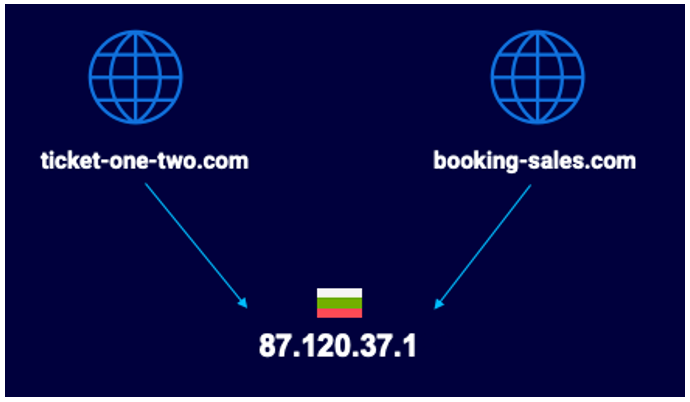
We saw two new domains registered on July 21, 2021, both of which resolved to the same IP address of 87.120.37[.]120:
- ticket-one-two[.]com
- booking-sales[.]com
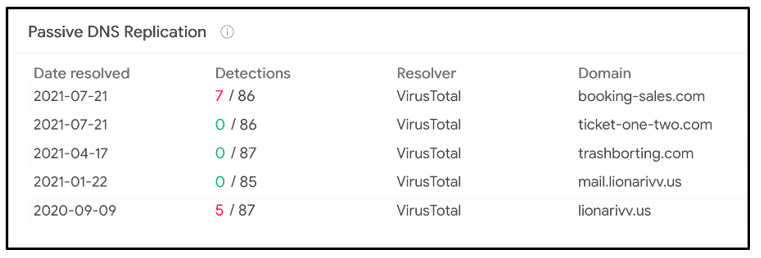
Figure 13 - IP resolution
That is the same IP that trashborting[.]com resolved to, as well as lionarivv[.]us!
Figure 14 - 87.120.37[.]120 reverse resolutions
Ticket-one-two[.]com has not been used at the time of writing, however its counterpart, booking-sales[.]com, had served one specific item of note; a tiny, 13KB portable executable (PE) file that upon inspection proved to be a shellcode loader.
This loader turned out to be loading a shellcode Cobalt Strike DNS stager, which is used to download a Cobalt Strike Beacon via DNS TXT records.
Taking a Closer Look at the Loader/DNS Stager
The shellcode loader expects a specific command-line argument in order to execute properly, which it hashes and then checks against the value 0xB6E35C. Fortunately, we can just patch a comparison and proceed without a match.
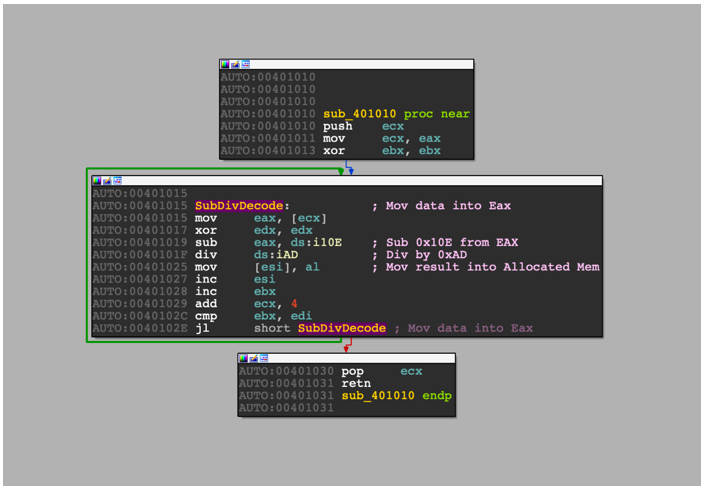
The file then allocates RWX memory using VirtualAlloc, and then decodes data stored within the binary into memory, using a combination of subtraction and division operations – no special cryptography necessary here.
Figure 15 – Subtraction and division decoding loop
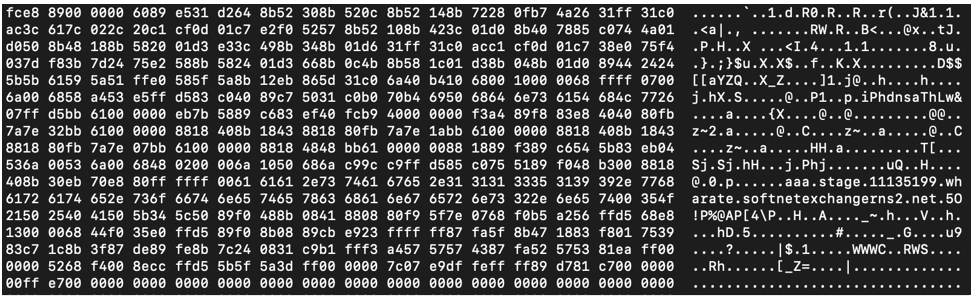
The resulting data is a shellcode blob, which we can identify based on the initial bytes FC E8 89 00 00 00, a fairly typical opcode sequence for shellcode.
Figure 16 - Resulting shellcode
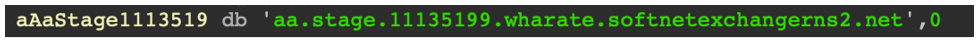
Disassembling the shellcode in the disassembly tool IDA, we can immediately identify a new domain that appears to be trying to masquerade as a DNS name-server:
Figure 17 - A new URL attempting to look like a name server
We can also see what appear to be 4-byte hex values being pushed onto the stack before a call. This is indicative of Windows API import name hashing, a common technique to masquerade the loading of API calls from identification during analysis. This can be seen in Figure 20, where C99CC96A is pushed onto the stack before a call to ebp.
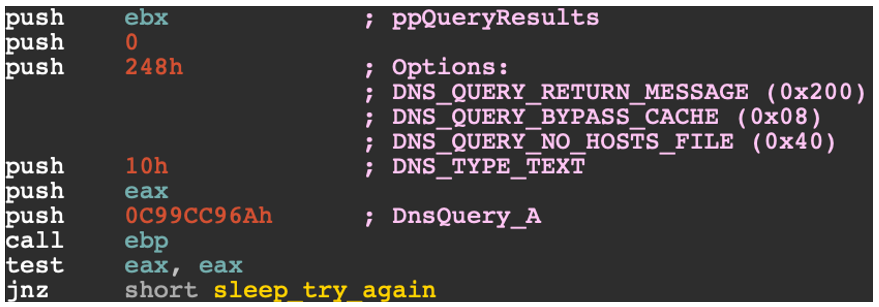
We then see that it performs a DNS query on the URL using DnsQueryA.
Figure 18 - Using DnsQuery_A to query the website’s DNS records
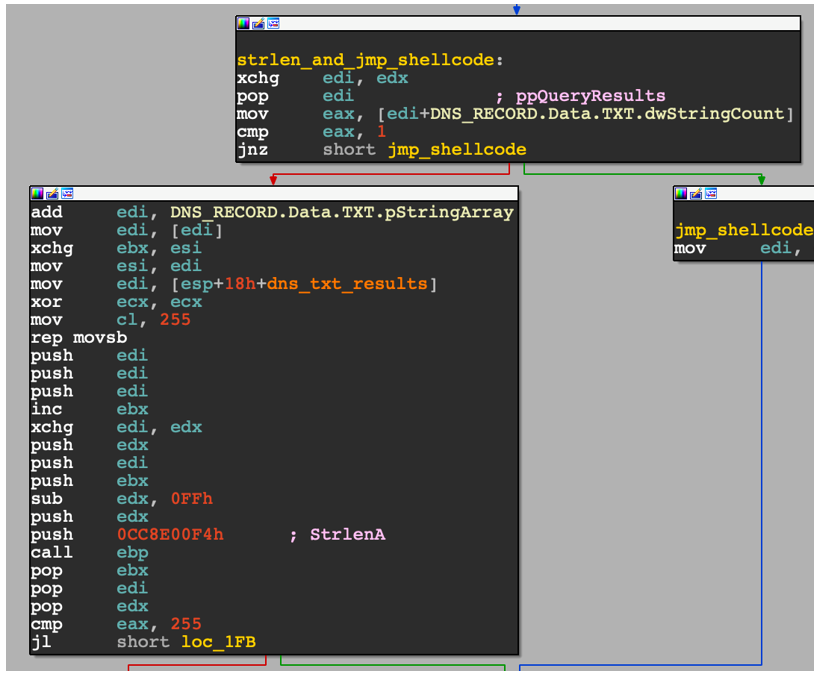
Once it receives a DNS response, it parses out the TXT Record from the DNS response and checks its length, as shown in Figure 19.
Figure 19 - Extracting the TXT record length and data from the DnsQueryA result
This behavior is typical of a DNS stager; it pulls down a later stage payload via the DNS TXT records, abusing the DNS protocol in an attempt to be stealthy. This is also why the domain name was set to masquerade as a DNS name server.
When we look at the Cobalt Strike Malleable C2 documentation, we can see that the URL above in Figure 17 uses a strikingly similar domain in their example. For that reason, we believe this to be a Cobalt Strike DNS stager that will download a Cobalt Strike Beacon upon successful execution.
Figure 20 – A striking similarity to the Cobalt Strike DNS server example from the developer’s documentation
One More Thing, Before You Go!
Now that we’ve seen the potential IAB group infrastructure in all its glory, do you notice anything about the IPs discussed here?
All the domains mentioned in this paper at one time resolved to IPs that were provided by the same Bulgarian Autonomous System Numbers (ASN), which belongs to Neterra Ltd.
This is not to say we believe the threat actor to be Bulgarian, but that all their infrastructure is hosted with one specific company. Furthermore, Neterra isn’t known to be a bulletproof hosting provider; it’s more likely that it’s being abused to facilitate this malicious activity.
The fact that all these IPs are on the same ASN helps us bind together the theory that this is in fact all the work of one threat group, underpinning the operation of the groups it sells its access to.
Figure 21 - Bulgarian IP addresses on the same ASN
Finding Beacons in the Dark
For those of you interested, here’s a shameless plug for our new book “Finding Beacons in the Dark: A Guide to Cyber Threat Intelligence,” which the BlackBerry Research & Threat Intelligence Team has lovingly crafted over the course of this year.
In the book, we demonstrate our Cyber Threat Intelligence (CTI) lifecycle, and show how you can build your own automation system to hunt for threats. In this case, that threat would be the Cobalt Strike Team Server.
We also give you an in-depth look at Beacon configuration and their Malleable C2 profiles, and reveal insights, trends, and discoveries from over 48,000 Beacons and 6,000 unique Team Servers.
In addition, we show you the power of intelligence correlation that can be gleaned from datasets such as these, including how it can be used to:
- Build profiles of threat actors
- Broaden knowledge of existing threat groups
- Track both ongoing and new threat actor campaigns
The end result is that you can then:
- Provide actionable intelligence to SOC analysis, IR teams and investigators
- Reduce “alert fatigue”
- Improve threat detection
- Fine-tune security solutions and services
Conclusions
As is the case with many cyber investigations in today’s threat landscape, this journey began with the analysis of a Cobalt Strike Beacon and the data contained within its configuration. The presence of a single domain – trashborting[.]com – along with both its current and historical resolution information, led us to uncover links to many different campaigns and a new group that the BlackBerry Research & Intelligence Team named, and continues to track, as Zebra2104. This name stems from the use of initial access services that, as a byproduct, allow for threat actors to “hide in the herd.”
One such campaign was the malspam infrastructure previously documented by Microsoft, which was seen to serve an assortment of malware – from ransomware to infostealers – and many more in between. This same infrastructure had also been observed waging a phishing campaign that targeted Australian entities, both in the governmental and private sector, in September of 2020.
When we delved deeper, we found two sister domains that led us down further intelligence avenues, to ultimately identifying both a MountLocker and a Phobos intrusion from the same domain.
We then identified another domain sharing a past IP resolution, linked to the StrongPity APT group by Talos Intelligence in June of 2020.
With three seemingly unrelated threat groups using and sharing overlapping infrastructure, we asked ourselves the question, “What is the most plausible explanation for these peculiar links?” (Especially as these groups’ motives didn’t seem to align.)
We concluded that this was not the work of the three groups together, but of a fourth player; an Initial Access Broker we dubbed Zebra2104, which provided the initial access into victim environments.
The interlinking web of malicious infrastructure seen throughout this research has shown that, in a manner that mirrors the legitimate business world, cybercrime groups are in some cases run not unlike multinational organizations. They create partnerships and alliances to help advance their goals. If anything, it is safe to assume that these threat group “business partnerships” are going to become even more prevalent in future.
To counter this, it is only via the tracking, documenting, and sharing of intelligence in relation to these groups (and many more) that the wider security community can monitor and defend against them. This cooperation will continue to further our collective understanding of how cybercriminals operate.
If the bad guys work together, so should we!
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.